
Beyond the Veil of Surveillance: Private Sector Offensive Actors (PSOAs)
Privacy and surveillance are two sides of a coin, and the conditions that have blurred the boundaries between them have also paved the way for the thriving of cyber commercial surveillance technologies and the offensive private actors industry.
The landscape of commercial cyber surveillance is becoming increasingly sophisticated with the technologies that can be used to track and monitor individuals’ online activity, such as their emails, web browsing history, and phone calls, and are being used by a wide range of actors, including governments, law enforcement agencies, and private companies.
While surveillance technologies are legal under national or international laws, there are rising concerns about privacy, human rights, transparency, accountability, and ethical considerations. In this context, Apple and Facebook have separately filed lawsuits against NSO Group, allegedly targeting WhatsApp and Apple users. The balance between security, individual rights, and the ethics of technology is the key point of a world where private sector companies create and sell cyberweapons for consumers, businesses of all sizes, and governments.
An upcoming event, ‘ISSWorld Europe Intelligence Support Systems for Electronic Surveillance, Social Media/DarkNet Monitoring and Cyber Threat Detection‘ conference, serves as a platform for industry leaders, experts, and professionals to exchange knowledge and insights, let once again, the cybersecurity world to focus on cyber commercial surveillance technologies and offensive private actors.

What is Private Sector Offensive Actors (PSOAs)?
The global cyber-surveillance industry has made “surveillance as a service” that includes various tools and advanced malware such as ‘Pegasus,’ ‘DevilsTongue,’ and ‘Predator‘ widely accessible, empowering both government and non-government entities with capabilities exclusive to highly sophisticated actors.
Private sector offensive actors (PSOAs) are commercial entities that engage in the cyber-surveillance industry, creating and selling cyberweapons, including “zero-day” exploits and malicious software.
PSOAs present themselves as providers of general security and information analysis services to commercial customers and claim that their tools are designed to address security concerns. On the other hand, in many cases, since dissidents, human rights defenders, journalists, civil society advocates, etc., are victims of targeted surveillance by PSOAs; they are increasingly associated with human rights and democratic principles violation.
Private sector offensive actors operate through various business models. Two common models employed by these actors are access-as-a-service and hack-for-hire. In the access-as-a-service model, actors provide purchasers with complete end-to-end hacking tools for independent operations without involvement in targeting or running the process. In the hack-for-hire model, the purchaser shares detailed information, and the actor performs targeted operations on their behalf.
These actors offer highly sophisticated products that are costly and challenging to detect. These tools are designed to be secretly installed on smartphones, leveraging zero-day and zero-click vulnerabilities to seize remote control of the device and extract sensitive data. Particularly zero-click exploits require no interaction from the victim, making the attack even more covert and impactful.
One of the research that seeks to raise awareness about the escalating and evolving threat landscape, “Threat Report on the Surveillance-for-Hire Industry” by Meta (formerly the Facebook company), outlines the stages of the commercial surveillance chain: Reconnaissance, Engagement, and Exploitation. Each phase builds upon one before it, and various PSOAs within the industry specialize in different stages or provide support for the entire attack chain.
Reconnaissance involves discreetly profiling targets on behalf of their clients. This stage utilizes software to automate online data collection from social media, blogs, news media, forums, and the dark web to gather as much information as possible without alerting the targets.
Engagement focuses on establishing contact with the targets or individuals close to them to gain their trust, extract information, and deceive them into clicking on malicious links or files. So this is a crucial phase to detect and prevent compromise.
Exploitation is the final stage that aims to compromise the targets’ devices or accounts. Providers may create phishing domains or use malicious links to trick individuals into revealing their credentials for sensitive accounts like email, social media, financial services, or corporate networks.
Analysis of Surveillance Landscape
PSOAs have witnessed remarkable advancements over the years, marked by their increasing sophistication. Several key factors contribute to this evolution, including the exponential growth in online data for tracking and monitoring individuals’ online activity, new technologies that make surveillance tools more advanced, and the growing demand for such technologies from governments, law enforcement agencies, and private companies.
