
SOCRadar New Threat Landscape Report: Financial Institutions are Most Targeted Sector in the UK
SOCRadar Threat Landscape Report provides U.K. organizations with an understanding of evolving cyber threats relevant to their geographical operating locations to enable security leaders to make better decisions. The intelligence provided in this report can help plan enterprise-wide security programs, make investment decisions, and define cybersecurity requirements.
Download our full UK Threat Landscape Report.
The intelligence provided in SOCRadar Threat Landscape Reports can be used to plan organization-wide security programs, make investment decisions, and define cybersecurity requirements.
For this report, SOCRadar characterizes the threat landscape by leveraging the activity of threat actors, malware campaigns, new critical vulnerabilities and exploits, data collected from open threat sharing platforms, and SOCRadar’s comprehensive data monitoring, collection, classification, and analysis capabilities.
SOCRadar’s unique perspective on understanding threat actors and their TTPs comes from combining information gathered from the SOCRadar CTIA Team’s deep/dark web threat research, HUMINT observations, cybersecurity vendor blogs, and social media trends.
What Are Our Key Findings?
- Based on 500+ deep web posts, financial institutions are the TOP targeted industry in the U.K.
- Top ransomware gangs targeting the U.K. are “LockBit, Conti, and Pysa.”
- Iranian and Chinese APT groups have recently targeted leading organizations in the military, government, high-tech, and finance verticals.
- SOCRadar has detected 37,358 phishing attacks targeting the U.K. since the beginning of 2021.
- In 2021, ProxyShell vulnerability on M.S. Exchange Servers was the most exploited vulnerability in the U.K.
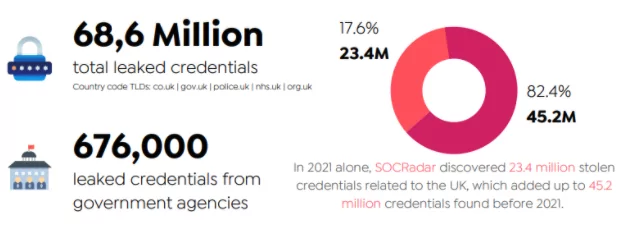
- In 2021 alone, SOCRadar discovered 23.4 million stolen credentials related to the U.K.
- DDoS attacks in 2021 impacted critical emergency services.
Dark Web Threats On The Rise for the U.K.
The dark web underground ecosystem is the number one communication channel and a global marketplace with various hacking tools and stolen databases available for purchase. When it came to the target countries, the U.K. was tied for number two globally, just behind the U.S. Most important to highlight is that over the last 12 months, the SOCRadar CTIA Team detected more than 521 posts.

Sixty-two different threat actors are targeting the UK entities. 18% of these posts were customer database sales, and 12% were unauthorized network access sales. These campaigns have exposed an extensive dataset of organizations from various verticals, including local government, finance, digital media, and healthcare.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free
What Were Major Dark Web Incidents of 2021 for the U.K.?
Unauthorized Citrix Access Sale Detected for a BritishAmerican Banking Giant: On June 26, on a dark web forum tracked by SOCRadar, a vendor attempted to sell unauthorized Citrix access allegedly for a BritishAmerican bank. While the dark web vendor did not give the name of the victim bank, it is claimed that its revenue is more than $30 billion.

