
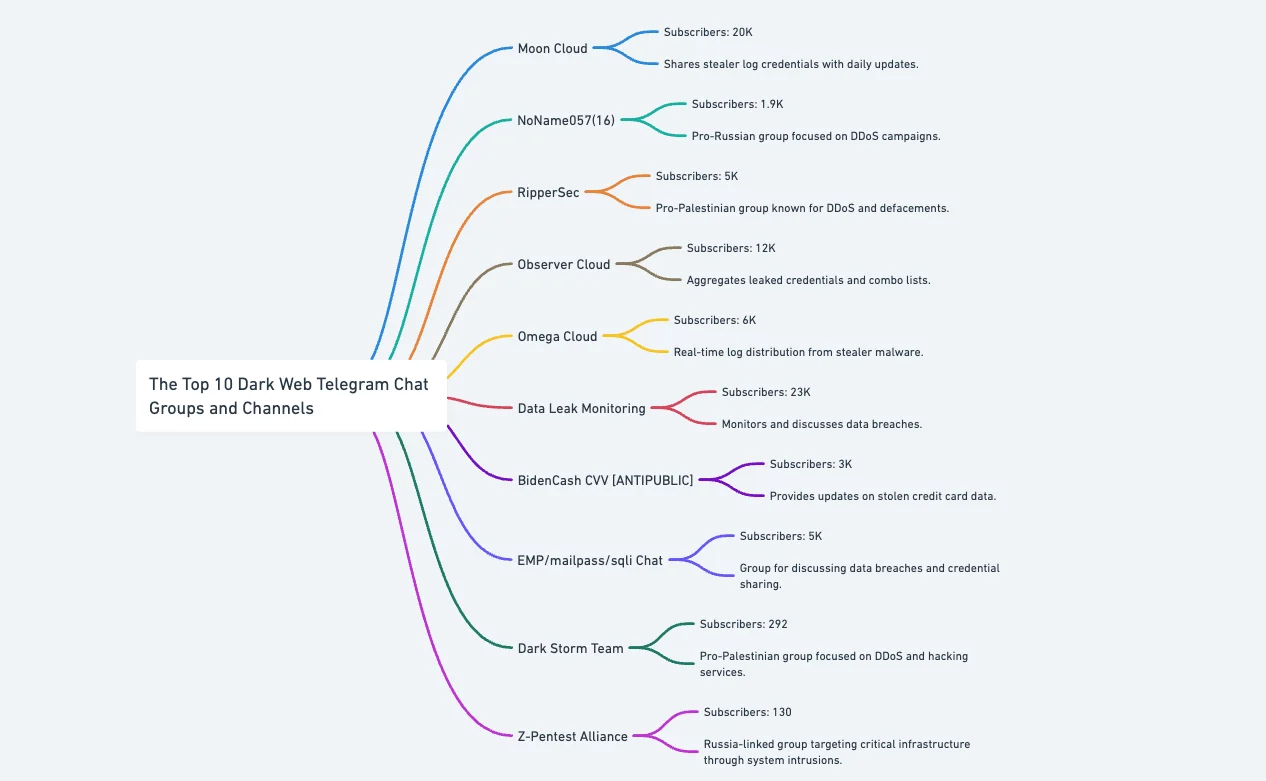
The Top 10 Dark Web Telegram Chat Groups and Channels
Since the WhatsApp privacy policy controversy in January 2021, Telegram rapidly gained traction as a privacy-focused alternative, attracting users seeking secure communication channels. However, its growing popularity also caught the attention of threat actors, who recognized its potential as a dark web-adjacent platform for facilitating cybercrime operations. The combination of encrypted messaging, large group capacities, and anonymity made Telegram an attractive hub for threat intelligence activity, underground marketplaces, and illicit coordination efforts.