As PSOAs grew in popularity, they established a traditional defense in which their software is used to combat terrorism and organized crime. But, the disclosure and research outputs have provided substantial evidence to support claims that these ethically questionable software also pose a threat to human rights defenders, journalists, activists, and dissidents. FinFisher, Hacking Team, and Pegasus leaks are notable incidents that have brought these concerns to light.
FinFisher, a surveillance software developed and distributed by Gamma International, faced a significant breach in 2014. The leaked archive contained 40GB of information, including price lists, source codes, invoices, and other confidential data linking spyware purchases to specific clients. These leaks confirmed suspicions that commercial spyware developers were selling surveillance tools to authoritarian regimes for spying on civilians.
Another example is the Italian surveillance company Hacking Team, which experienced a massive 400-gigabyte data breach in 2015. The breach exposed internal documents, administrative emails, customer invoices, and source codes. The leaked information further substantiated findings that Hacking Team sold its software to governments with poor human rights records. The leak shed light on the extent of their activities and unveiled the company’s inner workings.
In 2021, the Pegasus Project, a consortium of sixteen media outlets, investigated a military-grade spyware -known as Pegasus- licensed by the Israeli NSO Group. The investigation uncovered fifty thousand phone numbers targeted by NSO clients. The victims encompassed Arab royal family members, business executives, human rights activists, journalists, politicians, and government officials; at least ten prime ministers, three presidents, and one king were also found on Pegasus target lists. The leak also exposed NSO Group clients from multiple countries.
These leaks have drawn attention to PSOAs and their involvement in the surveillance industry. However, the leaks have not significantly impacted the activities of the surveillance sector, as other PSOAs continue to compete for government contracts and private customers.
To have an overview of the surveillance landscape and the ongoing activities of PSOAs, SOCRadar researchers examined the “Global Inventory of Commercial Spyware and Digital Forensics” compiled by the Carnegie Endowment for International Peace Institution. The inventory draws information from reputable sources such as Citizen Lab, Freedom House, Privacy International, the Council on Foreign Relations’ Cyber Operations Tracker, the Electronic Frontier Foundation, Article 19, Access Now, and various research organizations. Data from prominent print and news media outlets, including The New York Times, Reuters, Haaretz, Financial Times, and The Wall Street Journal, is incorporated. The inventory focuses on incidents between 2011 and 2023, with the latest update in March 2023.
The dataset has listed 193 deployments of targeted surveillance technologies. The number of deployments by disclosed years is as follows:
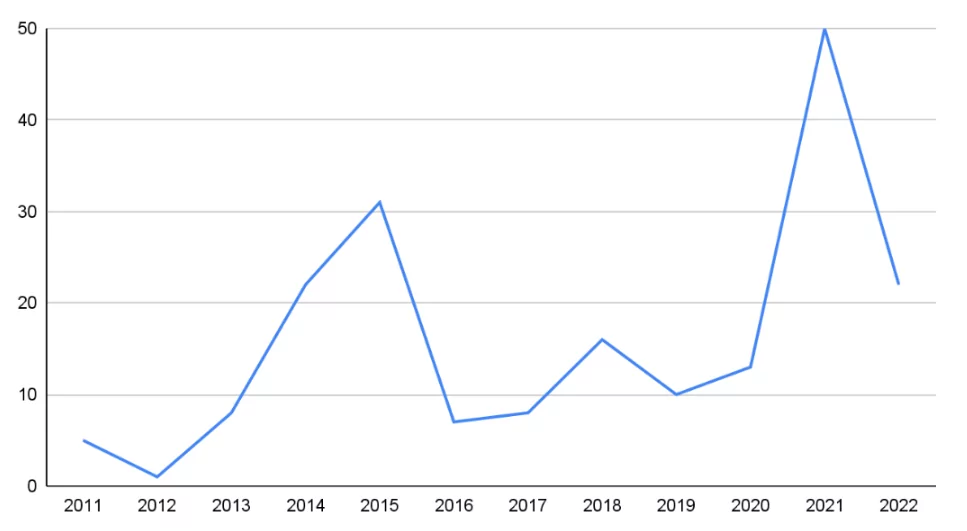
The leaks experienced by the critical actors of the industries mentioned above have drawn attention to PSOAs and their involvement in the surveillance industry. Researchers and journalists have focused more heavily on PSOAs. It is considered that the radical increases in software deployments detected in the dataset in 2014, 2015, and 2021 are a result of this focus.
