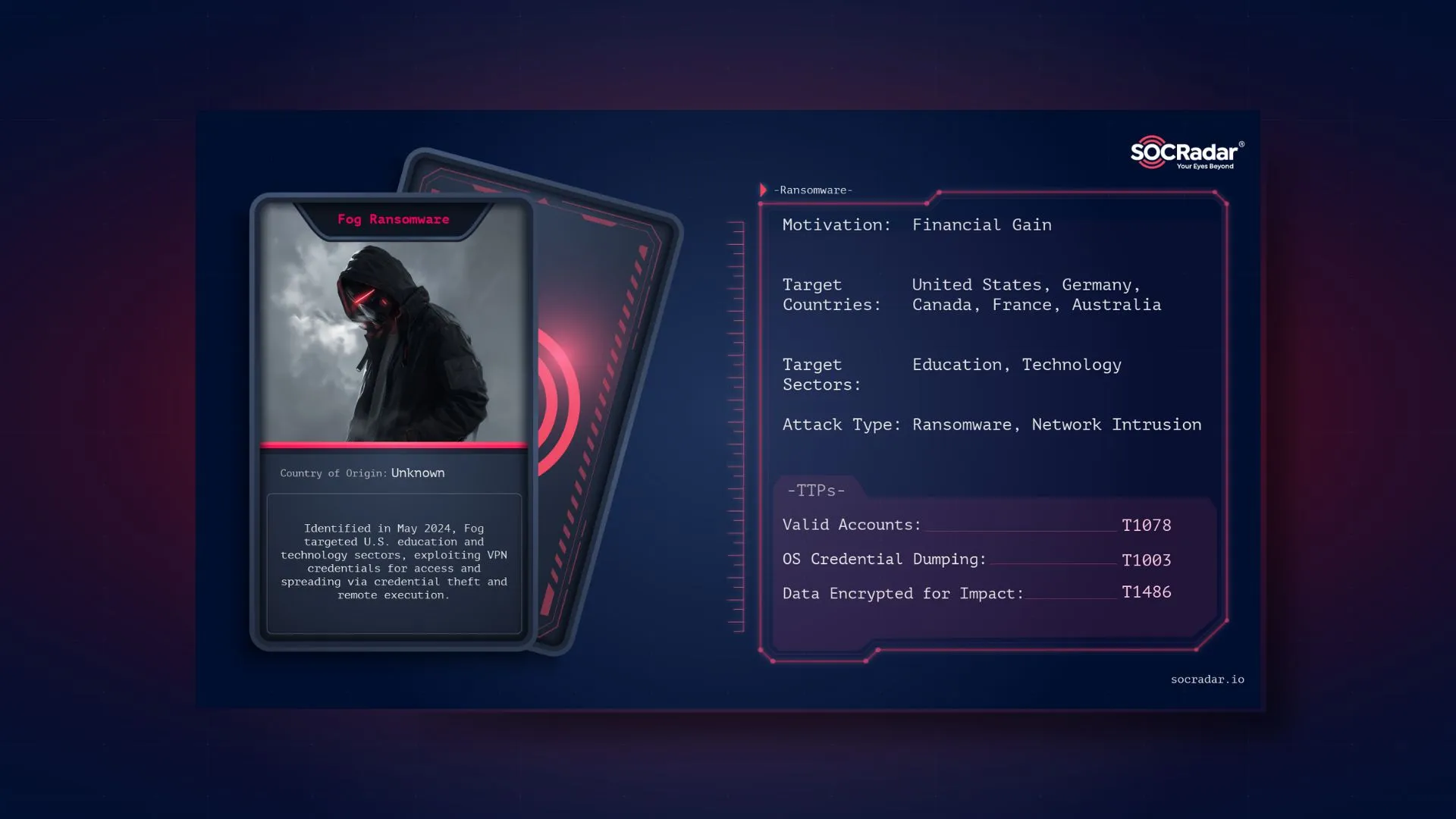
Dark Web Profile: Tropic Trooper (APT23)
Tropic Trooper, also known as Pirate Panda and APT 23, is a Chinese state-sponsored cyber threat group that has been active since 2011. Specializing in espionage, the group primarily targets sensitive sectors like government, healthcare, and transportation. Their operations have been focused on areas such as Taiwan, Hong Kong, and the Philippines, where they employ advanced tactics to compromise networks and steal valuable information.

