
Does the Killnet Pose a Serious Threat to Our Industry?
Killnet is a pro-Russian hacktivist group known for its DoS and DDoS attacks on government institutions and companies in multiple countries while the Russian invasion of Ukraine in 2022. The group even declared war on multiple nations and other hacktivist groups. They’re not working together with Russia but are supporting Russia. It is believed that the group was established around March 2022 and is currently not associated with any families.
What is Killnet?
Killnet was originally the name of a subscribers-only tool that could be used to launch DDoS attacks. On January 23, 2022, the tool became available and was advertised on their Telegram channel. According to their advertisement, users could rent a 500 Gbps botnet with 15 computers from Killnet for USD 1,350 per month and instantly launch Layer 3/4 or Layer 7 DDoS attacks using Killnet. The group released Killnet version 2.0 on March 20, 2022, but attacks worldwide quickly brought the domain down. It was also blocked in Russia and Europe. Although Killnet claimed it to be that way first, they then declared they took it down voluntarily until the end of the Russia-Ukraine war.
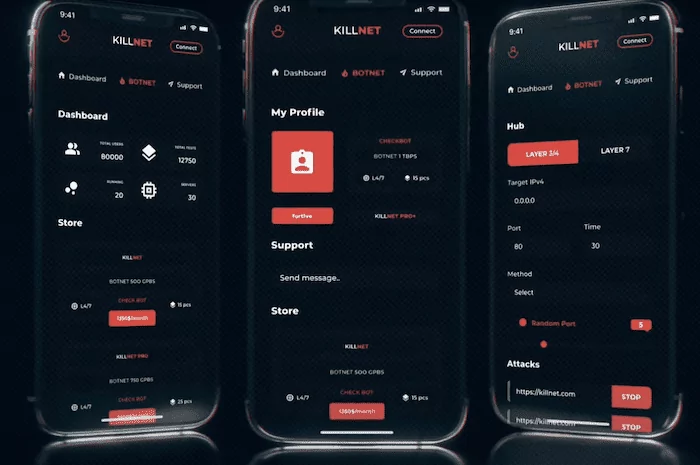
Killnet then abruptly turned into a hacktivist group. The creators of Killnet started using the tool’s name to launch DDoS attacks against nations that supported Ukraine or were against Russia. Killnet claimed that the sole purpose of its attacks was to “stop the aggression against Russia.”
Russian users’ support for Killnet encouraged the group to carry out its attacks. Killnet quickly grew to more than 100,000 subscribers on Telegram and started enlisting new members to form numerous sub-groups called “Cyber Special Forces of the Russian Federation.”
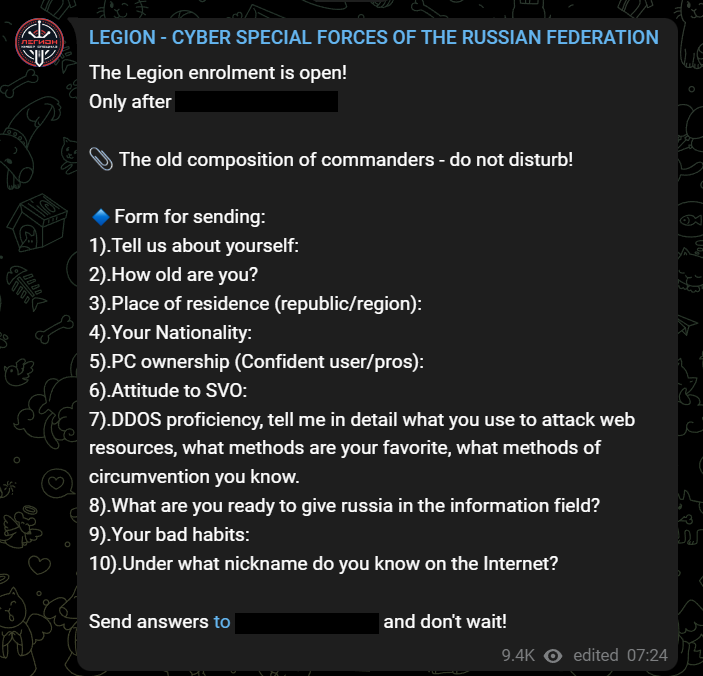
Many groups in this “Legion” follow the rules to perform targeted DDoS attacks assigned by Killnet. They use various tools, one that was noticed was “Auro DDoS.”