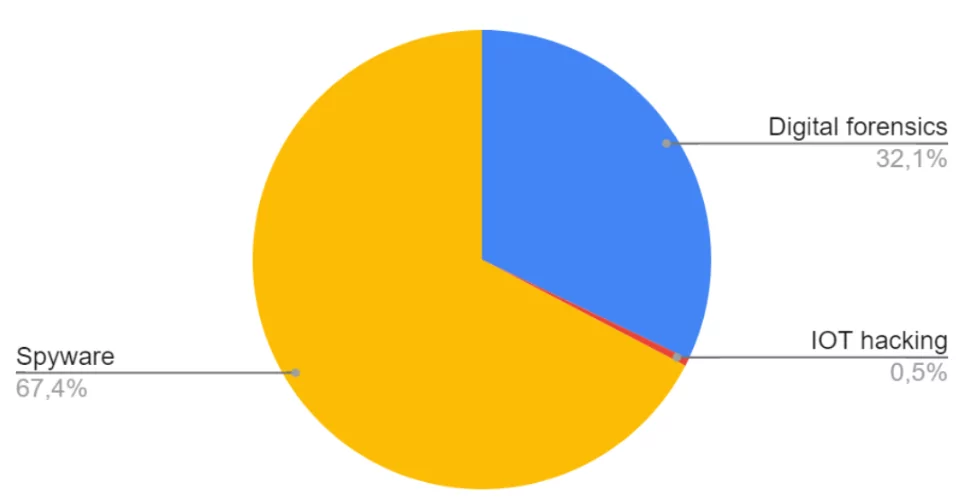
According to the inventory, 67,4% of the deployed technology is spyware, and 32.1%is digital forensics software, which requires a physical connection with the targeted device to extract and analyze stored data.
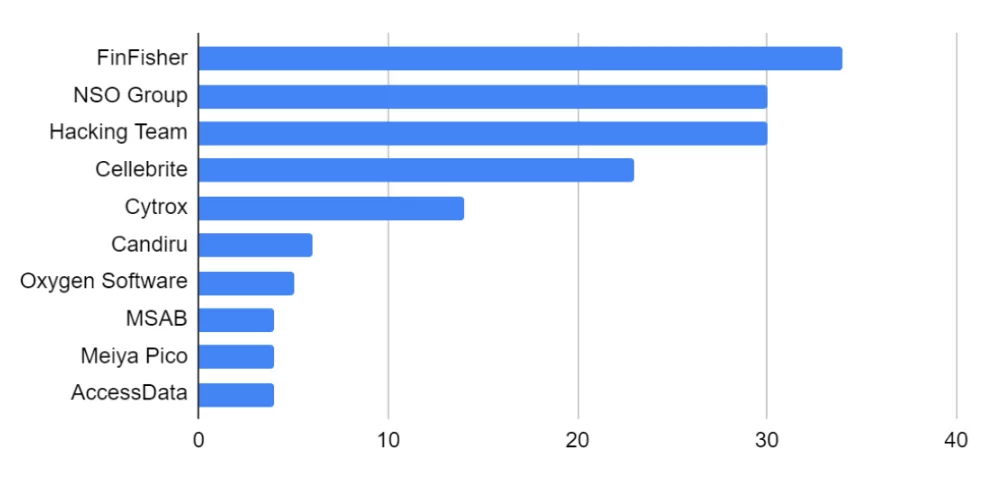
The database consists of 40 commercial entities, and the chart below displays the Top 10 among them. Notably, the first three entries in the chart are recognized players in the industry, namely FinFisher, NSO Group, and Hacking Team. These companies have gained more visibility due to leaked information about their activities and established industry presence over many years. The chart reflects the extensive research conducted on these actors and their significant impact on the industry.
