
What is Pretexting? Definition and Examples in Cybersecurity
Pretexting is a social engineering tactic in which attackers fabricate a scenario or a “pretext” to trick people into disclosing confidential information. Unlike other types of social engineering, it relies on creating a credible backstory in order to gain the victim’s trust.
This method is commonly used to obtain sensitive data such as login credentials, financial information, or personal information. Pretexting can take place through a variety of mediums, including phone calls, emails, and even in-person interactions, making it a versatile and dangerous tool in the cybercriminals’ arsenal.
What is a Pretexting Attack?
A pretexting attack occurs when an attacker uses a false identity or role to trick a victim into disclosing sensitive information. The attacker carefully crafts a plausible story or scenario that persuades the victim to trust them, allowing them access to valuable data.
Pretexting attacks are frequently meticulously planned, requiring research on the target to make the deception more convincing. These attacks can have serious consequences, including identity theft, financial loss, or unauthorized access to secure systems.

AI illustration of pretexting
For example, an attacker might impersonate a bank representative and contact a victim under the guise of needing to verify unusual activity on their account. The attacker could use prior research information, such as the victim’s banking habits or recent transactions, to strengthen the story and gain the victim’s trust.
These attacks can also evolve into phishing attacks, which use psychological manipulation techniques such as authority, urgency, and fear. The attacker may claim that the victim’s bank account is about to be frozen due to suspicious activity, instilling a sense of urgency in the victim and pressuring them to comply without fully verifying the request. Attackers may also use tools such as caller ID spoofing or forged email addresses to make their communications appear genuine.
Real-Life Pretexting Examples
Real-life examples of pretexting attacks include scenarios where attackers pose as trusted entities like IT support, law enforcement, or company executives. Here are some real-life pretexting examples:
Deepfake Video of A Company’s CFO
In an outstanding instance from 2024, cybercriminals used generative AI to carry out a sophisticated pretexting attack. A finance employee was deceived into transferring $25 million after participating in a live video call in which the attacker used deepfake technology to impersonate the company’s CFO. This incident emphasizes the growing threat of AI-driven social engineering tactics, which use highly realistic fake personas to deceive victims, making pretexting attacks more effective and dangerous than ever before,If you want to check more details about deepfake incidents and this scam, check our CISO Guide to Deepfake Scams blog post.
Retool’s SMS-Based Cyber Attack

Retool logo
In August 2023, Retool, a software development company, experienced a severe cyber attack initiated by pretexting. Attackers impersonated IT team members, sending SMS messages that tricked an employee into clicking a link related to a payroll issue. This pretext allowed the attackers to infiltrate Retool’s internal systems, leading to the theft of nearly $15 million worth of cryptocurrency.
Job Scams Exploiting Tech Layoffs
In early 2023, scammers took advantage of the wave of layoffs in the technology industry by creating fake job postings and impersonating recruiters from well-known companies. They created fraudulent job portals that looked like legitimate job sites in order to trick job seekers into disclosing sensitive personal information. By posing as hiring managers from reputable companies such as Zscaler, these attackers gained victims’ trust and led them through a bogus application and interview process. Finally, the scammers exploited this pretext to steal personal information and, in some cases, extort money from victims.
