
Major Cyber Attacks in Review: September 2024
September 2024 saw a wave of major cyber attacks hitting critical sectors. BingX and Indodax, two prominent cryptocurrency platforms, suffered combined losses of over $66 million. The healthcare sector wasn’t spared from concerning news, as it was revealed that 3.1 million individuals were affected in the Medicare MOVEit data breach.
With other significant attacks targeting the financial, public, and social sectors, this month’s incidents highlight the growing threat across industries.
$44 Million in Cryptocurrency Stolen from Singaporean Platform BingX
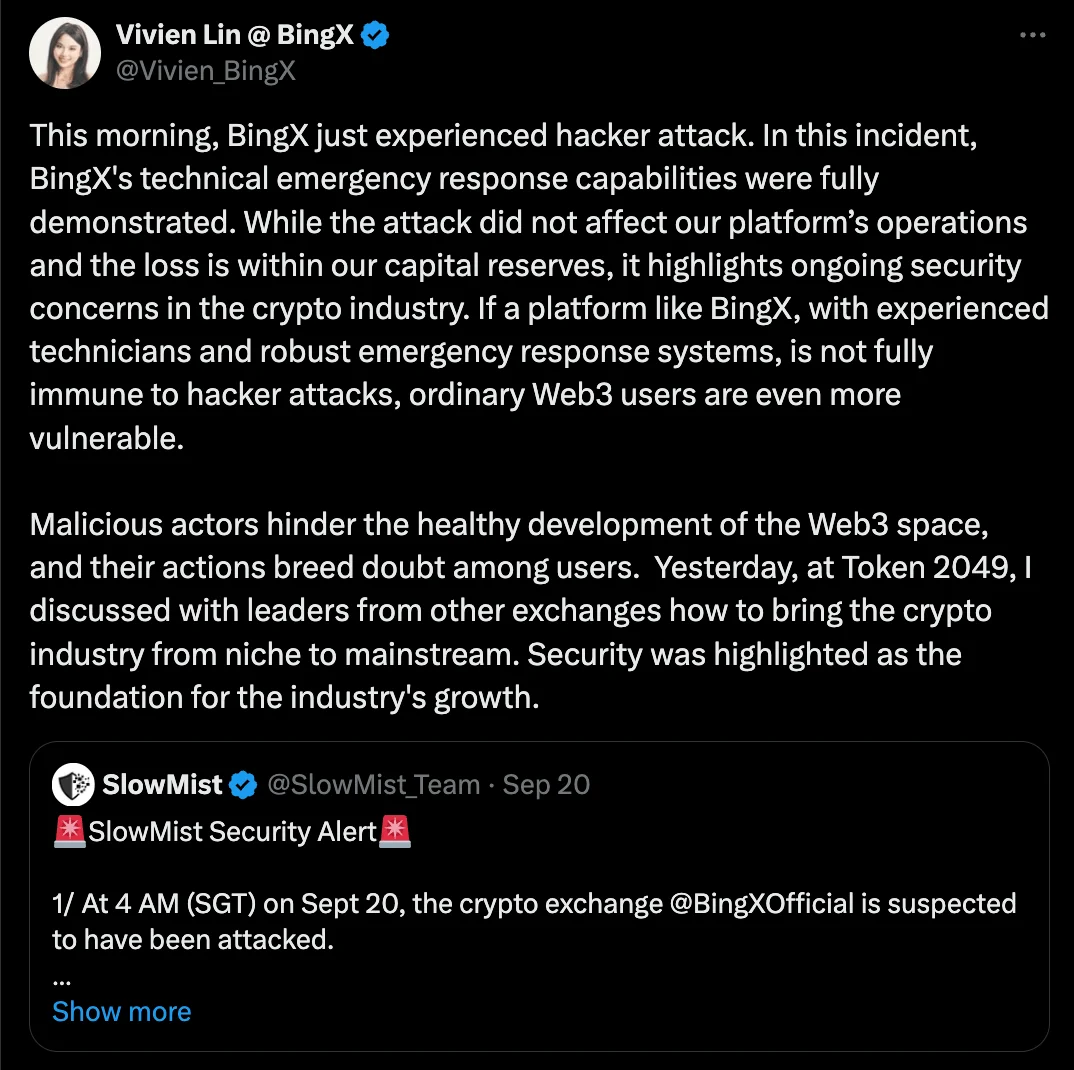
BingX, a Singaporean cryptocurrency platform, confirmed that over $44 million was stolen in a cyberattack. Blockchain security firms first noticed millions of dollars flowing out of BingX’s accounts before the platform announced a shutdown for “wallet maintenance.” BingX later acknowledged that abnormal network access signaled a hacker attack on its hot wallet.
