
Zyxel NAS Devices’ EoL Models Patched for Critical Code Execution Vulnerabilities: CVE-2024-29972, CVE-2024-29973, CVE-2024-29974
[Update] June 24, 2024: “Critical Zyxel NAS Vulnerability (CVE-2024-29973) Exploited by Mirai-like Botnet”
Zyxel has issued critical security updates for its NAS (Network-Attached Storage) devices, namely for the NAS326 and NAS542 models, both of which have reached End-of-Life (EoL) status.
These updates for Zyxel NAS devices are of great importance as they address multiple critical vulnerabilities that could potentially allow unauthenticated, remote attackers to execute arbitrary code and operating system (OS) commands, compromising the security of the systems using these devices.
Latest Zyxel NAS Vulnerabilities: Details of CVE-2024-29972, CVE-2024-29973, CVE-2024-29974, …
Security researcher Timothy Hjort has identified the vulnerabilities in Zyxel’s NAS326 and NAS542 devices. These vulnerabilities pose significant risks as they allow unauthenticated remote attackers to perform dangerous actions such as executing OS commands and running arbitrary code.
The most critical vulnerabilities in the update are as follows:
- CVE-2024-29972 and CVE-2024-29973 (CVSS 9.8): These are command injection vulnerabilities found in different parts of the system.
CVE-2024-29972 affects the “remote_help-cgi” CGI program, allowing the execution of OS commands via a crafted HTTP POST request.
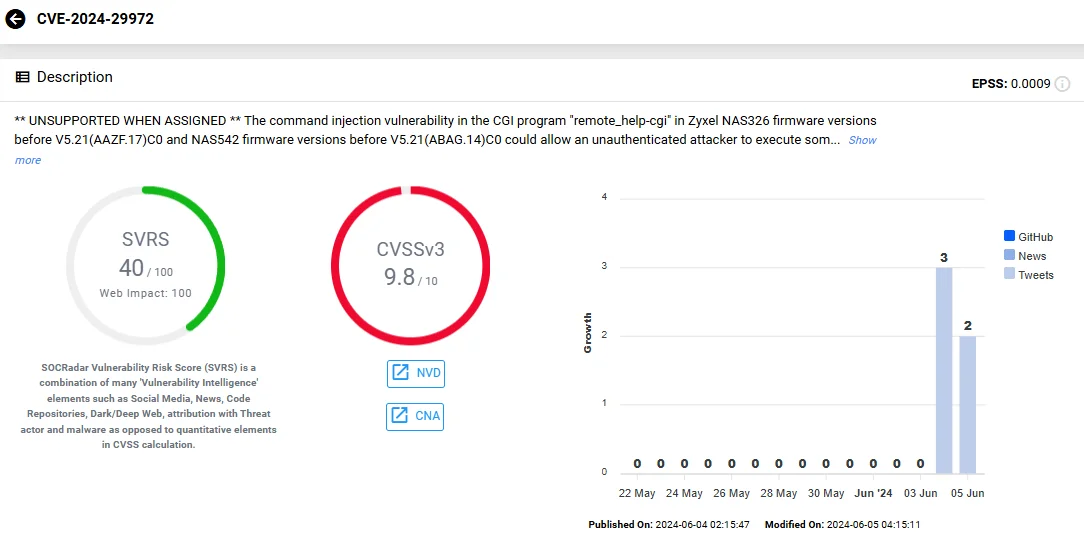
The vulnerability card of CVE-2024-29972 (SOCRadar Vulnerability Intelligence)
Similarly, CVE-2024-29973 stems from a vulnerability in the ‘setCookie’ parameter, which also permits OS command execution through a specially crafted HTTP POST request.
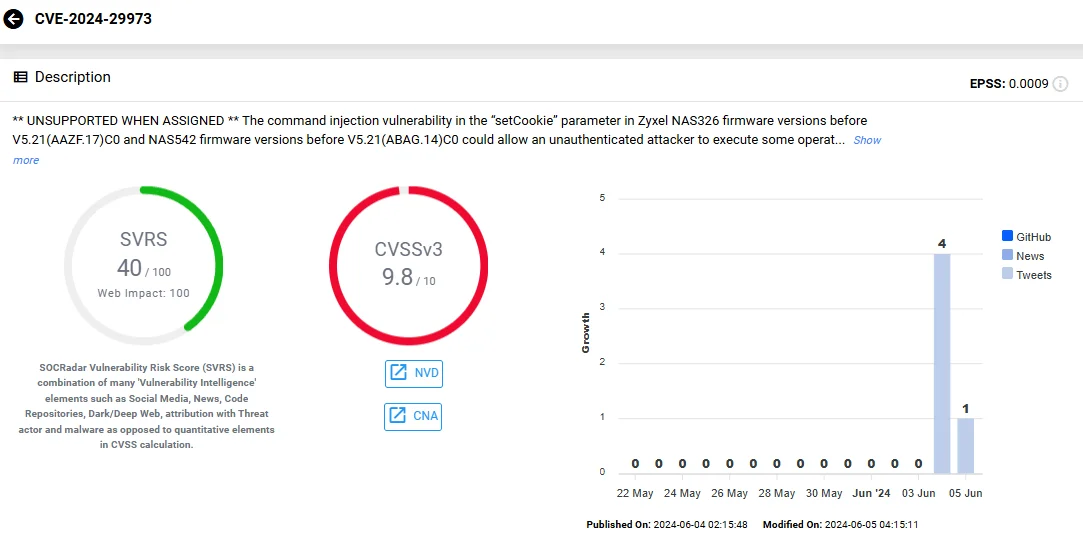
The vulnerability card of CVE-2024-29973 (SOCRadar Vulnerability Intelligence)
- CVE-2024-29974 (CVSS 9.8): This Remote Code Execution (RCE) vulnerability is found in the CGI program ‘file_upload-cgi’. It enables attackers to run arbitrary code by uploading a specially crafted configuration file.