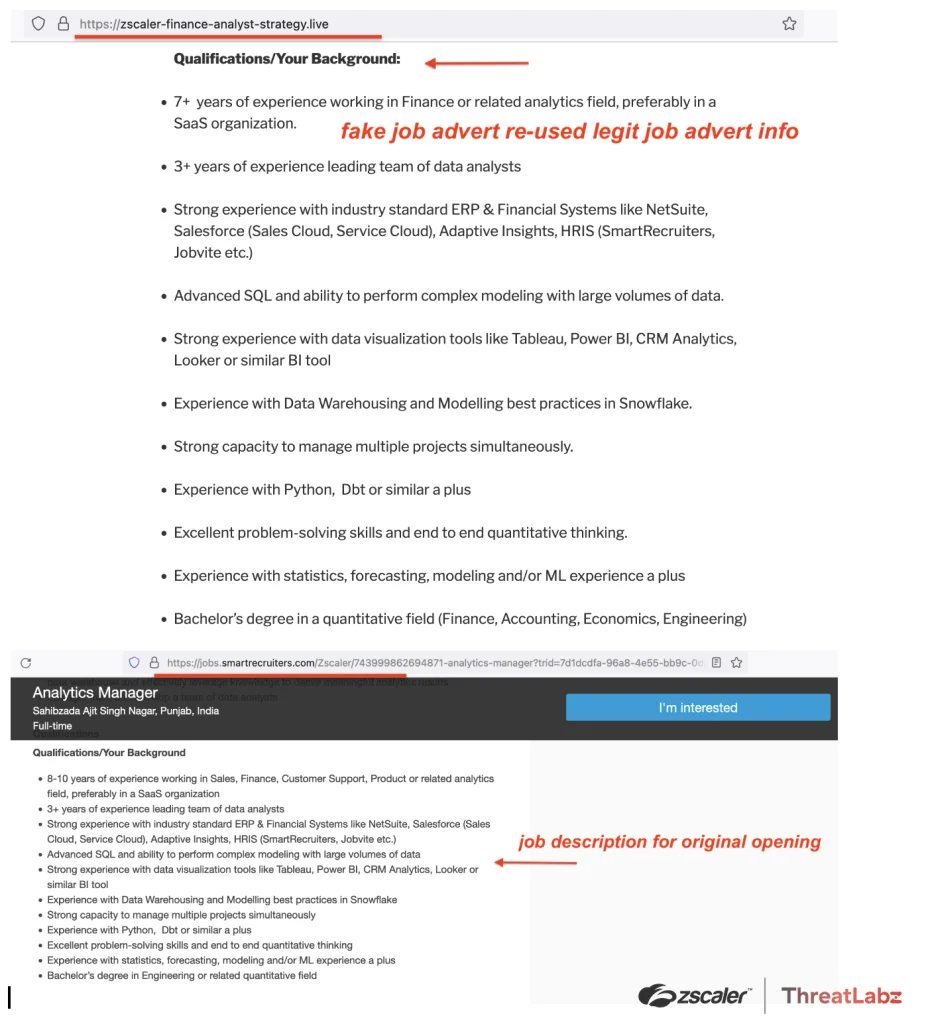
Fake job application copied from Zscaler posted on SmartRecruiters (Source: Zscaler)
What is the Difference Between Pretexting and Phishing?
Pretexting and phishing are both social engineering tactics, but they differ in their approach and objectives. Pretexting involves careful planning and setting up a scenario to build trust with the victim over time, aiming to create a believable situation that leads to information disclosure.
In contrast, phishing typically involves urgent, fear-driven emails that push victims to act quickly, often by clicking a malicious link or providing sensitive information. In some cases, these tactics can overlap, with pretexting used to set the stage for a phishing attack.
Conclusion
Pretexting exemplifies the complex and changing nature of social engineering tactics in cybersecurity. As cybercriminals improve their tactics, the importance of vigilance and proactive defense measures cannot be overstated. Pretexting, whether through the use of deepfake technology, targeted job scams, or the impersonation of trusted figures, has the potential to have a significant impact on individuals and organizations.
Pretexting is an effective reminder of the ever-changing tactics used by cybercriminals to deceive and exploit individuals and organizations. As these attacks become more sophisticated, the need for strong protective measures becomes more urgent. This is where SOCRadar’s Brand Protection Module comes in, providing an important layer of defense against impersonation and exploitation of your brand.