Threat actor card of Tropic Trooper
Who is Tropic Trooper?
Tropic Trooper is a cyber espionage group attributed to Chinese state-sponsored activities, primarily active since 2011. The group operates under various names, including Pirate Panda, APT 23, Iron, KeyBoy, Bronze Hobart, Earth Centaur. They are known for their sophisticated techniques and targeted attacks, often focusing on sectors crucial to national interests, such as government, telecommunications, and technology. With a strong emphasis on intelligence gathering, Tropic Trooper utilizes social engineering and advanced malware to infiltrate networks and extract sensitive data. Their operations typically align with the geopolitical interests of China.
Their attacks frequently involve the infiltration of networks through spear-phishing campaigns, which are designed to deceive individuals into providing access to confidential data or systems. Over the years, Tropic Trooper has adapted its tactics, demonstrating a keen ability to innovate and evade detection, which makes them a persistent threat in the cyber landscape. Their targeted approach and technical prowess underscore their significance as a key player among state-sponsored threat actors.
How Does Tropic Trooper Operate?
Initial Access
Tropic Trooper initiates attacks primarily through spear-phishing campaigns, carefully crafted with extensive social engineering to appeal directly to their targets. These emails often contain malicious attachments, such as Microsoft Office files or PDFs, or embed links that, once clicked, lead to websites hosting exploit kits.
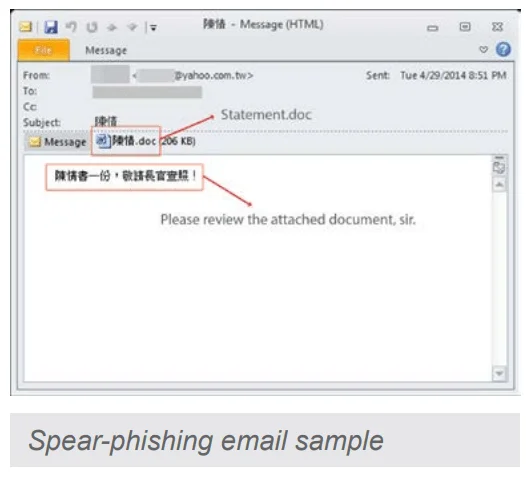
Point of entry, a malicious doc (TrendMicro)
They exploit common application vulnerabilities, including those in Microsoft Office, to execute malware payloads that establish a foothold in the victim’s system. Tropic Trooper’s spear-phishing emails are customized, often incorporating language, subject matter, and scenarios relevant to the target’s environment to maximize the chances of engagement. This calculated initial access strategy enables Tropic Trooper to breach networks within government, healthcare, and high-value sectors across Southeast Asia.
Thus, they not only gain access through phishing, but they can also exploit Web server vulnerabilities, especially Exchange Server, and create attack vectors using Webshell.
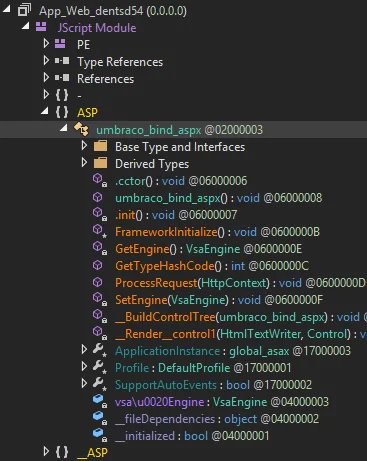
A malicious module was found inside Umbraco CMS – an open source .NET content management system- on the compromised server (Securelist)
Tools used in 2021 and 2024 attacks in this step:
Fscan: Used for vulnerability scanning, detecting open ports, and available services on target machines. Tropic Trooper also uses an ICMP-based script to identify accessible devices for exploitation.
Swor: Deployed for penetration testing, it facilitates initial access and includes mimikatz and FRP for additional exploitation.
Persistence
Following initial access, Tropic Trooper leverages sophisticated custom malware, including TClient, and Yahoyah ChinaChopper, designed for persistence. These tools allow Tropic Trooper to maintain continuous access to compromised systems, systematically collecting, encrypting, and transmitting sensitive data to their servers over long periods. To avoid detection, they employ advanced obfuscation and encryption techniques, modifying their malware periodically to evade signature-based security measures. This persistent access not only secures a stable position within the network but also supports Tropic Trooper’s broader espionage objectives, allowing them to collect intelligence and track target activity over time.
