
What are the Different Types of Attacks in Cybersecurity?
A cyber attack is a sort of attack that uses numerous tactics to target computer systems, infrastructures, networks, or personal computer devices. Cyber attacks come in many flavors, each capable of attacking a specific computer system for various goals.
If you’re familiar with how the internet works, you’re probably aware that several risks are associated with using it. Apart from your data being at risk, inadequate security might expose you to various threats. Indeed, it is one of the world’s most pernicious threats today, wreaking havoc on large and small organizations.
Given the rising cyber security threat to organizations, it is critical to educate oneself. Thus, this post will educate you about cyber security hazards and risks, describe the many cyber security threats, and explore measures to defend yourself. This article will discuss the many types of cyber-attacks that are currently known.
Top 10 Common Types of Attacks in Cybersecurity
1- Phishing
Phishing is a technique in which an attacker dupes an unwary victim into divulging sensitive information such as passwords, credit card numbers, etc. A notification addressing One-Time Passwords is an example of this (OTP). A hacker will send a clickable link to which the user may submit their OTPs via phishing. After clicking the link, the hacker gains access to the user’s personal information.
Due to its effectiveness and simplicity of execution, phishing is a common type of cyber attack.
Be proactive against phishing threats and get contextual data on potential attacks with SOCRadar.
2- Ransomware
Ransomware is a file encryption programming software that uses a robust encryption algorithm to corrupt data on a target framework.
It is a type of malware distributed to extort money from targets and is one of the most prevalent and well-known forms of cyberattack.
Assailant uses malware as an infection to get access to the target PC’s hard drive. It then encrypts data and renders the client’s computer/information inoperable until the assailant receives the payback installment required by the assailant. It is usually impossible to decipher the content of a record without the assistance of another person.
WannaCry and Maze ransomware are ongoing examples of how malware can wreak havoc, compelling several businesses to pay bitcoins and cash to retrieve their compromised equipment and data.
Click here and learn how to detect ransomware attacks with SOCRadar.
3- Denial of Service (DoS) or Distributed Denial of Service (DDoS) Attacks
Two frequent cyber security threats are Denial of Service (DoS) and Distributed Denial of Service (DDoS).
DoS attacks frequently include overwhelming your computer or network system with requests, resulting in traffic. On the other hand, a DDoS assault is similarly vast, except it often originates from a computer network.
The entire operation of a network system, whether DoS or DDoS or the mechanism that provides the “handshake,” is affected by many requests sent by cyber attackers. Some hackers even go so far as to incorporate other strategies, such as launching a Botnet, which may infect the network system with a virus or malware, thus taking control of the machine. The bad aspect of botnets (or zombie systems) is that the hacker’s location cannot be determined.
4- Cryptocurrency Hijacking
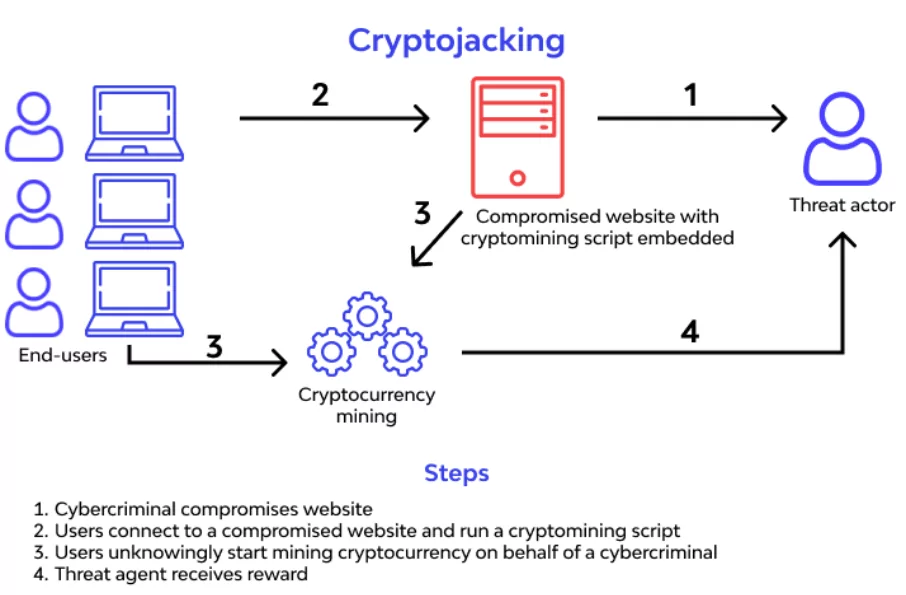
As digital money and mining gain popularity, so do cybercriminals. They’ve discovered an evil benefit in cryptocurrency mining, which entails complicated computation to mine virtual currencies such as Bitcoin, Ethereum, Monero, and Litecoin.
Hackers discreetly have two primary methods for mining cryptocurrency on a victim’s PC. One strategy is to dupe people into installing crypto mining software on their PCs. This is accomplished by using phishing-like tactics: Victims get an email that appears to be official and invites them to click on a link. The link executes code that installs a cryptocurrency mining script on the machine. The script is then performed in the background while the victim works.
The other way is to inject script into a website or advertisement distributed across several websites. Once victims visit a website or an infected ad is displayed in their browsers, the script is executed automatically. No code is kept on the systems of the victims.
Regardless of the approach utilized, the malware executes complicated mathematical problems on victims’ computers and sends the results to a hacker-controlled server.
