Your Data Is Not Safe: 8Base Deanonymized
In the ever-evolving world of cybercrime, the 8Base ransomware group has recently come under the spotlight. Known for its victim-shaming website, this group inadvertently revealed more than they probably intended. This article delves into the unexpected information leaks and the surprising connections that emerged from the 8Base darknet website by KrebsonSecurity’s blog.
The Darknet Website and Its Unexpected Vulnerabilities
8Base operates a darknet website accessible only via TOR, which lists hundreds of victim organizations and companies. These are primarily hacking victims who declined to pay a ransom, risking the publication of their stolen data. A unique feature of this website is its built-in chat, designed for victims to negotiate with their extortionists. However, a recent attempt to fetch data from this chat service resulted in a verbose error message, unintentionally revealing the IP address of the hosting, which serves as TOR hidden service. This error led to the discovery of a server in Finland associated with the Germany-based hosting giant, Hetzner.
- As a side note: A researcher known as @htmalgae on Twitter provided information about the vulnerable 8Base website to Krebs. According to @htmalgae, it is probable that the developer of the 8Base website unintentionally left it in “development mode,” leading to the excessive verbosity of its error messages. @htmalgae stated that if 8Base had operated the application in production mode rather than development mode, the TOR de-anonymization issue would not have arisen.
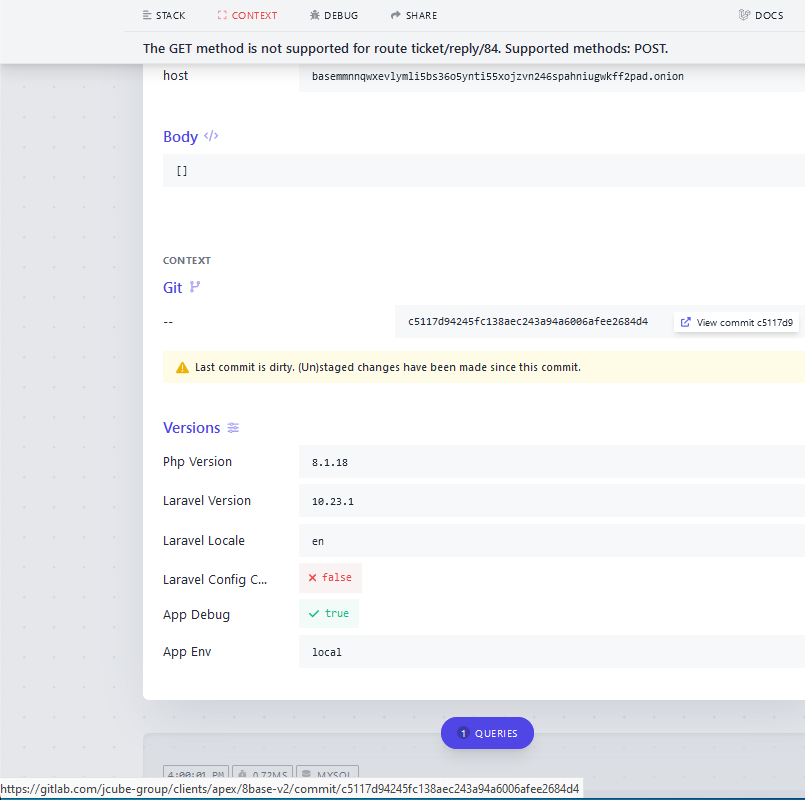
- The lengthy error message that appears when attempting to retrieve information from 8Base’s darknet website. Take note of the link displayed at the bottom of this image, which becomes visible when hovering over the “View commit” message found in the “Git” section.
Digging deeper, the error message provided a link to a private Gitlab server, JCube Group. This server’s public code repository contained several intriguing data points, including mentions of the term “KYC” (Know Your Customer). This term is significant as the 8Base darknet site has a section offering “special offers for journalists and reporters,” requiring them to undergo a KYC procedure.
