
Exploring the Top Vulnerabilities Exploited by State-Sponsored Threat Actors
While cyberattacks are a common concern for individuals and organizations alike, the shadowy realm of state-sponsored threat actors poses a uniquely ominous and formidable challenge. These adversaries, backed by the vast resources and strategic interests of their respective governments, operate in the dark corners of the internet, leveraging their technical prowess to wreak havoc on global scales.
State-sponsored threat actors, often the unseen hands behind sophisticated cyberattacks, represent a pervasive and persistent danger to national security, critical infrastructure, and sensitive data. Their motivations span a spectrum from espionage and political manipulation to economic gain and military advantage. Their capabilities are staggering, making it essential for us to delve into the heart of this topic, to understand the vulnerabilities they exploit, and to bolster our defenses.
This blog post aims to uncover some of the recent vulnerabilities exploited by state-sponsored threat actors. We will examine notable incidents to provide insights and guidance that will help individuals and organizations enhance their defenses against these clandestine digital adversaries.
Statistics Related to the Vulnerabilities Used By State-Sponsored Threat Actors
Alerts of nation-state activity targeting critical infrastructure surged from 20% in 2021 to 40% in 2022, according to the latest Microsoft Digital Defense Report, underscoring the growing threat posed by state-sponsored actors.
The Origin of Most State-Sponsored Threat Actors
The report identifies Russia, China, Iran, and North Korea as primary sources of state actors targeting organizations over the past year.
Geopolitical developments have molded the priorities and risk tolerance of these groups, leading to increased audacity and aggression. Russia, alongside its military actions in Ukraine, intensified its efforts to infiltrate critical infrastructure. Iran aggressively targeted U.S. critical infrastructure, focusing on entities like port authorities. North Korea persisted in its campaign to steal cryptocurrency from financial and tech companies, emphasizing economic motives. Meanwhile, China expanded its global cyberespionage operations.
Industries Targeted by State-Sponsored Threat Actors
Nation-state groups had a broad spectrum of industries, with Russian and Iranian state actors focusing on the IT industry. Additionally, they frequently targeted think tanks, nongovernmental organizations (NGOs), universities, and government agencies, establishing a diverse range of victims for their activities.
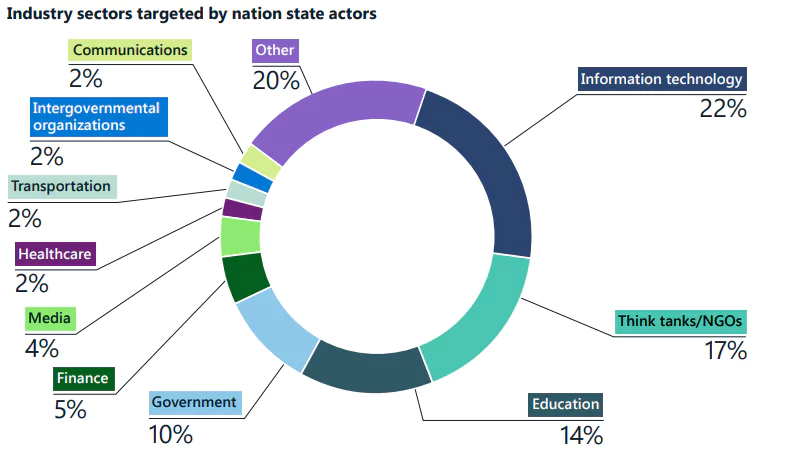
Nation-state threat actors strategically target IT service providers to exploit trust and capitalize on the access granted to supply chain providers. This tactic is especially concerning as it enables them to infiltrate downstream clients in government, policy, and critical infrastructure sectors – targets that are of interest to foreign intelligence services, as highlighted by Microsoft.
