
Weekly Vulnerability Summary by CISA – February 12, 2024; New ICS Advisories
The Cybersecurity and Infrastructure Security Agency (CISA) has once again issued a summary of the latest vulnerabilities. The latest CISA weekly vulnerability summary lists vulnerabilities identified between February 9 and February 17, 2024.
In this blog post, we will highlight critical and high-severity vulnerabilities featured in the CISA weekly vulnerability summary, which could significantly affect organizations’ digital resilience. As we explore this weekly roundup, our focus is on highlighting the most urgent threats, necessitating immediate attention and proactive mitigation efforts.
Overview of the Latest Significant Vulnerabilities
Diverse products are vulnerable to a wide range of critical and high-severity issues. In this review of the weekly CISA weekly vulnerability summary, we will explore vulnerabilities in Apache Solr, Adobe products, SolarWinds, Fortinet, GitHub, and more, highlighting a variety of security issues.
Furthermore, notable vulnerabilities affecting organizations such as IBM, Intel, Dell, Siemens, and SAP have also been mentioned in CISA’s weekly vulnerability summary.
Unrestricted File Upload in Apache Solr:
A high-severity vulnerability, CVE-2023-50386 (CVSS: 8.8), has been discovered in Apache Solr. This vulnerability allows the unrestricted upload of Java jar and class files via the ConfigSets API, leading to potential security risks.
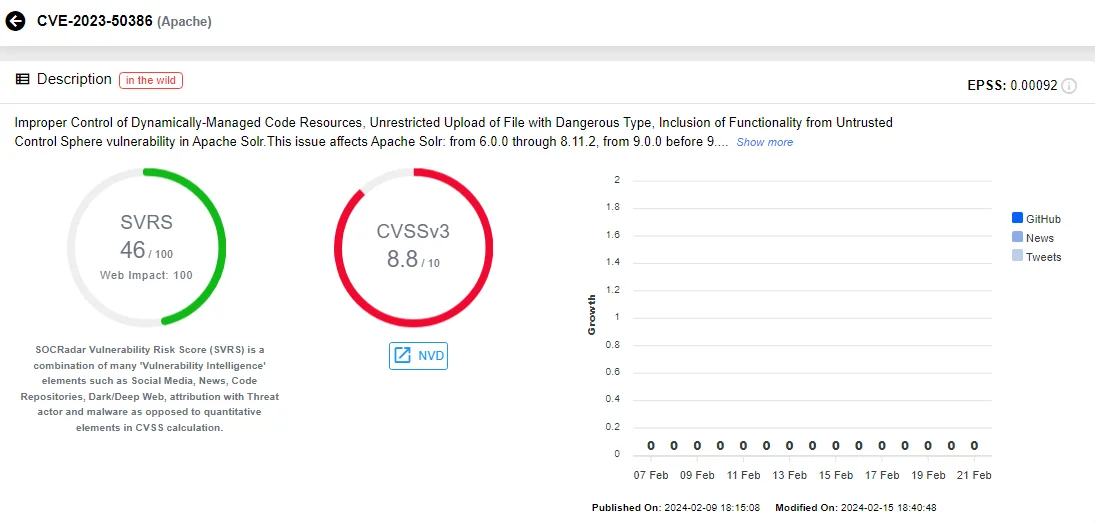
Intel card of CVE-2023-50386 (Source: SOCRadar)
During Solr Collections backup, ConfigSet files are saved to disk using the LocalFileSystemRepository; it poses a threat if these files are stored in directories accessible by Solr’s ClassPath/ClassLoaders, because then the jar and class files would be available to use with any ConfigSet, trusted or untrusted.
Vulnerabilities in Multiple Adobe Products:
Included in the list are also Adobe vulnerabilities affecting FrameMaker and Commerce, tracked as CVE-2024-20738, CVE-2024-20719, and CVE-2024-20720. CISA previously highlighted these vulnerabilities once security updates became available.
The Adobe vulnerabilities are deemed critical and encompass Security Feature Bypass, Cross-site Scripting (XSS), and OS Command Injection issues. For further insights into these vulnerabilities, you can explore another SOCRadar blog post: “CISA Highlights Critical Adobe Security Updates for Acrobat, Magento, and More (CVE-2024-20738, CVE-2024-20719, CVE-2024-20720).”
Severe Command Injection in F5 BIG-IP:
CVE-2024-22093 (CVSS: 8.7), affecting F5 BIG-IP, occurs when operating in appliance mode. This vulnerability involves an authenticated remote command injection flaw within an undisclosed iControl REST endpoint on multi-bladed systems. A successful exploit can enable attackers to breach security boundaries.
