
Dark Web Profile: APT35
APT35, also known as Charming Kitten, Phosphorus, Mint Sandstorm, and many other names, is an Iranian state-sponsored cyberwarfare group classified as an advanced persistent threat by multiple organizations and government officials. In December 2017, the group was identified as a nation state-backed advanced persistent threat, despite not exhibiting a high level of sophistication.
Who is APT35?
APT35, also known by various aliases such as Charming Kitten, Phosphorus, and Mint Sandstorm, is an Iranian state-sponsored cyber-espionage group active since at least 2014. The group has been involved in numerous cyber espionage campaigns targeting various sectors globally.

Threat actor card for APT35
In 2014, the group launched one of the most sophisticated internet-based spying campaigns organized by Iranian threat actors—a campaign conducted via social media.
In 2017, APT35 was implicated in a cyberattack on HBO, resulting in the leak of 1.5 terabytes of data, including unaired episodes of popular television series, Game of Thrones. The U.S. Department of Justice indicted Behzad Mesri, alleging his involvement in the attack and his affiliation with the group.
Between August and September 2019, Microsoft reported that APT35 attempted to compromise email accounts associated with a US presidential campaign, current and former U.S. government officials, journalists, and prominent Iranians living outside Iran.
In 2021, Google’s Threat Analysis Group highlighted APT35’s use of conference-themed phishing emails and the exploitation of Telegram for operator notifications.
In 2022, Google’s Threat Analysis Group identified a new tool developed by APT35, dubbed HYPERSCRAPE, designed to steal data from well-known email providers. This tool requires the target’s credentials to create a session on their behalf and acts in such a way that using old-style mail services appears normal to the server, downloading the victim’s emails and making changes to hide its fingerprint.
What are APT35’s Relations with Other Iranian Cyber Espionage Groups?
APT35 is an Iranian state-sponsored cyber espionage group affiliated with the Islamic Revolutionary Guard Corps (IRGC). Over time, various cybersecurity organizations have identified overlaps and distinctions between APT35 and other Iranian threat actors, leading to a complex understanding of their interrelations.
Overlap with APT42
Mandiant assesses with high confidence that APT42 is an Iranian state-sponsored cyber espionage group operating on behalf of the IRGC Intelligence Organization (IRGC-IO). While APT35 and APT42 share similarities in their affiliations and some operational tactics, Mandiant distinguishes between the two based on differences in targeting patterns, Tactics, Techniques, and Procedures (TTPs). Specifically, APT42 focuses on individuals and organizations of strategic interest to Iran, such as dissidents, activists, and researchers, employing credential harvesting and surveillance operations.
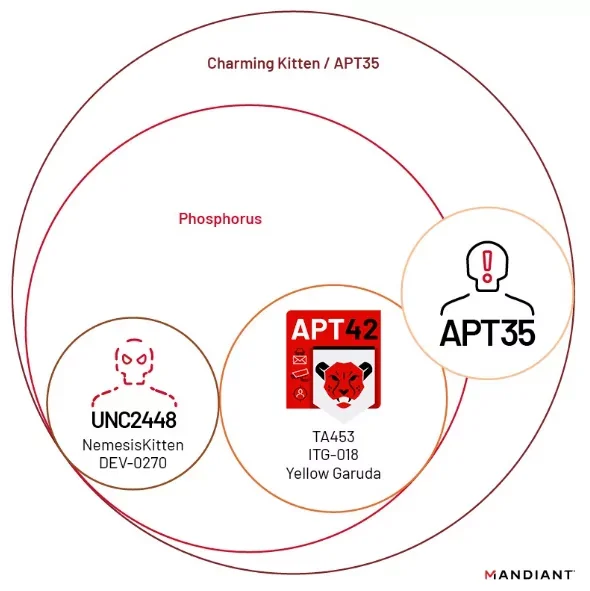
Diagram of Phosphorus and Charming Kitten (Mandiant)
Shared Aliases and Potential Connections
The cybersecurity community often assigns multiple aliases to threat groups based on observed activities and characteristics. For instance, MITRE ATT&CK® associates APT35 with several other names, including Magic Hound, TA453, COBALT ILLUSION, ITG18, Phosphorus, Newscaster, and Mint Sandstorm. This suggests potential overlaps or collaborations between these groups, although the exact nature of their relationships remains a subject of analysis.
