
What Type of Social Engineering Targets Senior Officials
Cybercriminals often utilize various social engineering tactics to manipulate and take advantage of human psychology to trick others into disclosing private information or taking activities that jeopardize security.
Because they have access to sensitive information and decision-making authority within businesses, senior officials are often the targets of social engineering attacks. Here, we will discuss what kind of social engineering techniques target top officials and how organizations can protect themselves from social engineering.
Social Engineering Attack Types Targeting Senior Officials
Whaling Attacks
Whaling attacks are a sophisticated form of spear phishing that specifically targets senior officials within an organization. These attacks are designed to deceive executives into sharing sensitive information or performing actions that compromise security, such as transferring funds to fraudulent accounts or granting access to secure systems.
Business Email Compromise (BEC)
Business Email Compromise (BEC) is a type of social engineering attack that specifically targets senior officials, particularly those involved in financial transactions. Threat actors gain access to a legitimate email account to impersonate trusted vendors or partners and use it to request fraudulent wire transfers or payments.
The reason why threat actors target senior executives is that they often have the authority to approve financial transactions without extensive scrutiny.
One of SOCRadar’s free tools, Phishing Radar, provides you with the ability to detect domain spoofing and phishing.
Phishing Radar in SOCRadar Labs SOC Tools
Spear Phishing
Spear phishing is a targeted form of phishing that focuses on specific groups. Unlike general phishing attacks that cast a wide net, spear phishing leverages detailed information about the target to establish trust and create a false sense of security.
The difference between spear phishing and whaling attacks is that in spear phishing attacks, threat actors target a specific group while in whaling attacks they target only high level individuals.
Sometimes these kinds of terms can be confusing since they overlap in various areas. You can check out our blog for a better understanding of the differences between these two types of phishing attacks.
Vishing (Voice Phishing)
Vishing, or voice phishing, is a social engineering technique that uses phone calls to manipulate victims into sharing sensitive information or performing actions that compromise security. Vishing attacks targeting senior officials often involve impersonating trusted contacts, such as IT support or financial institutions, to gain the victim’s trust.
Vishing scammers also spoof caller ID to make their phone numbers appear legitimate. They may have detailed personal information about the victim obtained through data breaches or social media to make the call seem more convincing.
Whaling Attacks: A Deep Dive
What is Whaling?
Whaling is a sophisticated phishing attack that specifically targets high-profile individuals within organizations, such as CEOs, CFOs, and other senior executives. Unlike traditional phishing attacks, in which the threat actors try to deceive many people, whaling focuses on a single target.
Threat actors often spend a significant amount of time gathering enough information about their targets for whaling attacks. Since they only have one target and, in certain cases, only one opportunity, they utilize social media and other publicly available sources and learn everything they can. Afterward, they use this information to craft highly personalized and legitimate-looking communications.
Whaling Techniques
At the end of the day, whaling attacks are essentially a more sophisticated form of phishing, specifically targeting high-ranking officials. Threat actors employ various tactics to deceive their victims, often creating a sense of urgency to prompt immediate actions, such as wire transfers or the disclosure of sensitive information. Additionally, they frequently use fake documents, like invoices, to trick individuals into processing unauthorized payments. To further legitimize their malicious attempts, these actors often utilize spoofed emails, making their messages appear to be from a trusted source.
For a comprehensive look at how to detect phishing attacks, you can check our detailed blog post here.
How to Protect Senior Officials from Social Engineering Attacks
Importance of Tailored Security Measures
Each organization has a different culture, communication style, and way of doing business. Since social engineering attacks are more about human interactions and convincing people, the social side of the business becomes more important than the technical capabilities.
That’s why tailored security measures are essential to protect senior officials from social engineering attacks. “One software for all” type of solutions won’t work in these situations because every company has a different web of relations. Instead, companies should look for products or services that can be modified based on their needs.
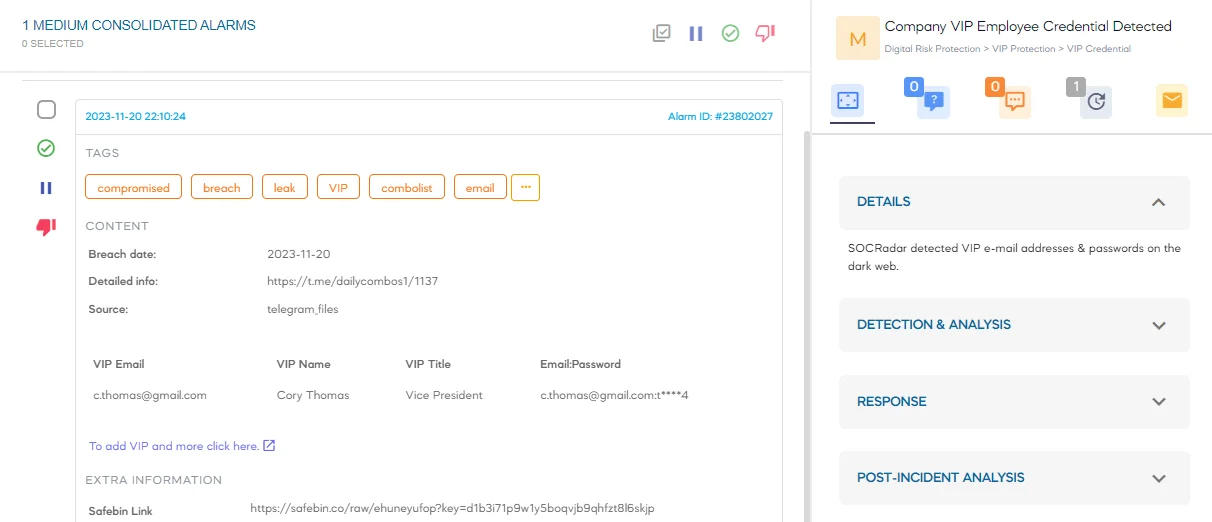
SOCRadar’s VIP Protection module
Monitoring for exposed personal data or the impersonation of key executives can mitigate risks in both the cyber and physical realms. SOCRadar’s VIP Protection enables security teams to search and monitor the personal email addresses of C-suite executives, checking if they’ve been indexed in the expanding database of significant global breaches that could be targeted by your adversaries. This way, SOCRadar enables organizations to effectively track unique breadcrumbs relevant to their needs.
Training and Awareness Programs
Senior officials must receive ongoing training to identify and prevent social engineering attempts. Since these risks are constantly changing, executives can attend training on the latest threats to stay up to date on the newest strategies employed by hackers.
Since SOCRadar knows the importance of training, we are planning new webinars and workshops based on the latest developments in the threat landscape. You can see our upcoming events and register here.
Another important aspect of training programs comes from the nature of humans. Unlike software vulnerabilities, which remain fixed once patched, human memory fades over time, and the dynamics of a workforce constantly change with the onboarding of new employees. To mitigate the risks of social engineering attacks, it is crucial to maintain ongoing training.
SOCRadar Academy
SOCRadar is an XTI (Extended Threat Intelligence) provider but at the same time, we offer educational content in order to improve the general security structure of organizations. SOCRadar Academy offers flexible online training modules, allowing your colleagues to learn at their own pace while covering essential topics related to cybersecurity.
Conclusion
Protecting senior officials from social engineering attacks is paramount in today’s increasingly complex cyber threat landscape. These high-profile individuals are prime targets due to their access to sensitive information and decision-making authority, making it essential for organizations to implement tailored security measures that address the unique risks they face.
Understanding what type of social engineering targets senior officials is the first step in developing effective strategies to mitigate these threats.




































