Threat Actors Accessed UK Military Data From Weakest Link
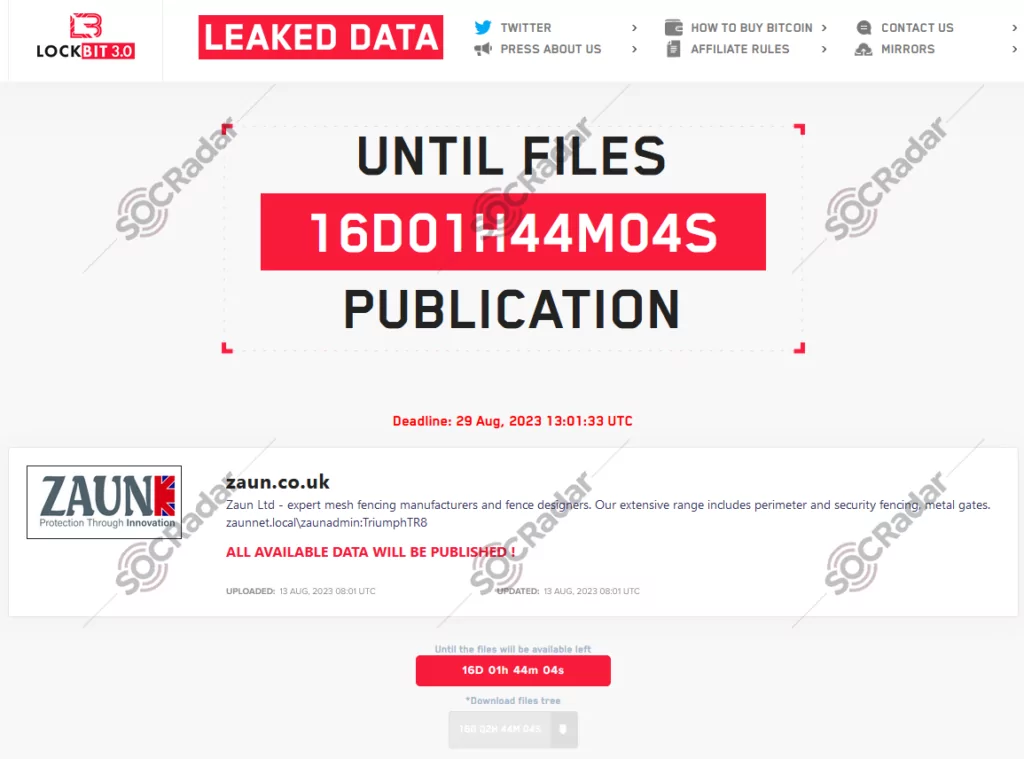
On the 13th of August, The LockBit Ransomware group added a new victim to its list. The victim supplier, manufacturing company Zaun, expressed its belief that no classified information had been downloaded. However, reports suggested that the attackers acquired data that could grant access to some of the United Kingdom’s most critical military and research facilities according to The Register.
Zaun specializes in high-security perimeter fencing and, while not officially recognized as a government-approved security contractor, is authorized for government use through the Centre for the Protection of National Infrastructure (CPNI).
Statements of The Company
The LockBit Ransom group attacked the company’s network, and Zaun acknowledged that the group may have extracted 10GB of data. Furthermore, the company admitted that the attack may have extended beyond their server’s initial Windows 7 entry point.
The company stated, “We have no reason to believe that classified documents were stored on our system or have been compromised.” This reassurance is significant, especially for the agencies that rely on the company’s services. Zaun also reported the breach to the UK National Cyber Security Centre (NCSC) and the Information Commissioner’s Office (ICO).
In an official statement, Zaun disclosed, “We became aware of an attack on our servers by the LockBit Ransom group in early August. Our cybersecurity systems successfully thwarted the attack before any files on the server could be encrypted. However, it has come to our attention that LockBit retrieved some data from our system, which has since surfaced on the Dark Web.”
Weakest Link of The Chain
The Company acknowledges that threat actors gained access to the system through a computer running on the Windows 7 operating system. Although Windows 7 updates ceased in 2015, full support was officially terminated in 2020, rendering this unpatched operating system vulnerable to attacks and an attractive target for malicious actors.
To some readers, the usage of Windows 7 may appear somewhat absurd. However, when we examine the industries most frequently targeted by ransomware groups, such as Manufacturing, which topped the list last month, it becomes evident that the use of systems lacking these updates is prevalent. A comparable scenario is also noticeable in the Education and Healthcare sectors. The rationales behind this phenomenon include the fact that certain computers or IoT devices serve specialized functions and remain operational as long as they are functional, limitations in resources prevent the adoption of newer versions, and there are embedded systems that are challenging to update.
Indeed, while keeping systems up to date and retiring end-of-life products seems like a straightforward solution, practical constraints often prevent this from being feasible. In such cases, focusing on alternative measures can be more cost-effective. To begin with, any system lacking updates should never be directly exposed to external networks. Even if it needs to be connected to an intranet, it should be placed within a separate subnet, isolated from the rest of the network. Additionally, such systems mustn’t store critical data and should undergo rigorous monitoring, with any unusual activities scrutinized closely.
How Can SOCRadar Help?
While the reactive solutions mentioned earlier can provide immediate relief, they still fall short of establishing a comprehensive security framework. To achieve complete coverage, it is imperative to adopt a proactive approach to security, which includes Cyber Threat Intelligence in addition to conventional methods.
The incident above serves as a prime example, illustrating that a vulnerability within the system can result in compromises or even threaten other companies when a compromised supplier is involved. As long as vulnerabilities persist within your system or supply chain, organizations will remain susceptible to threats.
To address this issue, SOCRadar offers a solution. Leveraging the SOCRadar Supply Chain Intelligence feature, you can assess companies’ vulnerabilities and security posture within your supply chain, allowing you to take early preventive measures. Simultaneously, by utilizing the SOCRadar Attack Surface Management module, you can pinpoint weaknesses within your own assets, bolstering your overall security.