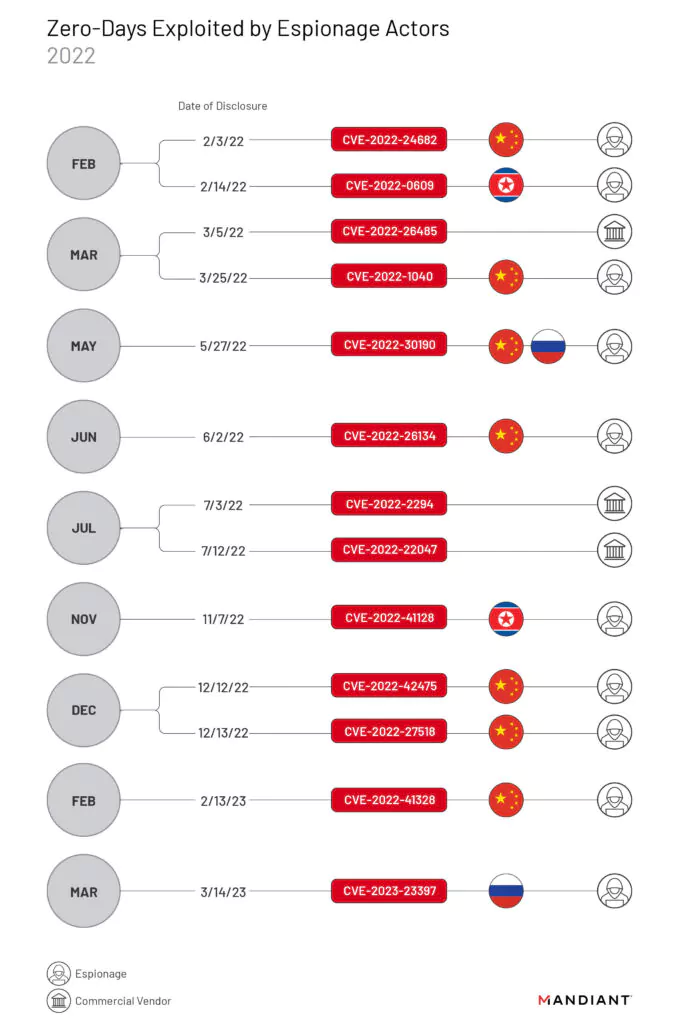
Yet Another Infiltration Method Used by Nation-State Actors: Exploiting Zero-Day Vulnerabilities
Zero-day vulnerabilities are also an effective means of initial infiltration. The report indicates that, on average, it takes just 14 days for an exploit to be available in the wild after a vulnerability has been publicly disclosed. This alarming trend underscores the importance of immediate patching by security teams to safeguard against such threats.
Cybersecurity firm Mandiant’s report further reveals that in 2022, nation-state threat actors were the driving force behind the exploitation of zero-day vulnerabilities. Groups linked to China were responsible for over 50% of these exploits, with Russia and North Korea following closely. In fact, a staggering 80% of zero-day exploits were attributed to groups with connections to nation-states.
Microsoft provides two crucial recommendations:
- Actively patch zero-day vulnerabilities without waiting for regular patch cycles.
- Maintain thorough documentation of all assets to assess risk and swiftly respond to identified vulnerabilities.
In this context, SOCRadar XTI offers valuable assistance. When a vulnerability is identified, the platform is promptly updated with relevant information, equipping you with the essential details to mitigate vulnerability risks, including available exploit codes and whether it is currently under exploitation.
Visit the Vulnerability Intelligence tab within the Cyber Threat Intelligence module to access information on vulnerabilities and stay informed about hacker trends.
Another module that can ensure your security is the Attack Surface Management (ASM). SOCRadar identifies organizational digital assets, allowing you to easily monitor them through the ASM module and stay well-informed about your digital footprint. This proactive approach ensures that you receive timely alerts concerning emerging threats, empowering you to take swift action against security risks.
Which Vulnerabilities Did State-Sponsored Threat Actors Utilize in Nation-State Attacks?
