
Alleged UAE Credit Cards and BMW Data for Sale, New SMS Bomber Service Detected
Recent investigations by the SOCRadar Dark Web Team have revealed a series of significant cyber threats. Among them is the sale of 1,500 credit cards from the United Arab Emirates and a large-scale data breach affecting Compass Group Australia. Additionally, a Sinbad database with 399,212 customer records is being offered for sale. The team also uncovered a new SMS bomber service and the alleged leak of BMW customer data from North Carolina.
Receive a Free Dark Web Report for Your Organization:
1500 Credit Cards Belonging to the United Arab Emirates are on Sale
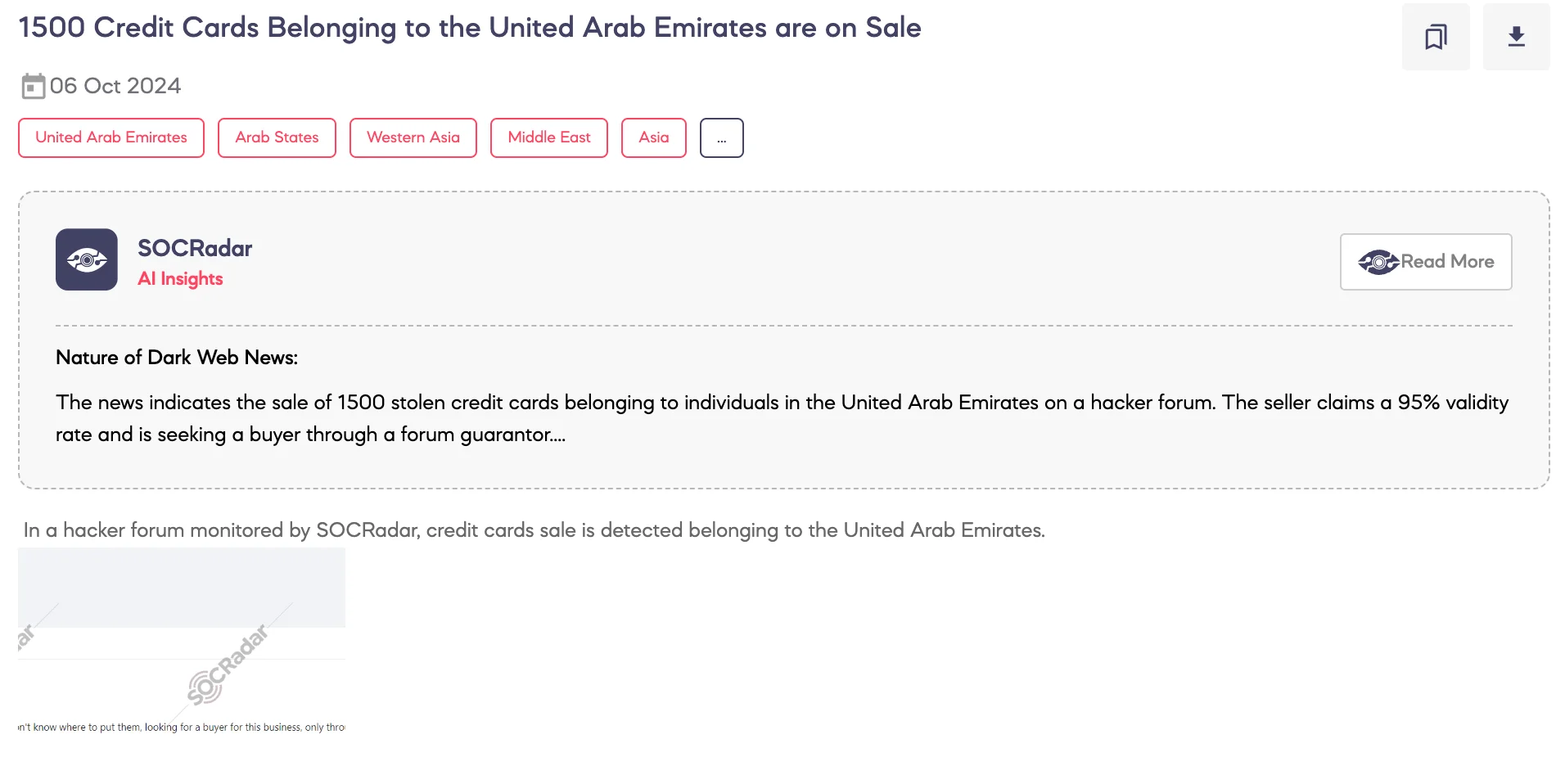
SOCRadar Dark Web Team detected that 1,500 credit cards belonging to individuals from the United Arab Emirates are currently being offered for sale on a Dark Web forum. The threat actor has listed the price at $20 per card and is advertising the sale as a one-time opportunity.