JCube Group and the Developer Connection
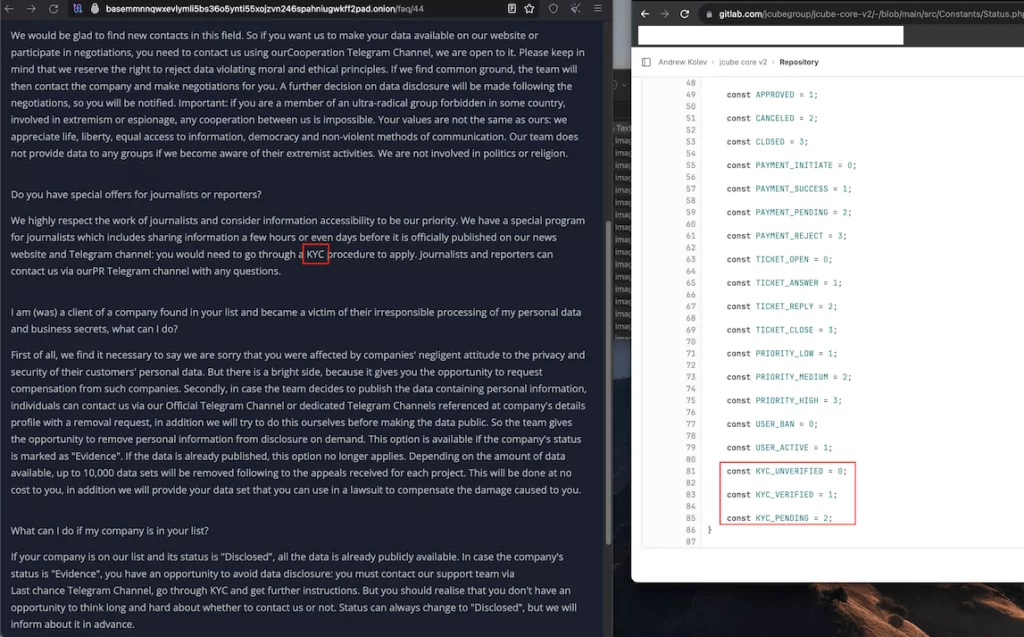
Further investigation into the 8Base website revealed a publicly accessible “admin” login page. The HTML code of this page bore a striking resemblance to a page from the JCube Group’s Gitlab repository. This connection led to Andrei Kolev, a 36-year-old developer from Chisinau, Moldova, associated with JCube Group. When approached, Kolev expressed unawareness about the link between his code and the 8Base website. Interestingly, the 8Base website underwent changes shortly after this interaction, and the revealing error message disappeared.
When Krebs tried to contact him, Mr. Kolev allegedly asserted that he had no knowledge of the previously removed error page on 8Base’s website, which referred to his private Gitlab repository. He also mentioned that he deleted the screenshot from our LinkedIn chat because it contained sensitive information.
Ransomware Tactics and Insights
8Base Ransomware group has emerged as a significant threat. According to our detailed profile, 8Base has been active since April 2022 and has rapidly gained notoriety for its aggressive tactics, primarily targeting small and medium-sized businesses across diverse sectors. Their modus operandi includes double-extortion tactics, where they encrypt a victim’s data and threaten its public release unless a ransom is paid. The group employs various ransomware strains, notably a variant called Phobos, suggesting their affiliation with Ransomware-as-a-Service (RaaS) offerings. Their digital presence is evident through their TOR website, which showcases victim announcements and features structured sections like FAQs. Interestingly, their communication style bears similarities to another group, RansomHouse, leading to speculations about potential connections. With a primary focus on companies in the United States, Brazil, and the United Kingdom, 8Base’s activities have surged, marking them as a significant player in the ransomware arena.
It’s evident that ransomware groups, like 8Base, often hire developers for specific tasks without revealing their true intentions. It’s possible that one of Kolev’s clients might be a front for 8Base. This practice underscores the covert operations of such groups and the challenges in tracing their activities. Nevertheless, it appeared that the repository name of the project was 8base.
In Conclusion
The 8Base ransomware group’s recent leaks offer a rare glimpse into the intricate web of cybercrime. These situations emphasize the importance of cybersecurity vigilance and the continuous challenges posed by ransomware groups but also their weaknesses. As the digital landscape evolves, staying informed and proactive is our best defense against such threats. One such way to achieve this stance is using SOCRadar Extended Threat Intelligence Platform.
SOCRadar is committed to continuously monitoring threat actors, explicitly focusing on ransomware groups such as 8Base. Our goal is to provide our users with actionable intelligence. In line with this objective, we are introducing the Vulnerability-Ransomware Check, a feature within our Attack Surface Management module. This feature conducts comprehensive scans of our users’ assets, considering security vulnerabilities commonly exploited by ransomware groups, and then presents the results.