Atlassian Confluence Data Center and Server – CVE-2023-22515, CVE-2022-26134
Microsoft detected exploitation activity linked to the Confluence Data Center and Server vulnerability, CVE-2023-22515, in mid-October, attributing it to the APT threat actor Storm-0062. This critical vulnerability, initially disclosed on October 4, 2023, is related to a privilege escalation issue, with a maximum CVSS score of 10.0. It can be remotely exploited, bearing more resemblance to an authentication bypass or remote code execution than a typical privilege escalation issue.
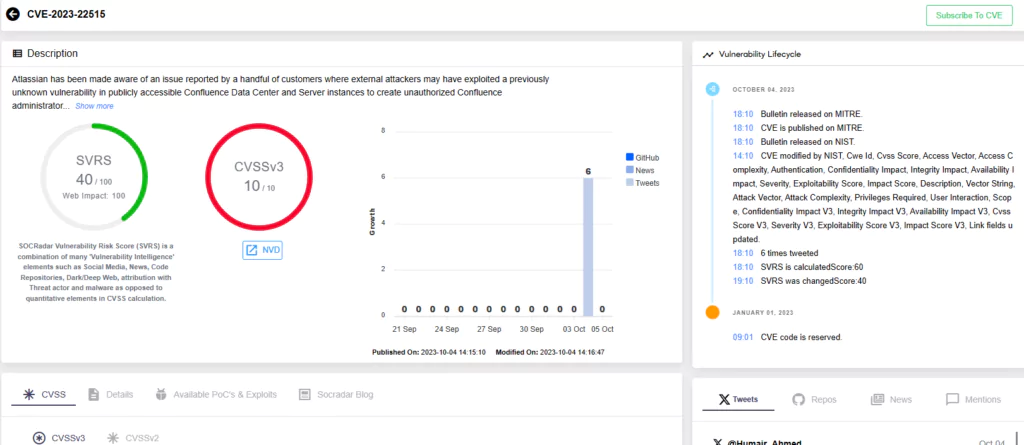
Storm-0062, a nation-state threat actor associated with China’s Ministry of State Security, also goes by the aliases DarkShadow and Oro0lxy. These aliases correspond to Chinese state hackers Li Xiaoyu and Dong Jiazhi, who have been active since at least 2009 and were accused by US authorities in 2020 of probing vulnerabilities affecting companies involved in COVID-19 treatments.
Storm-0062 is recognized for its intelligence-gathering operations, targeting a wide range of sectors, including software, medical research, government, and technology across various regions.
Microsoft revealed that Storm-0062 has actively exploited CVE-2023-22515 in real-world attacks since September 14, 2023. However, there is no further information regarding the specific motivations behind Storm-0062’s targeting of CVE-2023-22515, other than its potential advantage to the Chinese state.
A previous vulnerability in Atlassian was also targeted by Chinese state threat actors. In June 2022, Atlassian disclosed CVE-2022-26134, a critical remote code execution vulnerability affecting Atlassian Confluence Server and Data Center, with a critical CVSS score of 9.8.
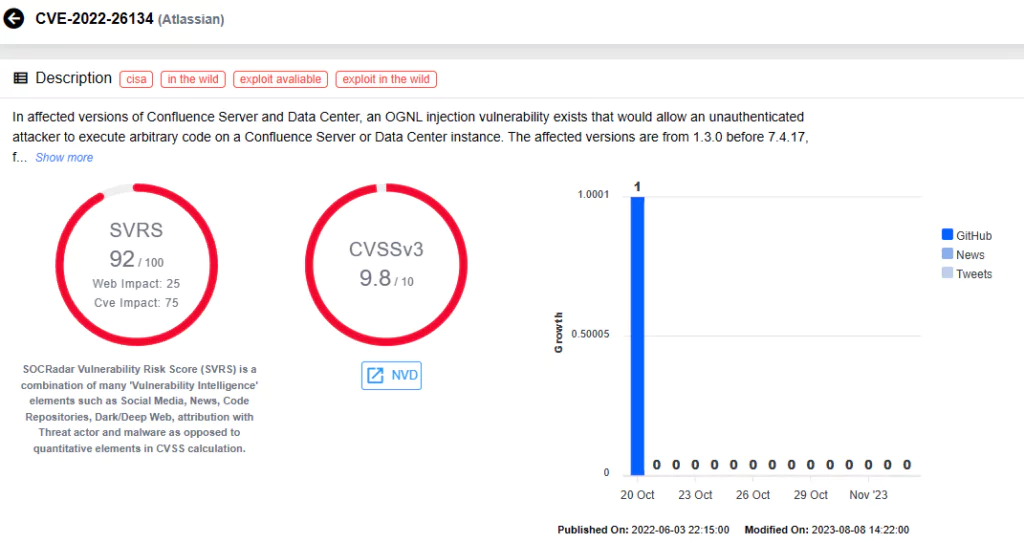
This vulnerability allowed unauthenticated attackers to execute arbitrary commands through OGNL injection by sending a malicious payload via an HTTP GET request.
