
Twilio and MailChimp Attackers Hit 130 Organizations with Okta Phishing Campaign
A larger phishing campaign that targeted 136 organizations and resulted in the theft of 9,931 account login credentials has been linked to the hackers behind a series of recent hacks, including those on Twilio, MailChimp, and Cloudflare.
These login credentials were stolen using a phishing kit with the codename 0ktapus.
The initial objective of the assaults was to collect Okta identification credentials and two-factor authentication (2FA) codes from users of the targeted organizations.
How the Attacks Happened
Targets were sent text messages with links to phishing websites that looked like the Okta authentication pages of the specific targeted entities. With the help of the identity-as-a-service (IDaaS) platform Okta, employees may access all of their company’s software resources with just one login.
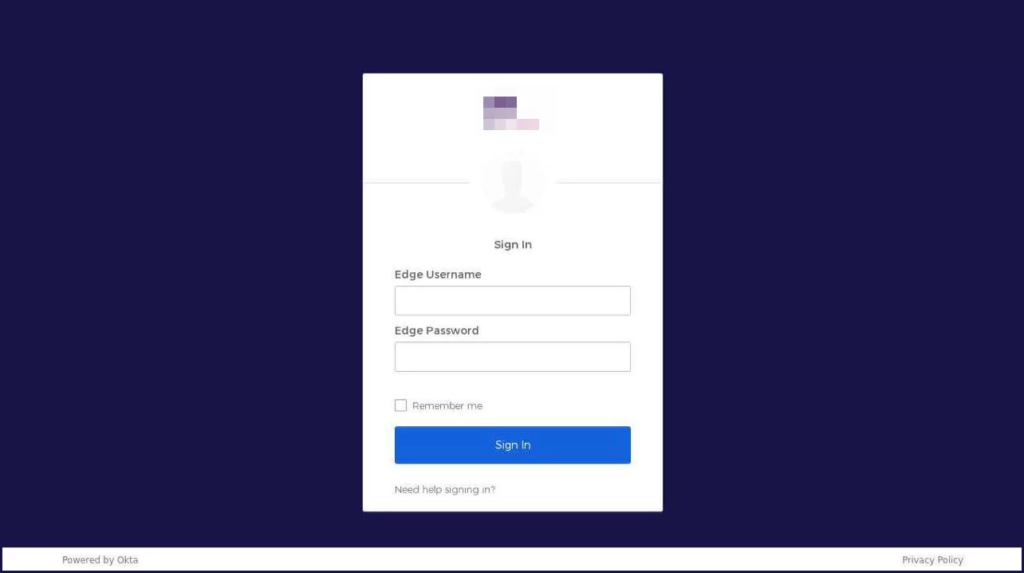
The websites send users’ login information and 2FA codes to a secret Telegram channel where threat actors can retrieve them. The hackers then utilized these login credentials to access business networks, VPNs, and internal customer support systems, allowing them to steal client data.
Researchers traced the activity of the Telegram channel’s admin user “X” and discovered that the account is located in the USA.
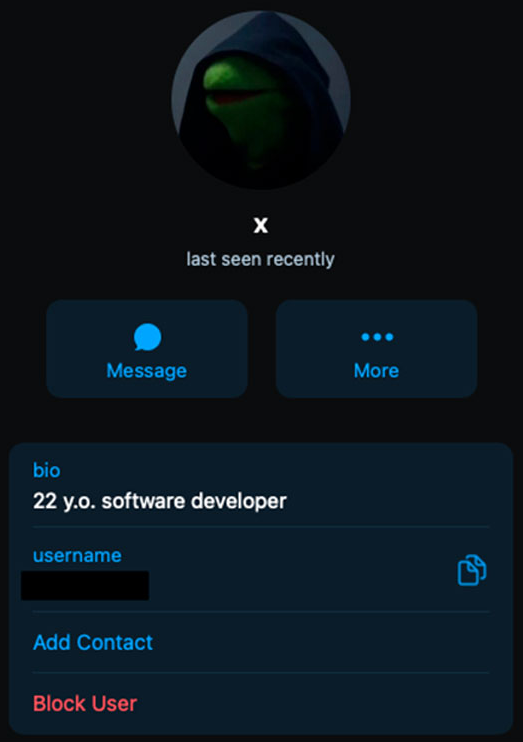
Because the phishing site is static, attackers cannot communicate with victims in real-time like they can with more advanced phishing kits. However, the attackers must utilize the compromised data as soon as they obtain it to gain access before the 2FA tokens expire. This most likely indicates that the attackers were constantly checking their tools and utilizing the credentials as soon as they were obtained.
