
The Buyer’s Guide to Extended Threat Intelligence – SOCRadar
Imagine walking into the office on a regular Tuesday morning. As the CISO, you grab your coffee, sit at your desk, and are immediately flooded with alerts. Phishing attempts, malware detections, dark web monitoring, and reports from third-party vendors pile up. It feels like you’re fighting a constant battle, spending hours chasing down vulnerabilities while the clock ticks. You ask yourself, “Is this the best use of my team’s time?”

Depiction of a CISO in a sleek, lost in thought during a calm night. Generated using Dall-E
For many cybersecurity teams, the answer is no. Time and effort are wasted on manual processes—chasing after vulnerabilities, digging through data, and reacting to threats that could have been caught earlier. Recent statistics show that 63% of ransom demands now exceed $1 million, with companies left scrambling to respond after the damage is done. The cost of a breach isn’t just monetary—it’s time, reputation, and effort.
The content in this blog is compiled by SOCRadar researchers from the Top 50 Cybersecurity Statistics in 2024 (Essential Insights on Ransomware, Phishing, Industry Trends, and More).
The Complexity of Cyber Threats Today
The landscape of cyber threats has evolved dramatically in recent years. Ransomware attacks are now more frequent and more sophisticated than ever before. In fact, ransomware attacks surged by 20% in Q1 2024 compared to the previous year, showing how relentless these attacks can be. And it’s not just ransomware. Phishing remains one of the top initial attack vectors, responsible for 79% of account takeover incidents. With 93% of organizations admitting to paying ransom after a breach, the stakes have never been higher.
Despite these statistics, the process of identifying and preventing these attacks remains largely manual for many organizations. Teams spend hours sifting through logs, responding to alerts, and patching vulnerabilities. On average, it takes 277 days to identify and contain a data breach, a staggering number when every second counts.
With cybercrime expected to cost the world $10.5 trillion annually by 2025, it’s clear that organizations cannot afford to waste time. Security teams are stretched thin, often spending more time reacting to threats than proactively defending against them. In fact, the skills gap has been cited as one of the top barriers to an effective cybersecurity strategy.
Manual Processes Are Holding Your Team Back
Let’s face it—your team is bogged down with manual processes. They’re juggling dozens of tools, trying to make sense of mountains of data, and barely keeping up with the constant stream of threats. According to Gartner, 80% of CIOs plan to increase their spending on cybersecurity this year, with a focus on efficiency and automation. But what does that look like in practice?

Extended Threat Intelligence (XTI) by SOCRadar
For many teams, it means adopting threat intelligence tools and automated systems that reduce the need for manual monitoring. Instead of responding to threats after they’ve already caused damage, security teams need real-time insights to stay ahead of attackers. This is where SOCRadar’s Extended Threat Intelligence (XTI) platform comes in.
The First Revelation: External Attack Surface Management
Your first major issue was understanding the full scope of your digital presence. With rapid expansion, you had new cloud services, third-party vendors, and online platforms sprouting up everywhere. You needed to map every digital asset, from servers and websites to IoT devices and rogue apps.

A depiction of the castle representing External Attack Surface Management, with its blend of strength and vulnerable areas. Generated using Dall-E.
The platform instantly scanned your external assets, delivering insights on over 1.6M domains, 5.5M ports, and hundreds of IP addresses that your company was exposed to. You quickly realized there were servers and websites still accessible from old projects, completely forgotten, leaving you vulnerable to attacks.
