Top 10 Free and Open-Source Tools for MSSPs
In the rapidly evolving landscape of cybersecurity, Managed Security Service Providers (MSSPs) face increasing challenges in protecting their clients’ digital assets. Open-source tools have emerged as powerful allies, offering robust capabilities without the hefty price tag of proprietary solutions. This comprehensive guide explores eight critical free and open-source tools that can significantly enhance an MSSP’s threat intelligence and security monitoring capabilities.
At SOCRadar, we’ve built our foundation on a single, unwavering principle: MSSP-First. This isn’t just a tagline; it’s a commitment woven into the very fabric of our organization.
Benefits of SOCRadar for MSSPs
When we say we’re MSSP-First, we’re making a bold declaration about where our priorities lie. Our partners aren’t just resellers; they’re fellow warriors in the battle to make the world a safer place. We understand that their success is intrinsically linked to global cybersecurity resilience, which is why we’ve aligned our entire organization – from sales and marketing to our technical teams – to provide comprehensive, unwavering support to our MSSP partners.
1. MISP (Malware Information Sharing Platform)
MISP (Malware Information Sharing Platform) is an open-source threat intelligence platform designed to facilitate the sharing of structured threat information among organizations. It allows users to collect, store, distribute, and collaborate on cybersecurity threat data, such as Indicators of Compromise (IoCs), malware attributes, and other relevant information. MISP is widely used by security teams, CERTs (Computer Emergency Response Teams), and organizations to improve their threat detection and response capabilities.
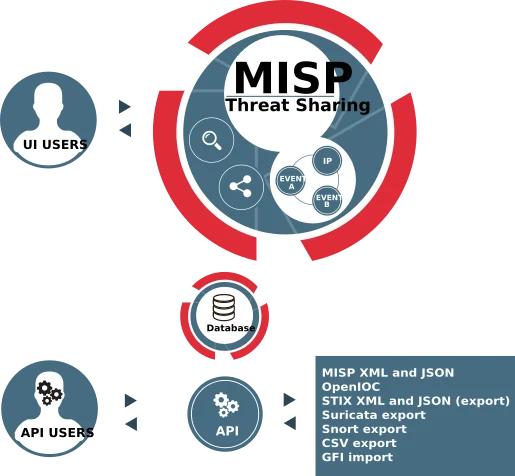
MISP Threat Sharing
How MSSPs Can Benefit from MISP:
- MISP enables MSSPs to collect and share threat intelligence data across their client base, allowing them to identify patterns and emerging threats that affect multiple organizations. When a security incident occurs at one client, MSSPs can quickly assess if other clients are at risk and take proactive measures.
- The platform’s automation capabilities help MSSPs scale their threat detection and response operations. Through MISP’s APIs and export features, they can automatically push threat indicators to their security tools (like SIEMs, firewalls, and EDR solutions) across multiple client environments, significantly reducing manual work.
- They can leverage MISP’s collaborative features to participate in trusted threat sharing communities, gaining access to high-quality intelligence from other security teams, researchers, and organizations. This expanded threat visibility helps them provide better protection for their clients.
- The platform’s flexible data model and taxonomy system allows MSSPs to organize and categorize threat intelligence based on different client industries, threat types, or severity levels. This structured approach helps in delivering customized threat intelligence services to clients with different security needs.
- MISP’s attribution capabilities help MSSPs maintain clear boundaries between different clients’ data while still benefiting from shared intelligence. They can control what information is shared with which clients or communities, ensuring compliance with confidentiality requirements.
2. OpenCTI
OpenCTI (Open Cyber Threat Intelligence) is an open-source platform designed to manage, organize, and operationalize Cyber Threat Intelligence (CTI). It provides a comprehensive framework for collecting, storing, analyzing, and sharing threat intelligence data. OpenCTI is built to support the STIX2 (Structured Threat Information Expression) standard, making it highly interoperable with other security tools and platforms. It is widely used by organizations, including MSSPs, to enhance their threat intelligence capabilities.