The threat actor claims to have found a small database of credit cards, with an estimated 95% validity. The database reportedly contains around 200 credit cards. The actor is seeking a buyer and insists that all transactions be conducted through the forum’s guarantor service, ensuring a level of security for the buyer. Communication with the seller is limited to private messages on the forum, as indicated by the contact details provided.
Data of Compass Group Australia are Allegedly Leaked
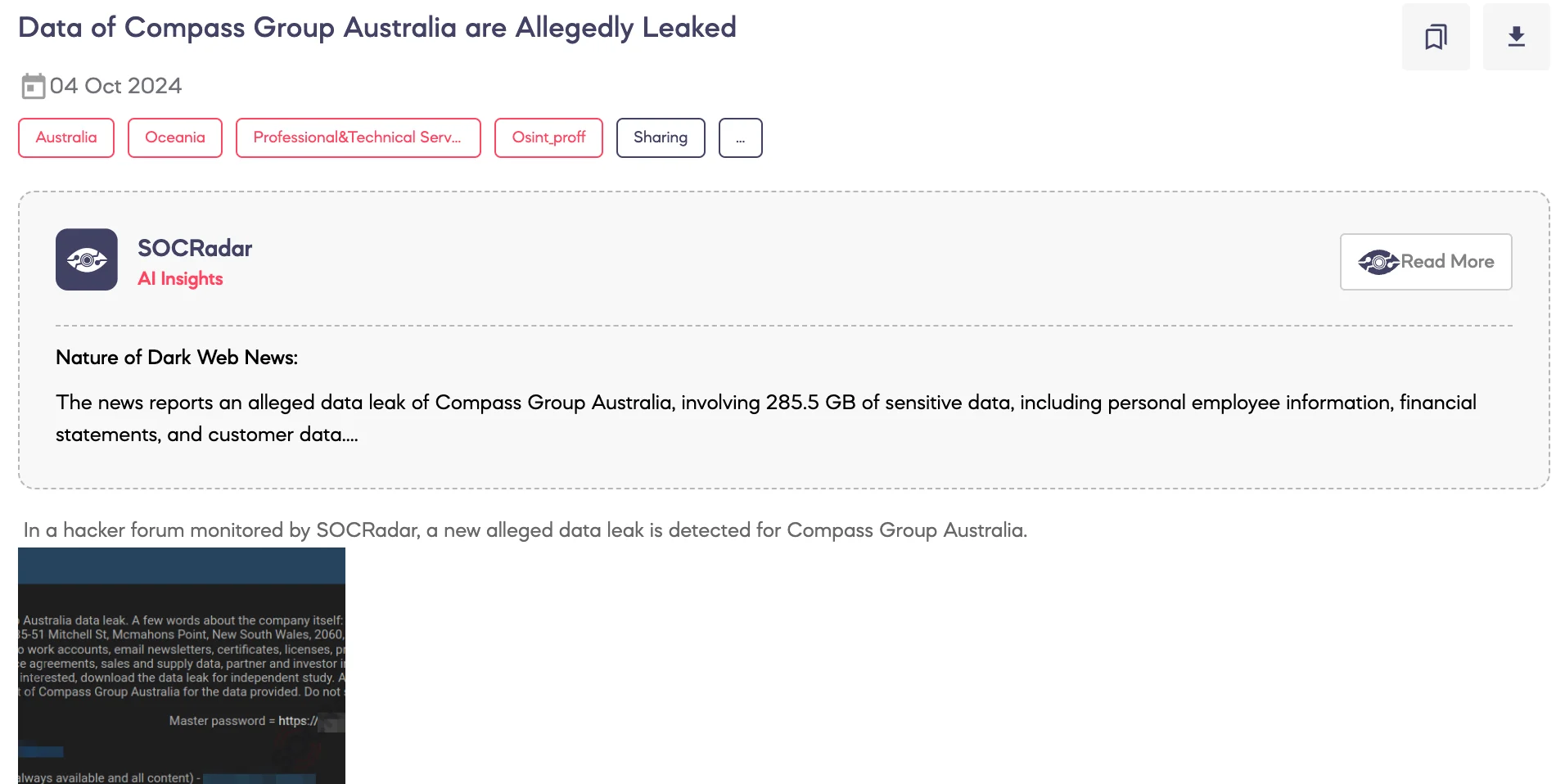
SOCRadar Dark Web Team detected a post on a hacker forum that a threat actor claims to have leaked 285.5 GB of sensitive data from Compass Group