Tweet from BingX’s Chief Product Officer (X)
Emergency measures were taken immediately, including suspending withdrawals and transferring assets. While the platform initially reported a “small” loss, a more detailed audit conducted with the help of blockchain security firm SlowMist revealed losses totaling around $44.7 million. Other estimates suggest the amount could be as high as $48 million.
BingX reassured users that it would fully compensate the losses using its own capital and that the attack will not affect its overall business operations.
Learn about the latest threats in the cryptocurrency and NFT space with SOCRadar’s 2024 Cryptocurrency & NFT Threat Landscape Report.
TfL Required 30,000 Employees to Reset Passwords After Cybersecurity Breach
Transport for London (TfL) mandated that all 30,000 of its employees attend in-person appointments to verify their identities and reset their passwords following a cybersecurity breach disclosed earlier this month. The breach affected internal systems and online services, but not transportation operations.

A security breach at Transport for London (TfL) affected 30,000 employees
Initially, TfL reassured the public that no customer data had been compromised. However, later updates confirmed that customer data, including names, contact details, and addresses, was exposed. Additionally, attackers accessed employee directory data, such as email addresses and job titles, though no evidence of compromised banking or sensitive personal data was found.
Indonesian Crypto Exchange Indodax Paused Operations After $22 Million Theft
Indodax, Indonesia’s largest cryptocurrency exchange with over 6 million users, halted operations after detecting a security breach that led to the theft of $22 million in various cryptocurrencies. The stolen assets included 25 Bitcoins worth $1.4 million and $14 million in Ethereum.
Indodax assured users they will be reimbursed for any lost funds and warned customers to stay vigilant against scammers exploiting the situation.
Blockchain security firm SlowMist ruled out the possibility of a compromised hot wallet, suggesting that the platform’s withdrawal system may have been hacked.

Crypto exchange firm Indodax experienced a hacking incident that led to $22 million theft
Fortinet Confirmed 440GB Data Theft from Its Sharepoint File Server
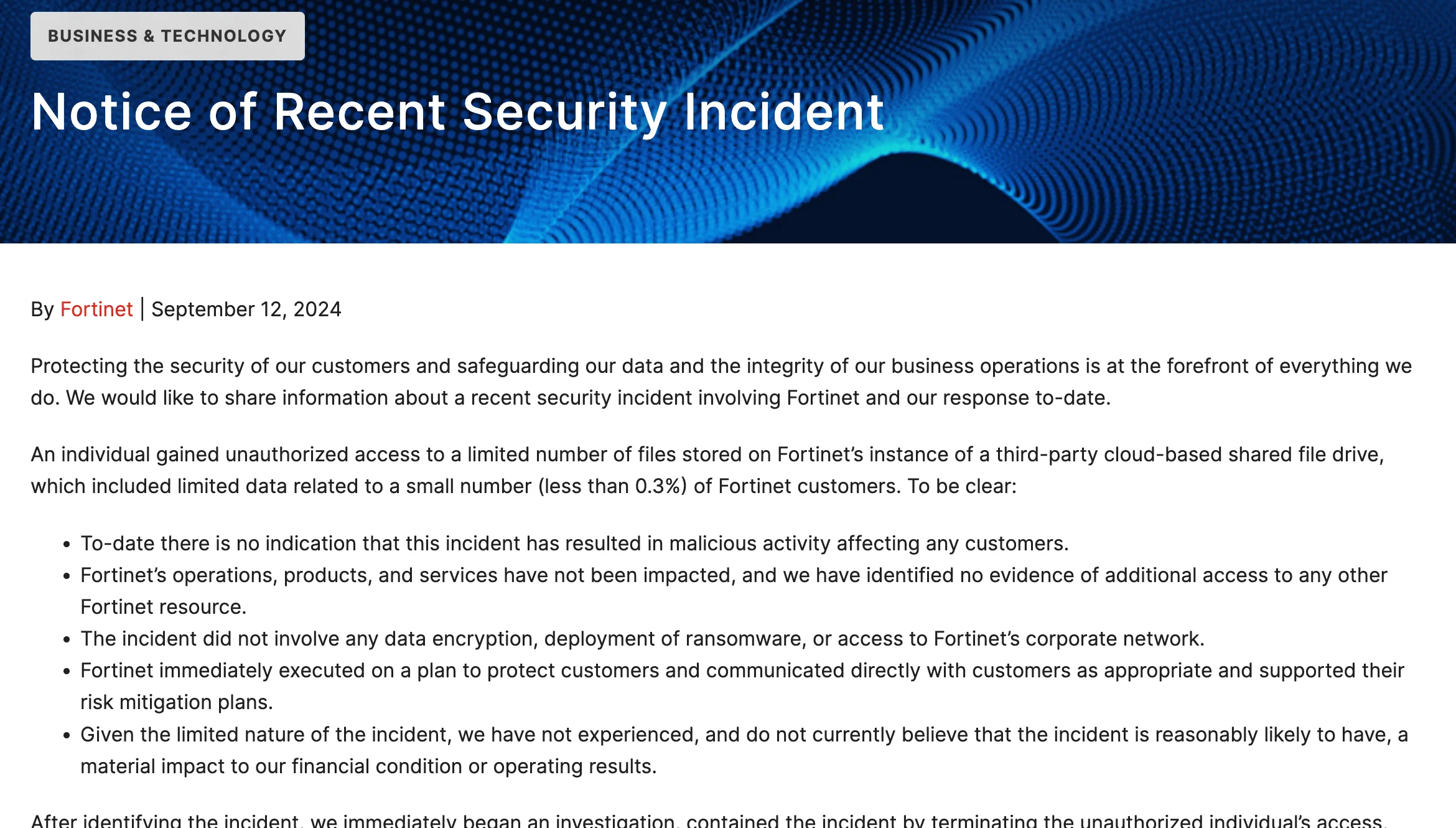
Fortinet has confirmed a data breach after a hacker, going by the alias “Fortibitch,” claimed to have stolen 440GB of files from the company’s Microsoft Sharepoint server. The hacker posted credentials on a hacking forum, allowing others to access the stolen data.
Fortinet stated that the breach involved unauthorized access to a third-party cloud-based shared file drive, affecting less than 0.3% of its customers.
Security incident notice by Fortinet
While specific data types were not disclosed, Fortinet reassured that no ransomware or encryption was involved, and its corporate network was not accessed.