OpenCTI Dashboard
How MSSPs Can Benefit from OpenCTI:
- OpenCTI enhances threat detection capabilities by providing a comprehensive platform for collecting, organizing, and analyzing threat intelligence from multiple sources. This allows MSSPs to offer more robust security monitoring and incident response services to their clients while maintaining a centralized knowledge base of threats.
- The platform’s automation features significantly reduce manual work by automatically ingesting, processing, and correlating threat data from various feeds and sources. This efficiency allows MSSP analysts to focus on high-value activities like threat hunting and incident investigation rather than spending time on data entry and organization.
- OpenCTI’s collaborative features enable MSSP teams to share threat intelligence findings, investigation notes, and analysis results across their organization. This knowledge sharing improves team coordination and ensures consistent threat response across different client environments.
- The platform’s visualization capabilities help MSSPs create clear, actionable reports for their clients, demonstrating the value of their services through comprehensive threat landscapes and attack pattern analyses. This enhances client communication and justifies security investments.
- By leveraging OpenCTI’s integration capabilities with other security tools (like SIEM systems and EDR platforms), MSSPs can create automated workflows that enhance their security operations and provide more comprehensive protection for their clients.
3. GoPhish
GoPhish is an open-source phishing toolkit designed to simulate phishing attacks for security awareness training and testing. It provides a user-friendly interface for creating, launching, and managing phishing campaigns, making it a popular tool for organizations and MSSPs to assess and improve their clients’ resilience against phishing attacks.
How MSSPs Can Benefit from GoPhish:
- MSSPs can utilize GoPhish to conduct comprehensive phishing assessments for their clients, allowing them to identify vulnerabilities in employees’ security awareness and response capabilities. This provides tangible data about an organization’s susceptibility to phishing attacks.
- The platform enables MSSPs to create tailored phishing simulation campaigns that match real-world scenarios specific to each client’s industry. These customized campaigns can include industry-specific terminology, branding, and attack vectors that employees are likely to encounter.
- GoPhish provides robust reporting capabilities that MSSPs can use to demonstrate value to their clients. The platform tracks click rates, report rates, and other key metrics that help measure the effectiveness of security awareness programs and justify security investments.
- They can develop ongoing security awareness training programs using GoPhish, creating a steady revenue stream through regular phishing simulations, training sessions, and detailed reporting services. This transforms a one-time security assessment into a continuous security improvement program.
- GoPhish can be integrated with other security tools and services that MSSPs already provide, creating a more comprehensive security offering. This could include combining phishing simulation results with vulnerability assessments, penetration testing, and other security metrics.
- The platform’s user-friendly interface makes it easier for MSSPs to demonstrate phishing risks to clients and engage them in security discussions. This can lead to better client relationships and increased awareness of other security services the MSSP offers.
4. TheHive Project
TheHive Project is an open-source Security Incident Response Platform (SIRP) designed to help organizations manage and respond to security incidents efficiently. It provides a centralized platform for incident detection, analysis, and response, enabling security teams to collaborate effectively and streamline their workflows. TheHive is widely used by SOCs, CERTs, and MSSPs to enhance their incident response capabilities.
How MSSPs Can Benefit from TheHive Project:
- TheHive’s multi-tenancy capabilities allow MSSPs to efficiently manage multiple client environments from a single platform, with strong isolation between different customers’ data and cases. This enables secure and segregated incident response management for various clients while maintaining operational efficiency.
- The platform’s robust API integration capabilities enable MSSPs to connect TheHive with their existing security tools and client systems, creating automated workflows for incident detection, analysis, and response. This integration potential includes SIEM systems, threat intelligence platforms, and other security tools commonly used in MSSP environments.
- TheHive’s collaborative features support distributed teams working across different locations and time zones, which is essential for MSSPs operating Security Operations Centers (SOCs). Teams can share cases, findings, and updates in real-time, ensuring smooth handoffs between shifts and maintaining continuous incident response coverage.
- The platform’s customizable case templates and playbooks allow MSSPs to standardize their incident response procedures across different clients while maintaining the flexibility to adapt to specific client requirements. This helps ensure consistent service quality while accommodating unique client needs.