Malicious function implementing China Chopper registered as a callback function (Securelist)
Tools used:
ChinaChopper: A small but powerful web shell used for persistent access, allowing Tropic Trooper to maintain control even if other tools are detected.
YAHOYAH: Ensures persistence by encrypting its payload, making it harder to detect and allowing the attacker to reload it as needed.
PoisonIvy: Ensures persistence through autostart execution and system modifications that help re-establish access upon reboot.
Privilege Escalation
Once established, Tropic Trooper seeks to elevate its privileges within the infected network. They exploit vulnerabilities in widely used applications or leverage privilege escalation exploits tailored to the target’s system environment. By doing so, they transition from low-level user access to higher-level administrative permissions, granting them enhanced control over critical network resources and security configurations. This escalation allows them to disable security controls selectively and to navigate the environment with greater freedom, ultimately facilitating deeper infiltration and access to high-value data assets.
In one instance in 2024, Kaspersky stated that attackers utilized DLL search-order hijacking to implant backdoor loaders (datast.dll and VERSION.dll). The process involves planting malicious DLLs alongside legitimate executables vulnerable to search-order hijacking, enabling the malicious DLL to load as if it were part of the original program. Once loaded, datast.dll decrypts and executes the shellcode for further malware stages, leveraging functions within a secondary DLL to conceal its activities. The attackers reportedly employed Umbraco web shells to place these malicious files on compromised servers.
Code stub responsible for decrypting the next stage (Securelist)
Tools used:
ShadowPad: Utilized for privilege escalation through dynamic-link library injection, bypassing security controls for enhanced access.
Lateral Movement
Upon achieving elevated privileges, Tropic Trooper initiates lateral movement, systematically navigating the network to extend their reach across interconnected devices and servers. Using reconnaissance tools, they map network topologies, identify accessible resources, and pinpoint potential vulnerabilities in the organization’s infrastructure. They then employ various propagation techniques, including credential harvesting and exploitation of network misconfigurations, to spread to additional systems. By doing so, Tropic Trooper ensures that they retain access to multiple points within the network, allowing them to re-establish connections even if detection efforts uncover some parts of their operation.
Tools used:
Neo-reGeorg: A SOCKS5 proxy tool, allowing Tropic Trooper to pivot across networks and evade network security controls.
FRPC (Fast Reverse Proxy Client): Assists in lateral movement by exposing local servers behind firewalls.
Chisel: Facilitates TCP/UDP tunneling, allowing traffic forwarding across the compromised network.
Data Exfiltration
Data exfiltration is the final objective, as Tropic Trooper systematically targets and extracts classified or strategically valuable information, including government documents, healthcare records, and military data. Once they’ve mapped out the network and identified high-priority assets, they employ data compression, encryption, and stealthy data transfer methods to exfiltrate information undetected. Often, exfiltration is staged to avoid triggering network alarms; Tropic Trooper minimizes data volumes or utilizes obscure channels to avoid standard detection protocols. Through encrypted tunnels, they transfer this intelligence to remote command and control servers, focusing on data that supports their long-term intelligence and espionage goals in political, economic, and security domains.
Tools used:
SharpHound: Maps Active Directory relationships and identifies key systems and paths for further infiltration.
USBferry: Used for network discovery and spreading across devices connected through removable media.
RClone: Syncs files to and from cloud storage for large-scale data exfiltration.
BITSAdmin: Transfers data over alternative protocols like BITS Jobs to avoid detection.
How Have Their Tactics Changed?
After 2020, two comprehensive reports, one from TrendMicro and another from Kaspersky, have been released to the community. The differences in each report’s approach highlight the ongoing evolution of the group’s tactics and strategies. Between 2021 and 2024, Tropic Trooper significantly expanded and evolved its operations. Originally focused on government, healthcare, and high-tech sectors in regions like Taiwan, Hong Kong, and the Philippines, Earth Centaur broadened its geographical and strategic scope by 2023, targeting transportation, governmental agencies, and human rights organizations in Southeast Asia and the Middle East. This shift included a focus on sensitive geopolitical areas and issues, like those involving Middle Eastern governments and human rights organizations linked to ongoing conflicts.