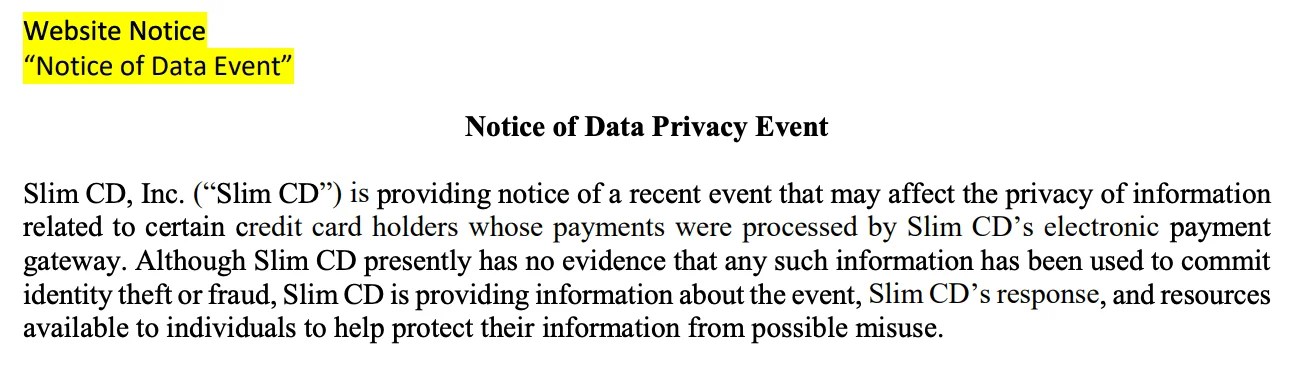
Slim CD Breach Exposed Credit Card Data of 1.7 Million Individuals
Payment gateway provider Slim CD has reported a data breach that exposed the credit card and personal information of nearly 1.7 million individuals.
Hackers accessed the company’s network from August 2023 until June 2024, with credit card data potentially compromised over two days in June 2024. The leaked data included full names, physical addresses, credit card numbers, and expiration dates. While the CVV was not exposed, the risk of credit card fraud remains.
Slim CD has since enhanced its security measures and advised affected individuals to monitor their accounts for suspicious activity. Despite the severity of the breach, no identity theft protection services were offered.
See the full incident notice by Slim CD here
3.1 Million Impacted in Medicare MOVEit Data Breach
The Centers for Medicare & Medicaid Services (CMS) and Wisconsin Physicians Service Insurance Corporation (WPS) revealed that personal data of 3.1 million individuals was exposed in the MOVEit breach connected to the Clop ransomware group. Compromised data included names, Social Security numbers (SSNs), Medicare account details, and health insurance information.
Initially, 946,801 individuals were confirmed as affected, but the total grew after a review by WPS in 2024. CMS is providing new Medicare cards to impacted recipients and encouraging them to use free credit monitoring services.

CMS and WPS report that 3.1 million individuals’ PII was exposed during MOVEit incidents