- TheHive’s reporting capabilities enable MSSPs to generate detailed incident reports and metrics for their clients, demonstrating the value of their services through comprehensive documentation of security incidents, response actions, and outcomes. These reports can be customized to meet different clients’ reporting requirements.
- TheHive’s scalability supports MSSPs as they grow their client base, allowing them to handle increasing case volumes and complexity without compromising performance or effectiveness. The platform can be deployed on-premises or in the cloud, providing deployment flexibility based on MSSP requirements.
5. Wazuh
Wazuh is an open-source security platform that provides unified XDR (Extended Detection and Response) and SIEM (Security Information and Event Management) capabilities. It is designed to help organizations detect and respond to security threats, monitor system and application activity, and ensure compliance with regulatory requirements. Wazuh integrates multiple security functionalities, including intrusion detection, log analysis, file integrity monitoring, vulnerability detection, and incident response, making it a comprehensive solution for security teams and MSSPs.
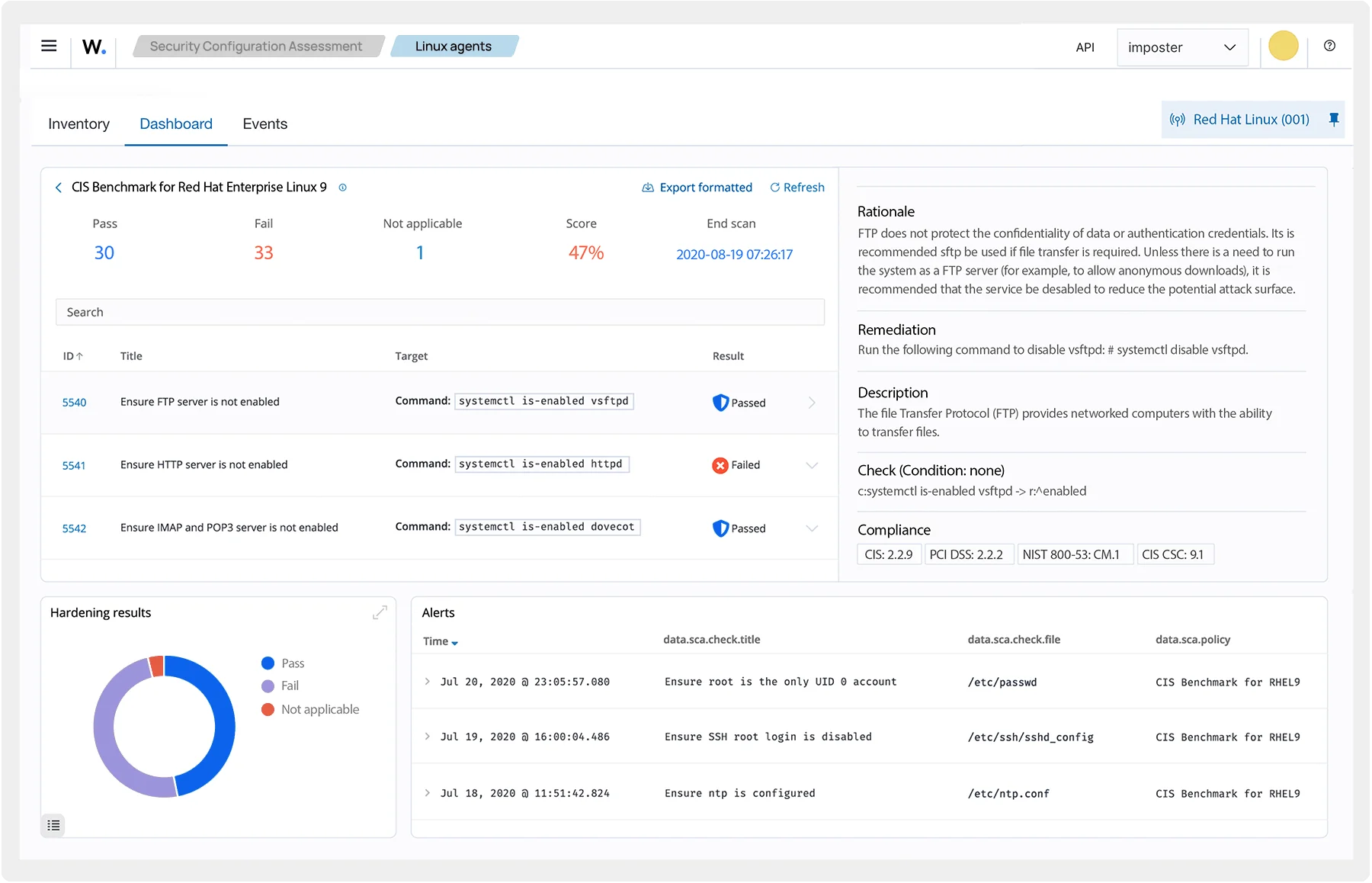
Wazuh Dashboard
How MSSPs Can Benefit from Wazuh:
- MSSPs can achieve faster client onboarding and deployment through Wazuh’s centralized management architecture, which allows them to monitor and manage multiple client environments from a single dashboard, streamlining operations and reducing the time required to set up new security monitoring services.
