3AM Ransomware: A Modern Threat with a Vintage Twist
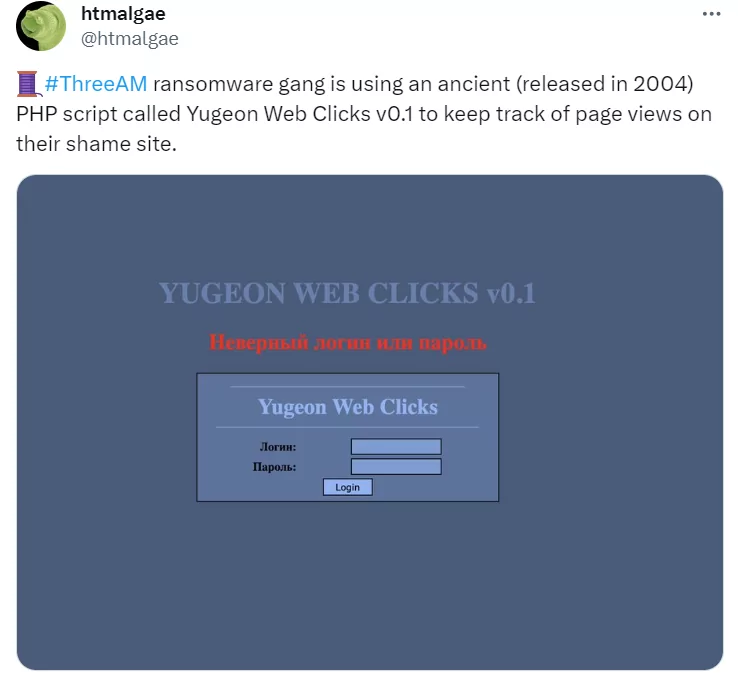
The 3AM ransomware group has recently been spotlighted for its cybercriminal activities. However, why it is the topic of the day is their choice of technology. A recent tweet by a security researcher highlighted that the 3AM ransomware gang is using an ancient PHP script, Yugeon Web Clicks v0.1, released way back in 2004, to monitor page views on their website. This choice of outdated technology raises several questions about the group’s modus operandi and the reasons behind such a decision.
Understanding 3AM Ransomware
Researchers have recently identified a new strain of ransomware called 3AM. This ransomware was notably used as a substitute for LockBit ransomware in a failed attack. Ransomware affiliates typically have various tools at their disposal, and this incident showcases their adaptability in switching between different ransomware strains to ensure the success of their attacks. In this particular case, after the initial attempt with LockBit was thwarted, the attackers resorted to using 3AM.
3AM ransomware is written in Rust and operates as a 64-bit executable. It has the capability to execute multiple commands that can halt applications, obstruct backup processes, and disable security software. The ransomware explicitly targets files that meet predefined criteria and appends the extension “.threeamtime” to the filenames of the compromised files. It also attempts to erase Volume Shadow (VSS) copies.
Why Use Outdated Technology?
The use of the Yugeon Web Clicks script from 2004 is perplexing. One might wonder why an emerging ransomware group would opt for such outdated technology. Here are some potential reasons:
- Obscurity: Older scripts and technologies might not be on the radar of modern security tools, making them less likely to be detected.
- Simplicity: The older script might offer straightforward functionality without the complexities of modern scripts, making it easier to deploy and manage.
- Overconfidence: The group might be confident in their ability and might not see the need to invest in more advanced technology, specifically for their website. It may seem unnecessary.
However, this choice also exposes the group to risks. Using outdated technology with known vulnerabilities can make their operations susceptible to external attacks, countermeasures, or even sabotage by other threat actors.
In a different article, we delved into a study on the 8Base ransomware‘s website, which appeared to have multiple vulnerabilities and issues. We’ve closely monitored leak websites, particularly those associated with recently emerging ransomware operators. Such observations suggest that similar entities might be responsible for these websites.
Despite the multitude of threat actors, the anonymity provided by the internet suggests that a few actual individuals might operate in similar domains under multiple identities. Instances like the deployment of 3AM when the previously mentioned LockBit strain faltered, and the recent discovery of identical websites underscore this notion. This trend is especially pronounced within the ransomware community.
Conclusion
The 3AM ransomware group’s decision to use an outdated PHP script is a testament to the unexpected nature of cybercriminals. While they employ advanced ransomware strains to target organizations, their backend choices might be driven by a mix of strategy, convenience, and overconfidence. Organizations must be vigilant and adopt a comprehensive security posture, considering that threats can come from cutting-edge and outdated technologies.
SOCRadar provides advanced threat actor tracking, allowing organizations to proactively monitor and understand the tactics of threat actors and APT groups. Using automated data collection and AI-driven analysis across various web layers, SOCRadar alerts users about APT activities, enhancing their ability to detect and counteract malicious actions. The platform’s alignment with the MITRE ATT&CK framework further ensures up-to-date threat intelligence.