Dark Web Profile: Cyber Av3ngers
The Cyber Av3ngers, reportedly connected to Iran’s Islamic Revolutionary Guard Corps, have become known for attacking critical infrastructure, especially in the US and Israel. This group often targets SCADA systems made in Israel, but used in other countries as well. While some of their claims of attacks might be questionable, other operations have been confirmed. They highlight the risks in internet-connected industrial systems by focusing on specific Israeli-made technology.
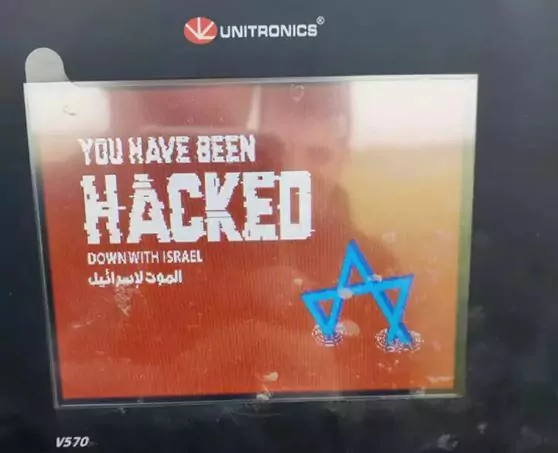
While some security researchers questioned the claims, they attracted attention with the similar images above, displayed on a Unitronics product. They had previously shared their attacks on X (formerly Twitter) and Telegram platforms and even sent alleged PoCs of their attacks to SOCRadar. However, defacement of the devices in the US attracted the wide attention of the mainstream media, which the group really wanted for so long.
Who is Cyber Av3ngers?
We have previously discussed them as a hacker/hacktivist collective, but the Cyber Av3ngers are Iranian Government Islamic Revolutionary Guard Corps (IRGC)-affiliated Advanced Persistent Threat (APT) cyber actors, according to CISA. Their primary focus has been on exploiting vulnerabilities in internet-connected devices, particularly those manufactured by Israeli companies like Unitronics.
The group emerged before the conflict, but came to the forefront in parallel with the Israel-Hamas conflict, and its first noteworthy attacks were on railway systems and water treatment facilities in Israel.
As CISA stated: “The group claimed responsibility for cyberattacks in Israel beginning in 2020. CyberAv3ngers falsely claimed they compromised several critical infrastructure organizations in Israel.”
Although the group claimed attacks from 2020, their current Telegram channel was created in September 2023, and they caught the public attention just in July 2023 and the wider attention during the recent conflict.
Some of these claims, particularly about compromising Israeli critical infrastructure, have been proven false. Furthermore, the group is also reportedly linked to another group known as Soldiers of Solomon, which is also claimed to be affiliated with the Iranian IRGC.
Cyber Av3ngers’ recent activities reflect a broader strategy of targeting critical infrastructure beyond regional boundaries, expanding their cyber operations to include significant targets within Israel and the United States. This background sets the stage for understanding the strategic intent and capabilities of Cyber Av3ngers in the global cyber warfare landscape.
Modus Operandi of Cyber Av3ngers
The Cyber Av3ngers’ operations focus on exploiting vulnerabilities in internet-connected operational technology devices. Their primary tactic involves targeting devices made by the Israeli company Unitronics, using default credentials and ports to gain access.
They have demonstrated a capability to infiltrate critical infrastructure systems, such as water facilities in the United States. This method of operation highlights the group’s focus on industrial control systems, emphasizing the risks associated with internet-connected devices in vital sectors.
The CISA advisory AA23-335A details the activities of the CyberAv3ngers as targeting Unitronics PLCs in U.S. water and wastewater facilities. These actors use default credentials or brute-forcing to compromise devices, leaving defacement messages, and leaking sensitive data.
It is also claimed that the group or their connections owns customizable Crucio Ransomware. CISA shared the following “suspected” ransomware IoCs in their advisory.
- MD5 Hash: ‘BA284A4B508A7ABD8070A427386E93E0’ – Suspected to be associated with Crucio Ransomware.
- SHA1 Hash: ’66AE21571FAEE1E258549078144325DC9DD60303′ – Suspected to be linked to Crucio Ransomware.
- SHA256 Hash: ‘440b5385d3838e3f6bc21220caa83b65cd5f3618daea676f271c3671650ce9a3’ – Suspected Crucio Ransomware hash.
- IP Address: ‘178.162.227[.]180’ – Suspected IP associated with Crucio Ransomware.
- IP Address: ‘185.162.235[.]206’ – Another suspected IP linked to Crucio Ransomware.
