CISA Issues Alert for Juniper Secure Analytics Vulnerabilities (CVE-2023-46604, CVE-2023-40787, CVE-2023-44487, and More)
In a recent alert, the Cybersecurity and Infrastructure Security Agency (CISA) emphasized that Juniper has released security updates to address multiple vulnerabilities in the Juniper Secure Analytics Virtual Appliance. This Security Information and Event Management (SIEM) system compiles large volumes of event data in near real-time, catering specifically to virtualized IT and cloud environments.The vulnerabilities, discovered during external security research, vary in severity, also encompassing critical and high-severity issues. The agency cautions that threat actors could exploit any of these vulnerabilities to gain control of an affected system. Therefore, it urges organizations to promptly identify and mitigate these potential risks.
Which Versions of Juniper Secure Analytics Are Affected?
The vulnerabilities impact Juniper Secure Analytics (JSA) Series Virtual Appliance in all versions up to 7.5.0 UP7, and Juniper has addressed them in JSA 7.5.0 UP7 IF03.
Details of Critical and High-Severity CVEs
Juniper’s advisory highlights two vulnerabilities of critical severity:
CVE-2023-46604 (CVSS Score: 9.8): The Java OpenWire protocol marshaller is susceptible to Remote Code Execution (RCE). Exploiting this vulnerability could enable an attacker with network access to a Java-based OpenWire broker or client, to execute arbitrary shell commands.
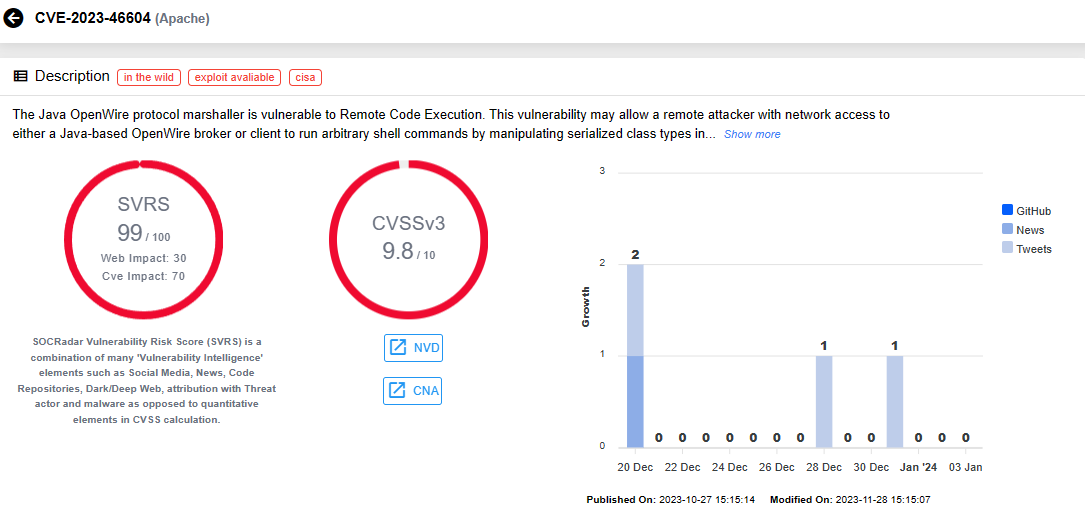
Vulnerability card for CVE-2023-46604 (SOCRadar Vulnerability Intelligence)
CVE-2023-40787 (CVSS Score: 9.8): In SpringBlade V3.6.0, a SQL injection vulnerability arises when user-submitted parameters lack necessary quotation marks during SQL query execution.