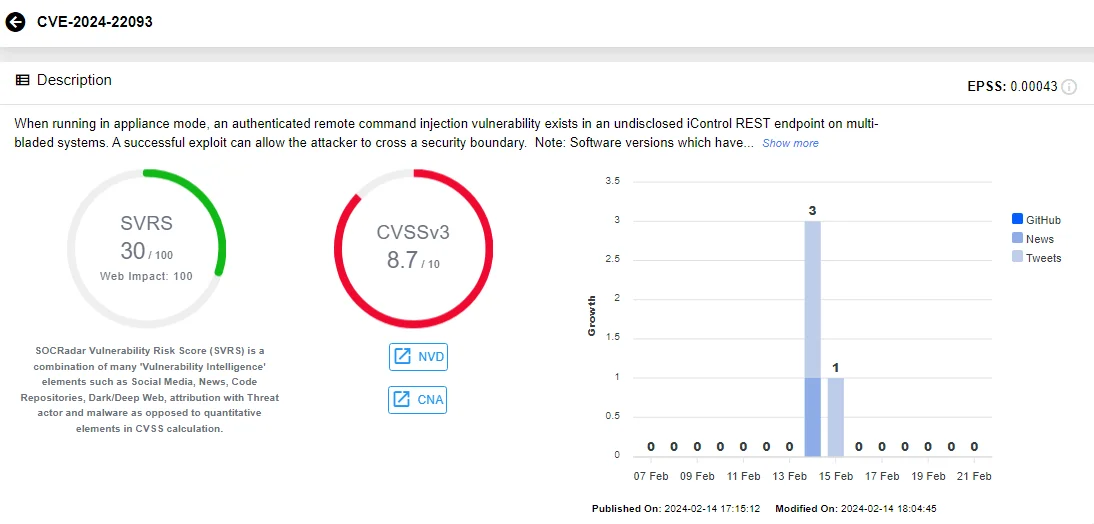
Intel card of CVE-2024-22093 (Source: SOCRadar)
SolarWinds ARM Affected by Several RCE Flaws:
CISA has listed critical Remote Code Execution (RCE) vulnerabilities in SolarWinds Access Rights Manager (ARM) among the latest highly severe vulnerabilities.
Two of these critical vulnerabilities, CVE-2024-23476 and CVE-2024-23479, stem from path traversal issues, while the third, CVE-2023-40057, is an input validation issue.
To learn more about these recent vulnerabilities in SolarWinds and discover methods to safeguard against their exploitation, visit SOCRadar’s blog post: “Multiple Zero-Day and RCE Vulnerabilities Aboard: AutoCAD, SolarWinds ARM, Bricks Builder Under Risk.”
Critical Zoom Vulnerability Affects Products Deployed on Windows:
An improper input validation vulnerability, CVE-2024-24691 (CVSS: 9.6), in Zoom Desktop/VDI Clients, and Zoom Meeting SDK for Windows platforms may enable an unauthenticated user to escalate privilege through network access.
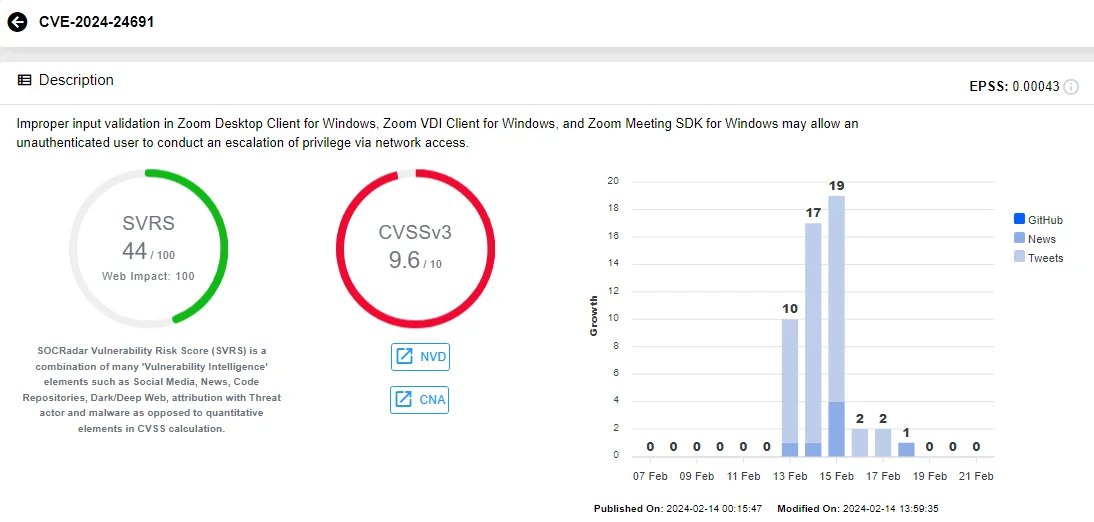
Intel card of CVE-2024-24691 (Source: SOCRadar)
For further details about the vulnerability, read our blog post: “Zoom Addressed Seven Vulnerabilities Across Windows, iOS, and Android, Including One Critical (CVE-2024-24691).”