- The platform’s multi-tenancy capabilities enable MSSPs to maintain strict data segregation between different clients while managing all security operations from a unified console, ensuring confidentiality and compliance with data privacy requirements while improving operational efficiency.
- MSSPs can expand their service offerings by utilizing Wazuh’s comprehensive feature set, including SIEM capabilities, FIM, vulnerability detection, cloud security monitoring, and compliance monitoring, allowing them to create tiered service packages and increase revenue opportunities with existing clients.
- The scalable architecture of Wazuh allows MSSPs to grow their client base without significant infrastructure changes, as the platform can efficiently handle security monitoring for thousands of endpoints across multiple client environments while maintaining performance.
- Real-time threat detection and automated response capabilities enable MSSPs to provide faster incident response services to their clients, reducing mean time to detect (MTTD) and mean time to respond (MTTR) to security incidents, thereby improving service level agreements (SLAs).
- Wazuh’s extensive API and integration capabilities allow MSSPs to customize and automate security workflows according to each client’s specific needs, enhancing service delivery while maintaining operational efficiency through automated processes and custom reporting.
- The platform’s robust compliance reporting features help MSSPs assist their clients in meeting various regulatory requirements (such as PCI DSS, HIPAA, and GDPR), providing additional value-added services and strengthening client relationships through comprehensive compliance management.
6. Snort
Snort is an open-source Network Intrusion Detection and Prevention System (NIDS/NIPS) that monitors network traffic in real-time to detect and prevent malicious activity. It uses a combination of signature-based detection, protocol analysis, and anomaly-based detection to identify threats such as malware, exploits, port scans, and other suspicious behavior. Snort is widely used by organizations, including MSSPs, to enhance their network security capabilities.
How MSSPs Can Benefit from Snort:
- Snort’s intrusion detection and prevention capabilities allow MSSPs to offer comprehensive network security monitoring across multiple client environments, helping them detect and block malicious traffic in real-time through customizable rule sets and signatures.
- They can leverage Snort’s scalability to monitor numerous client networks simultaneously through centralized management consoles, streamlining operations and allowing for efficient threat detection and response across diverse customer environments.
- The platform’s extensive reporting capabilities help MSSPs demonstrate value to clients through detailed threat intelligence reports and compliance documentation, strengthening client relationships and justifying security investments.
- Snort’s active community and regular updates ensure MSSPs stay current with emerging threats, while the ability to create custom rules allows them to tailor protection for specific client needs and industry requirements.
7. Suricata
Suricata is an open-source Network Intrusion Detection and Prevention System (NIDS/NIPS) that provides real-time threat detection, intrusion prevention, and network security monitoring. It is designed to analyze network traffic for malicious activity, such as exploits, malware, and policy violations, using a combination of signature-based detection, protocol analysis, and anomaly detection. Suricata is highly scalable and can handle high-speed networks, making it a popular choice for organizations and MSSPs looking to enhance their network security capabilities.