Australia, a food and support services company. The breach purportedly includes personal employee data, financial records, and other corporate information. The actor has made the alleged data available on a Telegram.
Threat Actor Claims to Sell Sinbad Database, Allegedly Containing 399,212 Customer Records
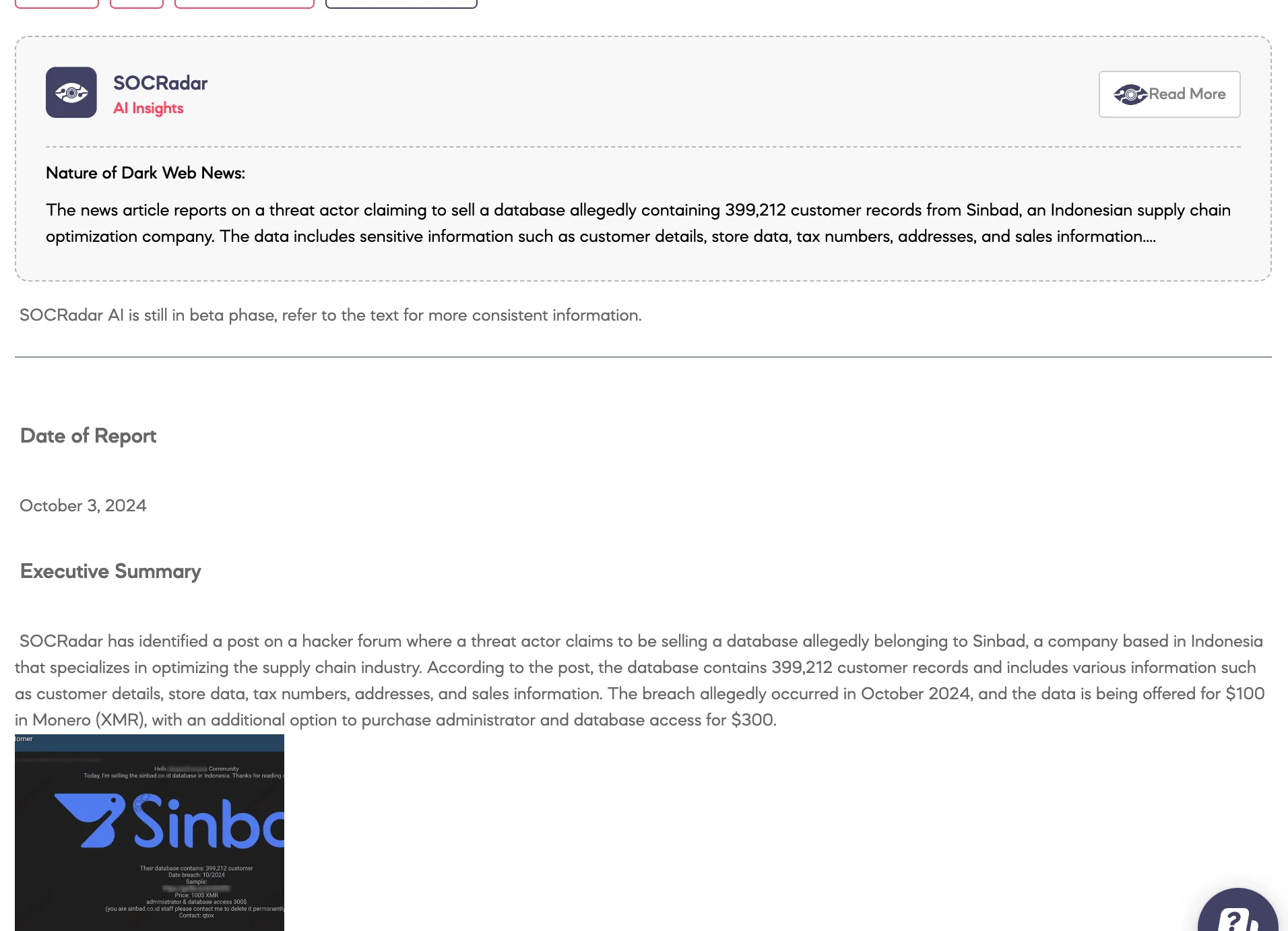
SOCRadar has identified a post on a hacker forum where a threat actor claims to be selling a database allegedly belonging to Sinbad, a company based in Indonesia that specializes in optimizing the supply chain industry. According to the post, the database contains 399,212 customer records and includes various information such as customer