Critical Fortinet Flaws Could Allow Code Execution:
An out-of-bounds write vulnerability in Fortinet FortiOS and FortiProxy, CVE-2024-21762 (CVSS: 9.8), enables attackers to execute unauthorized code or commands through specifically crafted requests.
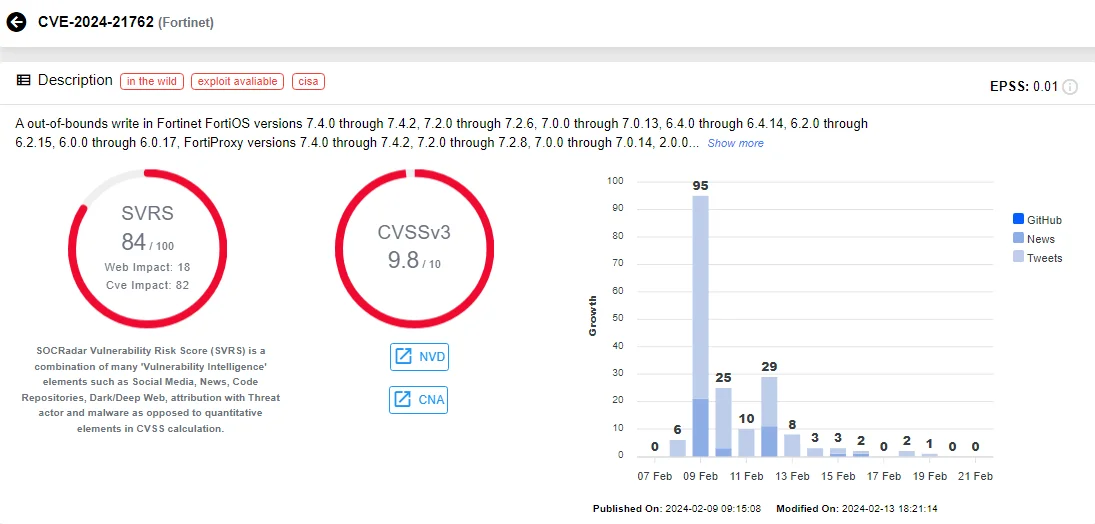
Intel card of CVE-2024-21762 (Source: SOCRadar)
Another critical vulnerability, CVE-2024-23113 (CVSS: 9.8), involving the use of externally-controlled format strings has been discovered in Fortinet FortiOS, FortiPAM, and FortiSwitchManager. Attackers can exploit this vulnerability to execute unauthorized code or commands via specially crafted packets.
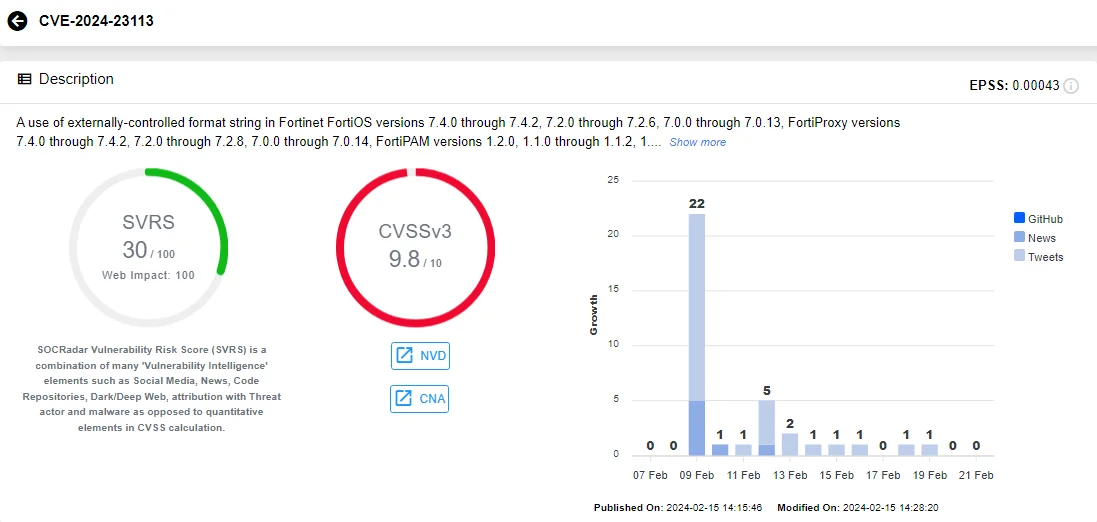
Intel card of CVE-2024-23113 (Source: SOCRadar)
Alongside the critical vulnerabilities identified, a high-severity improper privilege management vulnerability in Fortinet FortiClientEMS, CVE-2023-45581 (CVSS: 8.8), allows a Site administrator with Super Admin privileges to execute global administrative operations affecting other sites via crafted HTTP or HTTPS requests.
