Cloudflare Protection Bypass Vulnerability on Threat Actors’ Radar
Cloudflare, a leading cybersecurity provider, faces a security challenge due to vulnerabilities that could put its customer environments at risk. Researchers at Certitude have identified vulnerabilities that allow attackers to bypass Cloudflare’s protection mechanisms, leaving customers exposed to attacks.
The issue stems from gaps in the shared infrastructure within Cloudflare, which can render customer-configured protection mechanisms insignificant. Attackers can take advantage of the trust relationship between Cloudflare and customer websites by using Cloudflare accounts.
Researchers initially reported the problem to Cloudflare through a bug-bounty program in March. The issue was classified as “Informative,” and closed. The researchers have disclosed it publicly in late September – approximately six months after the bug informative – to help customers assess their configurations and prevent possible exploitation.
Following the disclosure, there has been notable activity among dark web threat actors, indicating a potential interest in targeting these vulnerabilities.
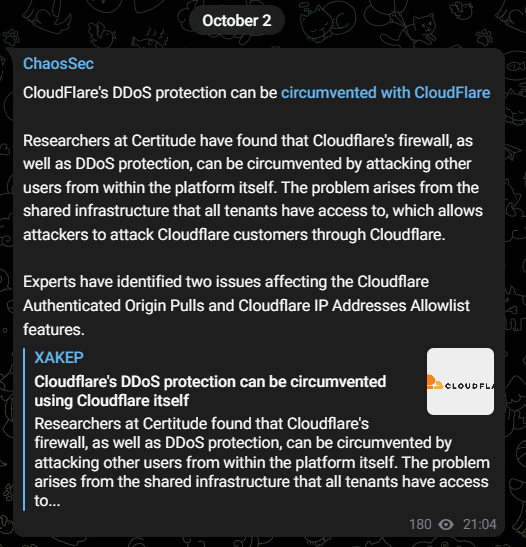
Cloudflare Vulnerability Draws the Attention of ChaosSec
The threat actor known as “ChaosSec” recently shared news of the Cloudflare vulnerability on its Telegram channel. This suggests that some threat actors may have been enticed by the opportunity presented by Cloudflare vulnerabilities and could be gearing up to exploit them in actual attacks in the near future.
Who Is ChaosSec?
ChaosSec is a newly emerged DDoS threat actor, active since early March 2023. This Russian-speaking group focuses its attacks on targets aligned with pro-Russian interests. Their targets have spanned across different countries, including Latvia, Romania, and France. Additionally, ChaosSec has displayed an interest in targeting NATO entities as part of its operations.
Understanding the Vulnerability: How Can Attackers Bypass Cloudflare Protections?
Cloudflare, to offer its protective solutions, maintains a network of reverse-proxy servers. These servers are strategically positioned between a customer’s webserver (the origin server) and its users, and actively analyze incoming traffic for any signs of malicious activity.
Researchers have identified two mechanisms that hinge on the assumption that traffic originating from Cloudflare towards the origin server is inherently trustworthy, while traffic from other origins should be blocked.
The subsequent section outlines how threat actors can capitalize on this trust in Cloudflare in two mechanisms and bypass the protection measures configured by the customer. To exploit either of these two mechanisms, the attacker must know the origin IP address.
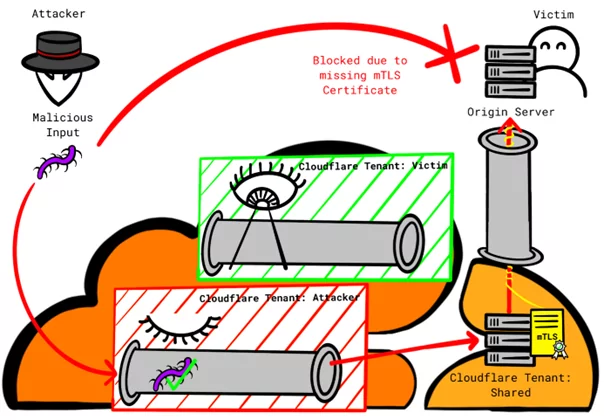
Mechanism 1: ‘Authenticated Origin Pulls’
This mechanism is considered highly secure by Cloudflare. It relies on client SSL certificates to authenticate connections between Cloudflare’s reverse-proxy servers and the origin server, which is called mTLS.