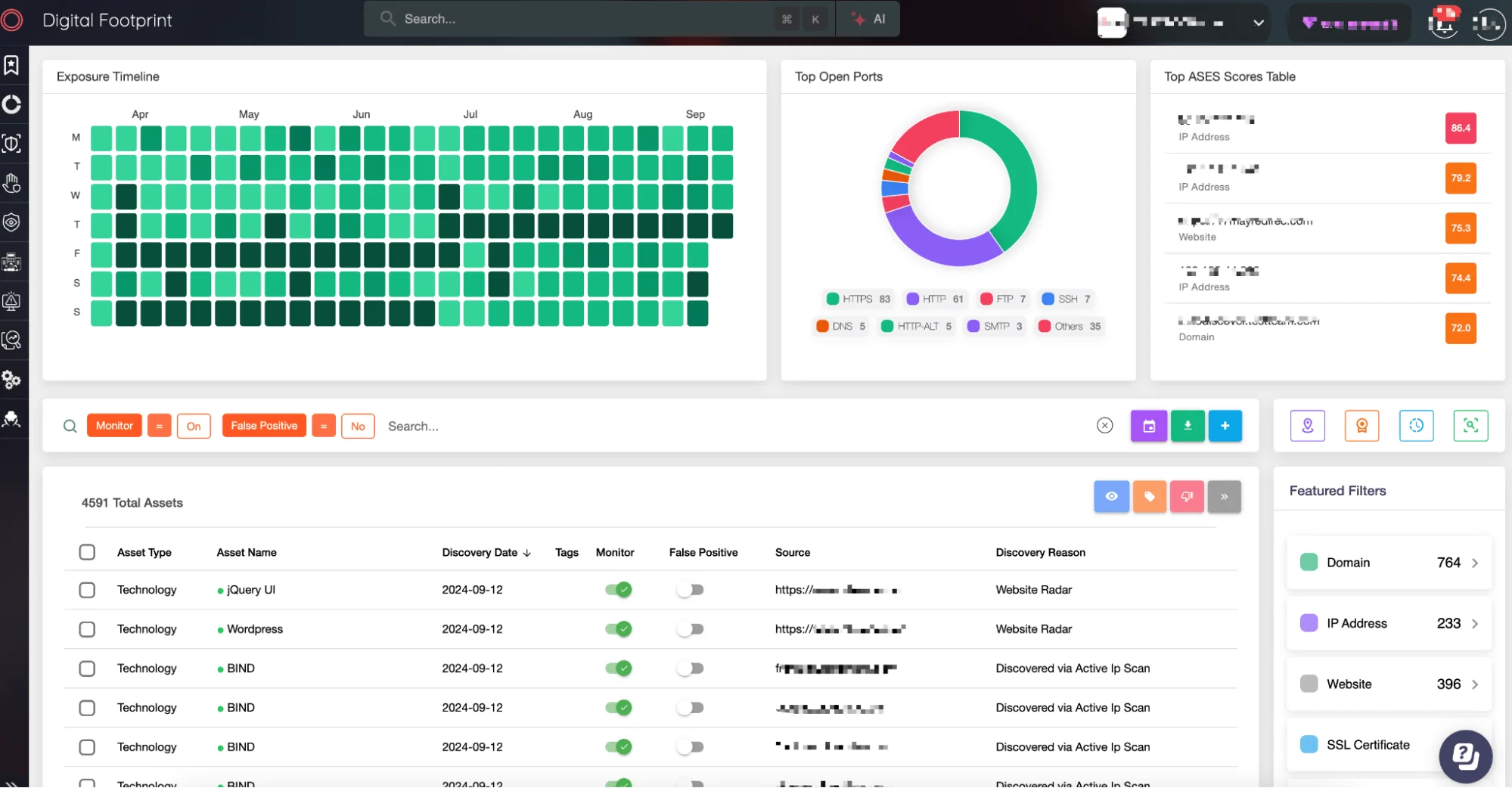
SOCRadar XTI External Attack Surface Management
According to the 2024 Gartner CIO and Technology Executive Survey, 80% of CIOs plan to increase spending on cyber/information security this year . Clearly, you weren’t alone in feeling the urgency of protecting your organization’s attack surface.
With SOCRadar, you gained continuous visibility over your digital landscape. Every time a new asset was created—or an old one forgotten—the system alerted you in real-time. You went from being a firefighter, always putting out cyber-fires, to a strategist with a bird’s-eye view of your entire digital empire.
The Dark Web Discovery: Advanced Dark Web Monitoring
One morning, a member of your team rushed into your office, pale-faced and holding a printout from a hacker forum. Your company’s data—customer credentials, even a few proprietary documents—was up for sale on the dark web.

The blend of mysticism and high-tech monitoring represents SOCRadar’s vigilance in identifying hidden threats. Generated using Dall-E.
Panic set in. Was this real? Could it be happening to your company? How would you find out?