During this period, Tropic Trooper’s tactics also became more sophisticated. They continued using known exploits for entry—particularly in vulnerable Microsoft Exchange and Adobe ColdFusion servers—and employed a revamped set of malware tools. For example, in 2024, they introduced the “Crowdoor” backdoor variant to deliver Cobalt Strike payloads, enabling them to establish persistent access and gather sensitive information covertly. This is alongside the continued use of Quasar RAT, a tool they’d utilized in previous years but with increased efficiency through enhancements like custom decryption algorithms and DLL side-loading.
Their technical approach increasingly mirrors advanced red-teaming techniques, which reflect an evolution toward a more agile, adaptable operation style, enabling them to bypass network security more effectively. Their goals, however, remain consistent with prior espionage-focused activities, with an emphasis on internal data collection from compromised networks for long-term strategic use.
What Are Their Targets?
Tropic Trooper’s attacks are concentrated on highly sensitive sectors, primarily in Southeast Asia. Government institutions, healthcare organizations, and military entities in Taiwan, the Philippines, and Hong Kong have been frequent targets. Their operations focus on accessing data that could provide strategic advantages in political, economic, or military arenas. By compromising governmental networks, Tropic Trooper aims to gather intelligence that informs national security interests, while attacks on healthcare sectors often seek to obtain sensitive personal and medical records, which can further their political or tactical objectives.
Government Institutions
Tropic Trooper’s most common targets are government agencies and ministries. By infiltrating these networks, they gather data that could serve national intelligence or political strategies, focusing on sectors involved in policy-making, economic development, and international relations.
Healthcare and Research Organizations
Healthcare facilities and research centers are targeted for their valuable data on citizens, medical records, and scientific advancements. Tropic Trooper leverages this information to analyze population health data or disrupt public health infrastructure. Attacks on these sectors are often strategic, serving geopolitical or economic motives aligned with the interests of their sponsors.
Military Networks and Infrastructure
The group also has a history of breaching military networks, seeking out plans, defense strategies, and communications data. These intrusions into defense sectors are intended to obtain intelligence on military capabilities, troop movements, and strategic defense postures, providing critical information that could be advantageous in regional security dynamics.
How Organizations Can Defend Against Tropic Trooper
Organizations facing potential threats from Tropic Trooper can employ a comprehensive defense strategy to detect, prevent, and respond to cyber incidents. By implementing the following security measures, companies can strengthen their defenses and reduce the likelihood of compromise:
-
Enhanced Email Security
Since Tropic Trooper frequently relies on spear-phishing emails to initiate attacks, organizations should implement robust email filtering solutions to detect and block malicious emails. Training employees to recognize phishing attempts and report suspicious emails is essential to prevent initial access.
-
Access Control and Privileged Account Management
Limiting user privileges based on job roles and implementing Multi-Factor Authentication (MFA) can prevent Tropic Trooper from easily gaining unauthorized access to sensitive systems. Privileged Account Management (PAM) tools can monitor and secure high-level access accounts, reducing the likelihood of lateral movement within the network.
-
Network Segmentation
To limit the spread of an intrusion, organizations should segment their networks by grouping systems with similar functions together and restricting communication between them. This containment measure can prevent threat actors from easily moving between different network segments, reducing the overall impact of a breach.
-
Endpoint Detection and Response (EDR)
Deploying advanced EDR solutions on endpoints allows security teams to monitor unusual activity, detect malware, and analyze suspicious files in real time. EDR tools offer insight into endpoint activity, aiding in the early detection of Tropic Trooper’s custom malware and persistence mechanisms.
-
Regular Patch Management
Organizations should prioritize regular software updates and patches for all systems and applications. Addressing known vulnerabilities can limit potential attack vectors exploited by groups like Tropic Trooper, reducing the risk of exploitation and unauthorized access.
-
Network Monitoring and Intrusion Detection
Continuous network monitoring and Intrusion Detection Systems (IDS) can help detect and mitigate unauthorized traffic within the organization’s infrastructure. By identifying abnormal traffic patterns or unauthorized access attempts, security teams can respond swiftly to potential threats, reducing the risk of data exfiltration.
-
Incident Response Plan and Cyber Threat Intelligence (CTI)
Having an incident response plan tailored to Advanced Persistent Threats (APTs) allows security teams to respond effectively if Tropic Trooper infiltrates the network. Cyber threat intelligence (CTI) teams can enhance this plan by staying informed of Tropic Trooper’s latest TTPs, enabling proactive defense and faster identification of attack patterns.