Multiple Command Injection Flaws in GitHub Enterprise Server:
Multiple critical command injection vulnerabilities with CVSS scores of 9.1 have been identified, affecting GitHub Enterprise Server. These vulnerabilities enable an attacker with an editor role in the Management Console to gain admin SSH access to the appliance. They were reported through the GitHub Bug Bounty program, and their CVE identifiers are as follows:
Vulnerabilities Addressed in the Latest Microsoft Patch Tuesday:
CISA’s weekly vulnerability summary lists critical Microsoft vulnerabilities; among them are CVE-2024-21410 and CVE-2024-21413, which were addressed in the most recent Patch Tuesday update.
CVE-2024-21410 represents a privilege escalation vulnerability in Microsoft Exchange Server. The advisory for this vulnerability has been updated post-Patch Tuesday to clarify its exploitation as a zero-day threat.
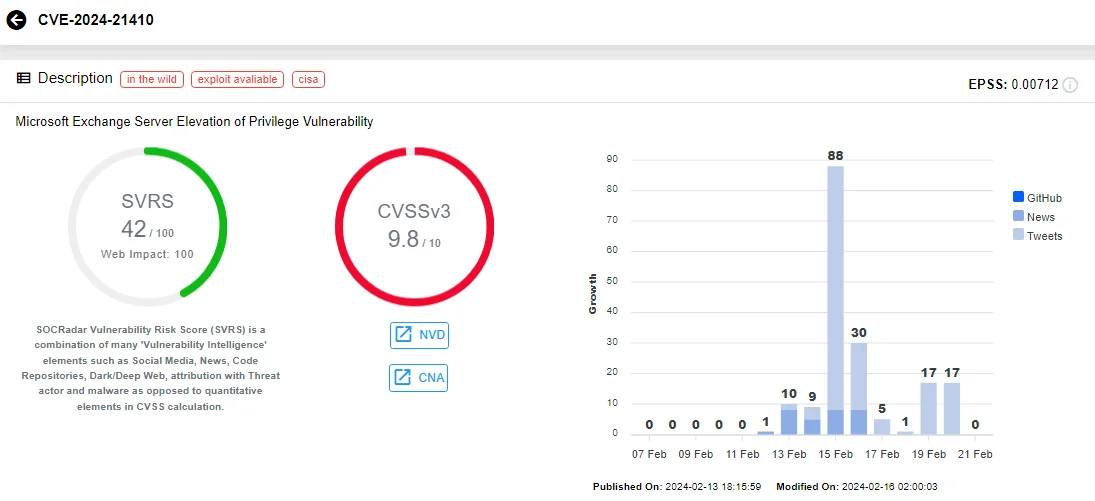
Intel card of CVE-2024-21410 (Source: SOCRadar)
On the other hand, CVE-2024-21413, also known as “Moniker Link” by its discoverer, represents a Remote Code Execution (RCE) vulnerability affecting Microsoft Outlook. This vulnerability is particularly concerning due to its high exploitability.
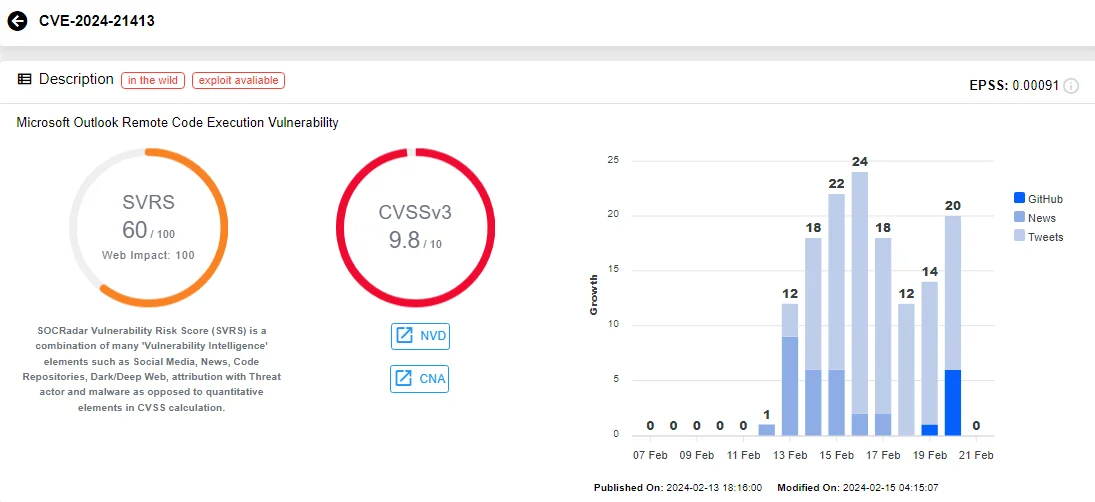
Intel card of CVE-2024-21413 (Source: SOCRadar)
Discover more about these vulnerabilities and their implications in our February 2024 Patch Tuesday Highlights blog post.