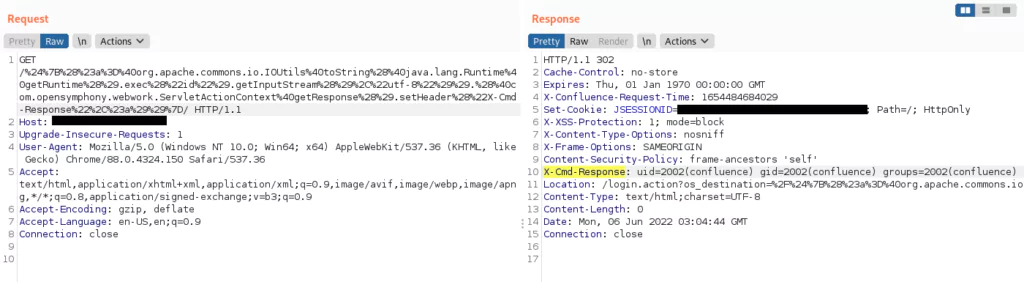
Microsoft asserted that a “China-affiliated actor” possessed the zero-day exploit code for CVE-2022-26134 four days before it was publicly disclosed on June 2, and they likely leveraged it against a US-based entity.
These actions highlight the proficiency of China-based nation-state threat actors in discovering and developing zero-day exploits.
While China’s Foreign Ministry has not responded to Microsoft’s claims regarding this vulnerability, Microsoft had also previously accused Chinese government hackers of abusing other specific zero-day vulnerabilities, affecting SolarWinds (CVE-2021-35211), Zoho products, and Microsoft Exchange (CVE-2021-42321).
Zoho ManageEngine, ServiceDesk Plus – CVE-2022-47966
On September 7, 2023, CISA, FBI, and CNMF issued a joint advisory to share insight about the nation-state and APT threat actors’ targeting of CVE-2022-47966 and CVE-2022-42475. This advisory revealed that an aeronautical organization had fallen victim to a security breach in early January 2023. The breach was orchestrated by APT actors who exploited CVE-2022-47966 – additional APT actors had also infiltrated the organization’s firewall, exploiting CVE-2022-42475, which impacts Fortinet’s FortiOS.
CVE-2022-47966 is a critical (CVSS: 9.8) remote code execution vulnerability that affects various Zoho ManageEngine on-premise products, including ServiceDesk Plus. The root cause of this vulnerability lies in the utilization of an outdated version of Apache Santuario, an XML security software library.