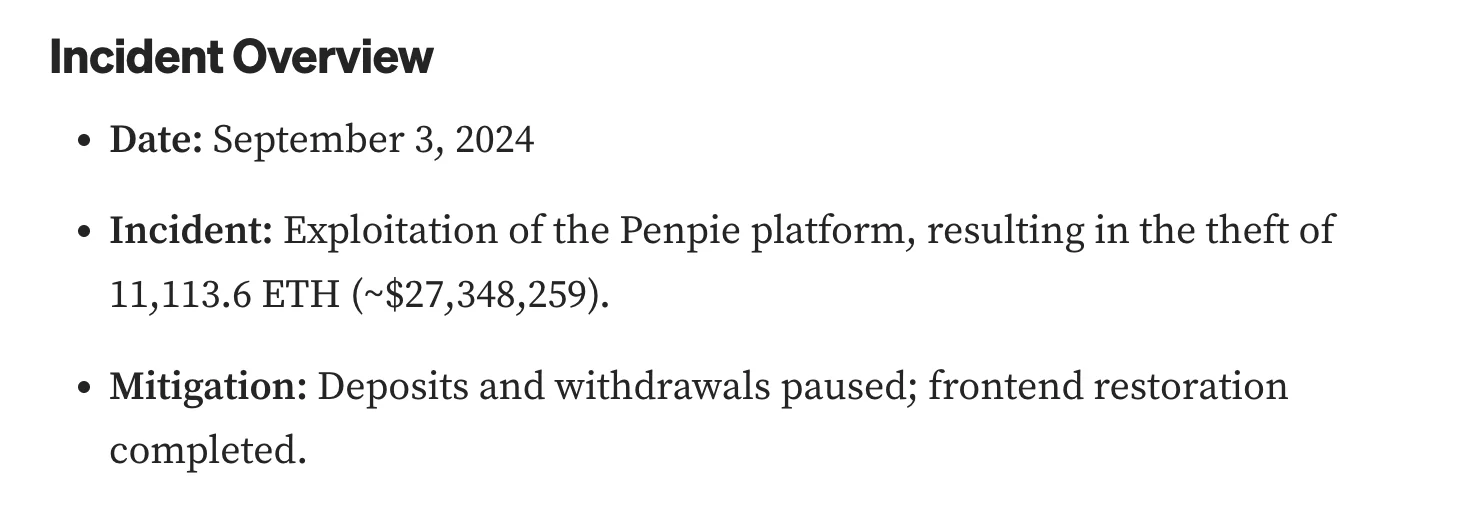
$27 Million Stolen in Penpie DeFi Hack Exploiting Vulnerability
Hackers stole approximately $27 million worth of Ethereum from the Penpie decentralized finance (DeFi) protocol, exploiting a vulnerability in the platform. Penpie confirmed the theft of 11,113.6 ETH, leading them to pause deposits and withdrawals.
See the incident post-mortem report here
The attack leveraged a reentrancy protection vulnerability in Penpie’s staking system, allowing the hacker to manipulate fake Pendle markets and siphon funds using flash loans.
Despite immediate actions by Pendle’s security system to halt the exploit, Penpie suffered the loss before mitigation could prevent further damage. The company filed reports with both Singapore police and the FBI’s Internet Crime Complaint Center (IC3), requesting negotiations with the hacker for the return of the funds, but no progress has been made.
Penpie acknowledged a missed vulnerability from a previous audit and pledged to conduct a full system review before resuming operations, while also developing a compensation plan for affected users.
Hacker Leaked Data of Over 390 Million VK Users on Breach Forums
A hacker known as “HikkI-Chan” leaked personal data of more than 390 million VK users on Breach Forums, a notorious cybercrime platform. The breach, which occurred in September 2024, includes the full names, cities, countries, and profile image URLs of 390,425,719 VK users, though no passwords or phone numbers were included. The data is reportedly over 27 GB in size and primarily in Russian.