The Top 10 Dark Web Telegram Chat Groups and Channels Overview
Over time, numerous malicious groups have established Telegram-based cybercrime networks, leveraging the platform to distribute stolen data, organize hacking campaigns, and conduct dark web operations. The absence of strict content moderation previously allowed hacktivist collectives, cybercriminal groups, and ransomware affiliates to thrive, using Telegram as an extension of the dark web ecosystem. Despite recent policy changes and enforcement efforts, the platform remains a critical part of the dark web monitoring landscape, where cybercriminals continue to engage in data leaks, DDoS-for-hire services, and other illicit activities.
The Changing Landscape of Cybercrime on Telegram
While Telegram was once a safe haven for illicit activity, recent policy changes have forced many threat actors to reconsider their presence on the platform. In September 2024, Telegram introduced AI-based content moderation, making it more difficult for cybercriminals to share and access illegal materials. Many hacktivist and cybercriminal groups have since started migrating to alternative platforms, such as Signal, Discord, and decentralized messaging networks.
For a broader analysis on how Telegram’s policies are reshaping the cybercrime ecosystem, check out our blog post: The Exodus Began: Alternatives for Telegram.
Despite these changes, many cybercrime-related Telegram channels remain active and influential.
What Happens in Telegram Channels?
Telegram’s large group capacities, encryption features, and anonymous user capabilities continue to make it an attractive tool for cybercriminals. Many Telegram channels operate in ways that mirror dark web forums, facilitating the exchange of stolen data, hacking tools, and cybercrime-related services. Within these groups, threat actors engage in a variety of activities, including:
- Sharing and selling stolen data, including credentials, credit card information, and corporate databases
- Offering hacking tools, malware, and ransomware services
- Coordinating DDoS attacks and hacktivist campaigns, often targeting governments, corporations, and financial institutions
- Discussing cybersecurity vulnerabilities and identifying potential targets
- Hosting private groups for vetted members to exchange sensitive data and cybercrime services