Other Microsoft vulnerabilities that have been listed in CISA’s weekly vulnerability summary include Elevation of Privilege (EoP) vulnerabilities such as CVE-2024-21403 (Azure Kubernetes), CVE-2024-21364 (Azure Site Recovery), and CVE-2024-21401 (Entra Jira Single-Sign-On Plugin), along with an RCE vulnerability, CVE-2024-21376 (Azure Kubernetes).
MISP Is Affected by A Critical Vulnerability:
A critical vulnerability labeled as CVE-2024-25675 (CVSS: 9.8) affects MISP, the open-source intelligence sharing platform, before version 2.4.184. The issue arises from a client’s ability to initiate an export generation process without requiring the use of POST requests.
The vulnerability is associated with files located at app/Controller/JobsController.php and app/View/Events/export.ctp.
High-Severity Oracle Vulnerability Could Result in Takeover:
A vulnerability was found in Oracle Agile PLM product of Oracle Supply Chain, CVE-2024-20953 (CVSS: 8.8). This vulnerability affects version 9.3.6 and allows a low-privileged attacker with network access via HTTP to compromise Oracle Agile PLM, potentially resulting in a takeover.
Another vulnerability, in Oracle WebLogic Server product of Oracle Fusion Middleware, CVE-2024-20927 (CVSS: 8.6), allows an unauthenticated attacker with network access via HTTP to compromise Oracle WebLogic Server. Although the primary impact is on Oracle WebLogic Server, attacks may extend to significantly impact additional products.
Latest ICS Advisories by CISA: Critical Vulnerabilities in Commend, Zeek, and Mitsubishi Electric
CISA has issued new advisories addressing security vulnerabilities in Industrial Control Systems (ICS), focusing on products from Commend, Zeek, and Mitsubishi Electric. These advisories contain vital information, urging users and administrators to thoroughly examine them for recommended mitigations and to swiftly secure their ICS environment.
In the following section, we will spotlight the critical vulnerabilities outlined in these recent ICS advisories.
Attackers Can Bypass Access Controls Due to a Severe Vulnerability in Commend Equipment
CVE-2024-21767 (CVSS: 9.4): A remote attacker could potentially bypass access control of Commend’s WS203VICM video door station with a crafted malicious request in versions 1.7 and earlier.
Critical Out-of-Bounds Write Vulnerabilities in Zeek’s Ethercat Plugin
CVE-2023-7243 (CVSS: 9.8): Industrial Control Systems Network Protocol Parsers (ICSNPP) – Ethercat Zeek Plugin versions d78dda6 and earlier are susceptible to out-of-bounds write issues when analyzing specific Ethercat datagrams. Exploiting this vulnerability could lead to arbitrary code execution.
CVE-2023-7244 (CVSS: 9.8): ICSNPP – Ethercat Zeek Plugin versions d78dda6 and earlier are vulnerable to out-of-bounds write flaws in their primary analysis function for Ethercat communication packets. This could permit an attacker to execute arbitrary code.
Mitsubishi EDMs Are Affected by a Critical Microsoft Vulnerability
CVE-2023-21554 (CVSS: 9.8): An RCE vulnerability stemming from the Microsoft Message Queuing (MSMQ) service on Microsoft Windows has been detected in Mitsubishi Electrical Discharge Machines (EDMs).
Mitsubishi Electric has reported that the following EDMs are affected by the vulnerability in the MSMQ service:
- Wire-cut EDM MV Series
- MV1200S, MV2400S, MV4800S
- MV1200R, MV2400R, MV4800R
- Wire-cut EDM MP Series
- MP1200, MP2400, MP4800
- Wire-cut EDM MX Series
- MX900, MX2400
- Sinker EDM SV-P Series
- SV8P, SV12
- Sinker EDM SG Series
- SG8, SG12, SG28
Recommendations
CISA strongly recommends that administrators and users visit the ICS advisories provided and take necessary security measures. When vendor fixes and mitigations are available, they are outlined in the advisories.
