4 Lessons Learned from Supply Chain Attacks in 2022
At the BlackBerry Security Summit in 2022, four-fifths of IT decision-makers said they had been notified of an attack or vulnerability in their supply chain within the year. 77% of organizations stated that they had detected the presence of unknown participants in their software supply chains in the last 12 months.

Although the Log4Shell vulnerability has opened the eyes of many organizations to attacks from their supply chains, according to Anchore’s report, attacks originating from the supply chain managed to increase by 62% in 2022.
Download SOCRadar’s 2022 End-of-Year Report to gain insights into supply chain attacks.
What is a Supply Chain Attack?
A supply chain attack is an attack that targets you through a 3rd party partner or provider that has access to your organizational data or resources. Various vulnerabilities in 3rd party organizations that exhibit weak security posture mean a weakness in the supply chains of other organizations.
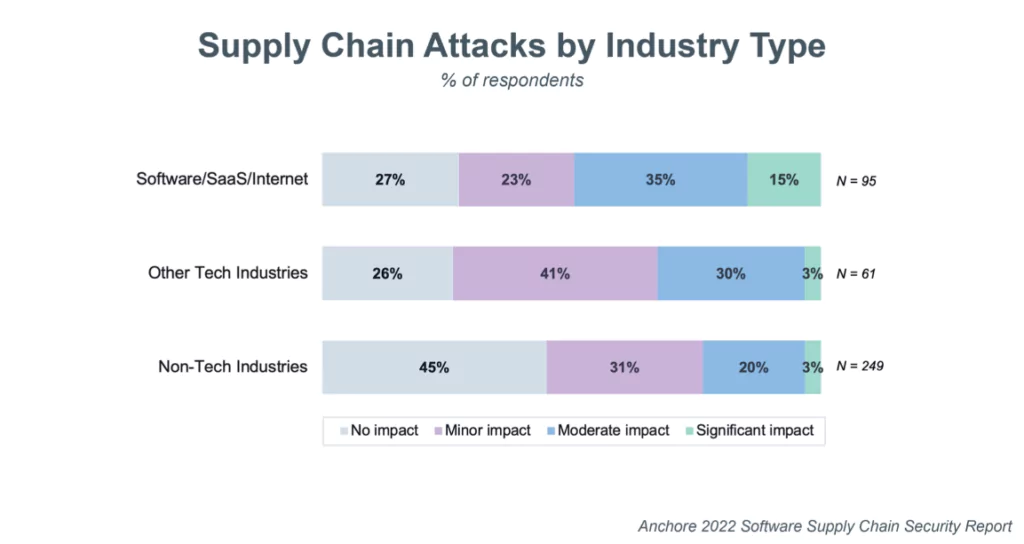
If a partner with access to the network is hacked, threat actors can leverage it to infiltrate other networks. A breached provider means that the shared data pool is also compromised, even if it does not have access to the internal network. Especially if a vendor with a large customer portfolio experiences such an incident, it could boost many attacks in the future.
Last year, the supply chain risk that had been relatively unseen shocked the whole security community with SolarWinds’ hack.
The Overlooked Threat
Threat actors infiltrated the SolarWinds network in 2019 but were discovered in the last quarter of 2020. The threat attributed to Russia managed to enter many government agencies, private companies, and organizations through SolarWinds, with a total number of 250, according to the New York Times. Threat actors infiltrating SolarWinds’ development operation were able to corrupt a software update distributed by the company. They send their malware, entering many companies doing business with SolarWinds in this way, revealing how important the phenomenon called supply chain attack is.
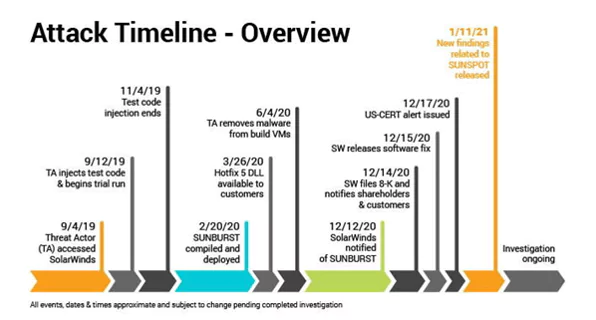
The biggest takeaway from the SolarWinds incident was how vital the software is, rather than network-related attacks from 3rd party organizations. Since every institution must use the tools and programs of various 3rd parties in its development and operational activities, many organizations may be affected in case of software corruption like SolarWinds example.
