What is the Role of Single Sign-On in Security Measures? – Part 2
By SOCRadar Research
Read the previous article: What is the Role of Single Sign-On in Security Measures? – Part 1
Maintaining easy and secure Identity and Access Management in an enterprise environment is vital. The need might stem from weary users who have to memorize different credentials for different services and also jaded administrators who have to carry out the overload of credential management. Or simply to have a better security posture. Single Sign-On can provide both easiness and security if implemented correctly. It will help mitigate security risks by reducing the attack surface. However, if not implemented with additional security measures such as MFA, it has its downsides.
Potential Challenges/Risks of Single Sign-On
- Stolen Credentials: Suppose there are no additional security measures in an environment with an SSO solution. In that case, a stolen credential means the attacker can access anything the user can.
- Application Compatibility: Some applications may not support the SSO solution in the environment. This can challenge both users and administrators because it adds another credential to memorize and manage.
How can Threat Actors Target SSO?
Vulnerabilities for SAML, Kerberos, and OAuth have been previously discovered. Golden Ticket Attack can be given as an example. In Golden Ticket Attack, the attacker abuses the Kerberos protocol’s trust relationship between KDC and KRBTGT service user. KRBTGT is used to generate Kerberos tickets required to access resources. If the attacker possesses the password hash for the KRBTGT service user, they can generate Kerberos tickets to their desire.
MITRE ATT&CK® framework can be referenced to provide a picture. Mitre associates some tactics and techniques concerning SSO. These are:
|
ID |
Name |
|
TA0006 |
Credential Access |
|
T1110.001 |
Brute Force: Password Guessing |
|
T1110.003 |
Brute Force: Password Spraying |
|
T1110.004 |
Brute Force: Credential Stuffing |
|
T1606.002 |
Forge Web Credentials: SAML Tokens |
|
T1003.001 |
OS Credential Dumping: LSASS Memory |
SSO manages credentials, so it is not surprising that SSO-related Mitre techniques are all about credentials. From the techniques Mitre associates with SSO, you can understand that the Brute Force technique is key when targeting SSO systems.
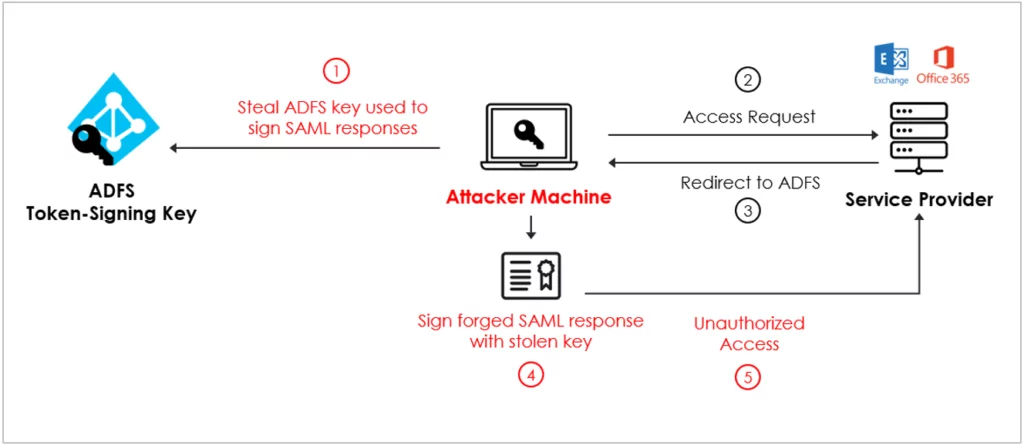
Golden SAML Attack
Golden SAML is a vulnerability found on SAML. Threat actors leverage the “Golden SAML” attack technique to forge SAML responses. With that, they can bypass ADFS authentication to access federated services. To successfully leverage Golden SAML, a threat actor must first gain administrative access to the ADFS server and extract the necessary certificate and private key. Once this is accomplished, anyone can perform unauthorized access from anywhere without further access to the victim’s environment. In 2020, APT 29, also known as Fancy Bear, or Cozy Bear, a Russia-linked threat actor, breached the SolarWinds Orion network management software. The compromise created a storm around the globe, affecting 18000 organizations. The US Treasury Department and Microsoft were among the victims of the attack.
How to Reduce the Risks of Single Sign-On
- More security measures for authentication: At the very least, 2FA or MFA should be used while authenticating to prevent attackers from accessing the system with stolen credentials.
- Implementation of the least privileged principle: The least privileged principle should be considered while implementing an SSO solution. The user should always access the least number of resources they need with the least amount of control over it to perform their tasks.
- Attack Surface Management with Threat Intelligence Services: Attack Surface Management provides an organization with the visibility of external-facing digital assets from the point of attackers. It is an automated process where ASM tools constantly monitor the organization’s digital infrastructure for potential threats. In the context of SSO, it is crucial to know whether or not the SSO solution implemented in the environment is vulnerable.
Conclusion
In March 2022, Okta was breached by the infamous ransomware group Lapsus$. In the confirmed breach, around 2.5 percent of Okta’s customer base, more than 350 companies, was affected. SOCRadar monitors unwanted exposure to protect your business against external cyber threats. It draws on a growing collection of data and processes it through advanced analytics algorithms and a team of talented analysts. In a case such as Okta’s breach, monitoring can help organizations detect if their top-level executives’ credentials, employee emails, or customer accounts have been compromised.