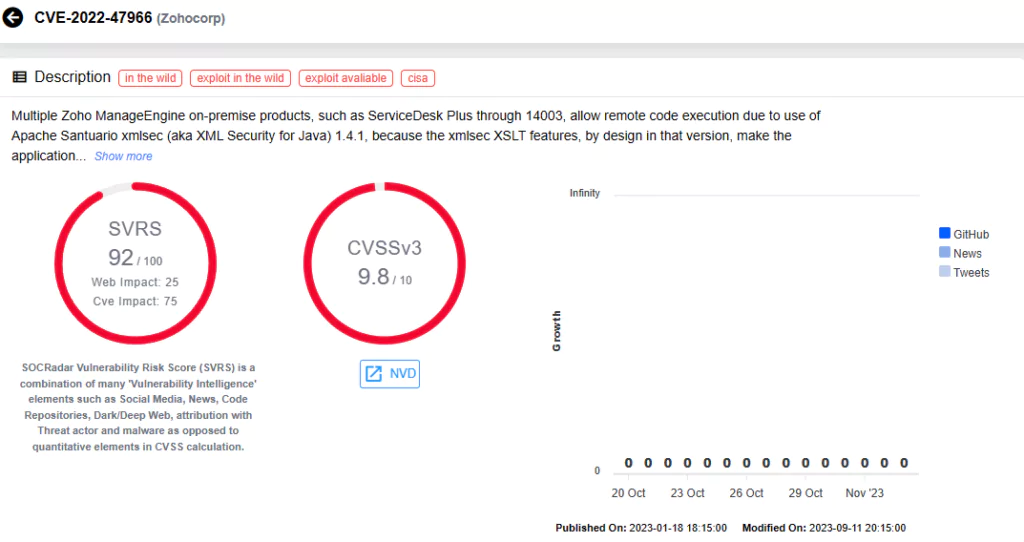
According to the advisory, the APT actors successfully exploited CVE-2022-47966 by targeting an unpatched, publicly accessible server hosting Zoho ManageEngine ServiceDesk Plus, which enabled them to achieve root-level access. Subsequently, they created a local user account equipped with administrator privileges. Armed with these elevated privileges, the APT actor navigated through the organization’s network, attempting to exfiltrate Local Security Authority Subsystem Service (LSASS) hashes. The threat actors also leveraged a range of legitimate applications and tools, such as Mimikatz, nmap, and Metasploit.
Furthermore, in April 2023, Microsoft published a blog post unveiling the TTPs of a threat actor known as Mint Sandstorm. This Iranian nation-state actor, previously tracked as PHOSPHORUS, had set its sights on CVE-2022-47966 starting on January 19, the same day its public Proof-of-Concept (PoC) was released. Although the CISA advisory made no explicit mention of the Microsoft blog post, notable similarities existed in the attackers’ tactics, suggesting the possibility of a shared affiliation between the two groups or even the prospect that they are one and the same. Additionally, the advisory provided a reference to a previously released advisory outlining the Iranian APT actors’ targeting of the federal network.
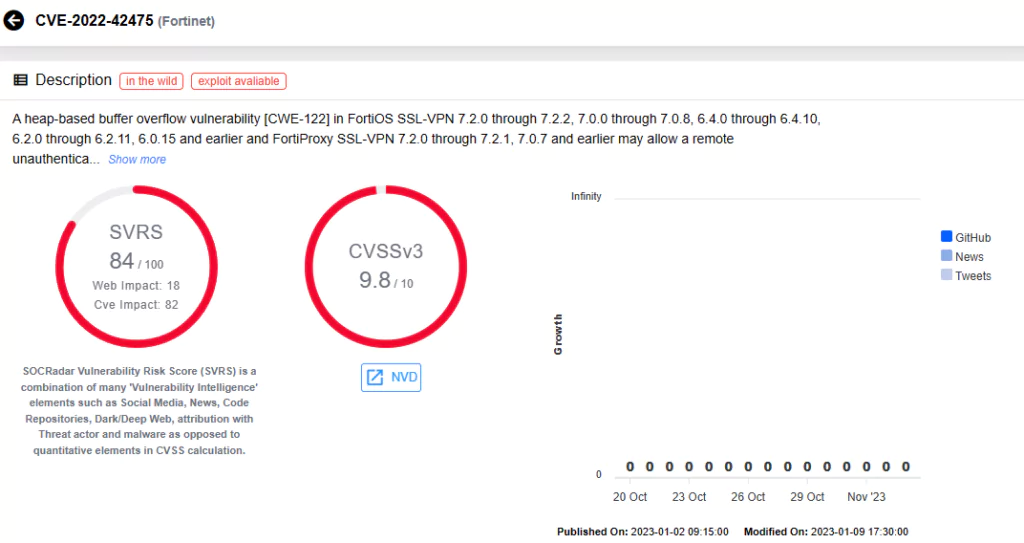
Fortinet FortiOS – CVE-2022-42475
The critical vulnerability, which emerged as a zero-day, affected Fortinet’s FortiOS SSL-VPN product. Known as CVE-2022-42475, this vulnerability represents a heap-based buffer overflow found in several Fortinet FortiOS versions. It opened the door for remote, unauthenticated attackers to exploit the system through a specially crafted request, allowing them to obtain code execution capabilities. The vulnerability initially came to light in December 2022, followed shortly by an advisory from Fortinet, acknowledging its active exploitation.
