
The Digital Industries Commonly Targeted by Phishing Attacks in Indonesia
Indonesia is a prime target for nation-state-sponsored actors as well as financially motivated ransomware gangs in 2021. It is precisely for this reason that SOCradar has produced an Indonesia-specific report to provide organizations with an understanding of emerging cyberthreats related to the country, to enable security leaders to make better decisions.
The intelligence provided in SOCRadar Threat Landscape Report can be used to plan organization-wide security programs, make investment decisions, and define cybersecurity requirements.
For this report, SOCRadar characterizes the threat landscape by leveraging the activity of threat actors, malware campaigns, new critical vulnerabilities and exploits, data collected from open threat sharing platforms, and SOCRadar’s comprehensive data monitoring, collection, classification, and analysis capabilities.
SOCRadar’s unique perspective on understanding threat actors and their TTPs comes from combining information gathered from the SOCRadar CTIA Team’s deep/dark web threat research, HUMINT observations, cybersecurity vendor blogs, and social media trends.
What’s Our Key Findings?
- Of the more than 60 posts seen regarding Indonesian assets in the last three months, 10% were ransomware threats, 15% were unauthorized network access sales, and more than 50% were database sharing.
- 24 APT groups have targeted leading organizations in the energy, telecommunications, high-tech, and finance industries.
- Indonesian companies and public institutions are observed to attract the attention of ransomware groups such as REvil, Conti, Avaddon, and LockBit.
- Nearly 20,000 phishing attacks targeting Indonesia have been detected since the start of 2021, a 38% increase from last year.
- More than 1 billion exposed credentials were identified by SOCRadar, most of which depend on plaintext passwords in Indonesia.
Dark Web Threats On The Rise for Indonesia
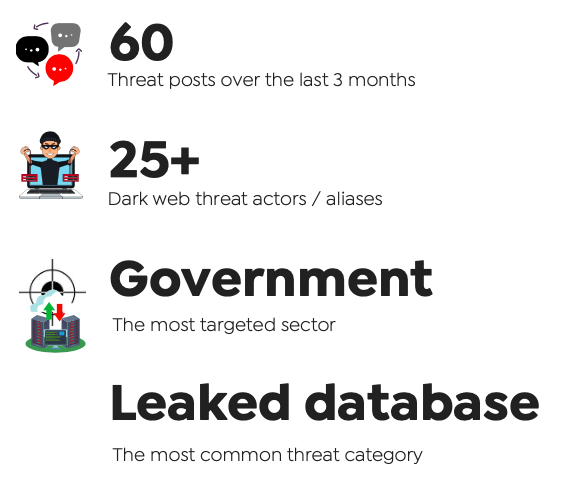
For threat actors, the dark web underground ecosystem has become a number one communication channel and a global marketplace with various hacking tools available for purchase. Dark web vendors have allegedly orchestrated mass data breaches. Over the last three months, the SOCRadar CTIA Team detected more than 60 posts related to Indonesian entities.
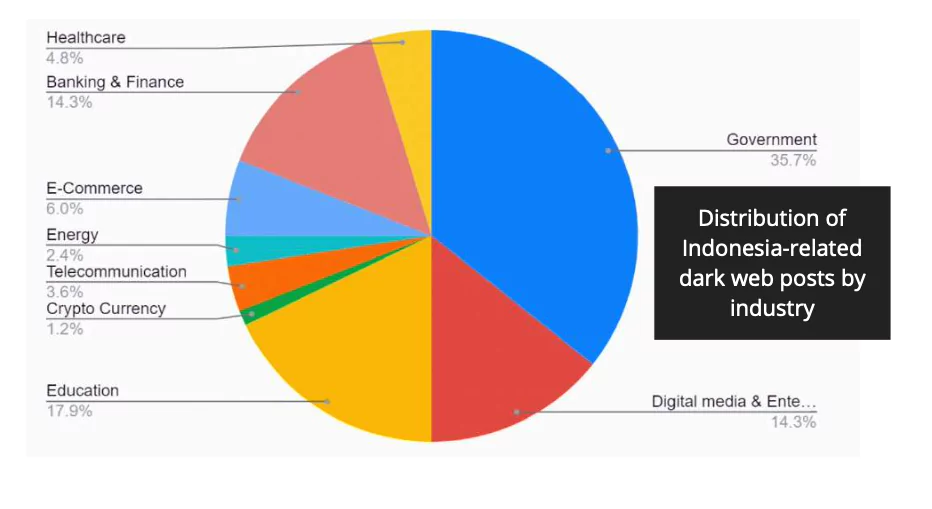
10% of these posts were ransomware threats, 15% were unauthorized network access sales, and more than 50% were database sharing. These campaigns have exposed an extensive dataset belonging to different companies from various sectors, including local government, education, law enforcement, agriculture.