Major Supply Chain Attacks of 2022
WordPress Plugin The AccessPress Compromised
In 2021 Access Press, a WordPress plugin used on more than 360 thousand active websites, was hacked, and threat actors infected the software with a backdoor. They could access all websites using this plugin, but in 2022 most plugins updated to the new versions.
The Okta’s Network Hacked
Authentication services provider Okta’s network was hacked in January by the Lapsus$ group, and Okta’s customer information was accessed through Sitel, a 3rd party organization. According to the statement of Okta, which has more than 15 thousand customers, 375 customers were affected by the attack.
GitHub Incident
In an incident uncovered by GitHub Security teams in April, threat actors aimed to steal the OAuth tokens assigned to 3rd party integrators named Heroku and Travis-CI and use them to steal data from GitHub customers who use the products of the 3rd party organizations mentioned.
Fishpig Infected
Threat actors infiltrating Fishpig’s systems in August were able to inject malware into the Magento Security Suite and WordPress Multisite modules, aiming to gain access to many websites using Fishpig extensions.
Comm100 Compromised
Comm100, a chat provider, also suffered a cyberattack in September, and threat actors who infiltrated the company’s infrastructure hijacked Comm100’s installer and hid a backdoor. Although it took a short time for the attack to be noticed and for security teams to take measures, it is thought that it may have affected thousands of customers from 51 countries.
What are the Lessons to Learned?
Lesson 1: You should monitor public Repositories like GitHub.
Today, many organizations manage their projects on GitHub and use external repositories at some point, but we should remember the threats on GitHub. If the repository of a trusted 3rd party organization is captured, their inclusion in our projects unchecked means that they are waiting to be abused by a threat actor.

Lesson 2: You need to know more details about your supply chain.
It becomes very difficult to prevent such attacks when you lack visibility or control within your supply chain. For this reason, organizations should aim to increase their controls in their supply chains. They should inform their partners about their baseline security practices or choose suitable partners for adequate security. On top of that, even if these policies are followed, every attack surface should be seen as a potential weakness both in the internal operation and the workflow with the partners within the framework of ZeroTrust logic.
Lesson 3: IoCs are not enough; firstly, know where attacks may come from.
While IoCs are critical warnings, they have a significant limit; your solutions may prove useless when faced with previously unused malware exploits and known infrastructures. In a supply chain scenario, attackers want to target you at points in your supply chain that contain vulnerabilities but don’t know about. In these cases, searching for indicators will not be an adequate cyber defense measure. However, by mastering Attack Surface Management, we can identify our weak points and observe them through (help) indicators.
Lesson 4: Switch your reactive security stance to proactive.
In 2022, we witnessed the rise of supply chain attacks; as it has been revealed in the past years, security tools and methods need to be more successful to prevent such attacks. Since reliable software is often corrupted in supply chain attacks, systems focused on vulnerabilities cause you to miss them. At this point, organizations may change this phenomenon by focusing on proactive defense rather than solely relying on reactive security measures.
Check out SOCRadar’s article to adopt a behavioral approach, and put the other lessons learned into practice.
What Could Happen in 2023?
The human factor has played a prominent role in many cybersecurity incidents, enabling attackers to initial intrusion. Lack of cybersecurity awareness is still one of the most critical deficiencies in hacking an institution.
According to various cyber security predictions, supply chain attacks will continue to increase in 2023, and on top of that, researchers state that these attacks will accelerate and diversify.
Platform owners, on the other hand, will take various precautions as:
- Malicious package detection.
- Integrated third-party package scanners.
- IP range locks for package publishing.
- Integrated password-reuse checks.
These measures are necessary steps, especially in software supply chain attacks. Still, threat actors will likely adapt to this and tend to different vulnerabilities in the supply chain. However, you can proactively configure your measures using SOCRadar’s supply chain intelligence.