Stay informed about the latest security vulnerabilities and ensure your products and software are kept up to date. SOCRadar continually monitors digital assets and issues alerts whenever a vulnerability emerges in your organization’s digital environment.
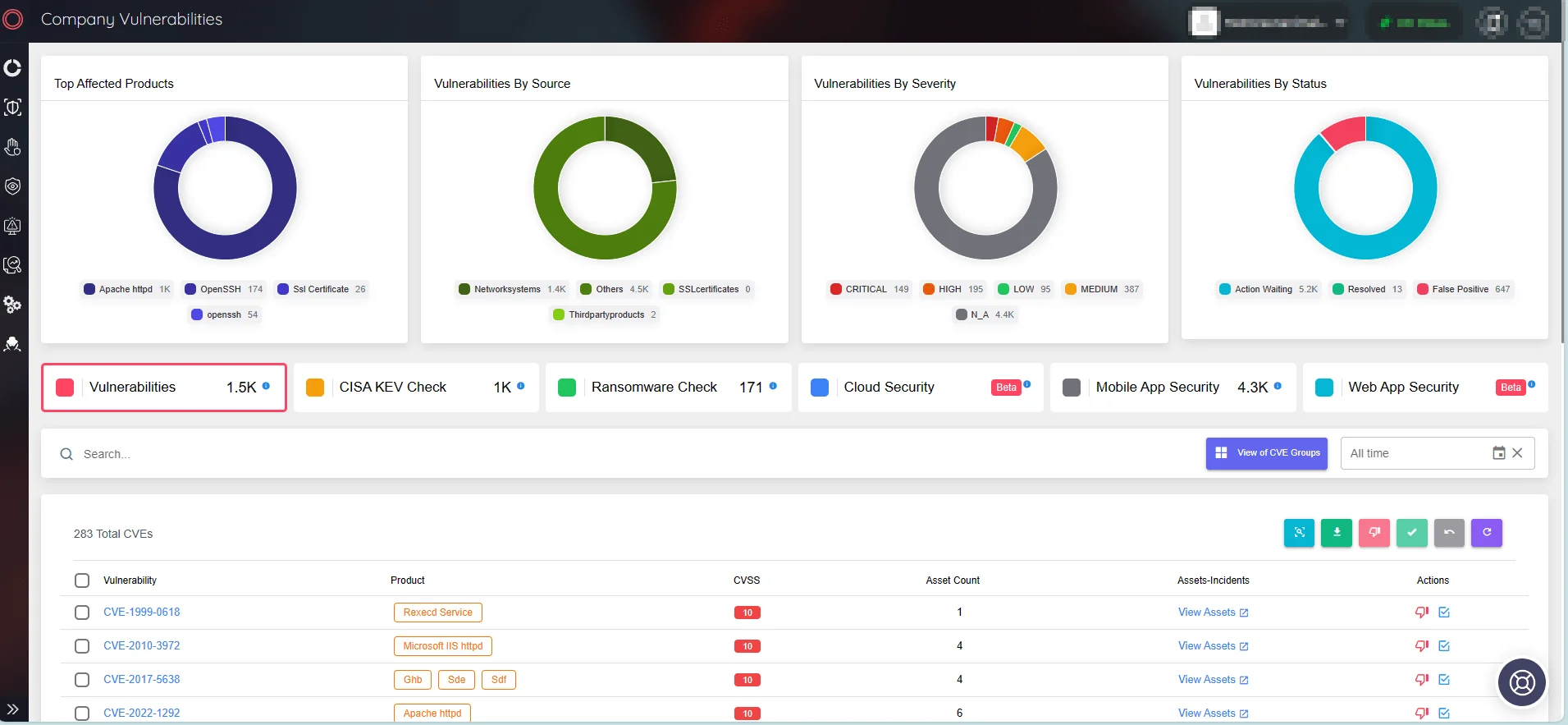
SOCRadar’s Attack Surface Management/Company Vulnerabilities
Use SOCRadar’s Vulnerability Intelligence to effectively manage vulnerability concerns and prioritize patches. Through this platform, you can search for vulnerabilities and access comprehensive details about them, including their lifecycle.
