
Dark Web Profile: Overthinker1877
Overthinker1877 or 1877 Team have recently drawn attention for their random attacks worldwide. Although the first remarkable attack was ransomware against a Romanian news agency in May 2021, they are now on the headlines with global attacks against government websites of various countries. The 1877 Team claims to be of Kurdish origin and allegedly affiliated with the PKK, a terrorist organization.
Who is Overthinker1877?
The Overthinker1877 threat actor specifically targets countries such as Turkey, Iran, Iraq, Israel, and in rare cases, Saudi Arabia.
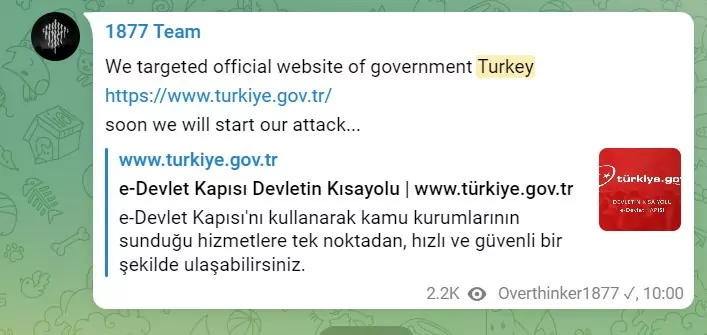
Overthinker1877 has also launched random attacks against various countries worldwide, and they claim the goal of these attacks is “introducing Kurdish hackers to governments and nations. “ The following countries are the victims of these attacks:
| Albania | Australia | Belarus | Belgium | Bolivia | Brazil |
| China | Colombia | Dominic | Ecuador | Egypt | Honduras |
| India | Indonesia | Italy | Kenya | Liberia | Libya |
| Mongolia | Morocco | Netherlands | Pakistan | Philippines | Romania |
| Russia | São Tomé and Príncipe | Sri Lanka | Thailand | Venezuela | Vietnam |
| Zimbabwe |
Overthinker 1877 targets government websites, academic institutions, banks, and media organizations. These attacks also affect commercial organizations, political parties, and personal digital assets.
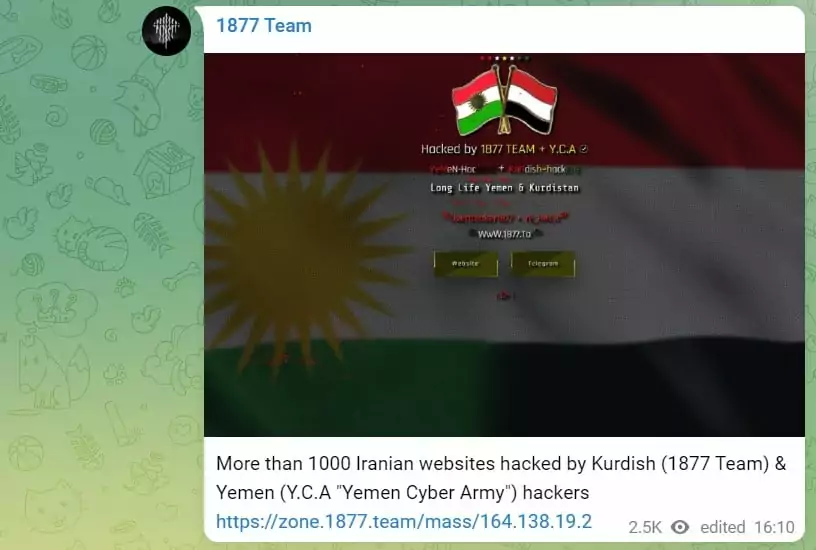
Which Groups does Overthinker1877 Collaborate With?
Overthinker1877 attacked American and Israeli websites with the Iraqi group Altahrae. They also helped the Yemeni group YCA (Yemen Cyber Army) actions on Iranian websites.
Communication Channels
- Telegram: https://t.me/s/x1877x (Created 13 July 2021)
- Twitter: https://twitter.com/1877team (Created June 2021)
- Forum: https://1877.to/
- YouTube: https://www.youtube.com/c/1877team/community
In addition to these,
- https://social.1877.team: Their own messaging platform
- https://zone.1877.team/: Archive of their attacks
Through these platforms they;
- Announce their activities,
- Promote accounts like @Owner1877, @oldboy1877, CodeBoy1877, Utchiha505,
- Create polls and invite subscribers/followers to vote on the next target country,
- Organize competitions among her subscribers,
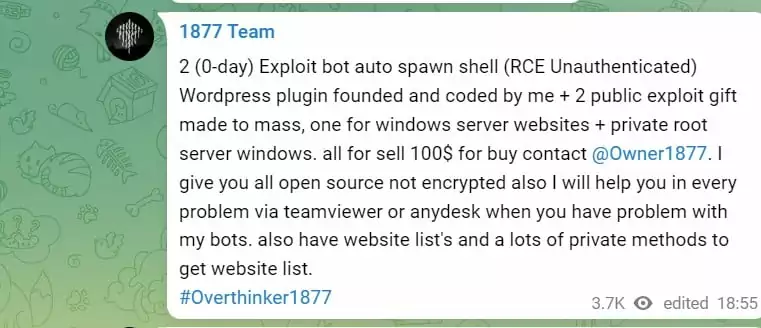
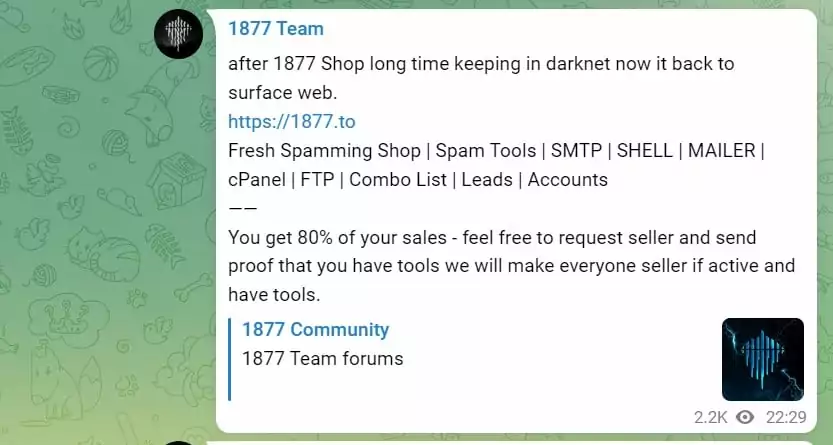
- Sell hacked data such as cards, WHM/C panels, mailers, methods, shells, scam pages, SMTP, leads, documents, accounts,
- Offer sales opportunities to their members who want to sell.
TTPs
TA 0005 Defense Evasion:
| T1112 | Modify Registry |
| T1497 | Virtualization/Sandbox Evasion |
| T1027.002 | Software Packing |
TA 0006 Credential Access
| T1056.004 | Credential API Hooking |
TA 0007 Discovery
| T1518.001 | Security Software Discovery |
| T1120 | Peripheral Device Discovery |
| T1497 | Virtualization/Sandbox Evasion |
TA 0009 Collection
| T1056.004 | Credential API Hooking |
According to MITRE ATT&CK, 4 malicious, 17 suspicious, and 14 informative indicators point to these tactics and techniques.
Overthinker1877 comes to the forefront with scattered attacks that do not have a specific criterion. Many countries have been subjected to such random attacks. The group previously stated they would operate ransomware attacks against government websites and systems. But on 3 September 2022, the group unexpectedly announced that they had stopped all operations. Time will tell whether the group will keep its promise of inaction.



