In January 2023, researchers discovered a sophisticated malware named BoldMove. This malware was tailor-made to operate on Fortinet’s FortiGate firewalls, specifically after gathering data associated with CVE-2022-42475. The BoldMove malware is linked to a threat actor originating from China, known for specializing in cyberespionage operations directed at individuals and groups with government affiliations.
In parallel, the CISA advisory (for CVE-2022-47966 and CVE-2022-42475) sheds light on a second group of unattributed threat actors, who employed legitimate credentials to transition from the compromised firewall to a web server. Once there, they discreetly placed multiple webshells.
Firewalls, SSL VPNs, and other internet-facing devices have long been attractive targets for threat actors, given their potential as an entry point into an organization’s network. In this context, Fortinet’s FortiOS became a strategic focus for state-sponsored actors, serving as a conduit to navigate through the network.
You can find an analysis of emerging Fortinet vulnerabilities on the SOCRadar blog.
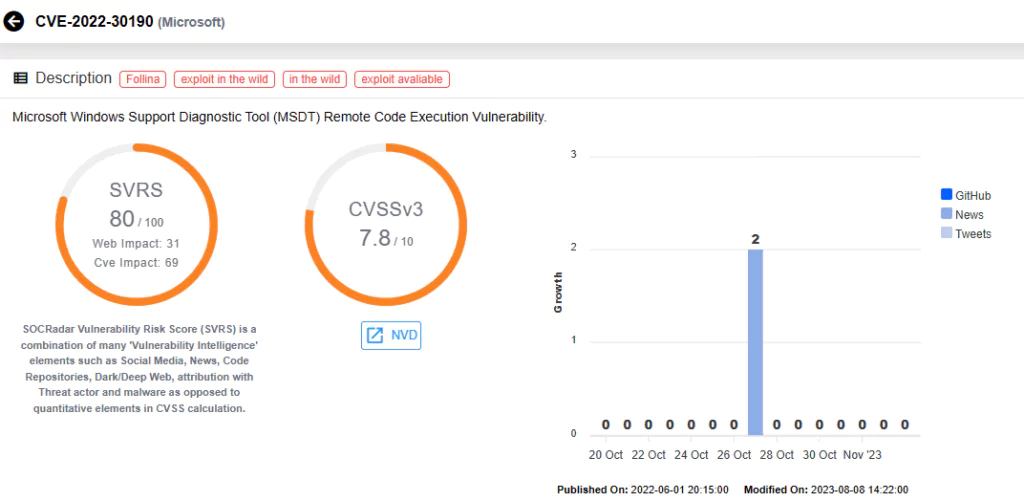
Microsoft Windows Support Diagnostic Tool (MSDT) – CVE-2022-30190 (Follina)
Researchers initially discovered the Follina vulnerability when the malicious Word document “05-2022-0438.doc” was identified on VirusTotal, originating from an IP address in Belarus.
Identified as CVE-2022-30190 and boasting a high CVSS score of 7.8, the vulnerability resided in the Microsoft Windows Support Diagnostic Tool (MSDT) and allowed for remote code execution, especially when utilizing the URL protocol within applications like Microsoft Word. The exploit functioned by leveraging the remote template feature to retrieve an HTML file from an external server and relied on the ms-msdt MSProtocol URI scheme to load code and initiate PowerShell.