Group-IB stated that attackers could swiftly change their strategy and carry out additional supply chain attacks once they had gained access to an organization, showing that the attack had been well planned.
Additionally, the attempts to get into Signal accounts suggest that the attackers are also trying to steal sensitive information, such as private conversations. The hackers’ method of obtaining employee names and phone numbers is yet unknown.
Which Businesses Are Affected?
According to reports, at least 169 different phishing domains have been created for this purpose, with the majority of the victim organizations being based in the United States (114), India (4), Canada (3), France (2), Sweden (2), and Australia (1), among other countries. These websites shared a commonality in that they utilized an undocumented phishing kit.
Software companies comprise the most affected businesses, followed by those in the telecom, business services, banking, education, retail, and logistics industries.
Several targeted businesses are Verizon Wireless, AT&T, Binance, KuCoin, CoinBase, Microsoft, Epic Games, Riot Games, T-Mobile, MetroPCS, Evernote, AT&T, HubSpot, TTEC, Slack, Twitter, and Best Buy.
IoCs
|
IPs |
C2 Domains |
|
45[.]76[.]80[.]199 |
twiiio-sso[.]com, box-okta[.]org, kucoin-pin[.]com, boxokta[.]com, kucoin-sso[.]com |
|
66[.]42[.]107[.]233 |
slack-mailchimp[.]com |
|
45[.]32[.]66[.]165 |
microsoft-sso[.]net, sendgrid-okta[.]org, mlcrosoft[.]info, mlcrosoft[.]cloud |
|
45[.]76[.]238[.]53 |
ouryahoo-okta[.]org, ouryahooinc-okta[.]com |
|
155[.]138[.]240[.]251 |
sykes-sso[.]com, internai-customer[.]io, ouryahoo-okta[.]com, ouryahoo-okta[.]net, techmahindra-sso[.]com |
|
149[.]28[.]37[.]137 |
qualfon-sso[.]com, twiiio[.]net, twiiio[.]org, teleperformanceusa-sso[.]com, tmo-sso[.]net, okta-sso[.]net |
|
149[.]248[.]1[.]50 |
att-mfa[.]com, att-rsa[.]com |
|
108[.]61[.]119[.]20 |
mcsupport-okta[.]com, mailgun-okta[.]com, sprint-idg[.]net |
|
149[.]28[.]212[.]53 |
tmobie[.]net |
|
140[.]82[.]63[.]209 |
kucoinpin[.]com, kucoinpin[.]net, twiiio-okta[.]net |
|
144[.]202[.]82[.]47 |
kucoin-pin[.]net, kucoin-sso[.]net |
|
45[.]63[.]39[.]116 |
telus-sso[.]com |
|
149[.]248[.]62[.]54 |
rogers-rci[.]net, rogers-ssp[.]com, iqor-duo[.]net, iqor-portal[.]com, cgslnc-okta[.]com, conexusonline[.]com, klaviyo-sso[.]com |
|
66[.]42[.]91[.]138 |
arise-okta[.]com |
|
216[.]128[.]141[.]52 |
rogers-rci[.]com, verizon-sso[.]net, taskus-sso[.]com |
|
45[.]63[.]39[.]151 |
medailia-okta[.]com, quaifone[.]com, quaifon[.]com, t-moblle[.]org, iqor-sso[.]com, rogers-sso[.]net, tmo-sso[.]com |
|
143[.]244[.]178[.]172 |
teleperformance-help[.]com |
|
66[.]42[.]90[.]140 |
twilio-sso[.]com, rogers-help[.]net, twilio-help[.]com, tmoblle[.]co, t-moblie[.]help, twlilo[.]net |
|
165[.]227[.]57[.]16 |
twilio-sso[.]com, att-sso[.]net |
|
147[.]182[.]201[.]149 |
coin-base-okta[.]com, rogers-sso[.]com, concentrlx[.]com, concentrix-sso[.]com |