Techniques
Killnet attacks are mostly Layer 4 and 7 DDoS attacks, which may disrupt targets, and are not thought to be particularly sophisticated. According to CSIRT Italy, Killnet’s attacks are divided into three phases:
- Phase 1: High frequency of packs in TCP-SYN, UDP, TCP SYN / ACK, Amplification attacks along with DNS Amplification and IP Fragmentation attacks
- Phase 2: IP Fragmentation attacks followed by previous attack types, except for DNS Amplification
- Phase 3: Volumetric attacks and state exhaustion. Phase 3 lasts longer but has a lower frequency.
Killnet attacks peak at 40Gbps and lasts for more than 10 hours. Killnet uses the following techniques:
- ICMP Flood
- IP Fragmentation
- TCP SYN Floof
- TCP RST Flood
- TCP SYN / ACK
- NTP Flood
- DNS Amplification
- LDAP Connection less (CLAP)
Killnet attacks are usually announced on their Telegram channels before occurring. Romanian National Cyber Security Directorate has released a list of more than 11,000 IP addresses associated with them, so the effects of an attack can be prevented if wary.
Important Incidents Involving Killnet
Killnet officially declared cyber war against the United States, the United Kingdom, Germany, Italy, Latvia, Romania, Lithuania, Estonia, Poland, and Ukraine on May 16, 2022. Since this announcement, the group has been launching DDoS attacks against organizations operating in the targeted nations.
Most of Killnet’s attacks were directed at governments, while its squads focused on important industries like finance, transportation, law enforcement, and technology.
For example, Sakurajima and Jacky were instructed to target Germany and Poland on May 11, 2022.
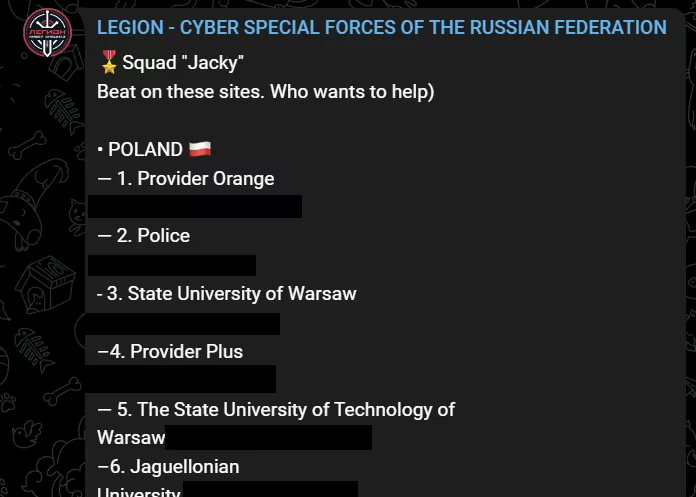
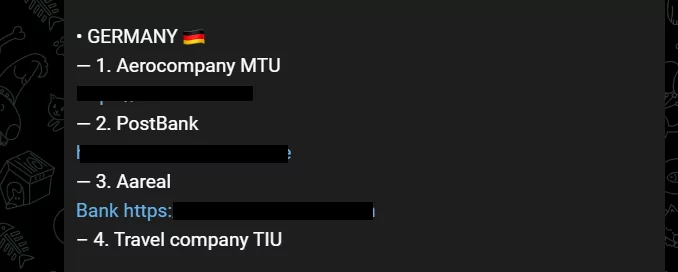
Killnet frequently posted its targets’ domains and IP addresses on its Telegram channel, inviting users to participate in attacks.
