
The Threat of SIM Swapping Attacks on Financial Institutions
SIM swapping attacks have evolved into a growing threat in the digital age, affecting not only individuals but, through them, financial institutions and other organizations. Initially targeting individuals for personal gain, SIM swapping now poses a significant risk to larger entities, including government agencies and major financial players.
In these attacks, cybercriminals manipulate telecommunications systems to hijack a victim’s phone number, gaining unauthorized access to sensitive accounts. This allows them to bypass SMS-based authentication, potentially resulting in fraudulent transactions, identity theft, and reputational damage.
In 2023 alone, the FBI reported that victims lost over $48 million to SIM swapping attacks, highlighting the growing financial implications of these crimes. By December 2024, the FBI recorded 800 cases of SIM swapping nationwide.

“SIM swapping attacks on financial institutions”, illustrated by DALL-E
The increasing prevalence of SIM swapping, coupled with its ability to disrupt financial systems, makes it critical for financial institutions to fully understand the risks involved. This growing threat can lead to devastating financial losses and long-term damage to an institution’s reputation, making it essential for businesses to adopt robust security measures. Continue reading to learn about the rising threat of SIM swapping attacks on financial institutions and how these businesses can safeguard themselves from such fraud.
What Is SIM Swapping?
SIM swapping is a type of account takeover fraud that occurs when a cybercriminal convinces a mobile carrier to transfer a victim’s phone number to a SIM card they control. The term is also coined as “SIM hijacking”. This type of attack allows the threat actor behind it to hijack the victim’s phone number, granting them access to sensitive accounts linked to that number, such as banking or social media.
Once in control of the phone number, attackers can intercept calls and text messages, including Two-Factor Authentication (2FA) codes, enabling them to bypass security measures and access the victim’s accounts.
SIM swapping can lead to the following:
- Intercepting Calls/SMS – Providing attackers with access to sensitive personal information.
- Bypassing SMS-based 2FA – Allowing cybercriminals to manipulate financial systems and accounts.
- Stealing Personal Info – Obtained through intercepting calls, SMS, and accessing accounts.
- Social Media Compromise – Using stolen personal information to hijack social media accounts and conduct other attacks.
- Access to Financial Accounts – Gained via bypassing SMS-based 2FA.
- Manipulating Transactions – Fraudulent transactions conducted after gaining access to financial accounts.
Therefore, this technique has become a common method for committing financial fraud, as cybercriminals can exploit it to steal funds, compromise personal data, and manipulate financial transactions.
How Cybercriminals Use SIM Swapping in Financial Fraud
SIM swapping is typically used as an attack vector in financial fraud, exploiting weaknesses in telecommunications and authentication systems to bypass security measures. Below, we look into the key aspects of this method, including how it’s used in financial attacks.
SIM Swapping as an Attack Vector
SIM swapping is a method used by cybercriminals to hijack a victim’s phone number. Attackers manipulate telecom carriers to transfer a phone number to a SIM card under their control. With the victim’s phone number now in their possession, attackers can bypass SMS-based two-factor authentication (2FA), which is commonly used by financial institutions. This allows cybercriminals to gain unauthorized access to financial accounts, make fraudulent transactions, and steal sensitive data.
Collaboration with Ransomware Gangs
SIM swapping often serves as the first step in a more extensive attack plan – previously, it was observed that SIM swappers collaborated with ransomware gangs such as BlackCat (ALPHV). In these cases, SIM swapping allows attackers to control financial accounts linked to victims’ phone numbers.
By gaining access, they can manipulate banking systems, execute fraudulent transactions, or extract valuable sensitive information. A growing trend is the use of SIM swapping as a critical component of ransomware attacks targeting financial systems, where attackers exploit these entry points to further their malicious objectives.
The Role of Social Engineering
Social engineering is a critical enabler of SIM swapping attacks. In many cases, cybercriminals use social engineering tactics to impersonate the victim and manipulate telecom customer service representatives into facilitating the SIM swap.
By exploiting trust and creating a sense of urgency, attackers can bypass security protocols and take control of a victim’s phone number. This technique is particularly effective when combined with phishing or other forms of deception, making it easier for attackers to carry out SIM swapping undetected.
Protect your organization with SOCRadar’s Cyber Threat Intelligence and Digital Risk Protection modules. Leveraging threat intelligence, SOCRadar’s platform helps organizations identify and respond to emerging threats like SIM swapping and identity theft tactics. With continuous monitoring, our solutions provide real-time alarms for unusual activities, such as unauthorized account changes or suspicious login attempts, offering early warning signs of potential attacks.
SIM Swapping in Major Financial Breaches
In January 2024, a significant SIM swapping attack occurred when attackers took over the U.S. Securities and Exchange Commission (SEC)’s official Twitter (X) account.
The cybercriminals hijacked the SEC’s phone number, gaining access to the account and posting a fake announcement about Bitcoin Exchange-Traded Fund (ETF) approvals. This false information led to a sharp and temporary rise in Bitcoin prices, demonstrating the potential for market manipulation via SIM swapping attacks. The breach also resulted in reputational damage to the SEC, highlighting the far-reaching consequences of such an attack, particularly in sectors with a high public profile.