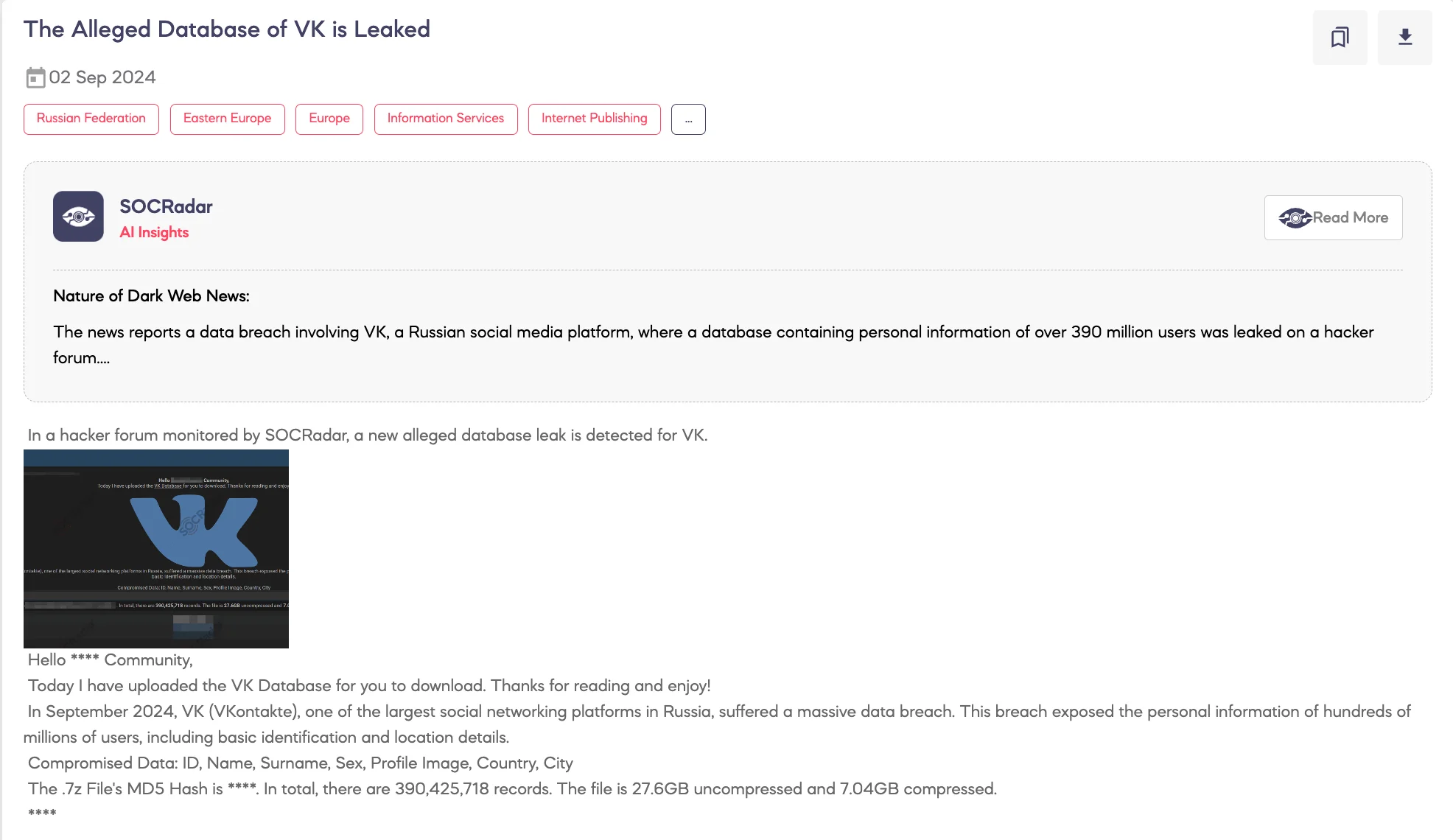
A notice of the threat actor’s post on VK breach (SOCRadar Dark Web News)
VK, one of Russia’s largest social media platforms, functions similarly to Facebook. The hacker revealed that this was a “second-order” breach, meaning VK’s servers were not directly compromised. Instead, the data was obtained through a third-party breach that exposed VK user details.
With SOCRadar Dark Web News, you can stay updated on the latest discussions in Deep and Dark Web forums, such as the VK incident, and also monitor hacker activity on Telegram channels.
Safeguard Your Business from Data Breaches with SOCRadar XTI
The risk of data breaches and security incidents continues to grow across all industries. With attackers constantly finding new ways to exploit vulnerabilities, organizations face a challenging task of keeping their systems secure. Many of these threats, from stolen credentials to exposed data on the dark web, can go unnoticed until it’s too late. Proactive protection and real-time monitoring are now essential to prevent and respond to breaches before they escalate. This is where having an advanced threat intelligence platform becomes critical.
The SOCRadar Extended Threat Intelligence (XTI) platform provides comprehensive cybersecurity solutions, combining Threat Intelligence, Digital Risk Protection, and Attack Surface Management. It continuously monitors external threats, dark web activities, and potential vulnerabilities, offering real-time alerts and actionable insights.