SOCRadar’s Extended Cyber Threat Intelligence (XTI) offers support to organizations combating the evolving threat of threat actors like Troopic Trooper through a suite of advanced cybersecurity tools and services.
SOCRadar’s Operational Intelligence/Threat Actor Intelligence
Summary
Tropic Trooper remains a formidable and adaptive threat, continually targeting sensitive sectors across East Asia with sophisticated techniques and a long history of state-sponsored espionage. Known by various names, including Pirate Panda and APT 23, this group has honed its approach to employ advanced malware, spear-phishing tactics, and lateral movement strategies that enable them to infiltrate and extract valuable information from critical infrastructures. Their operations reflect a strategic focus aligned with China’s geopolitical interests, making them a key player in the cyber threat landscape.
To combat the persistent threat posed by Tropic Trooper, organizations must adopt a comprehensive cybersecurity framework. This should include enhanced email security, strict access controls, network segmentation, and advanced endpoint detection solutions. By fostering a proactive security culture and maintaining an updated incident response plan, organizations can significantly bolster their defenses against the sophisticated tactics employed by Tropic Trooper and similar state-sponsored actors.
MITRE ATT&CK Matrix
| Tactic | ID | Technique |
| Initial Access | T1190 | Exploit public-facing application |
| T1566.001 | Spear Phishing Attachment | |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell | |
| T1569.002 | System Services: Service Execution | |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| T1574.002 | Hijack Execution Flow: DLL Side-Loading | |
| T1505.003 | Server Software Component: Web Shell | |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| T1070.001 | Indicator Removal on Host: Clear Windows Event Logs | |
| T1027.002 | Obfuscated Files or Information: Software Packing | |
| T1218.011 | Signed Binary Proxy Execution: Rundll32 | |
| T1036.005 | Masquerading: Match Legitimate Name or Location | |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| T1552.002 | OS Credential Dumping: Credentials in Registry | |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| T1482 | Domain Trust Discovery | |
| T1083 | File and Directory Discovery | |
| Collection | T1005 | Data from Local System |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| T1095 | Non-Application Layer Protocol | |
| T1090.001 | Proxy: Internal Proxy | |
| Exfiltration | T1567.002 | Exfiltration to Cloud Storage |
| T1020 | Automated Exfiltration | |
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | |
| T1203 | Exploitation for Client Execution | |
| T1564.001 | Hide Artifacts: Hidden Files and Directories | |
| T1518.001 | Software Discovery | |
| T1082 | System Information Discovery | |
| T1016 | System Network Configuration Discovery | |
| T1049 | System Network Connections Discovery | |
| T1033 | System Owner/User Discovery | |
| T1204.002 | User Execution: Malicious File | |
| T1078.003 | Valid Accounts: Local Accounts |
Tools&Software and IoCs
| Tool Name | Purpose | Description |
| Fscan | Vulnerability Scanning | Scans for host status, ports, services, and exploits vulnerabilities. |
| Swor | Penetration Testing | A tool for deploying payloads like mimikatz, designed to evade detection. |
| Neo-reGeorg | Network Pivoting | Open-source SOCKS5 proxy used to pivot and evade security controls. |
| ByPassGodzilla | Web Shell Obfuscation | Encrypts web shells to avoid detection, associated with CVE-2023-26360. |
| SharpHound | Active Directory Discovery | Identifies relationships within an Active Directory environment. |
| FRPC | Intranet Penetration | Fast reverse proxy for exposing local servers behind NAT/firewalls to the internet. |
| Chisel | Intranet Penetration | Facilitates fast TCP/UDP tunneling. |
| RClone | Data Exfiltration | Command-line tool for syncing files with various cloud storage providers. |
| BITSAdmin | Job Management and Exfiltration | Manages BITS jobs for transferring files using unencrypted protocols. |
| KeyBoy | System Control | Uses various methods for executing commands and capturing credentials. |
| PoisonIvy | Remote Access | Provides capabilities for remote control and data exfiltration via various techniques. |
| ShadowPad | Remote Access and Data Exfiltration | A versatile malware with capabilities for communication, data transfer, and persistence. |
| USBferry | Data Gathering and System Discovery | Gathers information from local accounts and can replicate through removable media. |
| YAHOYAH | Data Management | Handles data exfiltration and obfuscation through various protocols. |
For the latest IoCs and YARA / Sigma Rules visit SOCRadar Platform’s Threat Actor Intelligence tab.