Thus, while APT35 shares certain characteristics and aliases with other Iranian cyber espionage groups, specific distinctions in their targeting and operations suggest they function as separate entities under the broader umbrella of Iran’s state-sponsored cyber activities.
What are APT35’s Techniques?
APT35 conducts its operations by adhering to a structured attack lifecycle that aligns with the Cyber Kill Chain framework. It employs social engineering, credential theft, malware deployment, and persistence mechanisms to achieve its goals. Their methodology allows for prolonged access to compromised environments, which facilitates espionage and data exfiltration.
Reconnaissance – Identifying and Profiling Targets
APT35’s operations commence with the extensive gathering of open-source intelligence, where publicly available information is utilized to map organizational structures and identify key individuals. Targets are selected based on their access to sensitive systems, geopolitical relevance, or involvement in research fields of interest.
The creation of fake personas and the utilization of impersonation tactics are common practices used to initiate contact with targets. Online platforms, email, and messaging applications serve as initial engagement points, where targets are approached under the pretense of professional or academic collaboration.
The preparation of infrastructure occurs simultaneously, and includes the creation of spoofed domains, lookalike websites, and phishing pages designed to mimic trusted services. These resources establish the groundwork for credential theft and malware deployment in subsequent stages.
Weaponization – Crafting Payloads for Initial Compromise
Once reconnaissance efforts identify viable targets, weaponized payloads are crafted. These typically include malicious documents, browser-based exploits, and phishing frameworks that are customized to the target’s environment. Common techniques used by APT35 include:
- Malicious Macros & Remote Template Injection: Office documents embedded with macros or remote template links that download additional payloads upon opening.
- Credential Harvesting Portals: Fake login pages that mimic webmail, VPNs, or cloud services, and that capture authentication credentials upon user interaction.
- Browser Exploits & Session Hijacking: Malicious scripts injected into phishing sites to steal authentication cookies and bypass login protections.
Payloads are frequently updated to evade detection. They also incorporate sandbox evasion techniques and obfuscation mechanisms to ensure their execution within the target environment.
Delivery – Deploying Malicious Payloads to the Target
APT35 utilizes multiple delivery mechanisms to ensure high success rates. These include:
- Spear-Phishing Campaigns: Emails crafted with personalized lures, often referencing real-world events, research topics, or urgent security concerns.
- Social Media & Messaging Applications: Engagements initiated via professional networks, messaging platforms, and forums, where links to malicious content are shared.
- Watering Hole Attacks: Strategic compromise of websites frequented by target groups, injecting malicious scripts that exploit browser vulnerabilities.
Delivery infrastructure is maintained through rotating domain registrations, encrypted tunnels, and disposable communication channels, rendering detection and takedown efforts more challenging.
Exploitation – Executing Malicious Code for Initial Access
Once delivered, payloads exploit system vulnerabilities to gain execution. This is achieved through:
- PowerShell & Script-Based Attacks: Payloads leveraging obfuscated PowerShell commands to establish persistence and download secondary malware.
- Zero-Day & N-Day Vulnerabilities: Exploitation of unpatched software in browsers, VPNs, or email clients to execute arbitrary code.
- Multi-Factor Authentication Bypass: Techniques such as browser-in-the-middle (BitM) attacks and session token theft to gain access without user credentials.
Exploitation guarantees the establishment of a foothold within the network, permitting attackers to escalate privileges and deploy persistence mechanisms.
Installation – Establishing Persistence for Long-Term Access
Once access is gained, persistence mechanisms are deployed to maintain control over the compromised system. These include:
- Remote Access Trojans (RATs): Stealthy malware that enables remote command execution and system surveillance.