Luckily, SOCRadar’s Advanced Dark Web Monitoring was designed for exactly this. The platform was already monitoring over 4,659 Telegram channels, 340 Discord servers, and 231 hacker forums, where these illicit activities take place. Within minutes, SOCRadar confirmed the breach and alerted you to other, previously unknown, data leak discussions circulating online.
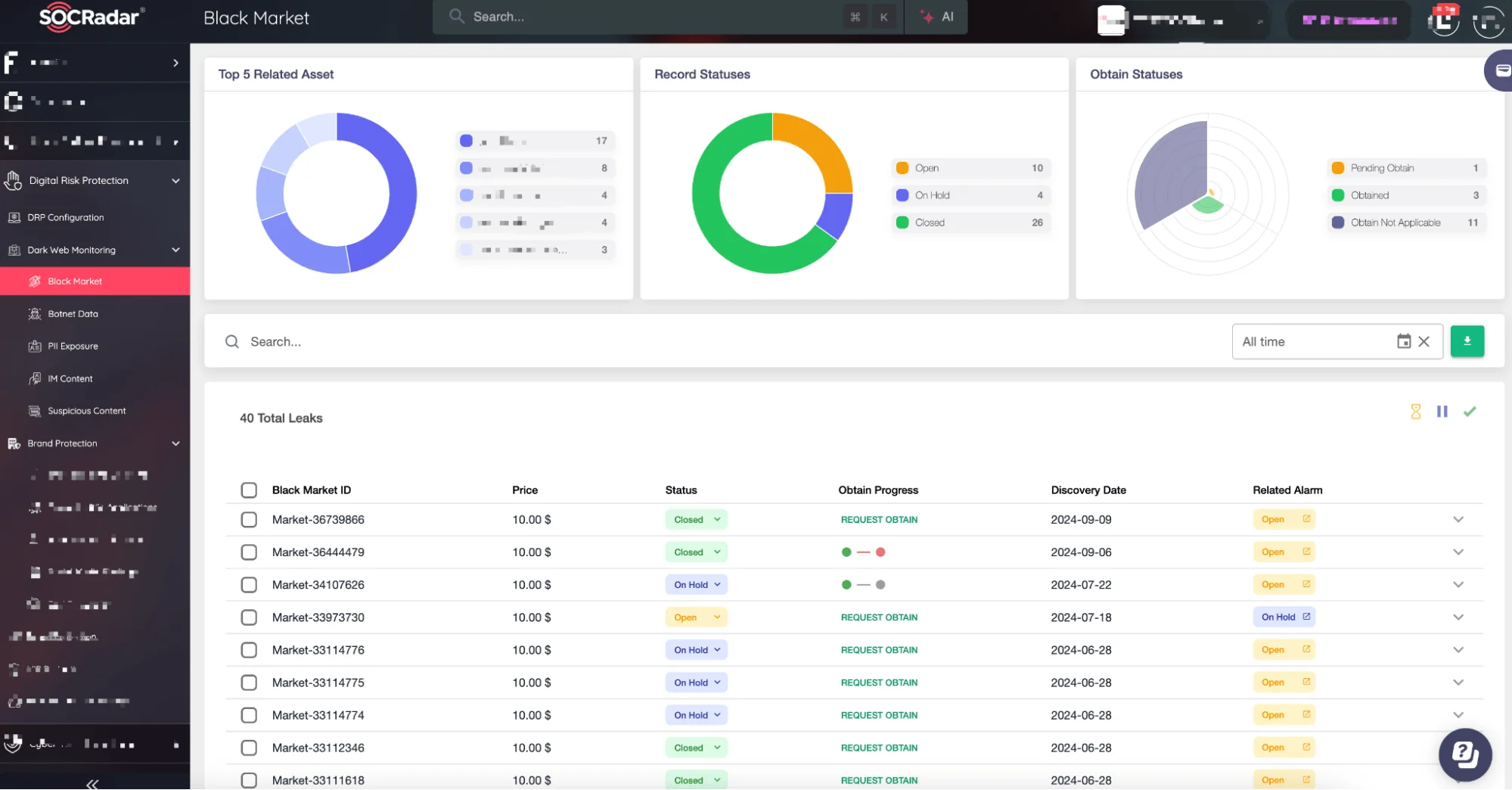
SOCRadar XTI Advanced Dark Web Monitoring
A 643% increase in compromised devices infected with infostealer malware over the past three years indicates how fast threats can escalate. But with SOCRadar, you had a fighting chance to act before the damage was irreversible.