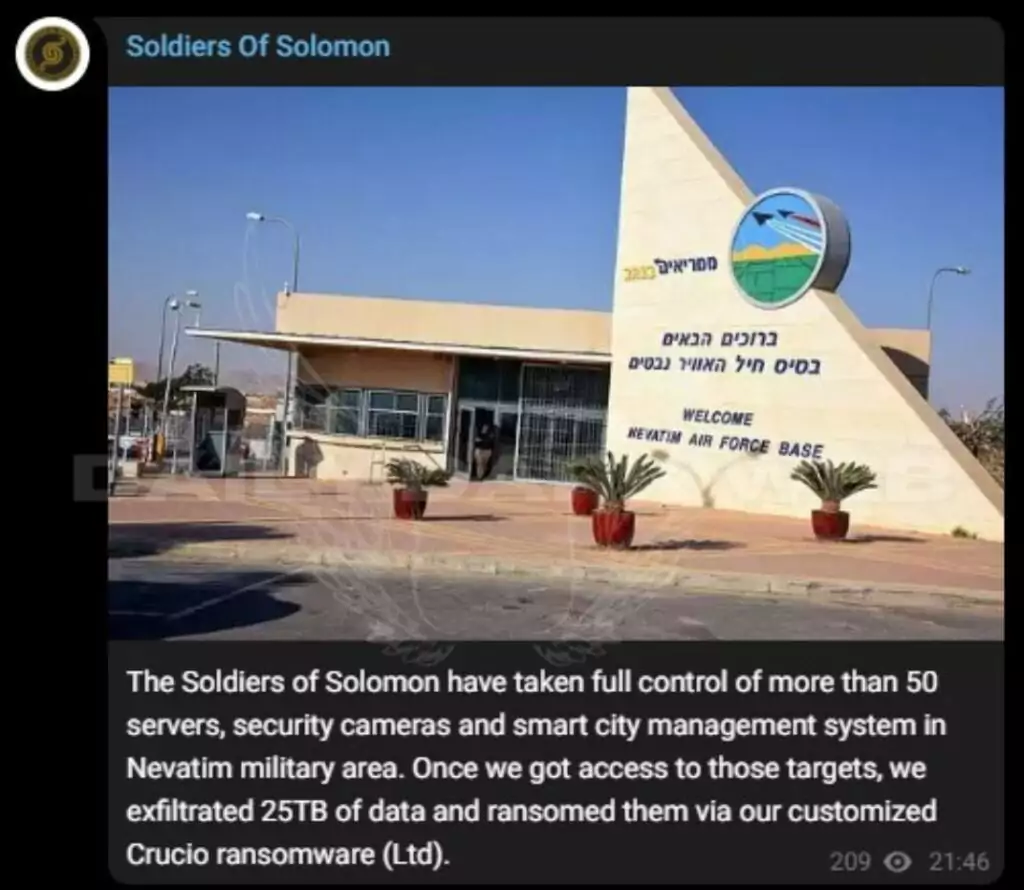
While we included this claim of Soldiers of Solomon in our daily blog, where we look at the reflection of the conflict in the cyber world, we stated that it was a highly questionable claim, and many of their claims in this attack were actually disproved later.
It is known that Iranian APTs engage in encryption, extortion, and data destruction in their espionage and sabotage operations. However, both Soldiers of Solomon and Cyber Av3ngers do not appear to be full-fledged APT groups but more like state-sponsored hacktivist movements.
Notable Attacks by Cyber Av3ngers
The first attack they were able to make their voices heard was the Israeli railway systems.
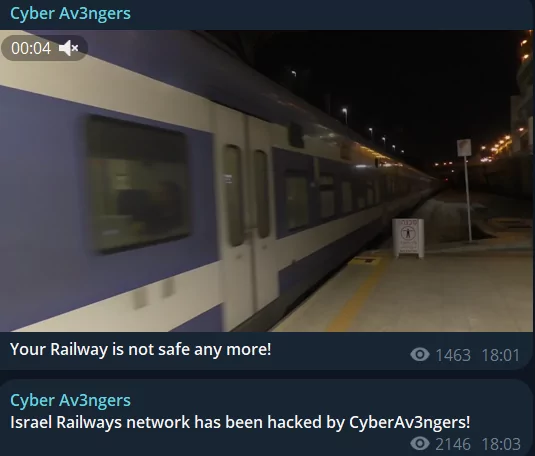
They claimed responsibility for cyberattacks on Israel’s railway infrastructure, beginning July 14. These attacks reportedly targeted 150 servers and disrupted operations at 28 railway stations. They stated the attacks were in retaliation for the killing of IRGC commander Qasem Soleimani and continued for ten days. They also claimed an electricity outage in Israel earlier in July.