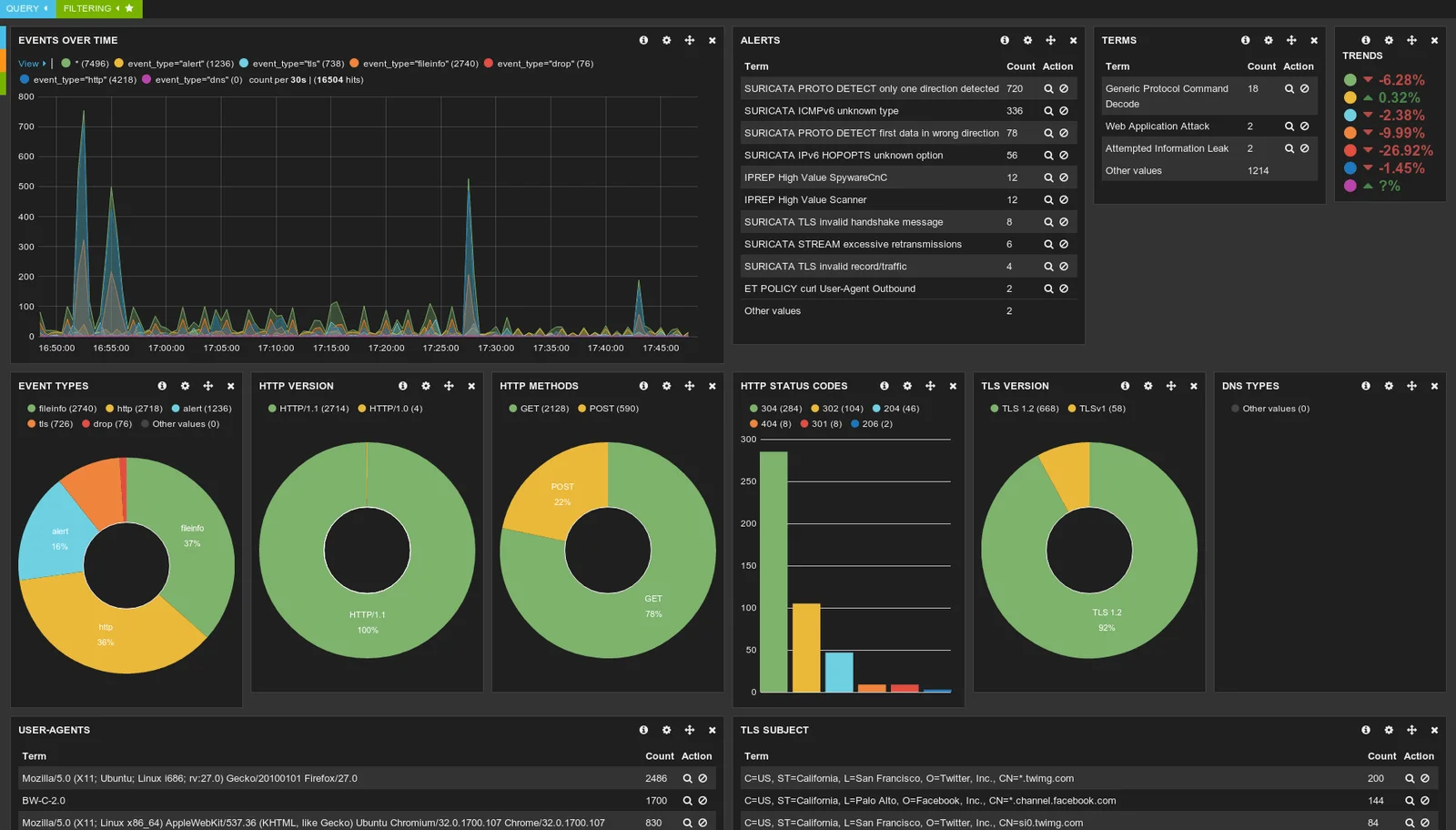
Suricata IDS
How MSSPs Can Benefit from Suricata:
- Suricata’s advanced threat detection capabilities enable MSSPs to provide enterprise-grade security monitoring across multiple client networks simultaneously. The intrusion detection and prevention system (IDS/IPS) can process network traffic at high speeds while maintaining accuracy in threat detection, making it ideal for managing security at scale.
