
Global Cybersecurity Coalition Brings Down Major Infostealer Malware Operations
In a recent milestone for international cybersecurity, authorities from around the world successfully dismantled the Redline and Meta infostealer malware networks. Dubbed as Operation Magnus, orchestrated by Eurojust with Europol support, this operation aimed to disrupt large-scale cybercrime operations exploiting these malware types to target millions of individuals globally. With extensive coordination across countries, law enforcement agencies have effectively put an end to some of the most significant infostealer campaigns to date.

Operation Magnus (Source)
The Infostealer Threat: Redline and Meta Malware
Redline and Meta infostealers are notorious malware types designed to infiltrate devices and extract sensitive data, including login credentials, banking information, and payment card details. Once a device is infected, these infostealers actively search for stored information and transmit it back to cybercriminals, who then sell or use the data for illicit gain. Redline, in particular, is a popular tool in underground forums, offering cybercriminals a cost-effective way to acquire a steady stream of valuable information.
The Meta infostealer operates similarly but with specific enhancements that improve data extraction efficiency and broaden its target range. Both are distributed widely, often through phishing emails, malicious downloads, and compromised websites, making them highly effective at reaching unsuspecting victims.
Key Strategies Behind the Operation
The international coalition employed a range of tactics to bring down these malware operations. Coordinated raids on servers hosting the malware infrastructure were a central focus, alongside seizing financial assets connected to the malware operators. By confiscating and neutralizing these assets, the coalition effectively cut off the cybercriminals’ main operational resources, crippling their ability to continue stealing data.
According to Eurojust, the cooperation between judicial and law enforcement bodies across several countries was vital in addressing this sophisticated network, marking a significant step in global cybersecurity efforts.
Agencies released a video providing a “final update” for Redline and Meta users, revealing they have obtained account credentials, IP addresses, and other personal data. This indicates that investigators possess evidence likely to lead to arrests. Authorities also gained access to malware source code and infrastructure, suggesting a shared origin between the two. The Dutch police are continuing their strategy of warning cybercriminals through direct messages and forum posts, emphasizing their surveillance efforts. More updates on potential arrests are expected tomorrow.
Impact on the Underground Market for Stolen Data
The success of this operation disrupts the supply chain of stolen data on the dark web. Infostealers like Redline and Meta fuel a thriving underground market where stolen credentials and sensitive information are bought and sold. With millions of users affected, the dismantling of these malware networks could significantly impact cybercriminal access to fresh data, at least in the short term. The decrease in fresh data can be expected to reduce further cyber crimes and may also lead to inflated prices in dark markets.
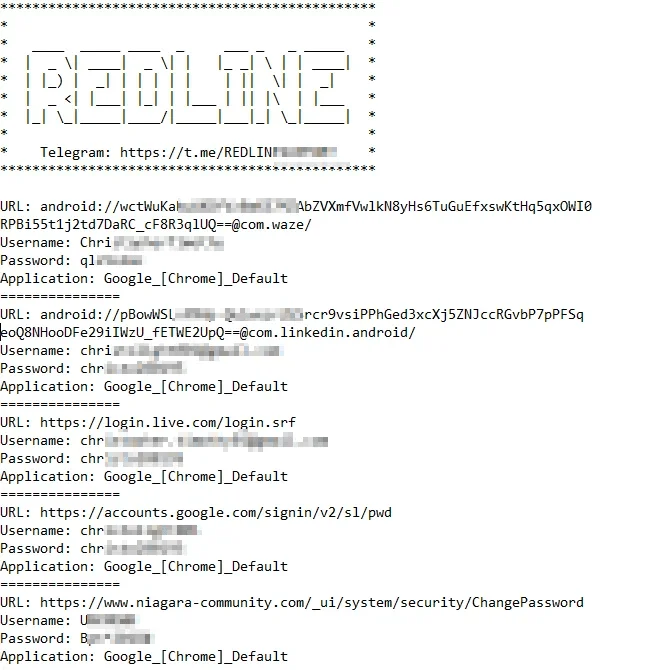
Compromised accounts of a machine through RedLine, the top log generating infostealer malware
Stealer logs—collections of stolen data—are a primary source for cybercriminals seeking to infiltrate organizations or launch further attacks. As detailed by SOCRadar, infostealers have become a popular choice among cybercriminals due to their efficiency and affordability, and the Redline and Meta takedown could signal a temporary scarcity in this data flow.
For an in-depth look at the role of stealer logs in cybercrime, refer toSOCRadar’s stealer logs overview and analysis of stealer anatomy.
Conclusion: A Temporary Win in a Continuous Battle Against Cybercrime
The recent takedown of the Redline and Meta infostealer malware operations marks a significant achievement in the ongoing battle against cybercrime. While this coordinated effort has temporarily disrupted the flow of stolen data and hampered the activities of these notorious infostealers, it is crucial to remember that the landscape of cyber threats is ever-evolving. Cybercriminals are continuously developing new strategies and tools to exploit vulnerabilities, making it essential for individuals and organizations to stay vigilant.
To effectively combat these persistent threats, proactive measures must be taken. This is where SOCRadar comes into play. With advanced threat intelligence solutions, SOCRadar equips businesses with the tools needed to monitor, detect, and respond to cyber threats in real time. By leveraging features such as Dark Web Monitoring, organizations can stay ahead of emerging threats, ensuring they are well-prepared against data breaches and malware attacks.
Where cyber threats are increasingly sophisticated, investing in proactive cybersecurity measures is not just prudent but necessary. SOCRadar’s comprehensive suite of products provides insights into threat landscapes, helping organizations understand their vulnerabilities and fortifying their defenses against potential breaches.
The fight against cybercrime is a continuous one, but with the right tools and intelligence, businesses can safeguard their assets and protect their data from the ever-present threats lurking in the digital world.




