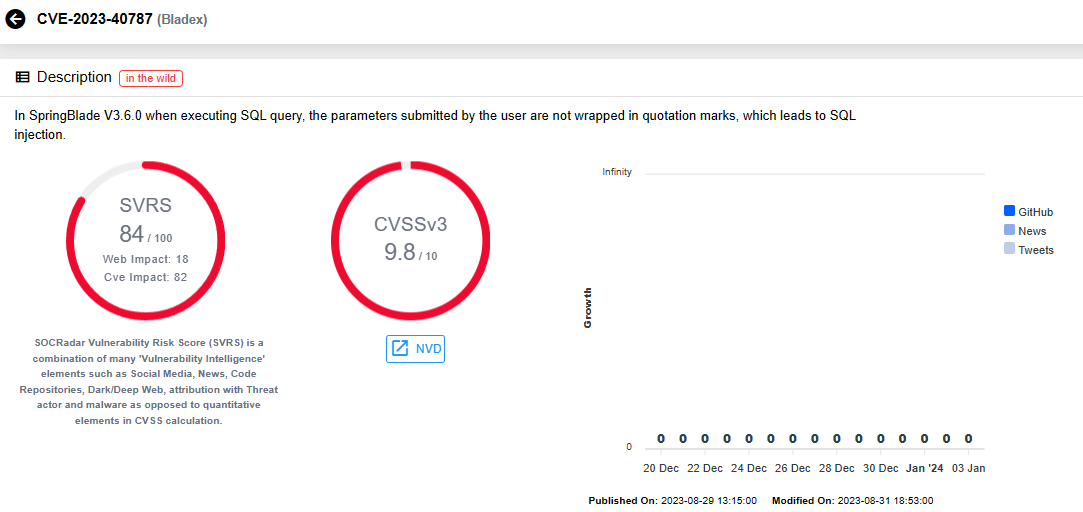
Vulnerability card for CVE-2023-40787 (SOCRadar Vulnerability Intelligence)
As of now, Juniper SIRT is unaware of any exploitation activity targeting Juniper instances via these vulnerabilities.
Among all the vulnerabilities included in the advisory, seven are classified as high-severity. Notably, one of these high-severity vulnerabilities relates to a previously discovered issue, known as the Rapid Reset attack:
CVE-2023-44487 (CVSS Score: 7.5): The HTTP/2 protocol is susceptible to a Denial-of-Service exploit, causing server resource consumption. This vulnerability, observed in the wild from August to October 2023, enables quick reset of multiple streams through request cancellation.
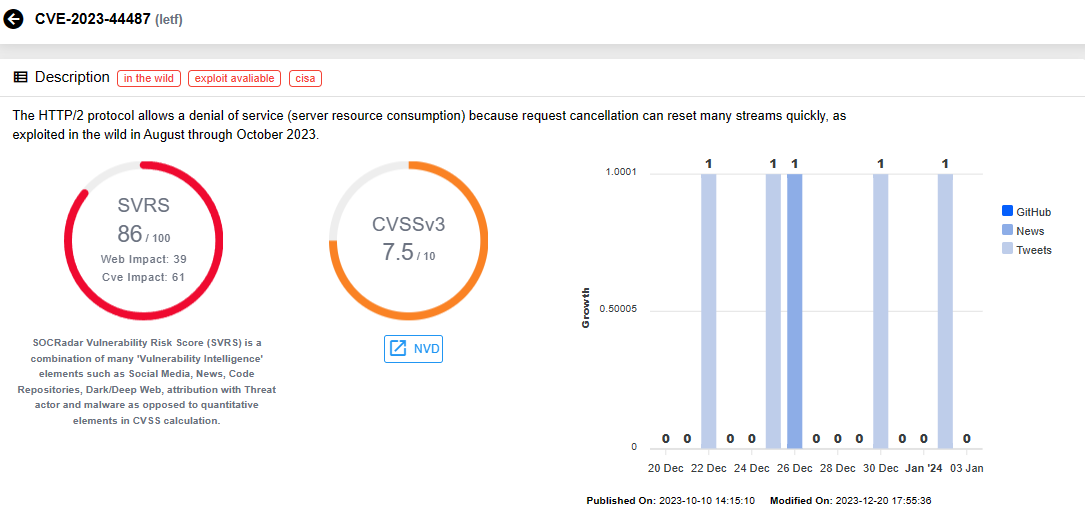
Vulnerability card for CVE-2023-44487 (SOCRadar Vulnerability Intelligence)
Additional information about the Rapid Reset vulnerabilities can be found in a previous SOCRadar blog post.