Actionable Insight: SOCRadar didn’t just stop at detection. It provided immediate, actionable intelligence on how to prevent further leaks. Within the hour, your team had secured the breached assets and taken steps to prevent further exploitation.
The Battle with Cyber Threats: Cyber Threat Intelligence (CTI)
While you were plugging holes in your attack surface and scanning the dark web, another battle was raging: managing the constant flood of cyber threat data. Your team was drowning in information—thousands of phishing alarms, endless vulnerability reports, and pages of Indicators of Compromise (IOCs).

Showing knights defending a castle from cyber threats, with magical elements representing CTI. Generated using Dall-E.
You needed a way to prioritize threats and sift through the noise. Enter SOCRadar’s Cyber Threat Intelligence (CTI) module.
CTI provided real-time, actionable intelligence on the threats specifically targeting your industry and region. With 5.18M discovered PII exposures and over 1M contextualized phishing alarms, you no longer had to guess which threats mattered. CTI took all that data and turned it into focused, prioritized alerts, allowing your team to tackle the most critical vulnerabilities first.
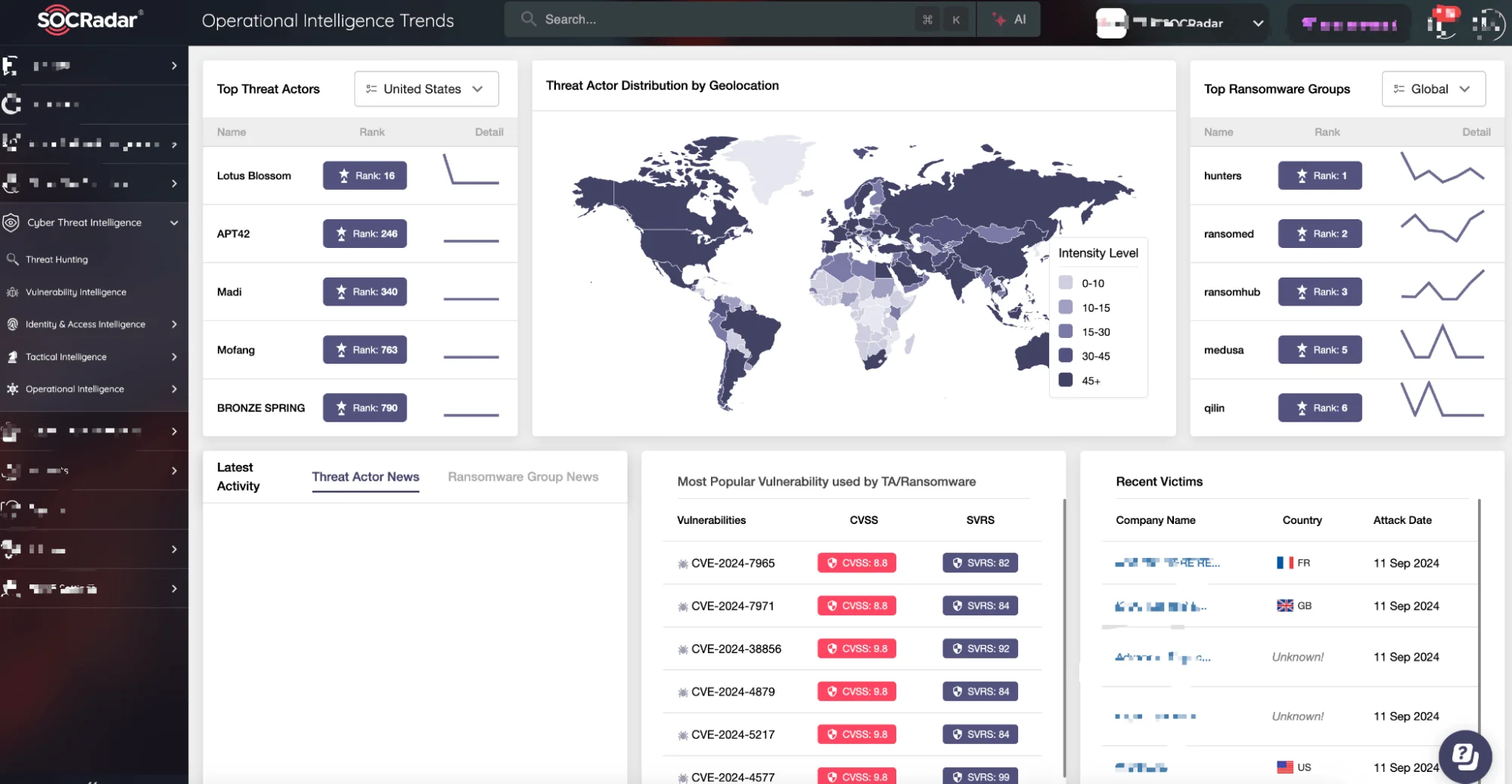
SOCRadar XTI, Cyber Threat Intelligence (CTI)