- The platform’s extensive ruleset customization allows them to create tailored security policies for different clients while maintaining a standardized security framework. This flexibility helps balance each client’s unique security requirements with the MSSP’s need for operational efficiency.
- By leveraging Suricata’s multi-threading capabilities and hardware acceleration support, MSSPs can optimize their infrastructure costs while handling large volumes of network traffic. This efficient resource utilization directly impacts the bottom line and helps maintain competitive pricing for security services.
- The robust API integration capabilities enable MSSPs to incorporate Suricata into their existing Security Operations Center (SOC) workflows and tools. This seamless integration enhances threat detection, incident response, and reporting processes across the entire security stack.
- Suricata’s comprehensive logging and alerting features provide MSSPs with detailed visibility into security events, supporting both real-time monitoring and historical analysis. This depth of information helps in creating detailed client reports and maintaining compliance requirements.
8. OpenVAS
OpenVAS (Open Vulnerability Assessment System) is an open-source vulnerability scanning and management tool designed to identify security vulnerabilities in networks, systems, and applications. It provides comprehensive scanning capabilities, including network vulnerability detection, configuration auditing, and compliance checking. OpenVAS is widely used by security professionals, including MSSPs, to assess and improve the security posture of their clients’ environments.
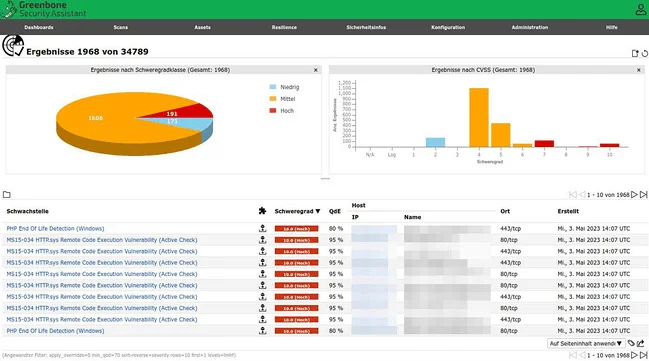
OpenVAS Dashboard
How MSSPs Can Benefit from OpenVAS:
- The platform’s extensive vulnerability database, which is regularly updated, allows MSSPs to deliver enterprise-grade vulnerability assessments to their clients. This comprehensive coverage helps identify potential security gaps across various systems, applications, and network devices, enhancing the MSSP’s value proposition.
- They can integrate OpenVAS into their existing security infrastructure through its well-documented API, enabling automated scanning schedules and custom report generation. This integration capability streamlines operations and allows for more efficient resource allocation across multiple client environments.
- The customizable reporting features of OpenVAS enable MSSPs to provide branded, professional vulnerability assessment reports tailored to each client’s needs. These detailed reports can include executive summaries, technical findings, and remediation recommendations, helping MSSPs demonstrate their expertise and value.
- OpenVAS supports multi-tenancy, allowing MSSPs to manage multiple client environments from a single installation while maintaining strict separation between different client data. This architecture helps ensure client confidentiality while simplifying the management overhead for the MSSP.
- The platform’s authentication capabilities and support for various scanning methods (authenticated, unauthenticated, and network-based) enable MSSPs to offer different levels of assessment services, from basic network scans to deep system analyses, creating tiered service offerings for different client needs.
9. SOCRadar Labs: Free SOC Tools
SOCRadar Labs offers a comprehensive suite of free security tools designed to help organizations assess and improve their cybersecurity posture across multiple critical domains. These tools provide actionable insights into various aspects of cybersecurity, enabling organizations to identify vulnerabilities, detect threats, and enhance their overall security resilience. SOCRadar Labs’ tools are particularly valuable for MSSPs looking to deliver enhanced security assessments and proactive threat management for their clients.