Ransomware Threats in the U.K.
Ransomware attacks dominated the headlines in 2021. The top 10 ransomware gangs believed to be behind criminal activity had moved about $5.2 billion worth of bitcoin over the past three years. This year, Ireland’s Health Service Executive also faced a significant attack, leading to months of disrupted appointments.
Dive Into the Deep Web: “Dark Mirror”
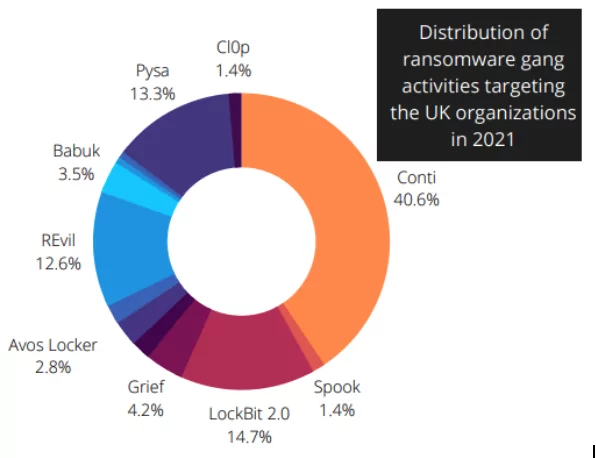
Top Ransomware Gangs Targeting the U.K.
LockBit
- Ransomware-as-a-service (RaaS) operator.
- It’s one of the best-designed lockers regarding encryption speed and overall functionality.
- Lately, the long list of victims has included Merseyrail UK, Accenture, and Bangkok Airways.
Conti
- Ransomware-as-a-service (RaaS) operator, operating out of Russia.
- The group has pulled off several high-profile attacks on the U.K. companies such as Graff Diamonds Limited.
- A playbook related to Conti was allegedly released by an affiliate upset with Conti in September 2021.
Pysa
- First observed in December 2019.
- They explicitly target higher education, K-12 schools, and seminaries in the U.S. and U.K.
- Routinely dump stolen data even after the victim company has paid the ransom.
State-Sponsored APT Activities
Organizations in the U.K. continue to be targets of advanced threats with diverse motivations. Specific APT groups from Iran and China have recently targeted leading organizations in the military, government, high-tech, and finance verticals. To reach the state goals through the collection of strategic intelligence is believed to be the primary motivation of the state-sponsored actors.
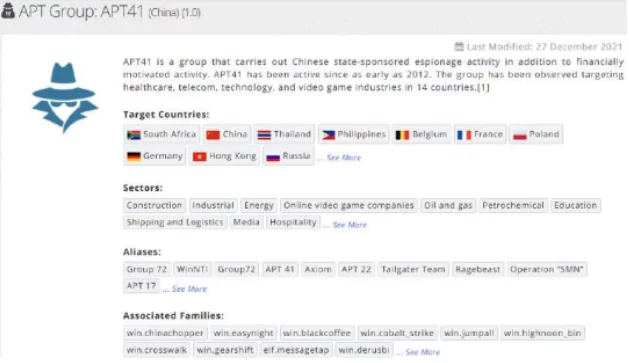
Over the last few months, the SOCRadar CTIA team has observed multiple activities reflecting these motivations by continuously collecting data across the surface, deep and dark web sources while tracking 12 APT groups that have targeted the U.K. government, military, and private sectors in the past.
Major APT Activities
The U.K.’s NCSC Blames China for the Hafnium Microsoft Incident: In March 2021, various organizations worldwide found their internal discussions cracked open by Chinese hackers – initially attributed to the Hafnium threat group.
Four undiscovered vulnerabilities in Microsoft Exchange software, which affected software released from 2012, enabled the hackers to take continual control of the corporate servers, calendars, emails, and anything else they solicited. After a detailed investigation, the U.K.’s National Cyber Security Centre (NCSC) has announced.
Iran-linked Charming Kitten (APT 35) Impersonate the U.K. Scholars: In a sophisticated campaign, Charming Kitten APT Group (aka TA453, APT35, and Phosphorus) has been found to approach individuals pretending to be British academics with the University of London’s School of Oriental and African Studies (SOAS) to obtain sensitive information.
The phishing campaign starts with detailed and lengthy chats with professors, journalists, and think tanks on Middle Eastern studies. Charming Kitten released a registration link to a website looking reliable and belonging to the University of London.
Phishing Threats on the Rise for the U.K.
Email phishing remains the top ransomware attack vector. The typical tactic is to deliver malicious macro-enabled Office documents attached to the email. Combined with business email compromise (BEC) scams and social engineering methods, the effects can increase dramatically.
SOCRadar has detected 37,358 phishing attacks targeting the U.K. since the beginning of 2021. SOCRadar CTIA team is seeing a phishing-enabled fraud trend targeting particularly fastgrowing digital industries, including e-commerce, FinTech, and cloud/SaaS.

Critical Asset Exposures & Vulnerabilities
Ransomware gangs heavily exploit these as they are exposed, but we can still observe them unpatched or exposed to any remote actors. It is highly recommended to check the technologies listed for unpatched, critical, exploited vulnerabilities.

GAIN VISIBILITY INTO HACKERS’ PERSPECTIVE: Discover External Attack Surface
Identity & Credentials Intelligence
Last year, SOCRadar detected more than one billion exposed credentials by analyzing the breach datasets shared on the deep and dark web forums, most of which are tied to plain-text passwords.
Password reuse remains a concern for security professionals. A bigger problem arises when password reuse is combined with the lack of MFA mechanisms. This makes it easier for ransomware and APT actors to continually access sensitive information, intellectual property, and confidential business data through stolen identities.
DDoS Attacks in the U.K. Threat Landscape: Risk-to-other
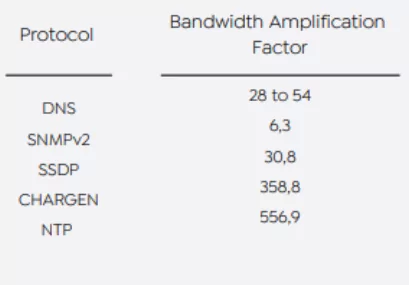
The global internet ecosystem is currently vulnerable and carrying high malicious traffic. Sophisticated threat actors take advantage of these weak points for amplifying disruptive DDoS attacks against businesses, resulting in financial losses and critical service disruptions.
UK VoIP operators (e.g., Voiphone) to the likes of police, critical emergency services, and the NHS were also victims of DDoS attacks in 2021. Based on the global risk condition dataset provided by Cyber Green Initiative, the United Kingdom can generate ~96TBit/sec DDoS traffic, ranking number ten globally.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