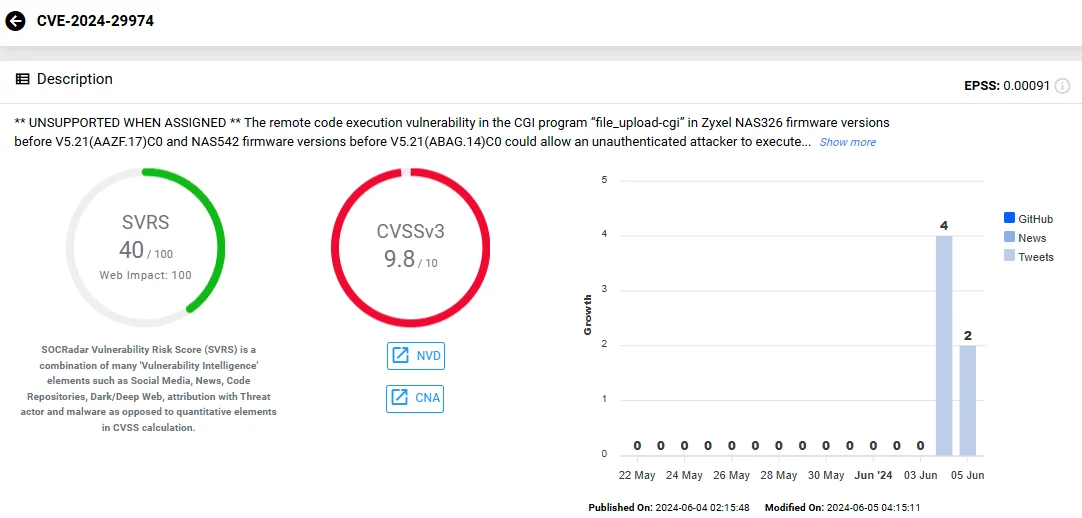
The vulnerability card of CVE-2024-29974 (SOCRadar Vulnerability Intelligence)
While patches have been released for these critical severity vulnerabilities, two other vulnerabilities, less severe and requiring local authentication for exploitation, remain unpatched. These vulnerabilities are identified as CVE-2024-29975 (CVSS 6.7) and CVE-2024-29976 (CVSS 6.5). Both CVEs represent improper privilege management vulnerabilities.
- CVE-2024-29975 (CVSS 6.7): The vulnerability, which resides in the SUID executable binary, could allow an authenticated local attacker with administrative privileges to execute system commands as the root user.
- CVE-2024-29976 (CVSS 6.5): Due to the vulnerability, it is possible for an authenticated attacker to access a logged-in administrator’s session information, including cookies, using the ‘show_allsessions’ command.
For more information about the latest Zyxel NAS vulnerabilities, refer to the official advisory.
Extended Support and Patch Availability for EoL Devices
Zyxel has issued patches for critical vulnerabilities in the NAS326 and NAS542 models, even though these products reached End-of-Life (EoL) in December 2023.
It is not very common for companies to extend support for devices that have reached the end of their life and support cycle. Users of such products are typically advised to upgrade to a supported version or, in some cases, provided with workarounds.
The company, prioritizing security, extended support to address the severe threats posed by the latest critical vulnerabilities affecting its NAS devices. By doing so, Zyxel ensures that customers using legacy devices can protect their networks effectively.