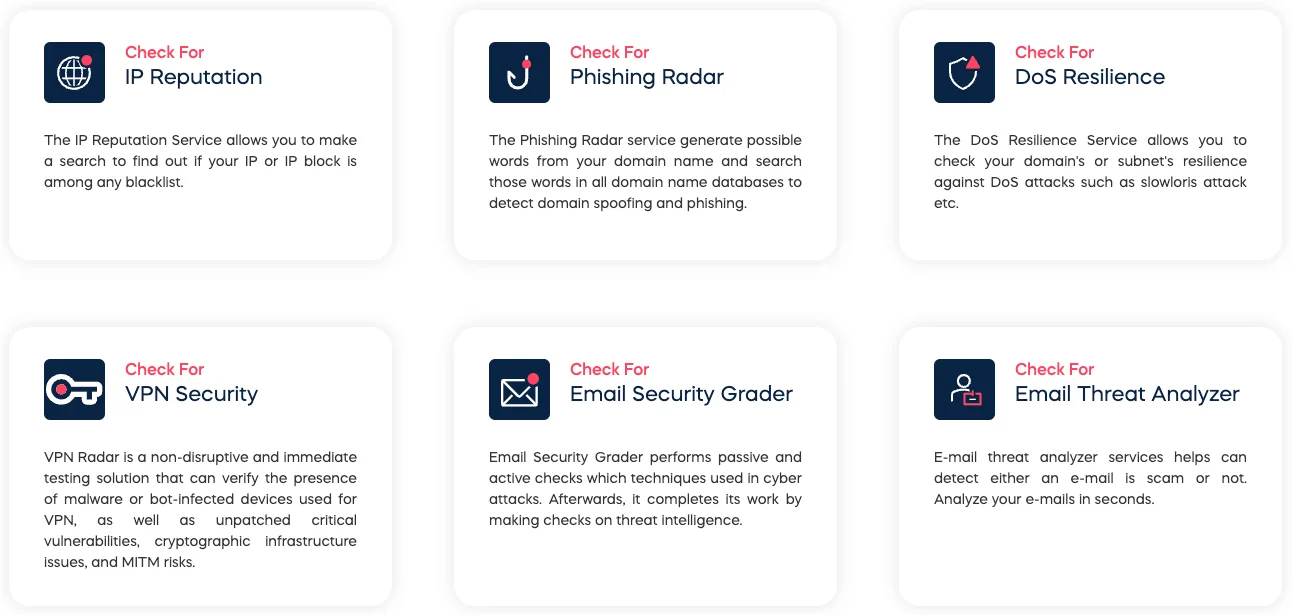
SOCRadar Free SOC Tools
How MSSPs Can Benefit from SOCRadar Labs:
- These tools provide them with comprehensive security assessment capabilities they can offer to their clients, enabling them to detect potential threats across multiple vectors (IP, domain, email) without having to develop or maintain these tools internally, which reduces operational costs and time-to-market for new security services.
- The combination of IP Reputation and Phishing Radar services allows MSSPs to proactively identify and mitigate brand impersonation attempts and malicious infrastructure targeting their clients, making their threat detection and response services more valuable to customers concerned about reputational damage and phishing attacks.
- Email Security Grader and Email Threat Analyzer give MSSPs robust email security assessment capabilities, which is particularly valuable since email remains one of the primary attack vectors. These tools help MSSPs demonstrate concrete value to clients by identifying vulnerabilities in their email security posture and detecting potential scams before they cause damage.
- The DoS Resilience and VPN Security tools enable MSSPs to expand their service portfolio with specialized security testing offerings, helping them differentiate from competitors and address specific client concerns about DDoS attacks and VPN infrastructure security, which became especially relevant with the rise of remote work.
10. SOCRadar Free Dark Web Report
SOCRadar’s Free Dark Web Report is a specialized threat intelligence tool designed to provide organizations with immediate insights into their digital exposure and potential security risks on the dark web. This tool helps organizations monitor their digital footprint, detect credential leaks, and identify potential threats lurking in underground markets. For MSSPs, this tool is a valuable resource for proactively protecting clients from emerging threats and enhancing their overall security posture.