Cyber Av3ngers has been implicated in several significant cyberattacks, notably many Israeli water treatment facilities and water systems related targets in the US. An attack in a water pumping station, involved penetrating a Programmable Logic Controller (PLC) made by Unitronics, once more illustrating the group’s focus on critical infrastructure.

Some other reported targets include a brewery in Pittsburgh, an aquarium, and several water facilities in Israel.
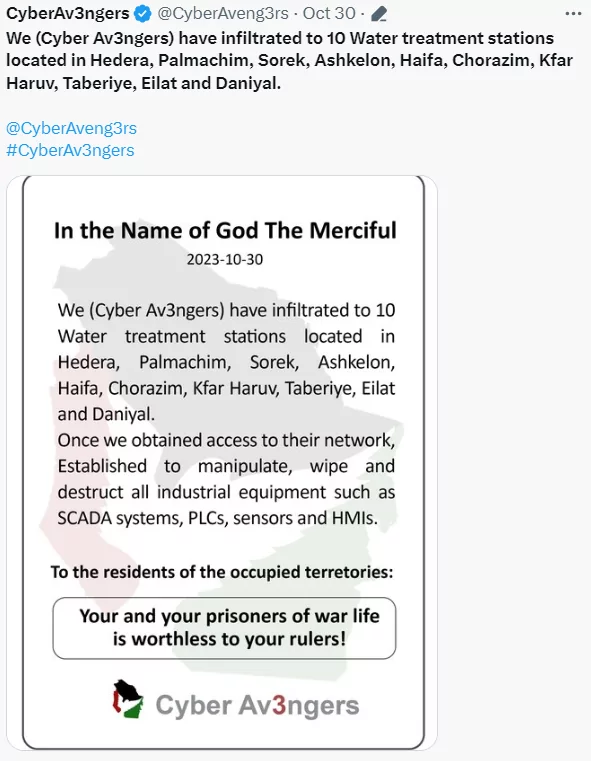
These attacks highlight the group’s capability to disrupt essential services and the broader risk posed by internet-connected industrial devices. However, it also shows that they have the ability to target only a very niche industry. The vast majority of their targets were aimed at similar types of devices and establishments.
Impact and Consequences
The attacks by Cyber Av3ngers, particularly on U.S. critical infrastructure, underscore a significant cybersecurity risk. Targeting internet-connected devices in essential services like water supply exposes vulnerabilities in industrial control systems.
These operations not only disrupt operations and possibly the public’s comfort but also raise national security concerns, highlighting the need for enhanced protection measures for critical infrastructure against cyber threats. The activities of Cyber Av3ngers thus demonstrate the growing sophistication and reach of cyber threat actors, emphasizing the importance of robust cybersecurity strategies.
Mitigation
To defend against CyberAv3ngers’ activities, critical infrastructure organizations, specifically those using Unitronics products, should implement several cybersecurity measures. These include upgrading to VisiLogic software that mandates changing default PLC passwords, disconnecting PLCs from public-facing internet, implementing Multi Factor Authentication (MFA), using firewalls or VPNs for remote access, creating strong backups using CISA advised 3-2-1 strategy that you should have three copies of your data (your production data and two backup copies) on two different media (disk and tape) with one copy off-site for disaster recovery, lastly keeping PLC devices updated.
Manufacturers should also ensure products are secure by design, avoiding default passwords and unnecessary internet exposure. Continuously testing and validating security controls against MITRE ATT&CK techniques is also recommended.
However, although manufacturers’ primary responsibility is to provide safe products, their users must also fulfill their duties within Supply Chain security. One way to achieve this is to follow incidents and vulnerabilities about your vendors and suppliers, and take proactive measures using the SOCRadar Supply Chain Intelligence.
For detailed information on these mitigations, visit the CISA Advisory.
MITRE ATT&CK TTPs of Cyber Av3ngers
| MITRE ATT&CK Tactic | MITRE ATT&CK Technique | Description |
| TA0040: Impact | T1485: Data Destruction | Cyber Av3ngers’ operations involve compromising and potentially damaging critical systems. |
| TA0043: Reconnaissance | T1595: Active Scanning | The group likely conducts active scanning to identify accessible internet-connected devices. |
| TA0042: Resource Development | T1583: Acquire Infrastructure | They might acquire specific infrastructure for their cyberattacks. |
| TA0006: Credential Access | T1110: Brute Force | The group uses brute force attacks to obtain login credentials. |
| TA0006: Credential Access | T1552: Unsecured Credentials | They exploit default credentials in devices to gain unauthorized access. |