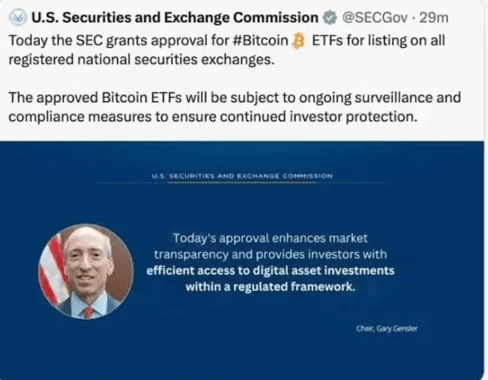
A fake announcement made from SEC’s hijacked account at the time of the incident
Another attack, conducted by a financially motivated threat group known for its SIM swapping tactics, took place in September 2023. The cybercriminal group Scattered Spider, affiliated with the ALPHV/BlackCat ransomware gang, targeted MGM Resorts. Using social engineering, the attackers manipulated MGM’s helpdesk staff to gain access to the company’s systems by impersonating an employee with information obtained from LinkedIn. Once inside, they bypassed security protocols, leading to widespread operational disruptions across MGM’s global network.
Notably, SIM swapping is a well-known tactic used by Scattered Spider. Another prominent tactic they combine with it is social engineering, allowing them to acquire one-time password (OTP) codes.

Scattered Spider threat actor card
Both incidents illustrate how attackers can combine social engineering with Multi-Factor Authentication (MFA) bypass and SIM swapping to manipulate access and cause financial harm. The financial sector, in particular, is vulnerable to such attacks, with SIM swapping directly threatening both individual customer accounts and possibly institutional systems.
To further highlight the growing threat of SIM swapping, consider the case of a Bank of America customer, who lost $38,000 in a SIM swapping attack. In this incident, the victim’s phone was hijacked through social engineering tactics, which allowed the attacker to bypass SMS-based 2FA and transfer funds from the victim’s account.
How Financial Institutions Can Protect Themselves
The growing threat of SIM swapping and similar cybercrimes poses significant risks to financial institutions. Cybercriminals have increasingly targeted financial systems, exploiting vulnerabilities to manipulate accounts and bypass security measures. To defend against these threats, financial institutions must adopt proactive and strong security strategies.
Preventative Measures
- Multi-Factor Authentication (MFA)
Financial institutions must implement strong multi-factor authentication across all systems. This adds an extra layer of protection by requiring users to verify their identity through something they know (password) and something they have (such as a biometric factor or hardware token), reducing the risk of unauthorized access. - Employee Training on Social Engineering Attacks
Employee awareness is critical in preventing cybercrimes. Financial institutions should regularly train employees to recognize and respond to social engineering tactics, ensuring they don’t fall victim to manipulative strategies used by cybercriminals to gain unauthorized access. - Securing Communication Channels
Organizations must ensure that sensitive communications, including those involving account changes or financial transactions, are conducted over secure channels. Encryption and secure messaging platforms should be adopted to prevent interception by malicious actors.
Importance of Dark Web Monitoring
To effectively address the growing threat of SIM swapping and similar cybercrimes, it is important for financial institutions to stay vigilant about the security of personal and financial information. Compromised data, including personally identifiable information (PII) and account details, can be exposed on the Dark Web, even without direct involvement from the organization. Cyber attackers often purchase this sensitive information and use it for malicious activities, such as fraud and identity theft.
This is where SOCRadar’s Dark Web Monitoring solution can make a difference. With SOCRadar’s comprehensive Dark & Deep Web Monitoring, financial institutions gain the ability to detect compromised data before it can be exploited. Our platform continuously monitors the Dark Web for stolen credentials, exposed accounts, and sensitive financial information, providing actionable intelligence for proactive threat mitigation.
SOCRadar’s Dark Web Monitoring
By integrating automated threat intelligence with expert analysis, SOCRadar empowers SOC teams to identify risks beyond their traditional perimeter, helping to secure both customer data and organizational assets from emerging cyber threats.
Additional Recommendations
- Stronger Verification Processes for Account Changes
Financial institutions should implement robust verification protocols for account changes, ensuring any modifications are thoroughly verified to prevent unauthorized transfers or data manipulation. - Using Biometrics as an Alternative to SMS-based 2FA
SMS-based two-factor authentication (2FA) is vulnerable to SIM swapping. Institutions should consider using biometric verification methods, such as fingerprint scanning or facial recognition, as a more secure alternative for customer verification. - Partnering with Cybersecurity Experts for Ongoing Protection
Collaborating with cybersecurity professionals can provide financial institutions with ongoing protection against emerging threats. By working with experts, institutions can strengthen their defenses, stay ahead of new attack vectors, and ensure their security measures are continually updated.
Financial institutions must take the threat of SIM swapping and other cybercrimes seriously. By adopting these protective measures, they can mitigate risks, safeguard customer data, and prevent financial harm. Proactive defense is key to maintaining trust and securing sensitive financial systems from future attacks.




































