
What is Network Port?
Computers must have an IP address to communicate with each other. IP addresses are divided into ports, which means virtual buses. It means port. However, its equivalent in computer language is a bridge.
Thanks to the port, computers send and receive data. Several files can be sent and received simultaneously over a laptop. For example, while receiving mails from port 120 on the computer, the website can be searched through port 90. These values start from 0 and continue intermittently until 65535.
Physical ports are the areas on a device that connect it to other hardware. Network ports allow devices to talk to each other remotely, routing how information flows from the internet or another program to a computer.
There are two types of ports. UDP(User Diagram Protocol) and TCP(Transmission Control Protocol) ports. There are two types of ports. These are UDP and TCP ports. UDP stands for a data block, and the TCP is the transmission control protocol. Using UDP, data is sent to the other party without establishing a connection.

This system is used in advanced computer networks, and thus message transmission is ensured with minimal protocol mechanism. In TCP, the data send a particular acknowledgment packet. Thanks to the package, it can be seen which byte part is received correctly or not from the boxes that have reached the computer. TCP is the more secure port compared to UDP.
Why Are Network Ports Risky?
A particular port is neither more secure nor riskier than other ports. What determines whether a port is specific is the intended use and how it is handled securely. The protocol used to communicate through a port, service, or application that consumes or generates traffic passing through the port must be valid applications and their manufacturers’ support period.
It should receive security and bug fix updates, and they should be applied on time. Here are some standard ports and how they can be abused.
- Port 21, File Transfer Protocol: An unsecured FTP port hosting an FTP server is significant. Many FTP servers have vulnerabilities in anonymous authentication, lateral movement within the network, access to privilege escalation techniques, and – because many FTP servers can be managed via scripts – a way of cross-site scripting. Malware programs such as Dark FTP, Windows, and WinCrash take advantage of unsafe FTP ports and services.
- Port22, Secure Shell: Secure Shell accounts (SSH) configured with short, non-unique, reused, or predictable passwords are insecure and easily compromised by password dictionary attacks. Many vulnerabilities were and are still being discovered in previous deployments of SSH services and daemons. Patching is crucial to maintaining security with SSH.
- Port 23, Telnet: Telnet is a legacy service and should be deprecated. It is an insecure method of text-based communication. All information it sends and receives over port 23 is sent in plain text. There is no encryption at all. Threat actors can eavesdrop on any Telnet communication and easily select authentication information. They can perform man-in-the-middle attacks by injecting specially crafted malicious packets into unmasked text streams.
Even an unauthenticated, remote attacker could exploit a buffer overflow vulnerability in the Telnet daemon or service and run processes on the remote server by creating malicious packets and inserting them into the text stream. This technique is known as Remote (or corrosive) Code Execution (RCE).
- Port 1080, Socks Proxies: SOCKS is a protocol used by SOCKS proxies to forward network packets on TCP connections to IP addresses. Port 1080 was once one of the ports of choice for malware like Mydoom and many worms and denial of service attacks.
- Port 4444, Transfer Control Protocol: Some rootkits, backdoors, and Trojans open and use port 4444. It uses this port to eavesdrop on traffic and communications, for its communications, and to receive data from the compromised computer. Malware such as the Blaster worm and its variants used port 4444 to create backdoors.
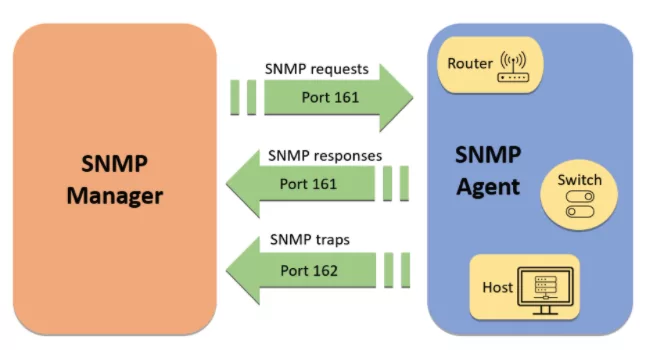
- Port 161, Small Network Messaging Protocol: Some ports and protocols can give attackers much information about your infrastructure. UDP port 161 is attractive to threat actors because it can query data from servers about itself and the hardware and users behind it.
Port 161 is used by the Simple Network Management Protocol (SNMP), which allows threat actors to request information such as infrastructure hardware, usernames, network share names, and other sensitive data, i.e., helpful information to the threat actor.
- Port 53, Domain Name Service: Threat actors should consider the infiltration path that malware will use to send data and files from your organization to their servers.
Because traffic is rarely monitored through the Domain Name Service, port 53 was used as the data theft port.
Threat actors disguise stolen data as DNS traffic and send it to their fake DNS servers. The fake DNS server accepts the traffic and restores the data to its original format.
How to Secure Risky Ports in 12 Ways?
-
It should recognize open ports.
-
Ports that do not have any justification for use should be closed.
- It should be known which services use ports. As part of understanding port usage, it is necessary to learn what processes or protocols are using the port. If the system administrator finds a process or protocol that it does not recognize, it might indicate a security vulnerability.
- The riskiest ports should be closed.
- Port used on the network should be monitored and examined for anomalies or unexplained open ports. Normal port usage should be displayed to identify any unusual behavior.
- The ports used on the network should be monitored and examined for anomalies or unexplained open ports. To identify any unusual behavior, look at what normal port usage looks like. Port scans and penetration testing should be performed.
- SSH ports can be secured through public key authentication and two-factor authentication.
- If it is necessary to use IRC, it is required to ensure that it is behind a firewall and requires IRC users to use a VPN on the network to use it. External traffic should not be allowed to hit IRC directly.
- DNS traffic must be monitored and filtered.
- A deep strategy must be applied, and defense must be multi-layered.
- All unnecessary proxies should be disabled.
- Unwanted HTTP and HTTPS response headers should be removed, and headers included by default in responses from certain network hardware should be disabled.
How SOCRadar Can Provide the Port Monitoring?
Much of the success of cyberattacks or any prevalent threat is due to open ports and cyber assets visible to cybercriminals and threat actors. Threat actors frequently target internet-exposed RDP servers, millions of which are protected by no more than a username and password.
From an external monitoring perspective, SOCRadar enables you to gain continuous visibility into critical or dangerous open ports, which can exploit vulnerable services or malicious traffic via worms or malware.
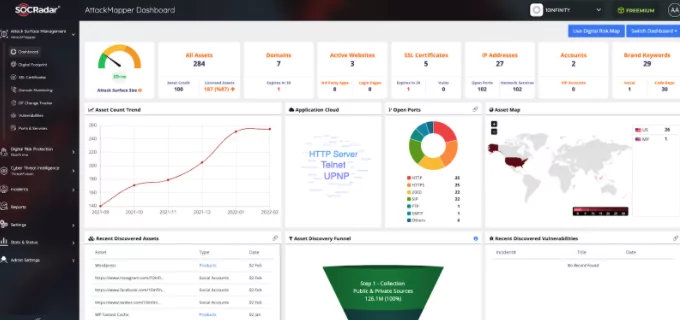
SOCRadar AttackMapper helps customers gain additional visibility and context regarding the severity of unknown external-facing digital assets in an automated manner. Through SOCRadar’s advanced internet-wide monitoring algorithms, AttackMapper provides security teams with direct visibility into all internet-facing technological assets in use as well as assets attributed to IP, Port, DNS, Domain, and cryptographic infrastructure.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free
