- Using Telegram bots to automate malware distribution and credential theft
- Providing hacking services for hire, including website defacements, data breaches, and system intrusions
While Telegram remains a critical hub for cybercriminal activities, it is just one part of the larger dark web ecosystem where threat actors exchange stolen data, hacking tools, and illicit services. Organizations must have real-time visibility into these underground networks to prevent data breaches, financial fraud, and cyberattacks.
SOCRadar’s Dark Web Monitoring module continuously scans Telegram, dark web forums, and cybercriminal marketplaces, detecting leaked credentials, compromised corporate data, and emerging cyber threats. By providing actionable intelligence, it enables organizations to respond swiftly to potential security incidents, minimizing risks before they escalate
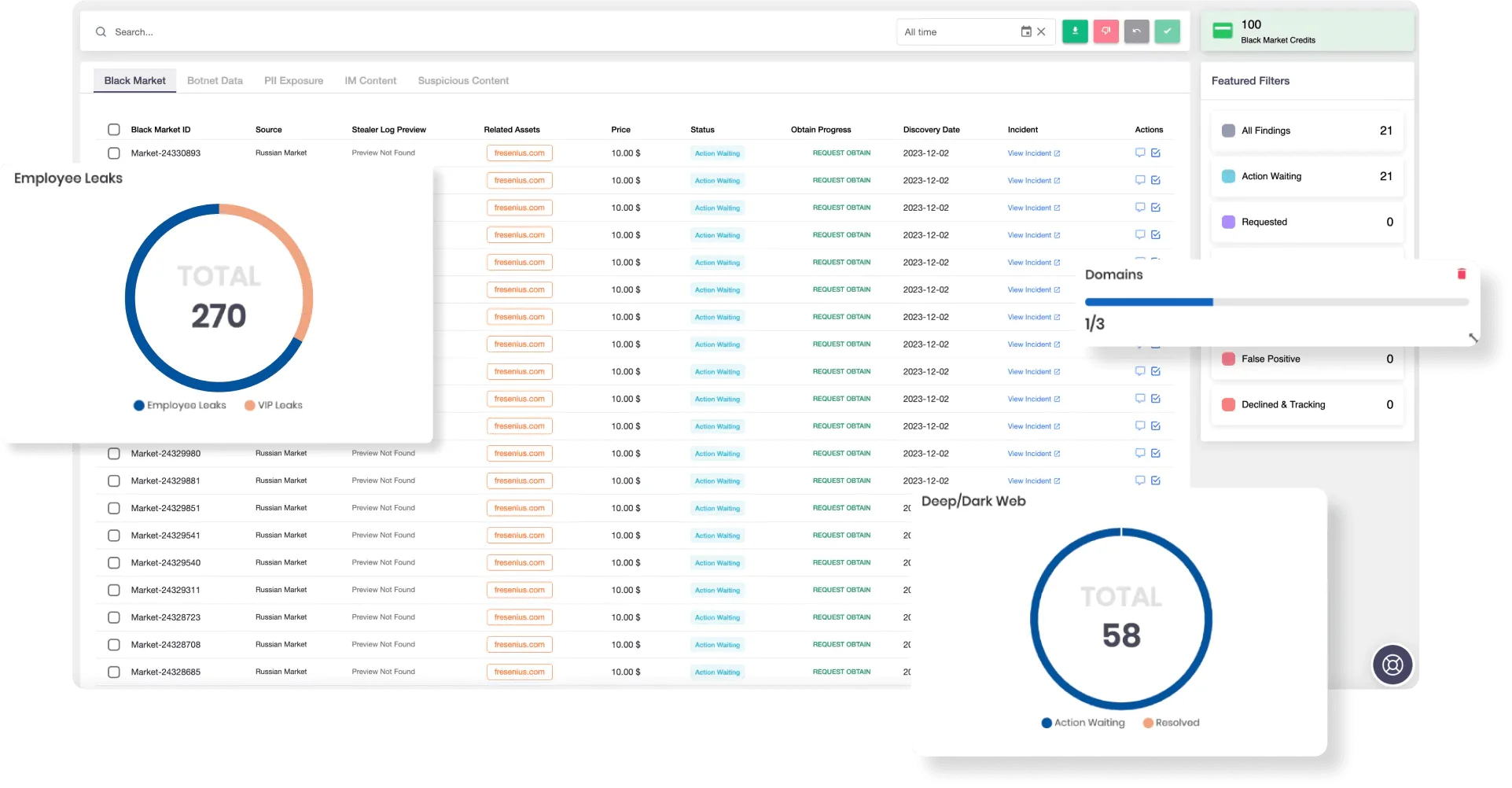
SOCRadar Dark Web Monitoring
Below are ten notable Telegram channels that play a significant role in dark web operations and underground cyber activities.
1. Moon Cloud

Telegram channel of Moon Cloud
A Telegram channel specializing in the distribution of credentials obtained from stealer logs. With 20,000 members, Moon Cloud shares a wide range of compromised data, including URLs, email addresses, IP addresses, passwords, and usernames.
According to its bio, “Moon Cloud is the largest, most versatile cloud in Telegram. All logs from other channels are posted here for convenience.”
This channel claims to offer the best logs in terms of price-to-quality ratio and provides daily updates with over 2,000 fresh logs per day. It aggregates logs from various sources, including those stolen using LummaC2 and Stealc malware.
Moon Cloud operates both free and paid services, acting as a central hub for threat actors to access and redistribute stolen credentials. Such large-scale exposure of compromised identity data highlights the increasing risks organizations face regarding account takeovers and unauthorized access attempts.
To mitigate the risks posed by exposed credentials, organizations must actively monitor and respond to identity-related threats. SOCRadar’s Identity & Access Intelligence module enables security teams to detect compromised credentials across various dark web sources, including stealer logs, data breaches, and underground Telegram channels.