Security expert Kevin Beaumont named this vulnerability “Follina” due to the fact that the “0438” in the document’s name corresponded to the area code of Follina in Treviso, Italy. The expert emphasized the vulnerability’s existence for over a month before its disclosure and confirmed that a Word file titled “interview invitation” directly exploited the Follina vulnerability while targeting a user in Russia under the guise of “Sputnik Radio.”
State-sponsored attackers attempted to exploit this Microsoft vulnerability against U.S. and E.U. government targets by using email-based exploits within phishing campaigns. The attackers adopted a recruitment-themed lure, enticing victims with promises of a 20% salary increase while coaxing them into downloading an accompanying attachment.
Additionally, the APT group TA570, an affiliate of the notorious Qbot malware group, also reportedly exploited this vulnerability.
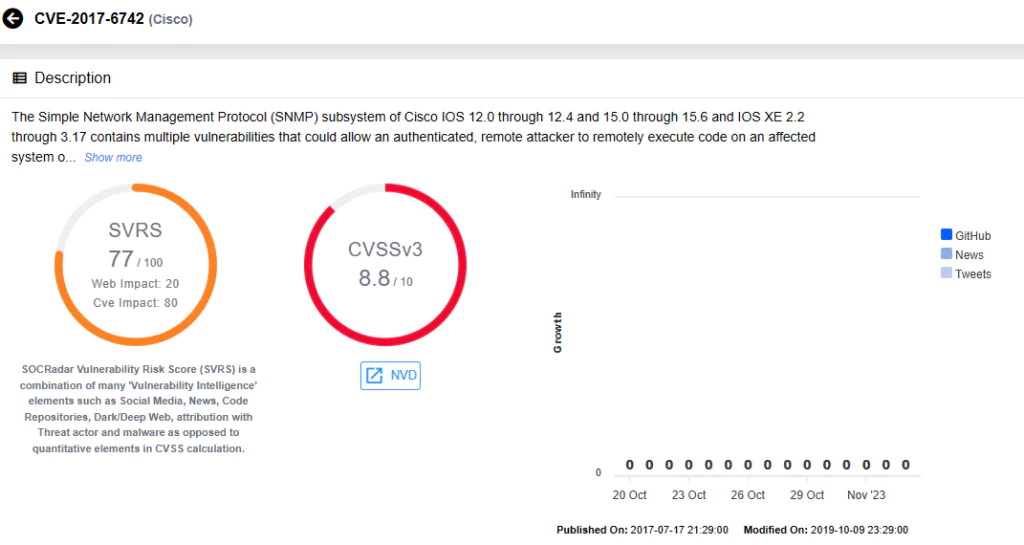
Cisco IOS & IOS XE – CVE-2017-6742
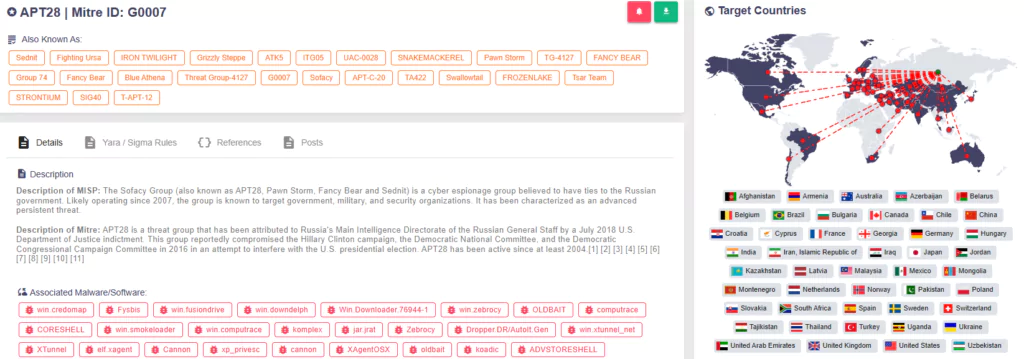
Russian state-sponsored threat actors of APT28 utilized a patched remote code execution vulnerability in Cisco network appliances for surveillance and malware deployment.