- Credential Dumping & Lateral Movement Tools: Post-exploitation frameworks used to extract stored passwords and move within the network.
- Cloud-Based Persistence Mechanisms: Manipulation of OAuth tokens, cloud synchronization services, and API keys to maintain access even after password resets.
Persistence ensures continued presence within the target environment, allowing attackers to execute long-term surveillance and intelligence collection.
Command & Control (C2) – Managing Compromised Systems
To control infected hosts, communication channels are established using:
- Encrypted C2 Infrastructure: DNS tunneling, HTTPS-based callbacks, and cloud storage abuse for covert data transfer.
- Decentralized Communication Platforms: Messaging applications and anonymized services used for command execution.
- Custom C2 Protocols: Malicious payloads configured with hardcoded domains and fallback servers for redundancy.
These techniques enable real-time control over compromised systems, allowing attackers to issue commands, deploy additional malware, and exfiltrate stolen data.
Actions on Objectives – Data Exfiltration and Intelligence Collection
Once inside a network, attackers focus on intelligence gathering, data theft, and account takeovers. Objectives include:
- Exfiltrating Email & Confidential Documents: Downloading sensitive communications, research files, and strategic data.
- Surveillance & Keylogging: Monitoring user activities, logging keystrokes, and capturing screen recordings.
- Account Hijacking & Social Engineering Amplification: Using compromised accounts to expand operations, launch additional phishing attacks, or manipulate narratives.
Exfiltrated data is transferred using encrypted archives, cloud storage services, and C2 channels, ensuring minimal detection by network monitoring tools.
APT35’s operations follow a structured, multi-stage attack lifecycle, leveraging social engineering, credential theft, and sophisticated malware to conduct long-term espionage campaigns. Their adaptability and use of legitimate cloud services for persistence and C2 operations make detection challenging. Organizations must adopt multi-layered security defenses, including phishing-resistant authentication, endpoint detection, and behavioral analytics, to mitigate the risks associated with their tactics.
How to Defend Against APT35 and Iranian APT Threats
APT35, also known as Charming Kitten, is a persistent Iranian threat group that relies heavily on phishing, credential theft, and social engineering to infiltrate organizations. Defending against these attacks requires a layered security approach that focuses on email security, access controls, continuous monitoring, and incident response preparedness.
Strengthening Phishing and Social Engineering Defenses
APT35 frequently uses spear-phishing emails, fake login pages, and social media impersonation to trick victims into revealing their credentials. Organizations must implement advanced email security solutions and employee training to mitigate these risks.
- Email filtering and threat detection: Deploy AI-driven email security solutions that analyze email metadata, attachments, and embedded links for phishing indicators.
- Email authentication protocols: Implement DMARC, SPF, and DKIM to prevent domain spoofing and phishing email delivery.
- Phishing domain detection: Monitor for domain registrations that imitate legitimate company sites, using tools like SOCRadar’s Phishing Domain Detection to identify and block fraudulent domains.
- Security awareness training: Conduct regular phishing simulations and employee training to help users recognize and report phishing attempts.
Enforcing Strong Authentication and Access Controls
APT35 frequently targets cloud services and VPN credentials to gain unauthorized access. Organizations must enforce strong authentication mechanisms and restrict unnecessary privileges.
- Multi-factor authentication (MFA): Require MFA for all external-facing services, cloud accounts, and privileged systems to reduce the impact of stolen credentials.
- Zero Trust architecture: Implement continuous verification of users and devices, requiring authentication even for internal network traffic.
- Privileged access management (PAM): Limit administrative access to only those who need it and monitor privileged account activity for suspicious behavior.
Patching Vulnerabilities and Securing Public-Facing Infrastructure
APT35 is known to exploit unpatched software vulnerabilities to gain persistence in target environments. Keeping systems updated is crucial to preventing exploitation.