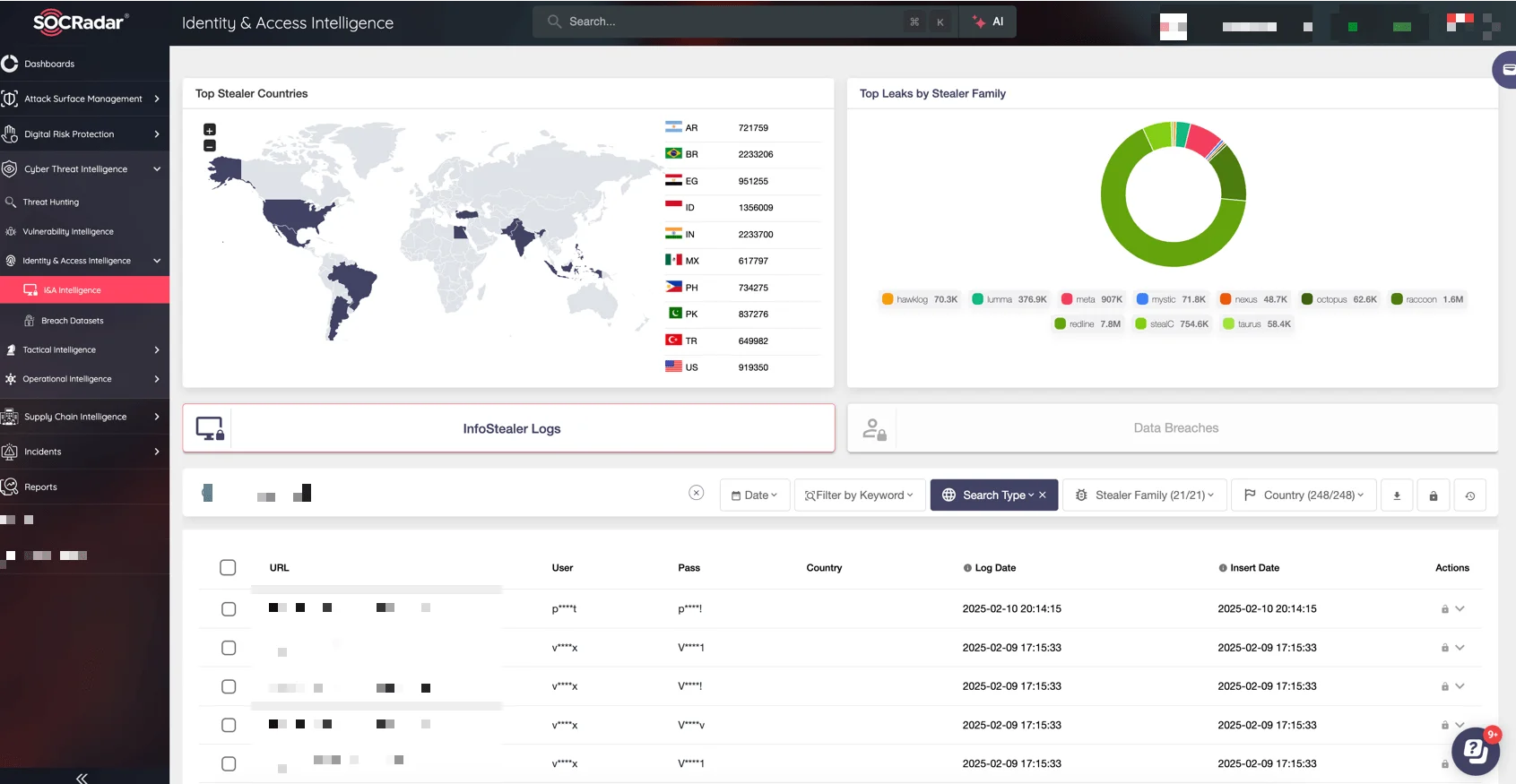
SOCRadar’s Identity & Access Intelligence module page
By leveraging this intelligence, organizations can proactively secure accounts, enforce password resets, and prevent unauthorized access attempts before they escalate into full-scale breaches.