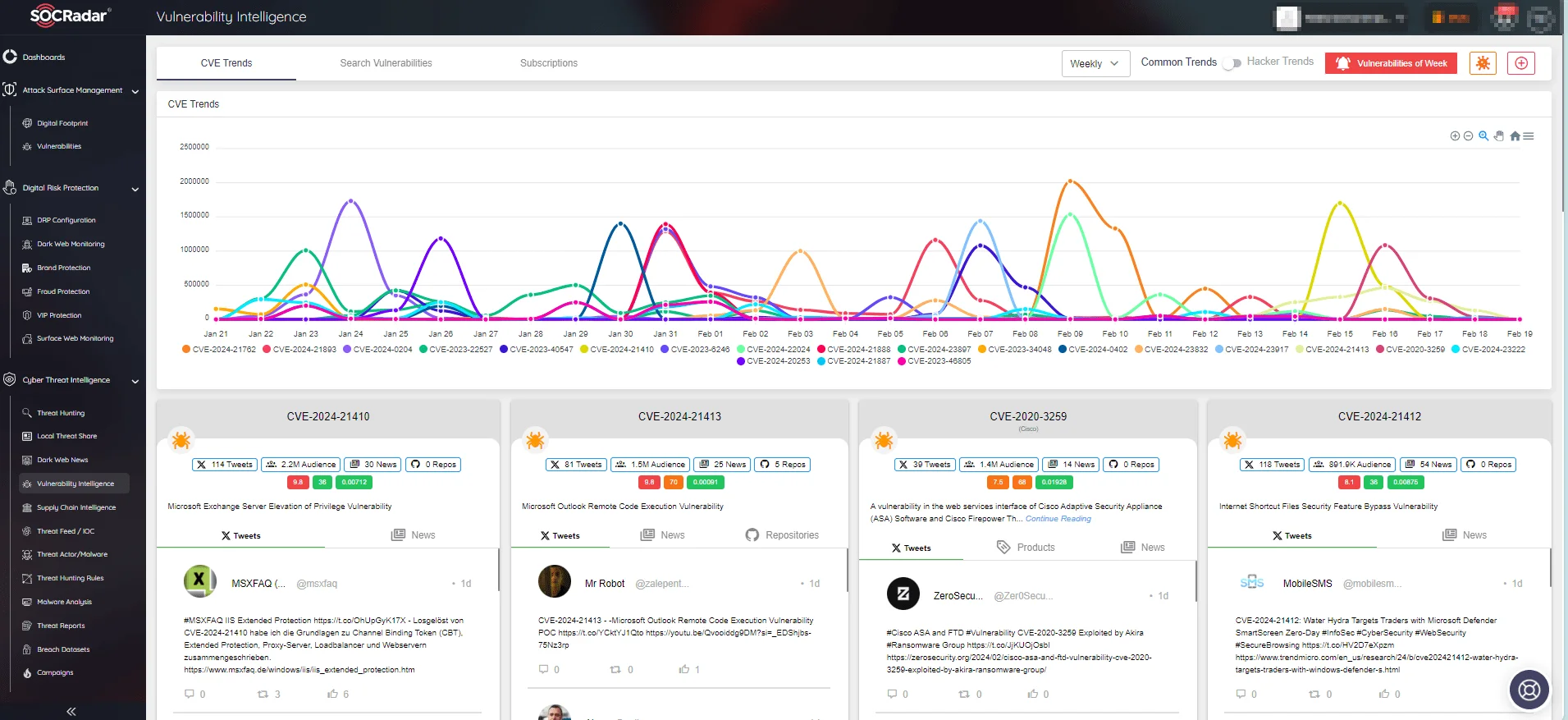
CVE trends on SOCRadar’s Vulnerability Intelligence
Below is an exemplary page showcasing the CVE-2023-21554 vulnerability affecting Mitsubishi’s EDMs.