- Regular patch management: Apply security patches for operating systems, web applications, and third-party software as soon as they are released.
- Cloud and VPN security: Regularly audit cloud configurations and VPN access controls to prevent unauthorized remote access.
- Web application firewalls (WAFs): Deploy WAFs to filter malicious traffic and block exploitation attempts on internet-facing applications.
Monitoring for Indicators of Compromise and Threat Actor Tactics
APT35 is known for deploying custom malware, Remote Access Tools (RATs), and keyloggers to maintain persistence. Continuous monitoring is essential to detect and respond to potential intrusions.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to monitor for suspicious file executions, process injections, and unusual network activity.
- Intrusion Detection and Prevention (IDPS): Use network-based monitoring solutions to identify Command-and-Control (C2) traffic linked to APT35 operations.
- User behavior analytics: Detect anomalous user activity, such as unusual login locations, excessive data transfers, or unauthorized privilege escalations.
Securing Third-Party Access and Supply Chains
APT35 has a history of targeting third-party contractors, IT providers, and supply chains to bypass direct security controls. Organizations must ensure vendors adhere to strict security standards.
- Third-party risk assessments: Evaluate vendor security postures and require compliance with security frameworks like ISO 27001 or NIST 800-171.
- Limited third-party access: Implement role-based access controls (RBAC) for third-party users, ensuring they only have access to necessary systems.
- Continuous monitoring of external access: Set up real-time alerts for unexpected third-party activity or logins from high-risk regions.
Developing and Testing Incident Response Plans
Given APT35’s persistence, organizations should prepare for potential breaches by maintaining a well-documented and tested incident response plan.
- Incident detection and containment: Define clear escalation paths for responding to detected intrusions.
- Red team and tabletop exercises: Conduct real-world attack simulations to test response capabilities against phishing, credential theft, and malware intrusions.
- Secure backups and recovery plans: Maintain offline, encrypted backups of critical data and test restoration procedures regularly.
APT35 remains a persistent threat, leveraging social engineering, phishing, and credential theft to infiltrate organizations. To defend against these tactics, organizations must implement strong email security, enforce access controls, continuously monitor their networks, and prepare incident response strategies.
Leveraging SOCRadar’s Threat Actor Intelligence can provide real-time insights into APT35’s evolving tactics, helping organizations stay ahead of emerging threats and minimize the risk of compromise.
What are MITRE ATT&CK Tactics, Techniques, and Tools Used by APT35?
APT35 (Charming Kitten) employs a range of tactics and techniques mapped in the MITRE ATT&CK framework, primarily focusing on initial access, credential theft, persistence, and command-and-control (C2) operations. The group extensively uses phishing, custom malware, and legitimate tools to infiltrate and maintain access to target environments.
| Tactic | Technique | ID |
| Reconnaissance | Spearphishing for Information | T1598.002 |
| Gather Victim Identity Information | T1589 | |
| Resource Development | Compromise Infrastructure | T1584 |
| Initial Access | Spearphishing Link | T1566.002 |
| Spearphishing Attachment | T1566.001 | |
| Drive-by Compromise | T1189 | |
| Execution | User Execution: Malicious Link | T1204.001 |
| Persistence | Web Shell | T1505.003 |
| Account Manipulation | T1098 | |
| Privilege Escalation | Exploitation for Privilege Escalation | T1068 |
| Defense Evasion | Obfuscated Files or Information | T1027 |
| Indicator Removal on Host | T1070 | |
| Credential Access | Credential Dumping | T1003 |
| Input Capture: Keylogging | T1056.001 | |
| Discovery | System Information Discovery | T1082 |
| Account Discovery | T1087 | |
| Lateral Movement | Remote Services: SSH | T1021.004 |
| Command and Control | Web Service C2 | T1102 |
| Application Layer Protocol | T1071 | |
| Exfiltration | Exfiltration Over Web | T1041 |




