Meanwhile, three of the high-severity CVEs carry CVSS scores of 7.8:
CVE-2023-32233 (CVSS Score: 7.8): In Linux kernel up to version 6.3.1, a use-after-free vulnerability is triggered during batch request processing. It allows unprivileged local users to gain root privileges by exploiting arbitrary read/write access to kernel memory, due to mishandling of anonymous sets.
CVE-2023-34040 (CVSS Score: 7.8): Spring for Apache Kafka versions 3.0.9 and earlier and versions 2.9.10 and earlier are susceptible to a deserialization attack, contingent upon uncommon configurations. Specifically, when users do not set an ErrorHandlingDeserializer for key and/or value, and certain container properties are explicitly configured as true, untrusted sources can potentially execute the attack.
CVE-2023-35001 (CVSS Score: 7.8): Linux Kernel nftables exhibits an Out-Of-Bounds Read/Write vulnerability, specifically in the poor handling of vm register contents by nft_byteorder. This issue is exploitable when CAP_NET_ADMIN is present in any user or network namespace.
The remaining high-severity vulnerabilities in the Juniper Secure Analytics advisory, with CVSS scores of 7.5, namely CVE-2023-36478, CVE-2023-41835, and CVE-2023-46589, impact Eclipse Jetty, Apache Struts, and Apache Tomcat, respectively. These vulnerabilities have the potential to result in Denial-of-Service (DoS) attacks, request denial, and request smuggling.
For further information about the vulnerabilities affecting Juniper Secure Analytics, visit the official advisory here.
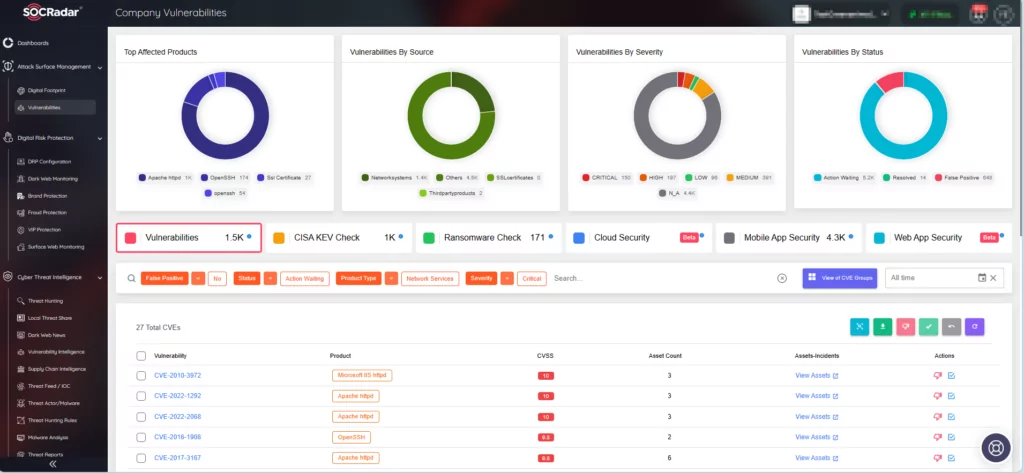
How Can SOCRadar Help?
SOCRadar ensures timely identification and response to critical vulnerabilities. The platform’s real-time alert system coupled with comprehensive Vulnerability Intelligence enables organizations to stay informed about vulnerabilities targeted by threat actors. The platform offers actionable insights and contextual information with its alarms, streamlining the response process.
SOCRadar’s Vulnerability Intelligence
Additionally, the Attack Surface Management (ASM) module by SOCRadar ensures continuous monitoring of your digital assets for emerging threats. This module provides detailed information about your asset inventory and enables monitoring for security vulnerabilities that could potentially impact your organizational assets.