2. NoName057(16)
Telegram channel of NoName057(16)
A pro-Russian hacktivist group that emerged in March 2022 amid the Russia-Ukraine war. Known for its DDoS campaigns, NoName057(16) primarily targets Ukraine, NATO countries, and Ukraine’s allies.
The group operates multiple Telegram channels, including the DDoSia Project, which recruits volunteers for cyberattacks. Participants receive cryptocurrency rewards based on their contribution, incentivizing large-scale DDoS operations.
Recently, NoName057(16)’s Telegram channel was taken down, likely due to Telegram’s updated policies. However, the group quickly re-established itself, regaining over 1,900 subscribers, despite previously having more than 30,000 members.
3. RipperSec
RipperSec’s DDoS channel
A pro-Palestinian hacktivist group from Malaysia, active on Telegram since June 2023, with 5,107 subscribers. Targeting Israel and its allies, RipperSec has also allied with pro-Russian threat actors.
While primarily recognized for its DDoS attacks, the group is also involved in website defacement campaigns and intrusions into SCADA-like systems. These operations align with its broader goal of causing disruption and amplifying its message.
One of RipperSec’s most notable contributions is MegaMedusa, a NodeJS-based Layer-7 Web DDoS tool developed by a group member. This tool enables users to launch scalable DDoS attacks with minimal technical expertise. MegaMedusa is compatible with Debian, Ubuntu, Kali Linux, Termux, and Windows, making it widely accessible.
4. Observer Cloud

Observer Cloud’s Telegram channel
Observer Cloud is a Telegram-based log aggregation channel with 12,755 subscribers, collecting and republishing logs and combo lists from various Telegram sources. Active since April 2022, it serves as a centralized hub for accessing leaked credentials.
In addition to its main log-sharing function, Observer Cloud provides custom-built programs, a scam list, and chat groups for discussions and transactions related to logs. The community continues to expand, aiming to strengthen its presence in the underground cyber ecosystem.
The channel states that all shared content is sourced from open internet platforms and intended for educational purposes, disclaiming responsibility for any misuse of the published information.
Is Your Data on the Dark Web? Get a Free Dark Web Report
As cybercriminals continue to exploit dark web markets, Telegram channels, and underground forums, organizations must take a proactive approach to identifying potential risks. Many underground platforms facilitate the sale of stolen credentials, financial data, and corporate information, making it crucial for businesses to monitor whether their sensitive assets have been exposed.
SOCRadar Labs Free Dark Web Report
With SOCRadar’s Free Dark Web Report, you can instantly check if your email addresses, domain names, or company assets have been leaked on dark web forums, black markets, leak sites, or Telegram channels. This free tool provides insights into:
- Dark Web Threat Severity – Understand how exposed your organization is.
- Dark Web Mentions – Find out who is talking about your company on underground platforms.
- Employee Credentials – Detect whether your employees’ credentials have been compromised.
- Data from Infected Machines – Identify malware infections affecting your network.
- Latest Exposure – Discover the last time your sensitive data appeared in leaks.
- Data for Sale – Check if cybercriminals are selling your information on black markets.
Find out if your data is at risk! Run a free Dark Web Report today and stay ahead of cyber threats.
5. Omega Cloud
Omega Cloud’s Telegram Channel
A Telegram-based log distribution platform with 6,200+ subscribers, providing both free and paid services. Omega Cloud facilitates the dissemination of real-time logs obtained from stealer malware, including credentials sourced from platforms such as YouTube and Google Ads, with a regional focus on Europe, the United States, Canada, and Brazil.
The platform offers Live Traffic, delivering logs in real time, and Private Cloud, which provides up to 5,000 logs daily, amounting to 120,000 logs per month. Additionally, Omega Cloud maintains a database exceeding 2 billion records, accessible through a subscription-based model.