|
146[.]190[.]42[.]89 |
teleperformance-sso[.]com, transcom-help[.]com, atento-help[.]com, sykes-help[.]com, sitel-sso[.]com, mailchimp-help[.]com, sinch-sso[.]com |
|
146[.]190[.]44[.]66 |
transcom-sso[.]com, hubspot-sso[.]com, mailchimp-sso[.]com, maiichlmp[.]com |
|
167[.]99[.]221[.]10 |
att-sso[.]com, sitel-help[.]com, bandwidth-okta[.]com |
|
147[.]182[.]132[.]52 |
cloudflare-okta[.]com |
|
167[.]172[.]141[.]4 |
twilio-okta[.]com, iqor-helpdesk[.]com, ttec-help[.]com |
|
67[.]205[.]146[.]165 |
vzw-corp[.]net, iqor-help[.]net, metropcs-edge[.]net |
|
143[.]198[.]164[.]89 |
iqor-tmobile[.]com, iqor-help[.]com |
|
45[.]63[.]79[.]150 |
sykes-vpn[.]com, startek-vpn[.]com, t-moblie-okta[.]com, att-uid[.]co, at-uid[.]com, att-ctx[.]com, att-uid[.]co, activecampaign-okta[.]com |
|
144[.]202[.]117[.]57 |
vzwcorp[.]co |
|
138[.]197[.]7[.]153 |
tmoblle[.]org, t-mobiie[.]co |
|
144[.]202[.]17[.]28 |
att-id[.]net, att-uid[.]net |
|
45[.]76[.]171[.]233 |
uid-att[.]com, att-uid[.]com, intercom-vpn[.]com, sutherlandglobal-vpn[.]com, sitel-vpn[.]net |
|
95[.]179[.]238[.]3 |
t-mobilers[.]com |
|
137[.]184[.]55[.]52 |
tmoble[.]net, tp-update[.]com |
|
159[.]223[.]160[.]128 |
tmoblle[.]net |
|
69[.]55[.]49[.]252 |
teleperformance-usa[.]net, mytpusa[.]net |
|
143[.]198[.]156[.]234 |
tmobiler[.]net, t-mobile-okta[.]net, t-moblier[.]org, teleperformance-usa[.]net |
|
159[.]89[.]93[.]54 |
att-opus[.]net, opus-att[.]com |
|
161[.]35[.]119[.]80 |
t-mobile-okta[.]org, mytpusa[.]com, twit-vpn[.]com, epicgames-vpn[.]com |
|
67[.]205[.]151[.]76 |
att-citrix[.]net, tpusa-citrix[.]com, att-citrix[.]com |
|
138[.]68[.]27[.]0 |
okta-hubspot[.]com, mailchimp-okta[.]com, twitter-okta[.]com, infosys-vpn[.]com, ttec-vpn[.]com, taskus-vpn[.]com |
|
104[.]248[.]234[.]27 |
tp-usa[.]net, tmoblie[.]net |
|
67[.]205[.]154[.]21 |
t-mobiie[.]org, t-mobiie[.]net |
|
64[.]227[.]23[.]72 |
t-mobiie[.]net, okta-oath[.]com |
|
159[.]89[.]159[.]7 |
okta-tmobiie[.]net, t-mobile-okta[.]com, t-mobile-okta[.]us |
|
66[.]175[.]217[.]141 |
okta-tmo[.]org, okta-tmobile[.]org |
|
172[.]105[.]98[.]36 |
tmo-okta[.]com, okta.tmobiie[.]net, okta-drop[.]com |
|
138[.]197[.]194[.]87 |
loginxarth[.]tv |
|
138[.]68[.]26[.]2 |
binance-okta[.]com, snap-okta[.]net, snap-okta[.]com, epicgames-okta[.]com, evernote-onelogin[.]com, riotgames-vpn[.]net, okta-riotgames[.]com, one-login[.]co, cb-okta[.]com, cb-okta[.]net |
|
149[.]28[.]110[.]16 |
tmobile-okta[.]com, tmobile-okta[.]net |
|
157[.]245[.]246[.]85 |
riotgames-okta[.]com, tmobile-okta[.]com, riotgames-vpn[.]com, customer-internal[.]com |
|
147[.]182[.]218[.]194 |
alorica-vpn[.]com, concentrixhelp[.]com, att-vmware[.]com |
|
104[.]248[.]236[.]115 |
att-vpn[.]org, corp-att[.]net, att-vpn[.]com |
|
192[.]241[.]142[.]113 |
att-support[.]org |
|
165[.]227[.]79[.]161 |
tmo[.]ac |
|
137[.]184[.]136[.]163 |
bestbuy-vpn[.]com, ttecvpn[.]com |




