In one instance, the platform flagged a new phishing attack targeted at your executive team. 94% of organizations report experiencing email security incidents, and phishing is still the most common method for launching these attacks. Without SOCRadar’s CTI, the phishing emails might have slipped through the cracks. But now, you were able to act quickly, shut down the campaign, and protect your team.
The Brand at Stake: Brand Protection (Digital Risk Protection)
A month later, while enjoying your morning coffee, an email from the marketing team caught your eye. Someone had created a fake website using your company’s name and was tricking customers into sharing their login credentials. Worse still, they were using your logo and brand colors, making the website appear legitimate.
You felt the heat rising. Your company’s reputation was at risk.

The scene where the enemy attacks the brand’s banner while a knight stands in defense, shielding it with determination. Generated using Dall-E.
Luckily, SOCRadar’s Brand Protection (Digital Risk Protection) was already on the case. It had been monitoring not just websites but also social media channels, dark web forums, and other sources for any sign of brand impersonation. The fake website was flagged within minutes of going live, and with SOCRadar’s help, you were able to take it down before any major damage was done.
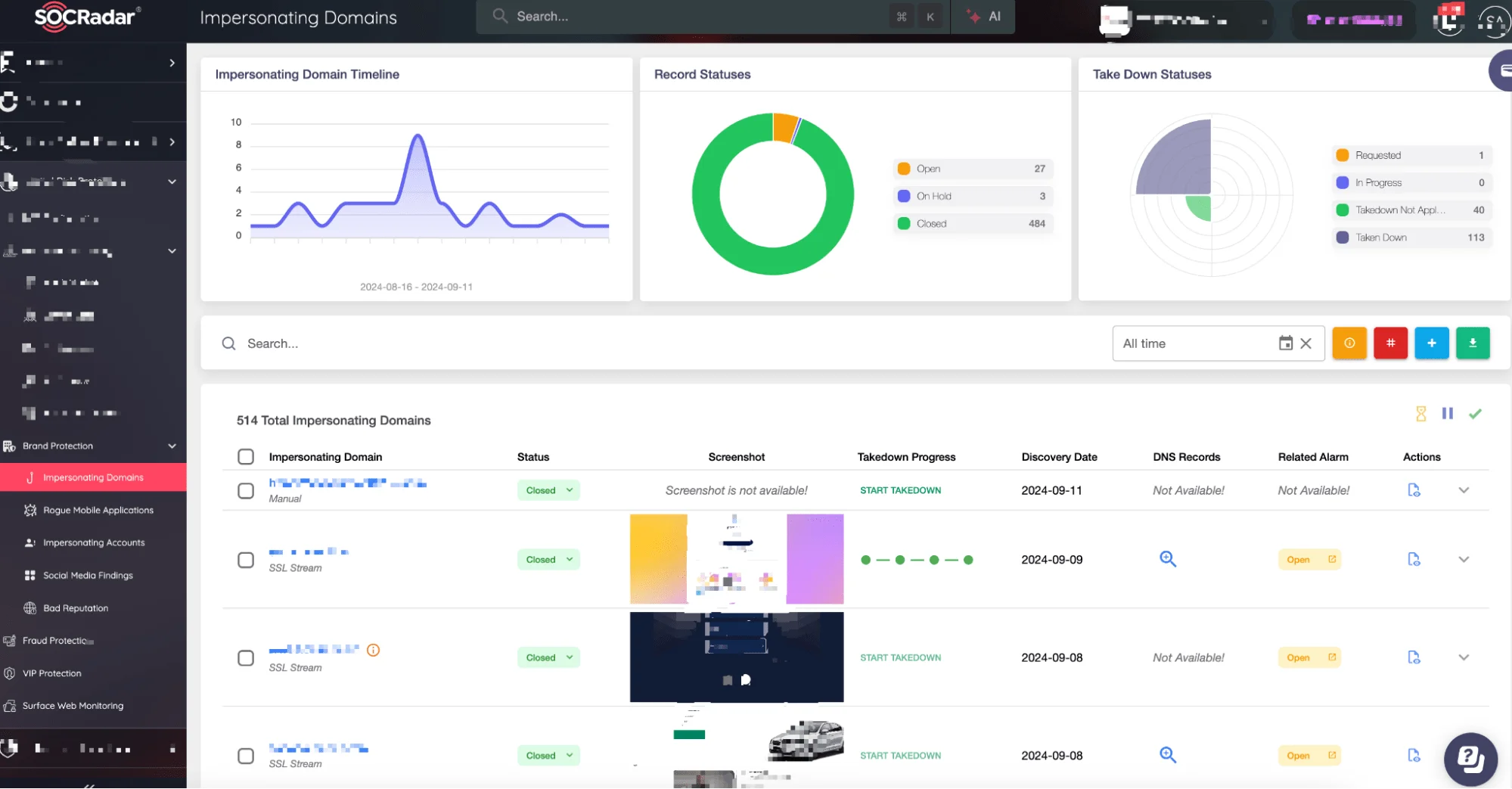
SOCRadar XTI, Brand Protection (Digital Risk Protection)
Takeaway: In the digital world, your brand is often your most valuable asset. Protecting it is not optional—it’s essential.
Securing the Supply Chain: Supply Chain Intelligence
But there was one more weak link in your cybersecurity armor—your supply chain. Your organization relied on dozens of third-party vendors, each with their own security vulnerabilities. According to the Cost of a Data Breach Report 2024 by IBM, approximately 40% of all breaches involved data distributed across multiple environments. This meant that your partners were just as much of a risk as internal assets.

The visual depiction of supply chain with a medieval theme, featuring fortified trade routes protected by knights and magical barriers. Generated using Dall-E.
That’s where SOCRadar’s Supply Chain Intelligence came in. It provided continuous monitoring of your vendors and partners, assessing their security postures and flagging any vulnerabilities that could impact your business.
With real-time risk scoring, you could see which suppliers were most vulnerable to attack and proactively work with them to mitigate risks. You even identified a critical vulnerability in a third-party SaaS provider, allowing you to take action before it impacted your systems.