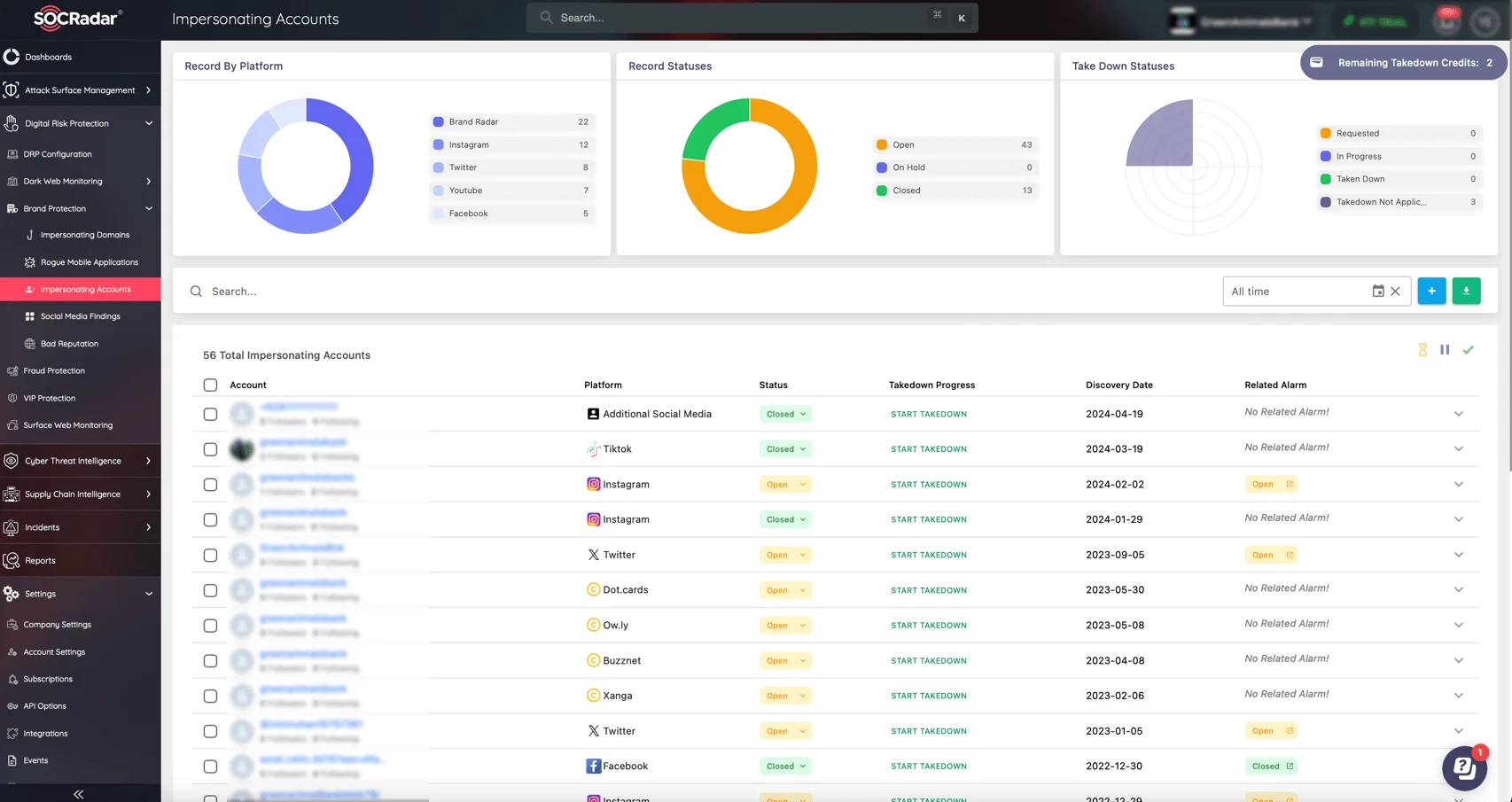
SOCRadar’s Brand Protection module Impersonating Accounts service
With SOCRadar’s Brand Protection Services, security teams can stay one step ahead of threat actors by receiving actionable intelligence alerts that detect and neutralize threats before they cause harm. The module is especially effective at detecting and responding to impersonated accounts on social media, hacker forums, and other digital platforms.
SOCRadar helps to avoid brand discreditation, legal issues, and intellectual property theft by automatically monitoring these channels. SOCRadar’s proactive monitoring and rapid takedown capabilities will enable your security teams to protect your brand’s reputation and integrity, ensuring that your organization remains resilient in the face of ever-present cyber threats.


