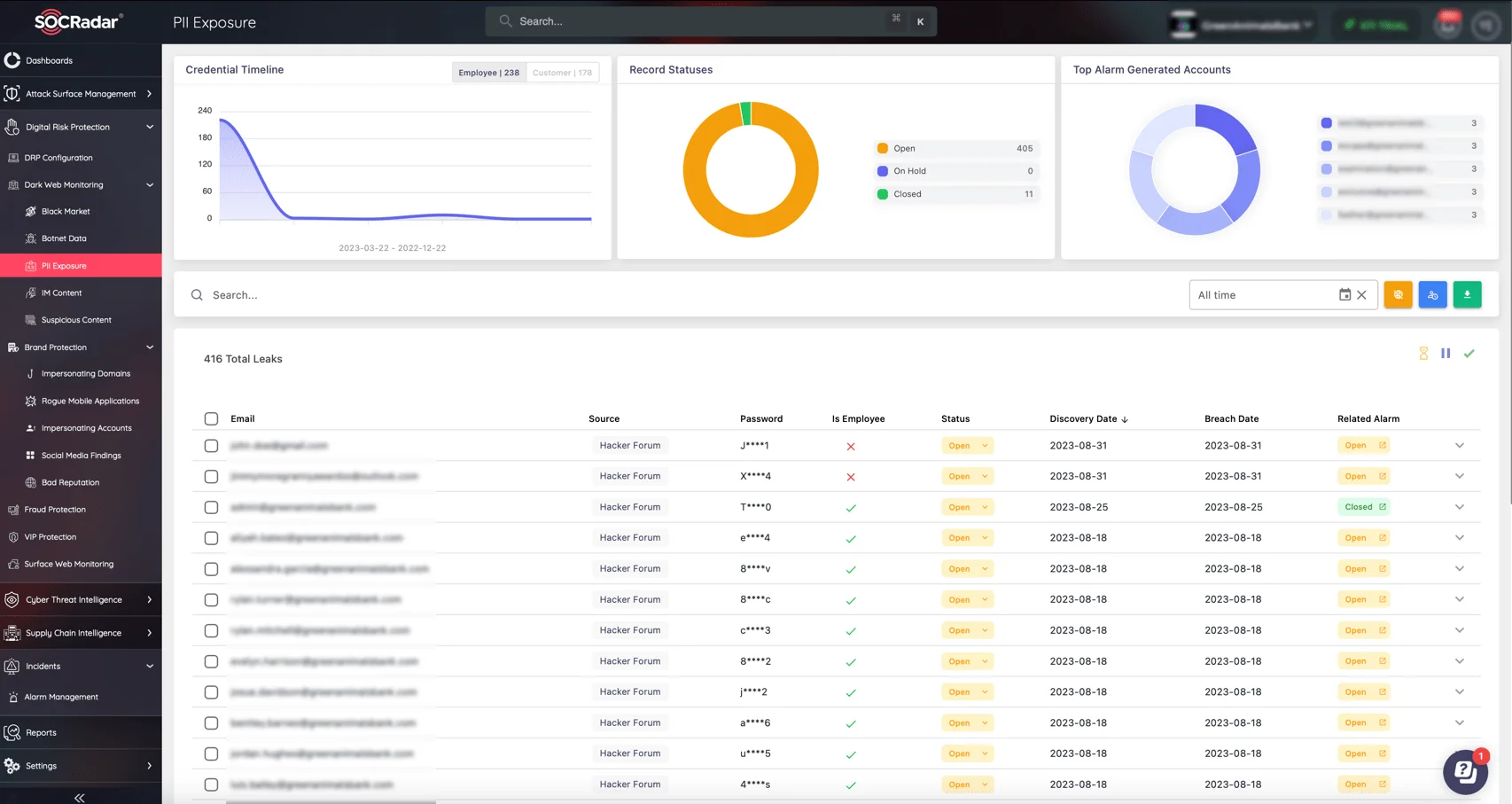
SOCRadar’s Dark Web Monitoring
In combat against data breaches, SOCRadar’s Digital Risk Protection (DRP) module offers early detection of data leaks and exposure of sensitive information across dark web channels and hacker forums. By monitoring for compromised assets, businesses can be alerted to breaches before they escalate, helping to mitigate the damage and protect users from further exploitation.




































