
Critical JetBrains TeamCity Authentication Bypass (CVE-2024-23917); CISA Adds Chrome Type Confusion to KEV (CVE-2023-4762)
JetBrains recently discovered a critical authentication bypass vulnerability in TeamCity On-Premises servers. This vulnerability could allow attackers to take over vulnerable instances with elevated privileges.
TeamCity is a powerful CI/CD tool, used in automating the Software Development Lifecycle (SDLC) pipeline. It is a popular choice for developers and DevOps teams due to its extensive features, flexibility, and ease of integration.
Due to the vulnerability, tracked as CVE-2024-23917 (CVSS: 9.8), an attacker with HTTP(S) access can bypass authentication checks.
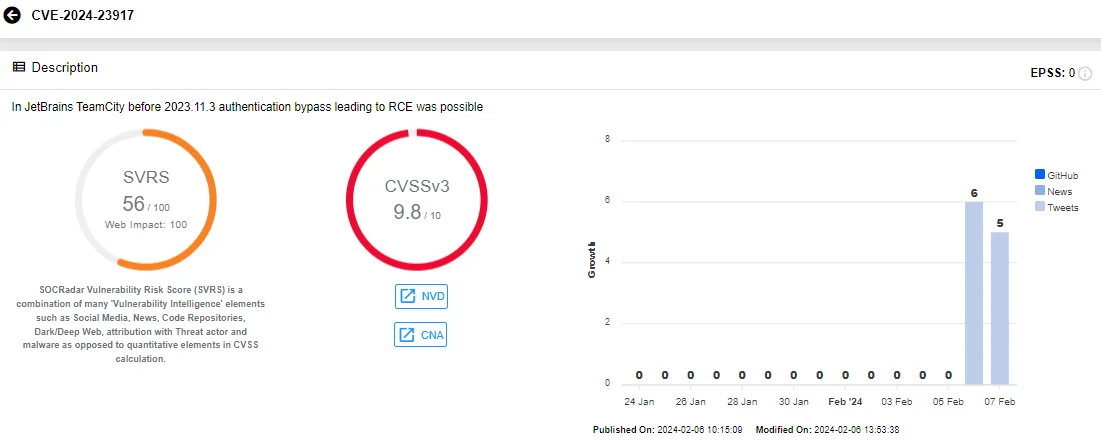
Details of CVE-2024-23917 (SOCRadar Vulnerability Intelligence)
Seizing administrative control over a TeamCity server, attackers could compromise the security of SDLC pipelines. Furthermore, the vulnerability can be exploited remotely and does not require user interaction.
The critical vulnerability affects all versions of TeamCity On-Premises from 2017.1 through 2023.11.2. JetBrains released TeamCity On-Premises version 2023.11.3 to address CVE-2024-23917 and advises users to update as soon as possible to prevent exploitation.
For those unable to update immediately, JetBrains has also provided a security patch plugin as a solution.
Warning for Exposed TeamCity Servers
If your TeamCity On-Premises server is publicly accessible over the internet and you are unable to update or apply the mitigation immediately, JetBrains recommends temporarily making it inaccessible until mitigation actions have been completed.
Currently, a Shodan search on TeamCity shows that there are approximately 2,300 instances exposed to the internet.
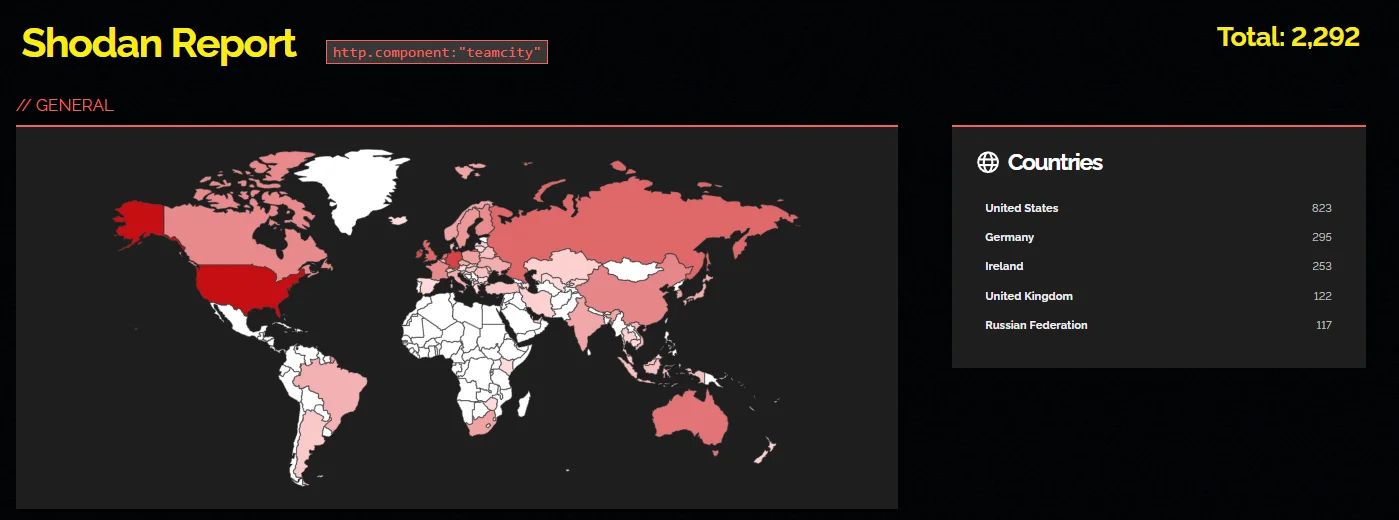
Shodan search on exposed TeamCity instances
SOCRadar’s Attack Surface Management (ASM) feature provides efficient tools for rapidly detecting, assessing, and resolving security vulnerabilities. With ASM, organizations acquire insights into their asset inventory and receive timely alerts regarding relevant security issues, enabling swift response and enhanced protection against potential threats.