First Strike Against Ukraine
The first strike in the timeline was the shutdown of the Ukrainian branch of Vodafone (vodafone.ua) and Ukrainian news service korrespondent.net websites on March 3. The group justifies its measures as “an assault against propaganda.”
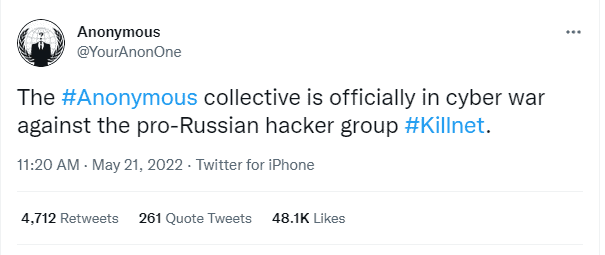
Anonymous Retaliates Them
Italy has recently become a bigger target for Killnet. This occurred due to the Italian Anonymous group targeting Killnet domains and threatening to expose information about Killnet members. The Anonymous collective also announced a cyber war against Killnet shortly after to support Anonymous Italy. They leaked a database that contained the email addresses and passwords of 146 Killnet users.
Norwegian Websites Under Cyberattack
On June 28, Killnet launched a cyberattack against NATO member Norway, focusing on several public service websites. Some websites were disrupted, but there were no signs that any sensitive data had been compromised. The DDoS attack affected multiple websites, including the public administration portal, the corporate page of an online banking identification service, and the Norwegian Labor Inspection Authority. The website of the biggest newspaper in Norway also experienced a 25-minute outage. They added an altered picture of Norwegian Foreign Minister Anniken Huitfeldt in their Telegram announcement and called her “Mrs. Error.”

Bradley Airport Website Attack
On March 29, Killnet announced a successful attack on the Bradley International Airport, a target in the United States. The primary goal of the attackers was to block any military assistance to Ukraine.
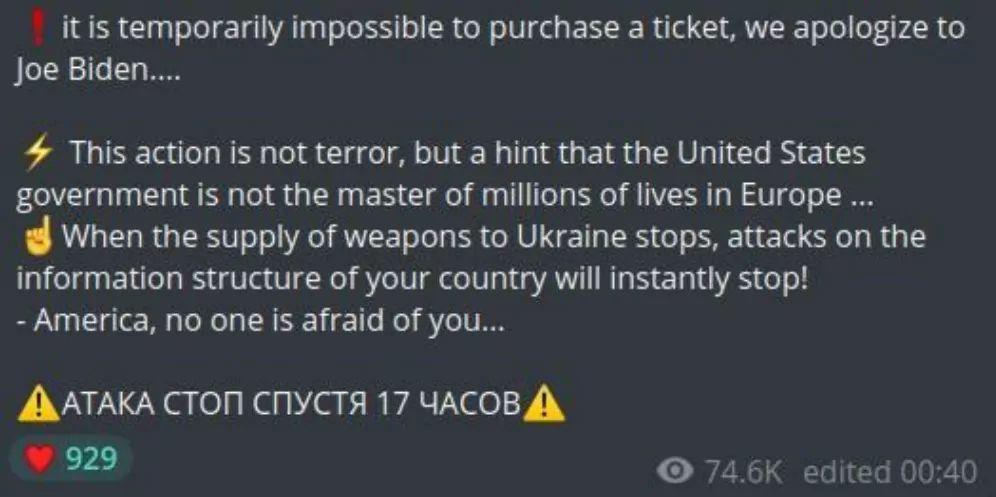
Italy Prevents Attack on Eurovision 2022
Killnet hackers are accused of having attempted to launch a DDoS attack against the Eurovision Song Contest website during Ukraine’s performance at the 2022 competition. The attempt was stopped by the Italian state police, although the group denied on their Telegram channel that it had failed.
They then launched an attack on the state police station, highlighting how they had prevented the attack on Eurovision. After the assault, they put 11 European nations, including Italy, under threat.