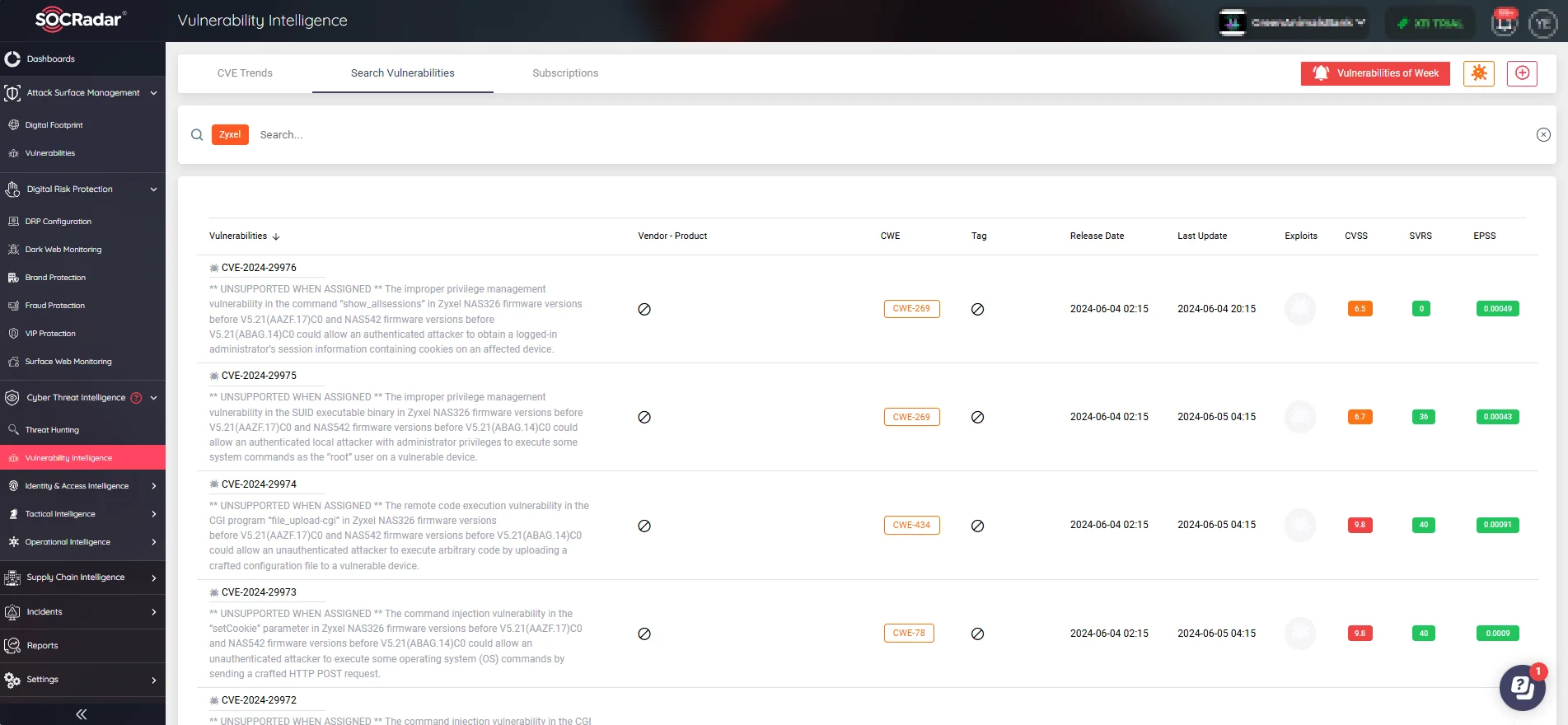
Search Vendor/Product names on SOCRadar’s Vulnerability Intelligence to see related vulnerabilities, as well as their detailed information, updates, and exploit alerts.
Which Zyxel NAS Devices Are Vulnerable?
The security vulnerabilities identified in Zyxel affect specific firmware versions of the NAS326 and NAS542 storage devices. Users of these models should be aware of the firmware versions involved and the updates provided to address the issues:
- For NAS326, models running firmware version V5.21(AAZF.16)C0 and earlier are vulnerable to the critical security issues discussed. Zyxel has released an updated firmware version, V5.21(AAZF.17)C0, to resolve these vulnerabilities.
- For NAS542, firmware versions up to V5.21(ABAG.13)C0 are impacted. The necessary patch has been issued in firmware version V5.21(ABAG.14)C0, mitigating the identified security risks.
Customers using these models are highly encouraged to update their devices to the most recent firmware versions provided by Zyxel. These updates are critical for protecting devices from unauthorized access and maintaining the integrity and safety of stored data.
How to Address the Critical Zyxel NAS Vulnerabilities?
Zyxel recommends to all users of the affected NAS models to promptly update their devices.
The identified vulnerabilities, particularly those allowing unauthorized command execution and arbitrary code execution, are considered highly severe. Such vulnerabilities are common attack vectors, and exploiting these could lead to significant security breaches.
Given the potential risks, it is essential that users install the most recent firmware updates to protect their data.
Are There Any Reports of Exploitation?