Viev company vulnerabilities via SOCRadar ASM module
Type Confusion in Chrome’s V8 Enters the CISA KEV Catalog (CVE-2023-4762)
CISA has added a type confusion vulnerability in Google Chrome’s V8 JavaScript engine to its Known Exploited Vulnerabilities Catalog, citing evidence of active exploitation. The agency cautions that such vulnerabilities are common attack vectors and pose significant risks to the federal enterprise. Organizations are expected to patch the vulnerability by the deadline of February 27, 2024.
Tracked as CVE-2023-4762 (CVSS: 8.8, High severity), the vulnerability was reported to Google by an anonymous individual in August 2023. Google has addressed it in a September 2023 advisory.
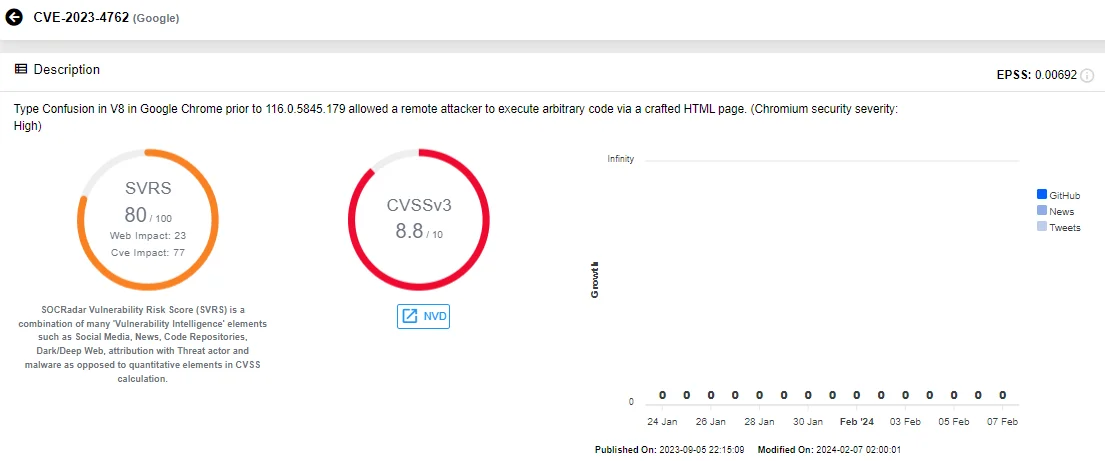
Details of CVE-2023-4762 (SOCRadar Vulnerability Intelligence)
In a separate blog post in September, Google mentioned the discovery of a zero-day exploit chain in the wild, which also involves the specific V8 type confusion vulnerability, CVE-2023-4762.
Intellexa’s Zero-Day Exploit Chain: Installing Predator Spyware & Exploiting Chrome’s CVE-2023-4762
The zero-day exploit chain, reportedly developed by the commercial surveillance vendor Intellexa, installed Predator spyware on devices. In the campaign, the exploit chain utilized a Man-in-the-Middle (MiTM) attack. If a target accessed any ‘http’ site, attackers injected traffic to redirect them to an Intellexa site, c.betly[.]me. Then, if the user matched the expected target, the site redirected them to the exploit server, sec-flare[.]com.
The MiTM delivery did not involve any user interaction, resembling a zero-click exploit. Upon redirecting the target to their exploit server, the exploit chain initiated execution.
For iOS, the exploit chain included three vulnerabilities: CVE-2023-41993 (an RCE in Safari), CVE-2023-41991: (Certificate validation issue), and CVE-2023-41992 (Local privilege escalation in the XNU Kernel).
The attacker also installed Predator on Android devices in Egypt, by MiTM injection and via one-time links sent to the target. Google TAG said they only obtained the initial renderer RCE vulnerability for Chrome, exploiting the V8 type confusion vulnerability, CVE-2023-4762.
Google believes Intellexa previously used this vulnerability as a zero-day before it was patched in early September.
Understanding the Timing of This Vulnerability in KEV Catalog
CISA has specific criteria for security vulnerabilities’ inclusion in the KEV Catalog, one being solid evidence of exploitation in the wild. Due to such criteria, inclusion in the catalog can take time.
To learn more about CISA KEV inclusion timeframes, read our blog post: CISA KEV Timeframe Problems While Prioritizing Vulnerabilities.
While the CISA KEV catalog is a valuable resource, guiding federal organizations in remediation processes for critical vulnerabilities under exploitation, organizations should not rely solely on it for information on exploited vulnerabilities. For this purpose, consider using threat intelligence platforms such as SOCRadar.
SOCRadar delivers comprehensive Vulnerability Intelligence, providing the latest updates on known vulnerabilities, associated exploits, repositories, and emerging hacker trends. Equipping organizations with critical information, SOCRadar aids them to stay ahead of potential threats and bolster their vulnerability management strategies.
SOCRadar Vulnerability Intelligence
Sign up for a free edition of SOCRadar XTI to gain access to its full capabilities.



