Major Dark Web Incidents of 2021
- PII of Over 270 Million Indonesian Citizens Leaked: On July 1, 2021, on a dark web forum monitored by SOCRadar, a vendor attempted to sell databases allegedly including Indonesian citizens. According to the dark web post, leaked information comprises First Name, Last Name, Date of Birth, Mobile Phone Number, National Identity Numbers, and salaries for some individuals.
- Indonesia’s BRI Life Probes Data Leak of 2 Million Users: On July 28, 2021, a dark web vendor offered to sell a database assertedly belonging to an Insurance company Indonesia on a dark web forum tracked by SOCRadar. A vendor who claimed to sell a collection of 460,000 documents for seven thousand dollars implements that the database was gathered from the customer information belonging to over two million clients.
Ransomware Threats
Ransomware attacks today go beyond data hijacking. Ransomware gangs now leak victim organizations’ confidential data, which calls a Double Extortion Tactic. These cybercriminals threaten to release the victims’ data by using pressure tactics, further increasing victims’ need to protect their precious reputations.
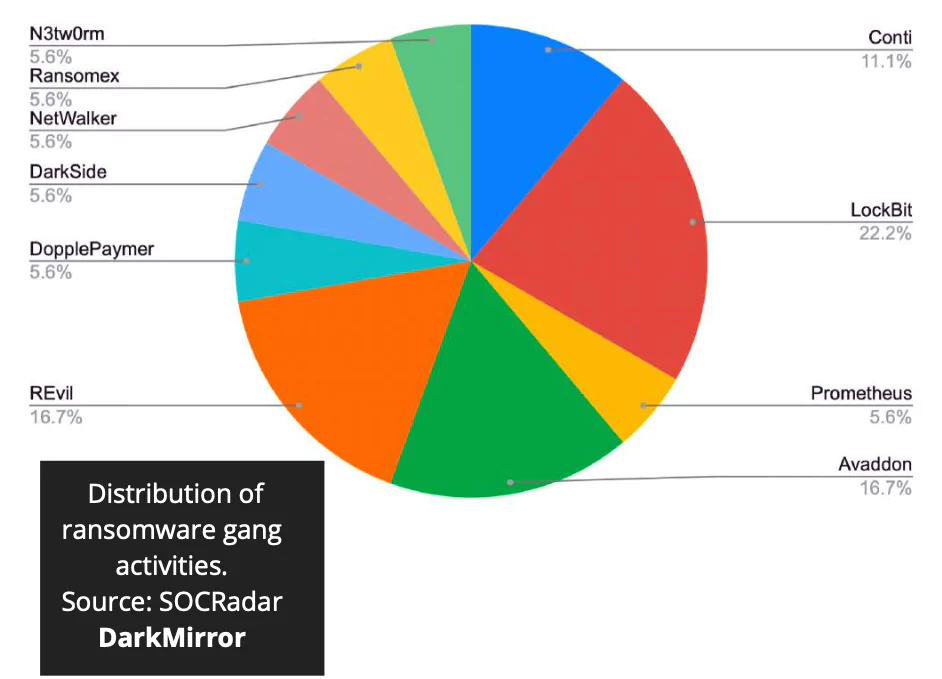
Top Ransomware Gangs Targeting Indonesia
LockBit
–Ransomware-as-a-service (RaaS) operator.
-It’s one of the best designed lockers in terms of encryption speed and overall functionality.
-The long list of victims has lately included the consultancy firm – Accenture.
REvil
-Ransomware-as-a-service (RaaS) operator, also called Sodinokibi.
-The group has pulled off several high-profile attacks on enterprises like the Apple supplier Quanta Computer Inc., meat supplier JBS, tech giant Acer and Kaseya.
-The data leak site of REvil is called Happy Blog.
Avaddon
-First observed in February 2020.
-Recent victims include the American company American Bank Systems (ABS), and more recently the insurer Group AXA.
-Avaddon is usually distributed via phishing campaigns through e-mails containing obfuscated JPEG or ZIP attachments.
State-Sponsored APT Activities
Advanced persistent threat (APT) actors are historically one of the biggest challenges for the region. Specific APT groups have targeted leading organizations in the energy, telecommunications, high-tech, and finance industries.