While there were no known exploits of these vulnerabilities in the wild at the time this article was published, the landscape of cyber threats is ever-evolving. Procrastination in applying these updates could open doors to attackers, putting sensitive data at risk.
Therefore, users are advised to verify their current firmware versions and ensure their devices are updated to the latest firmware releases provided by Zyxel to maintain optimal protection against potential threats.
Critical Zyxel NAS Vulnerability (CVE-2024-29973) Exploited by Mirai-like Botnet
Shadowserver recently reported observing RCE exploitation attempts targeting the critical vulnerability in Zyxel NAS devices, CVE-2024-29973.
In a post on the social platform X, Shadowserver cited that these exploitations are being attempted by a Mirai-like botnet.
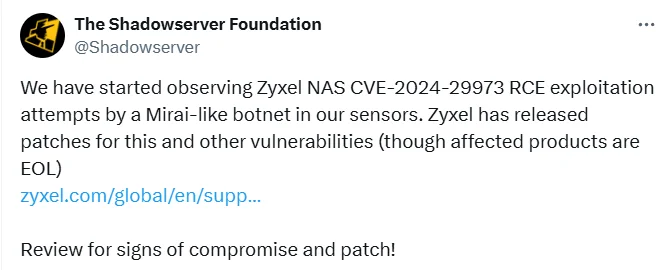
Tweet by Shadowserver (X)
Mirai is an infamous malware family that has contributed to many variants used to create massive botnets. Threat actors can utilize these botnets to target online services and websites, causing DDoS attacks.
A search for NAS542 and NAS326 devices on ZoomEye reveals nearly 43,000 exposed devices, indicating the number of potential targets.
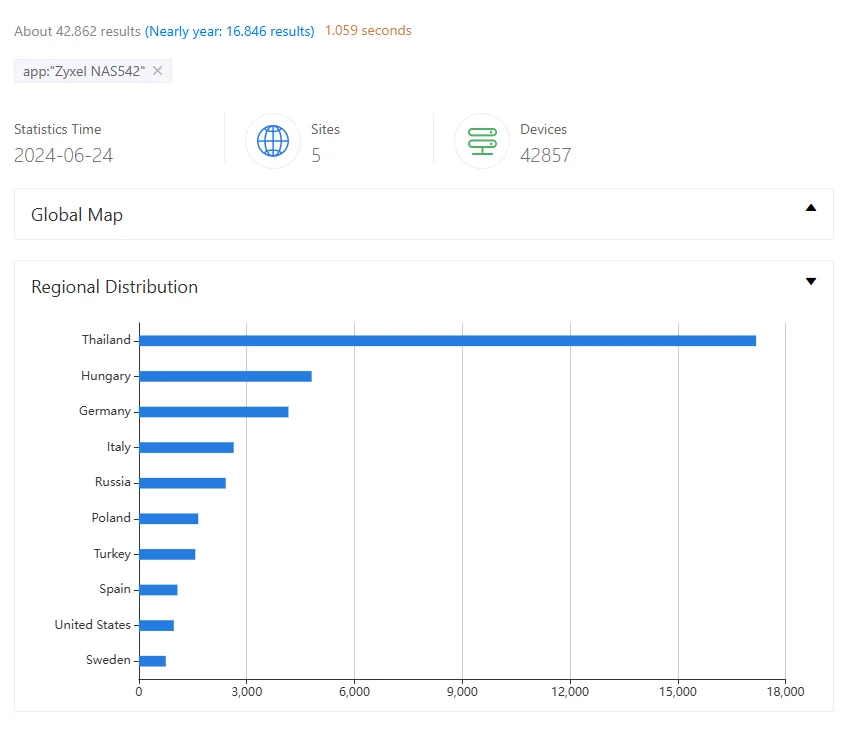
ZoomEye search results for Zyxel NAS devices
It is urgently advised to update Zyxel NAS devices to evade exploitation. Visit Zyxel’s advisory to see available updates.
Maximize Security with SOCRadar’s Intelligence and Monitoring Features
SOCRadar offers two critical services to enhance your vulnerability management strategy: the Vulnerability Intelligence feature and the Attack Surface Management (ASM) module.
The Vulnerability Intelligence feature provides an in-depth view of identified security vulnerabilities. It delivers real-time alerts and comprehensive insights into emerging threats, helping organizations stay ahead of potential breaches by monitoring new exploits and their developments across various platforms.
The Vulnerability Intelligence page offers continuous updates about emerging CVEs and hacker trends
The Attack Surface Management (ASM) module complements this by offering continuous surveillance of your digital assets. It identifies and highlights security gaps, providing actionable insights within alarms to mitigate risks effectively.
SOCRadar’s ASM module, Company Vulnerabilities page
Together, these tools empower businesses to proactively manage and respond to threats, ensuring protection against exploitation threats.

