details, store data, tax numbers, addresses, and sales information. The breach allegedly occurred in October 2024, and the data is being offered for $100 in Monero (XMR), with an additional option to purchase administrator and database access for $300.
A New Alleged SMS Bomber Service is Detected
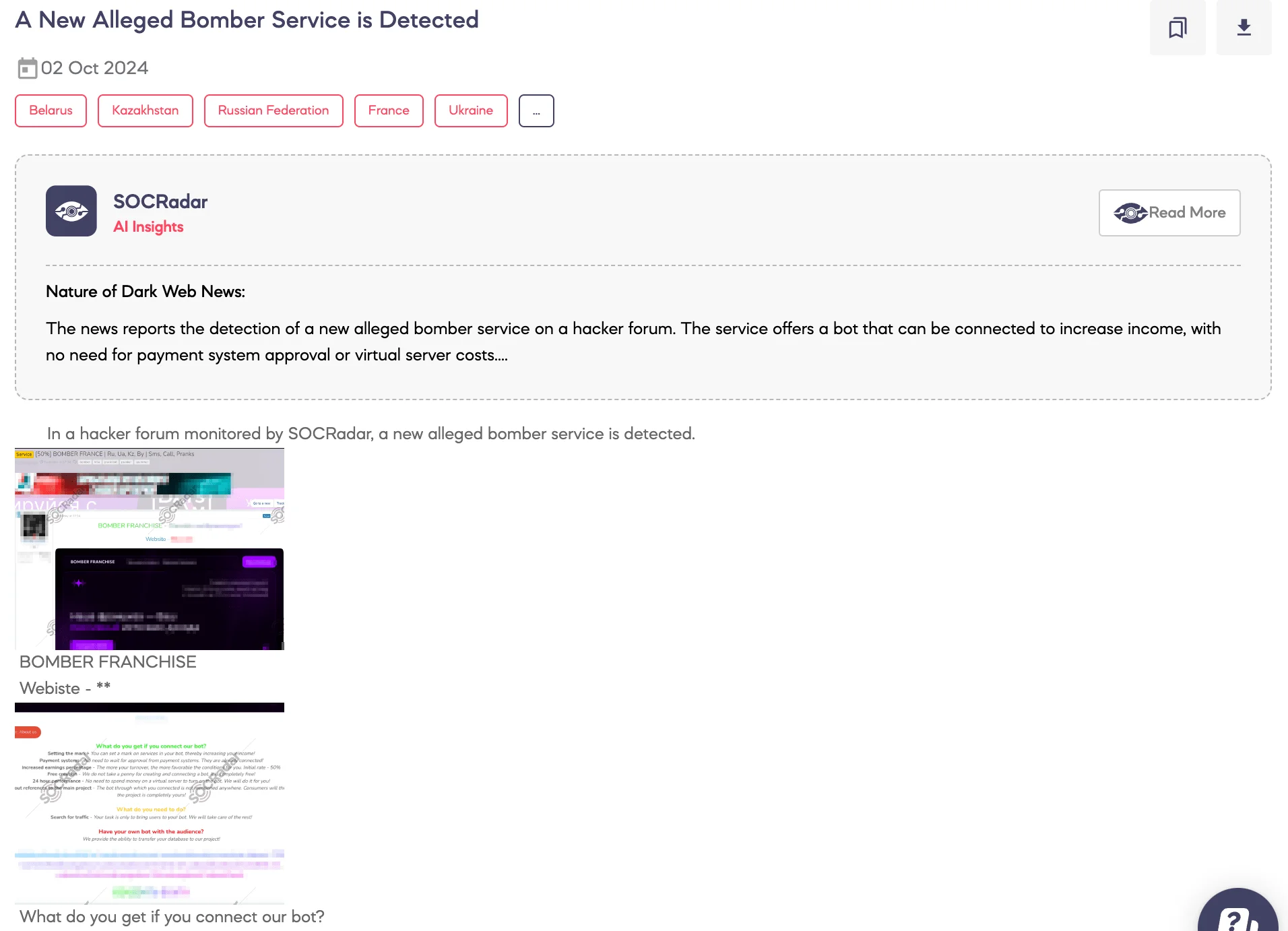
SOCRadar Dark Web Team detected a new alleged call and SMS bomber service advertised by a threat actor on a Dark Web forum. The actor claims users can connect their bot to the service, offering several enticing features. According to the actor, users can set specific targets within their bots, which may increase their potential earnings. Payment systems are reportedly pre-configured, eliminating the need for approval. The actor promises a favorable earnings structure, starting with a 50% commission rate that increases with higher turnover.
The service is designed to operate 24/7 without requiring users to spend money on a virtual server, as the threat actor maintains the bot. Furthermore, the bot is branded independently, meaning consumers will believe it to be a separate project, unlinked to the actor’s main operation. The only requirement for users is to generate traffic by bringing users to the bot. The actor can transfer their existing database into the service for those who already have their bot and audience.