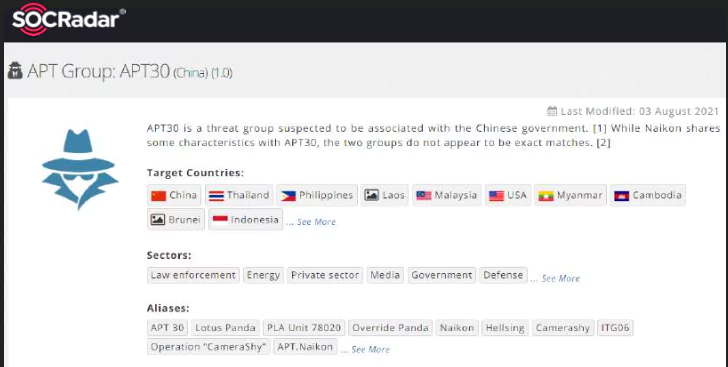
Over the last few months, the SOCRadar CTIA team has observed multiple activities reflecting these motivations by continuously collecting data from surface, deep and dark web sources while tracking 28 APT groups that have targeted Indonesia’s government, military, and private sectors.
Major APT Activities
- 4 Hackers Tied to China Charged by the US: On July 19, 2021, the United States accused China of deliberately using contract hackers. According to the indictment, China targeted organizations from Indonesia and countries such as the USA, Canada, and Germany in the campaign between 2011-2018. Further, victims from aviation, defense, education, government, health care, pharmaceutical, and maritime sectors were involved in the attacks, aligning with APT17 and APT41 – well-known China-backed hacking groups.
- Alleged Cyber Espionage Campaign Targeting BIN: On September 10th, the cybersecurity news portal, The Record, claimed that a threat actor group from China attacked computers belonging to the intelligence service of Indonesia – the Badan Intelijen Negara (BIN). However, they rejected the claim, and “our server is safe, and under control, there is no indication that suspected Chinese hackers hacked it,” said a spokesman for the agency. The representative also stated that their computers are an attractive target for threat actors, and the agency conducts routine controls and maintenance on its systems.
Phishing Threats
Email phishing remains the top ransomware attack vector. The typical tactic is to deliver malicious macro- enabled Office documents attached to the email. Combined with business email compromise (BEC) scams and social engineering methods, the effects can increase dramatically.
SOCRadar has detected almost 20,000 phishing attacks targeting Indonesia since the beginning of 2021, showing a 38% increase comparing to the last year. SOCRadar CTIA team is seeing a phishing trend targeting fast-growing digital industries, including e- commerce, FinTech, cryptocurrency exchange, and cloud/SaaS.

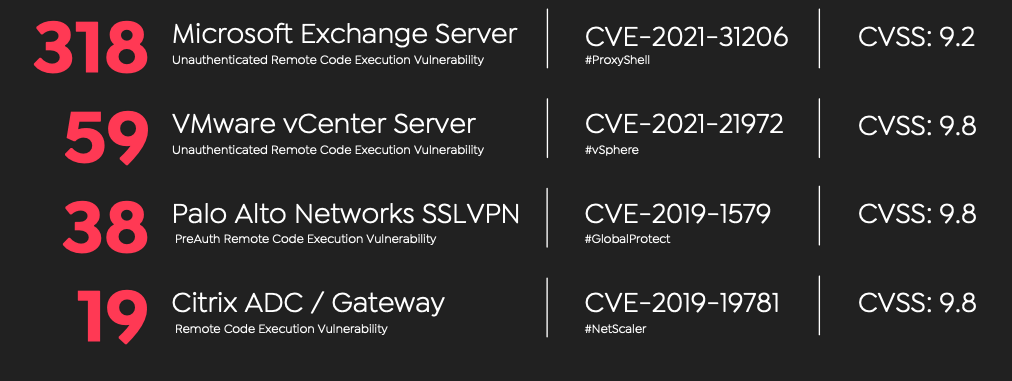
Critical Asset Exposures & Vulnerabilities
When SOC analysts, vulnerability management teams, and security leaders have limited time and budget, prioritizing vulnerabilities to reduce the public attack surface becomes paramount. Following is a high-level statistical view of the critical ports and vulnerabilities on the internet-facing infrastructure and technologies.
According to Shodan, ransomware gangs heavily exploit these as they are exposed, but we can still observe them unpatched or exposed to any remote actors. It is highly recommended to check the technologies listed so far for unpatched, critical, exploited vulnerabilities.
Click here to read the full report and other findings.



