The vulnerability, identified as CVE-2017-6742 with a high-severity CVSS score of 8.8, has seen exploitation by various actors since 2018. In April 2023, CISA, NCSC, NSA, and the FBI jointly issued an advisory detailing APT28’s exploitation activity in 2021.
CISA assesses that APT28, also known as Fancy Bear, Sofacy, and STRONTIUM, is highly likely to have ties to the Russian General Staff Main Intelligence Directorate (GRU).
CVE-2017-6742 is a remote code execution vulnerability in Cisco IOS and IOS XE software resulting from a buffer overflow in the Simple Network Management Protocol (SNMP) subsystem. Exploiting this vulnerability allows an attacker to write shellcode into the router’s memory by appending extra bytes to an object identifier (OID) named alpsRemPeerConnLocalPort.
In 2021, as part of an international malware campaign, APT28 infiltrated multiple European organizations, US government institutions, and approximately 250 Ukrainian victims. Research on the APT28 campaign and similar attacks revealed that attackers often have pre-existing network access, granting them credentials and a whitelisted position. The group covertly gained access to Cisco routers worldwide using the Simple Network Management Protocol (SNMP) and leveraged the vulnerability to deploy a malware called Jaguar Tooth.
Conclusion
State-sponsored cyberattacks present exceptional risks to individuals, organizations, and nations. These adversaries, backed by substantial resources and strategic interests, employ their technical expertise to wreak havoc on a global scale.
The surge in state-sponsored cyber activity, targeting critical infrastructure, has been a cause for concern, with alerts rising from 20% in 2021 to a staggering 40% in 2022. Nations such as Russia, China, Iran, and North Korea have actively pursued their agendas, displaying audacity and aggression in their cyber operations, with motives of espionage, political manipulation, economic gain, and military advantage.
Amid this heightened risk, the importance of proactive defense measures cannot be overstated. While state-sponsored attacks may seem sophisticated, threat actors still often resort to relatively low-tech methods. Implementing a set of fundamental security practices can offer a layer of protection against these threats. Regular software updates and responsible patch management are crucial. Companies should also institute multifactor authentication, implement centralized logs and monitoring, and maintain a cyber incident response plan.
Staying ahead of state-sponsored threat actors requires vigilance, advanced tools, and a commitment to cybersecurity best practices. By maintaining robust cybersecurity measures, organizations can protect themselves and their critical assets from state-sponsored cyberattacks, bolstering their resilience in an increasingly interconnected and vulnerable digital landscape.
Organizations can leverage advanced tools like SOCRadar’s comprehensive External Attack Surface Management (EASM) solution. EASM enables businesses to gain a holistic view of their external attack surface, helping them identify potential entry points for adversaries.
SOCRadar EASM automates asset inventory, vulnerability assessment, and threat intelligence integration, helping you monitor digital assets with ease and streamlining risk management processes while enhancing incident response capabilities.
Additional References:
- Move, Patch, Get Out the Way: 2022 Zero-Day Exploitation Continues at an Elevated Pace | Mandiant
- Threat actors linked to nation-states exploited zero-days the most in 2022 | SC Media
- Should you worry about state-sponsored attacks? Maybe not. | securityintelligence.com
- Nation-State-Sponsored Attacks: Not Your Grandfather’s Cyber Attacks | sidley.com
- Microsoft accuses China of abusing vulnerability disclosure requirements | therecord.media
- Top Vulnerabilities Actively Exploited by Chinese State-Sponsored APT Actors | picussecurity.com
- https://www.cisa.gov/topics/cyber-threats-and-advisories/advanced-persistent-threats-and-nation-state-actors
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-047a
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-011a



