6. Data Leak Monitoring
Data Leak Monitor Telegram Channel
A Telegram channel focused on tracking data leaks and cybercrime-related threats, particularly those originating from ransomware groups and underground sources. With 23,400+ subscribers, the group shares posts from various cybercriminal entities, providing insights into ongoing breaches and leaked data.
Although it monitors hacker forums, its coverage remains limited, as it does not track some of the key platforms listed in our Top 10 Dark Web Hacker Forums.
7. BidenCash CVV [ANTIPUBLIC]

Telegram channel of BidenCash
BidenCash, a dark web market, operates an automated monitoring system that scans Telegram, Discord, and hacker forums for stolen card data. To showcase this system, the marketplace runs a dedicated Telegram channel, 𝐁𝐢𝐝𝐞𝐧𝐂𝐚𝐬𝐡 𝐂𝐕𝐕 [𝐀𝐍𝐓𝐈𝐏𝐔𝐁𝐋𝐈𝐂].
This channel provides real-time updates on detected credit card data, with some posts visibly displaying card numbers and other financial details. BidenCash claims to impose fines or bans on suppliers whose listings are repeatedly found in public sources.
The presence of such a channel highlights how stolen financial data circulates within dark web markets, making Telegram an essential tool for cybercriminal activities.
8. EMP/mailpass/sqli Chat

EMP/mailpass/sqli Chat Telegram group
Established in April 2019 as a Russian-language group, EMP/mailpass/sqli Chat has since expanded into a global cybercrime discussion channel. With 5,695 members, the group remains active, serving as a hub for discussions on data breaches, compromised credentials, and underground trading.
Unlike more specialized cybercrime groups, EMP/mailpass/sqli Chat covers a broad range of topics, including stolen account sales, financial fraud, SQL injection techniques, and malware deployment. Members frequently share logs, stealer data, and access credentials for various platforms, ranging from streaming services and social media to financial accounts and VPN services.
The group also facilitates connections between buyers and sellers, with some members offering daily-updated data sources and private datasets for a fee. Over time, EMP/mailpass/sqli Chat has established itself as a long-running discussion channel where cybercriminals exchange knowledge, trade illicit data, and promote underground services.
9. Dark Storm Team
Dark Storm Team’s Telegram Channel
Dark Storm Team is a hacktivist threat group known for its pro-Palestinian cyber activities and past collaborations with groups such as Anonymous Sudan. The group has carried out cyberattacks against Denmark, Egypt, France, Israel, the UAE, and the United States, frequently working alongside other threat actors.
Primarily focused on DDoS attacks, Dark Storm Team follows an opportunistic targeting strategy across various sectors. In addition to its cyber operations, the group also promotes hacking services for hire through its Telegram channel, offering DDoS attacks on protected websites and database dumps from organizations such as banks and airports.
All transactions are conducted through cryptocurrency payments, with coordination handled via Telegram contacts. Although its Telegram channel was previously taken down due to policy changes, the group has successfully reestablished its presence and continues its operations.
10. Z-Pentest Alliance
Telegram channel of Z-Pentest Alliance
Z-Pentest Alliance is a Russia-linked threat group known for targeting critical infrastructure, including oil and gas facilities, water treatment plants, and industrial control systems. Active since October 2024, the group primarily focuses on compromising operational technology (OT) environments through direct system intrusions rather than DDoS attacks.
Z-Pentest has gained visibility through its collaborations with the now-defunct Cyber Army of Russia, formerly one of the most prominent pro-Russian threat groups, and NoName057(16), a well-known hacktivist collective. Unlike its counterparts, which predominantly rely on DDoS campaigns, Z-Pentest distinguishes itself by infiltrating industrial control systems and interacting with critical process automation tools.
Following Telegram’s policy changes, the group’s original channel was taken down. In response, threat actors established a new channel under the same name to maintain their operations.





