Specific crypto mining programs have worming capabilities, which enable them to infect other network devices and servers. Additionally, locating and removing the crypto jacked is more challenging; keeping persistence on the network is in the cryptojacker’s financial interest.
5- Zero-day exploit
When cybercriminals become aware of a vulnerability in a widely used software program, they target consumers and businesses that utilize the software to exploit it until a patch becomes available. This situation is referred to as a “zero-day exploit.”
6- SQL Injection
This form of cyber attack is directed at particular SQL databases. These databases make use of SQL commands to retrieve data. If permissions are not correctly specified, a hacker can manipulate SQL queries to alter or delete data.
7- Drive-By Attacks
Cybercriminals like to distribute harmful software via drive-by assaults. A drive-by attack is a technique in which hackers inject a malicious script into an unsecured website’s PHP or HTTP code.
When a user visits a website, attackers often build a malicious script to install malware directly on the victim’s machine. Additionally, the script may reroute a user to another website controlled by the hacker.
Drive-by assaults are common because cyber attackers can attack anybody who visits a malware-infected website. In contrast to most cyber-attacks, drive-by attackers do not require the victim to do anything other than click on the malicious website. The assault does not rely on a victim opening a malicious email attachment or downloading a malicious file to infect them. Drive-by download attacks use flaws in the host machine’s operating system, web browser, or an installed application.
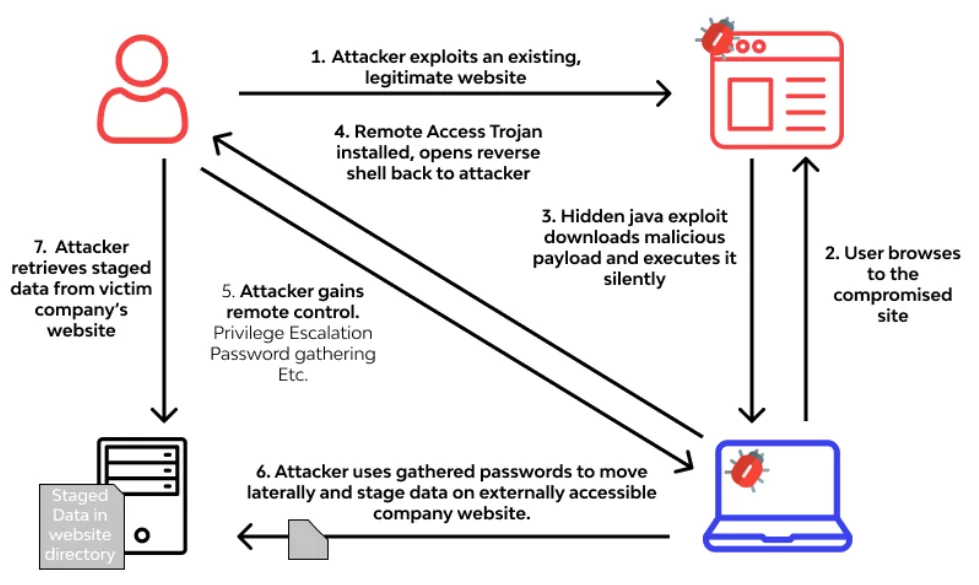
8- Rootkits
Rootkits are embedded in legal software, allowing them to obtain remote control and administrative access to a machine. The attacker exploits the rootkit to steal passwords, keys, and credentials and get sensitive data.
Because rootkits conceal themselves within legitimate software, once you grant the program permission to modify your operating system, the rootkit installs itself in the system (host, computer, server, etc.). It remains dormant until the attacker activates it. It is triggered via a persistence mechanism. Rootkits are frequently transmitted via email attachments and unsecured website downloads.
9- Man-in-the-Middle (MitM) Attacks
MitM occurs when an attacker intercepts and inserts themself into a two-party transaction. Cyber intruders can then steal and modify data by interfering with communication.
Man-in-the-Middle (MitM) Attacks typically take advantage of security flaws in a network, such as an unprotected public WiFi network, to install themselves between a visitor’s device and the network. The disadvantage of this type of attack is that it is tough to detect, as the victim believes the data is being sent to a valid location. Phishing and malware assaults are frequently used to launch a MitM attack.
10- Internet of Things (IoT) Attacks
While internet connection across nearly every possible gadget provides users with convenience and simplicity, it also enables an increasing — almost infinite — number of entry points for attackers to exploit and cause devastation. Due to the linked nature of things, attackers can compromise an entry point and use it as a gateway to target other devices on the network.
IoT attacks are gaining popularity due to the fast proliferation of IoT devices and the (often) poor attention placed on embedded security in these devices and their operating systems. In one IoT assault, a hacker got access to a Vegas casino using an internet-connected thermometer located within one of the casino’s fishtanks.
How To Protect Against Cyber Attacks with SOCRadar
Cyberattacks are becoming increasingly complicated and varied, with a distinct form of assault being used for each evil objective. While cybersecurity protection techniques vary according to the attack type, solid security practices, and basic IT hygiene effectively neutralize these assaults.
Along with good cybersecurity practices, your organization should practice secure coding and keep systems and security software up to date. Your organization should leverage firewalls and threat management tools and solutions, install antivirus software between systems, and control access and user privileges. In addition, you can proactively monitor compromised systems through the SOCRadar Extended Threat Intelligence (XTI) solution.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