Configuring the custom certificate for this purpose requires using an API, thus, customers may opt for the more convenient Cloudflare certificate. However, using Cloudflare’s certificate allows any connection from Cloudflare, regardless of the tenant, to be accepted. The use of the same certificate for all tenants is the root cause of this problem.
Attackers can exploit this by setting up a custom domain pointing to the victim’s IP address. They then disable protection features for that custom domain in their tenant and tunnel their attacks through Cloudflare’s infrastructure, bypassing the victim’s protection features.
Mitigation:
To mitigate this issue, customers should use custom certificates, necessitating the creation and maintenance of their own origin pull certificates.
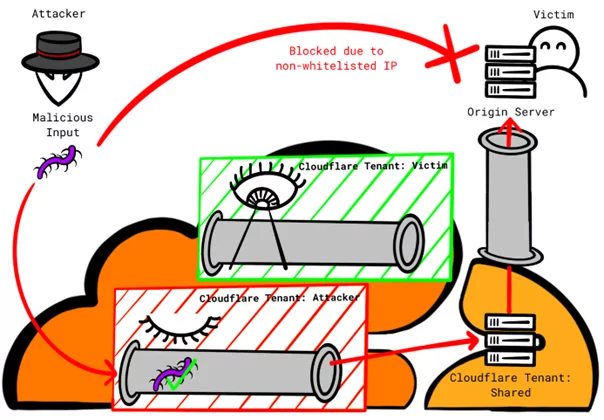
Mechanism 2: ‘Allowlist Cloudflare IP Addresses’
This mechanism is categorized as “moderately secure,” and can only be considered as defense-in-depth. It functions by rejecting connections that do not originate from Cloudflare’s IP address ranges.
This mechanism is also affected by the vulnerability, allowing all connections from Cloudflare, regardless of the tenant, to be accepted.
It can be exploited by attackers who direct their attacks through Cloudflare’s infrastructure, bypassing the victim’s protection features.
Mitigation:
To mitigate this issue, customers can opt for Cloudflare Aegis, which provides dedicated egress IP addresses rather than relying on the shared IP address range.
Proof-of-Concept (PoC) Cloudflare Setups
A PoC is available, which demonstrates the setups for a successful bypass of a domain protected by a Web Application Firewall (WAF), victim.test.
In the attack scenario, the attacker configures the domain attacker.test without any WAF protection, setting the same origin IP address as victim.test (203.0.113.42). As a result, the attacker can effectively send requests to 203.0.113.42 via attacker.test, a task that would be blocked if attempted through victim.test.
See the PoC here.
Recommendations
In light of this disclosure, it is anticipated that Cloudflare will offer clearer guidance to customers who have weaker configurations.
The main attack vector of the vulnerabilities are forwarding requests through attacker-controlled custom domain to victim’s origin IP through Cloudflare. A proper virtual host configuration of web servers play a crucial role to prevent exploitation of the vulnerabilities. Servers should be set to conduct Host header checks without exception, and refrain from providing a web response by default. This practice guarantees that access will be denied if the Host header does not match the expected value since only the attacker’s controlled custom domain would be shown in the Host header of the request, otherwise the attacker could not route malicious requests to the victim’s origin IP through Cloudflare. In essence, Virtual Host settings should be established accurately and with a strict approach.
Until Cloudflare issues further directives, the safest approach is to apply the mitigation measures and opt for secure alternatives over vulnerable mechanisms, thereby mitigating the risk of potential cyberattacks.
Stay Alert to Potential Cyber Threats with SOCRadar
SOCRadar continuously monitors the dark web, where security threats are ever-evolving. It actively sifts through and highlights critical events, providing valuable insights. Through the Dark Web Monitoring module, SOCRadar promptly keeps you informed about activities on Telegram channels, discussions among hackers in dark web forums, and cybersecurity incidents aimed at your digital assets.
By monitoring the dark web, you can stay alert to data breaches and potential attacks, enabling swift response to resolve issues and preventing minor incidents from turning into major catastrophes.