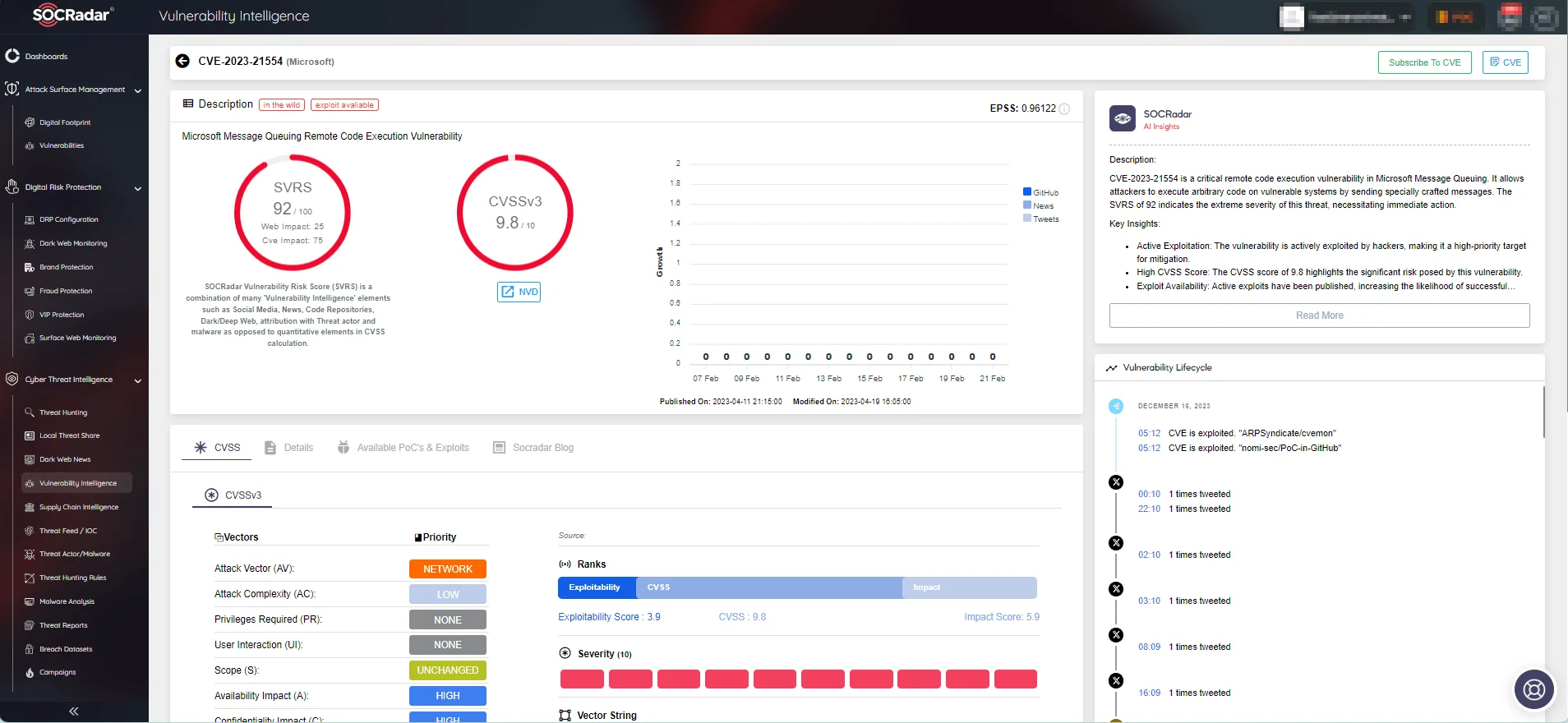
Vulnerability Intelligence page of CVE-2023-21554 (Source: SOCRadar)
Access the latest information about vulnerabilities, such as their exploitability status, utilized attack vectors, and complexity.
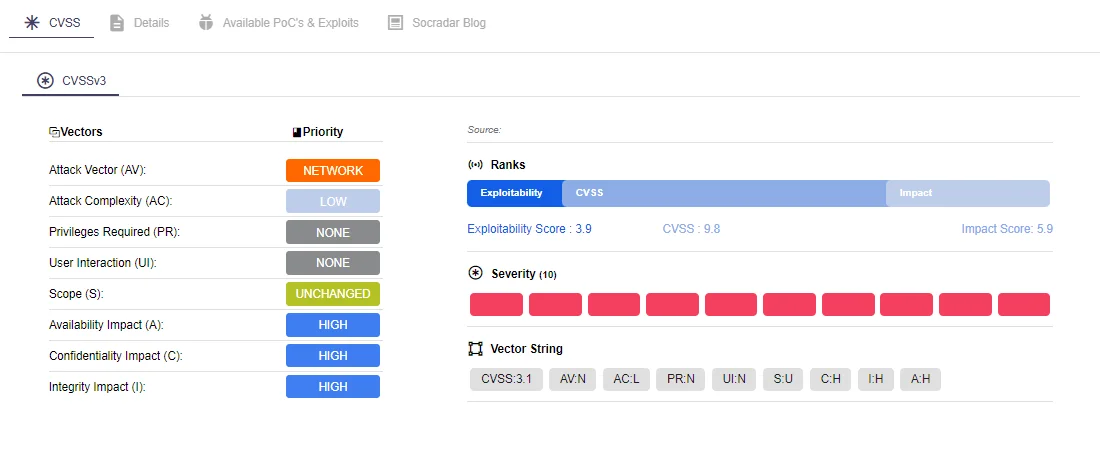
Vulnerability details (Source: SOCRadar)




