Allegedly Lithuania Attack
The Russian hacking group Killnet took credit for the DDOS cyberattack on Lithuania. According to them, the attack was punishment for blocking the flow of cargo to the Russian exclave of Kaliningrad.
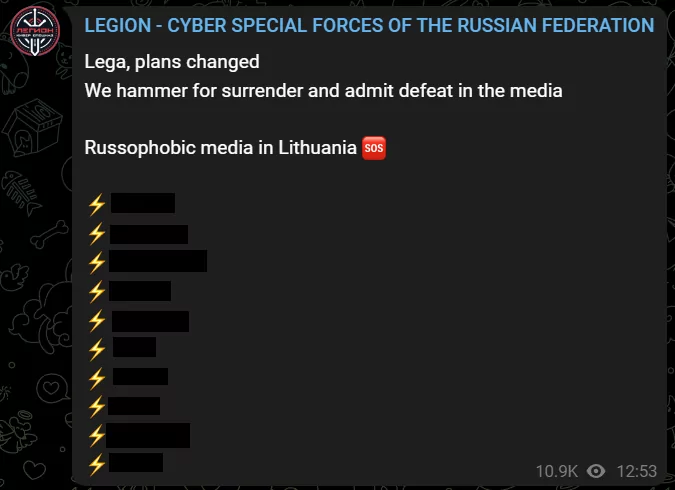
“The attack will continue until Lithuania lifts the blockade,” a Killnet group spokesperson stated. “We have demolished 1652 web resources. And that’s just so far.”
Several Cyberattacks by Killnet Target Websites in the Czech Republic
They have launched attacks against Czech railroads, local airports, and a government portal.
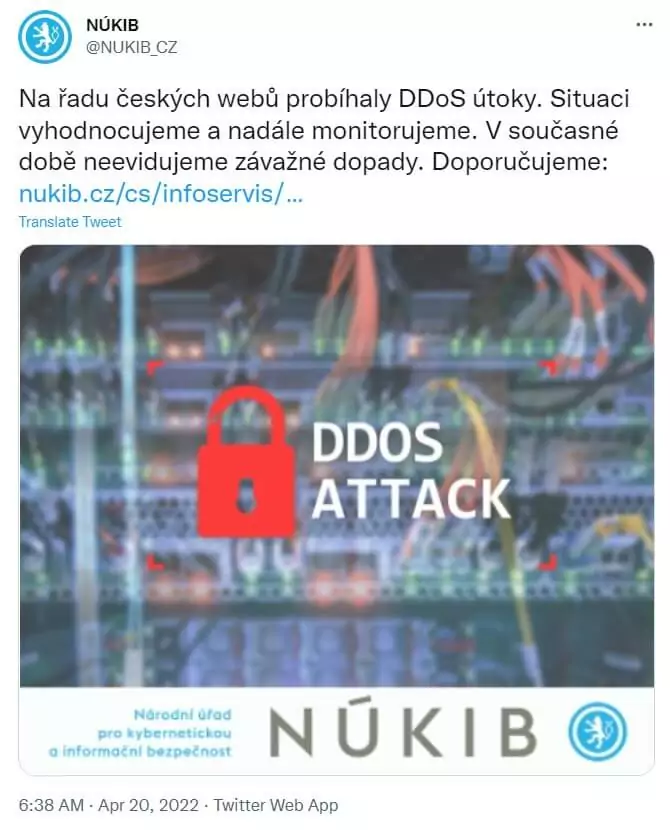
According to Interior Minister Vít Rakušan, no information or private data of residents were disclosed despite Russian hackers attacking the Internet infrastructure of the Czech state and commercial organizations today.
The website of NÚKIB (The National Office for Cyber and Information Security) was also targeted. The website may become unavailable from abroad due to the DDoS attack, it said on Twitter. NÚKIB tweeted that no significant effects had yet been felt.
According to Luká Kubát, a spokesman for Czech Railways, the Můj vlak (My train) smartphone application has been having problems. Online ticket purchases did not operate, and connections were difficult to make.
Smaller airports in the Czech Republic were also attacked. A DDoS attack was reported against the Karlovy Vary Airport.
