
Could Rackspace Incident Be Related to ProxyNotShell?
UPDATE [January 5, 2023]
Play Ransomware Is Responsible for the Rackspace Attack
Rackspace confirmed in recent interviews that the OWASSRF exploit was discovered on its network, and Play ransomware was behind the attack.
To achieve remote code execution via Outlook Web Access (OWA), Play Ransomware exploits CVE-2022-41080 and CVE-2022-41082 vulnerabilities in the new OWASSRF technique. According to researchers, Play ransomware used the OWASSRF exploit to install remote access programs like Plink and AnyDesk on compromised Rackspace servers.
The company is working on automatically generating download links for affected users’ mailboxes, which contain Hosted Exchange email data before December 2. Customers could do this through the company’s customer portal.
Read more about Play Ransomware’s operation in our blog.
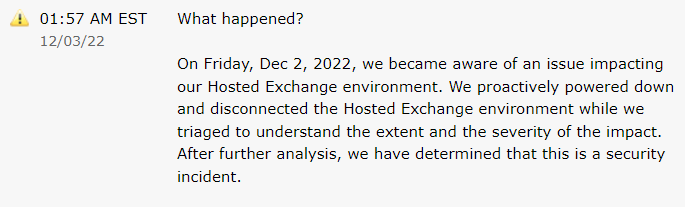
Rackspace, a cloud service provider, has been experiencing disruptions in its hosted Microsoft Exchange environments. Thousands of customers are still expecting clarification.
At first, the company described the problem as a “system disruption” they are attempting to fix with their team on Rackspace Status Page. Almost a day after the problem began, Rackspace revealed that the root cause of the disruption was a security incident but provided no additional information in the following updates.
Affected services are as follows:
- MAPI/RPC
- POP
- IMAP
- SMTP
- ActiveSync
- Outlook Web Access (OWA)
Unpatched Exchange Servers Might Have Caused
Security expert Kevin Beaumont has shared a possible explanation for the ProxyNotShell (CVE-2022-41040) vulnerability being involved in the security incident.
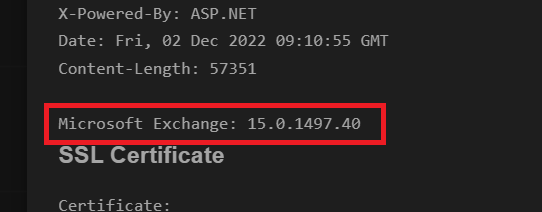
Beaumont posted his documentation as a Mastodon thread and noted that Rackspace has been using Microsoft Exchange build 15[.]0[.]1497[.]40, which was before the ProxyNotShell patches were available.
The CVE-2022-41040 and CVE-2022-41082 related to ProxyNotShell have been fixed in Microsoft’s November Patch Tuesday. The build used by Rackspace is from August and is vulnerable to ProxyNotShell, which might have caused the problem.
The zero-day vulnerability ProxyNotShell was discovered in September 2022, and since then, it has been actively exploited to deploy web shells on vulnerable Microsoft Exchange servers.
Learn more about the ProxyNotShell vulnerability on our blog.
Prioritize Patches with SOCRadar
SOCRadar assists security teams at every stage of a vulnerability’s lifecycle with its Extended Threat Intelligence concept. It automatically detects your external-facing assets, scans them regularly, and ensures that you are prepared for new vulnerabilities.
Vulnerability Intelligence helps you find what you need instantly by collecting all valuable resources on vulnerability trends on a single page.
SOCRadar uncovers adversaries that exploit vulnerabilities with its dark web monitoring module.
Is There a Way for Mitigation?
According to the last update (December 5), Rackspace has seemingly restored many of its customers’ email services on Microsoft 365. The full scope of the security incident is still unknown.
As the disruption is still being addressed, the company recommends migrating services and providing affected customers with free Microsoft Exchange Plan 1 licenses.
You can find instructions to migrate and activate a license here.
See the Rackspace System Status page here.


