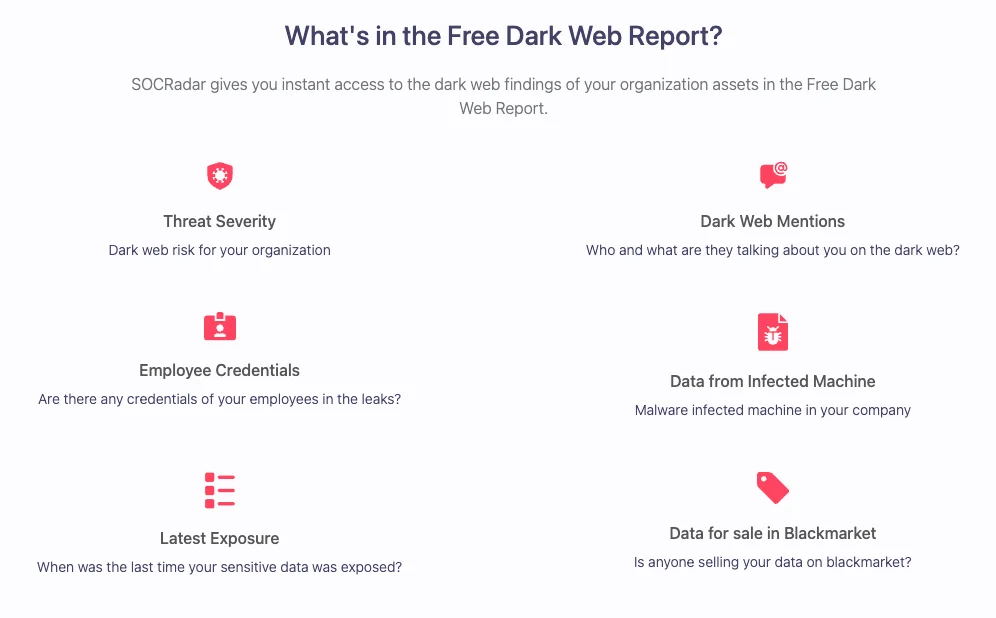
SOCRadar Free Dark Web Report
How MSSPs Can Benefit from SOCRadar’s Free Dark Web Report:
MSSPs can leverage SOCRadar’s Free Dark Web Report to enhance their threat intelligence capabilities and provide proactive protection for their clients. Here are some ways MSSPs can benefit:
- They can use this tool as an initial assessment offering for potential clients, demonstrating the real cyber risks their organizations face by showing concrete evidence of dark web exposure. This tangible proof of vulnerabilities often helps convert prospects into clients more effectively than theoretical security discussions.
- The tool provides them with actionable intelligence about their clients’ security posture, allowing them to prioritize security services based on actual threats. For example, if the report shows compromised employee credentials, the MSSP can recommend and implement immediate password resets and multi-factor authentication.
- By regularly monitoring these reports for their clients, MSSPs can proactively identify new threats and data leaks, enabling them to provide early warning and rapid response services. This strengthens their value proposition as a proactive security partner rather than just a reactive service provider.
- The variety of data points in the report (credentials, malware infections, dark web mentions, marketplace listings) helps MSSPs build comprehensive security programs tailored to each client’s specific risks and vulnerabilities, rather than applying one-size-fits-all solutions.
- They can use these reports in their regular client security reviews to demonstrate the ongoing value of their services by showing threats they’ve helped mitigate and highlighting emerging risks that require attention. This helps justify security investments and retain clients long-term.
Conclusion
These ten free and open-source tools provide MSSPs with powerful capabilities to enhance threat intelligence, vulnerability management, and security monitoring. By strategically implementing these solutions, security providers can deliver high-value services while maintaining cost-effectiveness.
You can also check Dark Web Monitoring to keep track of your credentials as it is a vital tool for MSSPs
While these tools offer significant advantages, successful implementation requires expertise, proper configuration, and ongoing management. MSSPs should invest time in understanding each tool’s nuances and integrating them effectively into their security frameworks.