According to Alice Undus, CEO of the Karlovy Vary Airport, “the attacks in no way affect the safety of transportation.”
They Chose Lockheed Martin as New Target
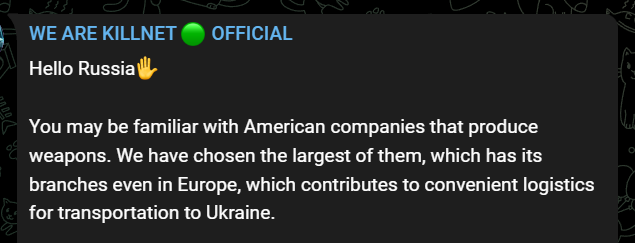
Their latest action is against the American weapon industry, and Lockheed Martin is their specific target. Killnet posted a notice on Telegram on July 21, describing it as a new attack technique.
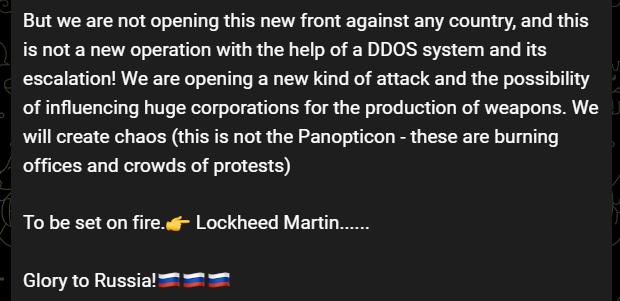
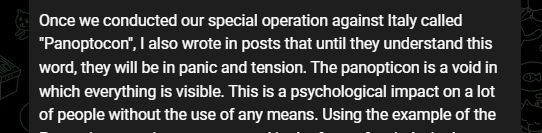
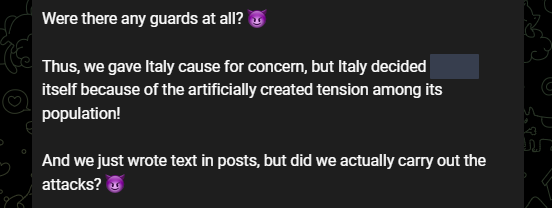
About Panopticon Operation Against Italy
Killnet also talked about the Panopticon operation in their Lockheed Martin announcement, which shows Panopticon might have actually been a bluff. It is unclear if they took action against Italy on May 30 after Panopticon threats were posted.
Organizations should do these things below to protect themselves:
- Use anti-DDoS solutions to safeguard their systems from these kinds of attacks.
- Keep an eye out for any mentions of their domains on the Killnet Telegram channels because the gang frequently announces attacks there before they happen.
Killnet IoCs
5.2.69.50
92.255.85.237
92.255.85.135
173.212.250.114
144.217.86.109
156.146.34.193
162.247.74.200
164.92.218.139
171.25.193.25
171.25.193.78
185.100.87.133
185.100.87.202
185.129.61.9
185.220.100.241
185.220.100.242
185.220.100.243
185.220.100.248
185.220.100.250
185.220.100.252
185.220.100.255
185.220.101.15
185.220.101.35
185.220.102.242
185.220.102.243
185.220.102.253
185.56.80.65
185.67.82.114
185.83.214.69
195.206.105.217
199.249.230.87
205.185.115.33
209.141.57.178
209.141.58.146
23.129.64.130
23.129.64.131
23.129.64.132
23.129.64.133
23.129.64.134
23.129.64.137
23.129.64.139
23.129.64.142
23.129.64.147
23.129.64.148
23.129.64.149
23.129.64.210
23.129.64.212
23.129.64.213
23.129.64.216
23.129.64.217
23.129.64.218
23.129.64.219
45.153.160.132
45.153.160.139
45.154.255.138
45.154.255.139
45.227.72.50
72.167.47.69
81.17.18.58
81.17.18.62
91.132.147.168



