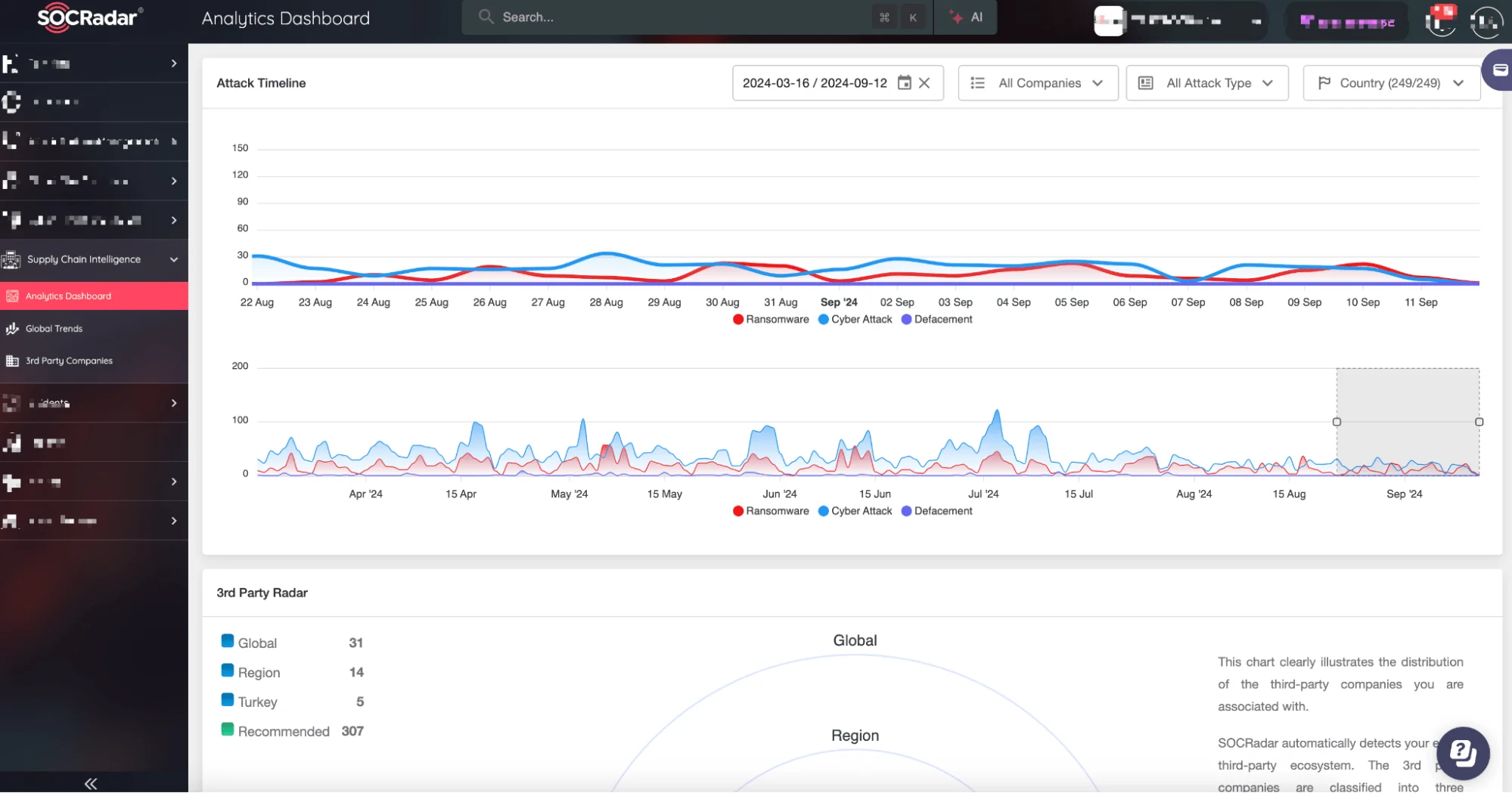
SOCRadar XTI Supply Chain Intelligence
Insight: The security of your supply chain is the security of your business. SOCRadar helped you ensure that every link in the chain was strong.
The Final Verdict: Use the Power of Extended Threat Intelligence (XTI)
As the months went on, your role as CISO became less about fighting fires and more about building a fortress around your organization. SOCRadar Extended Threat Intelligence (XTI) equipped you with the tools to see the full scope of your attack surface, monitor dark web activities, stay ahead of evolving cyber threats, protect your brand, and secure your supply chain.

Their handshake highlights unity and collaboration in leading and securing the kingdom. Generated using Dall-E.
You weren’t just reacting to threats anymore—you were preventing them before they had a chance to cause harm.
According to recent reports, cybercrime is expected to cost the world $10.5 trillion annually by 2025, highlighting the increasing need for platforms like SOCRadar . SOCRadar’s comprehensive approach helps organizations mitigate those financial risks effectively.
SOCRadar Extended Threat Intelligence (XTI) wasn’t just a platform. It was your strategic partner in cybersecurity, enabling you to protect your company’s digital assets in a rapidly evolving threat landscape. And the best part? Your team wasn’t overwhelmed by data anymore. With automated threat detection, advanced machine learning, and actionable insights, you had everything you needed to secure your organization effectively.
Handle the complexities of today’s cybersecurity landscape, ensuring that your digital assets are protected from every angle.





