Database of BMW is Allegedly Leaked
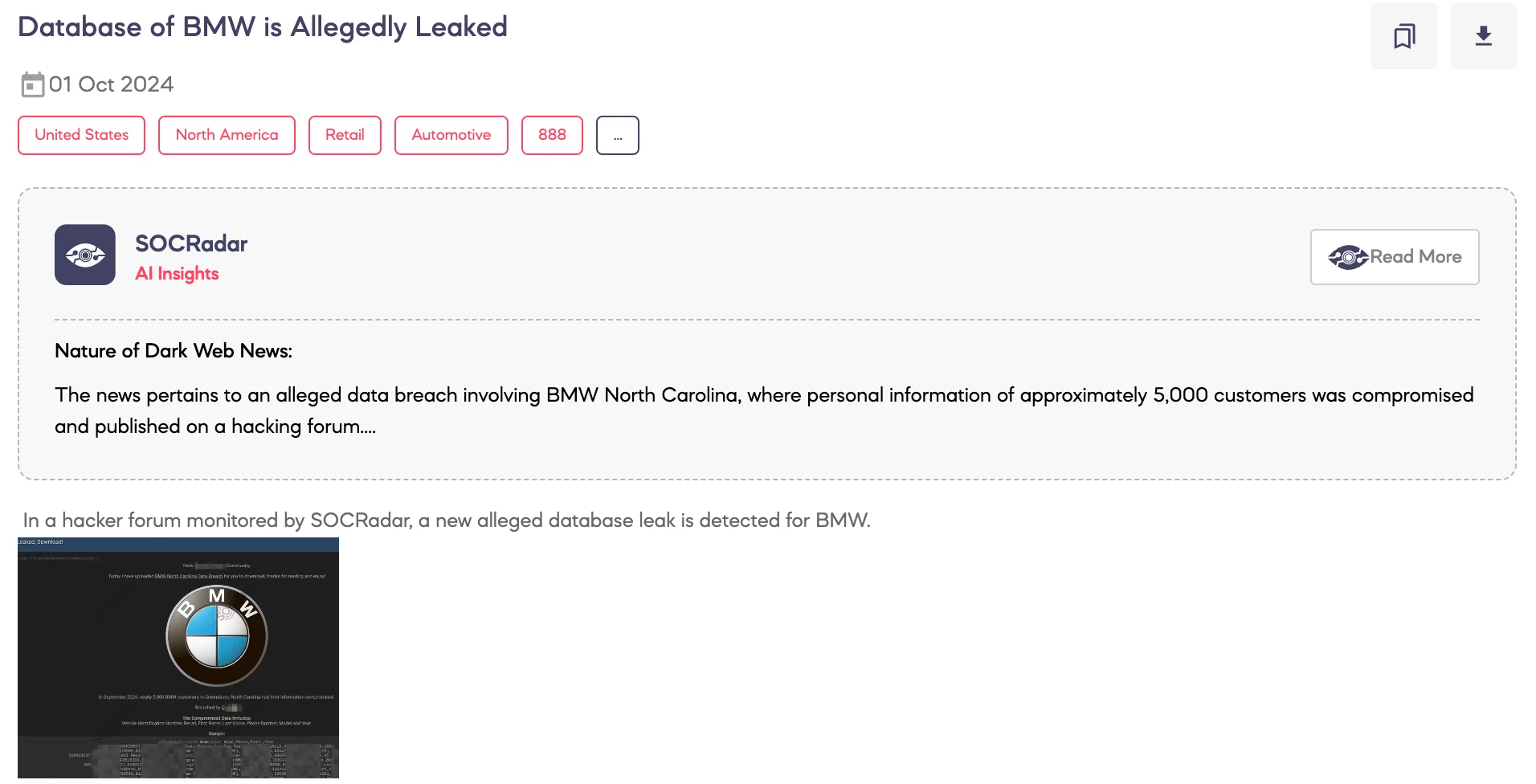
SOCRadar Dark Web Team detected a post on a hacker forum that a threat actor has allegedly leaked a database containing information related to BMW customers in North Carolina. This claim was observed on a hacker forum monitored by SOCRadar.
The post, made by the threat actor, announces the upload of data from a BMW North Carolina data breach that occurred in September 2024. According to the actor, nearly 5,000 BMW customers from Greensboro, North Carolina, had their information compromised, which was published on the forum.
The compromised data allegedly includes Vehicle Identification Numbers (VIN), recall details, first and last names, phone numbers, and the models and years of the vehicles. The threat actor provided a sample of the leaked data, showcasing the fields: VIN, recall information, first name, last name, phone number, model, and year of the vehicles involved.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