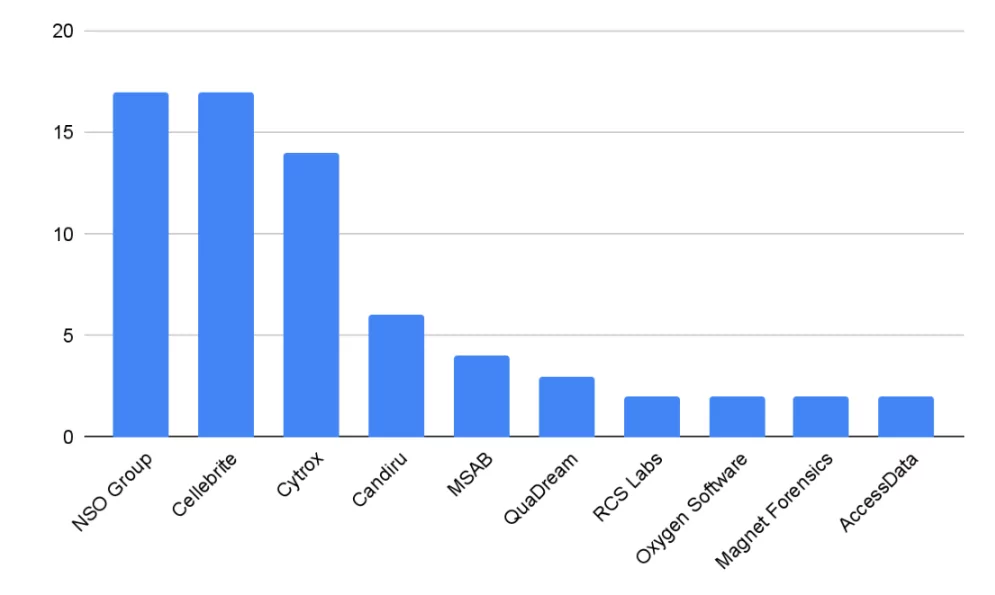
Additional analysis has been conducted on commercial entity data to gain insights beyond the influence of the three prominent entities and comprehend the recent dynamics and changes within the industry over the past three years.
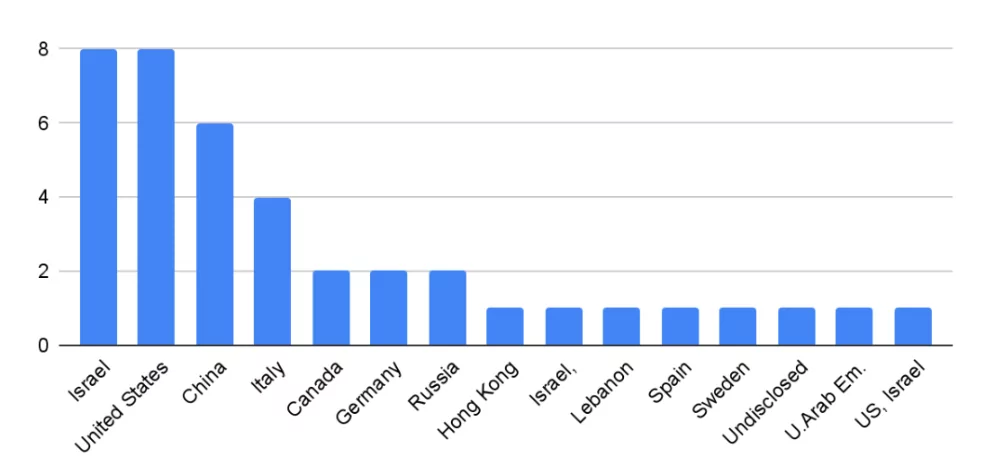
The Israeli dominance in the industry is underscored by the fact that five out of the top ten actors are of Israeli origin (QuaDream announced its shutdown by April 2023). The following chart displays the distribution of commercial entities based on their respective countries of origin:
The deployment of this surveillance software has been observed in 74 countries, with the top 10 most exposed countries listed below.
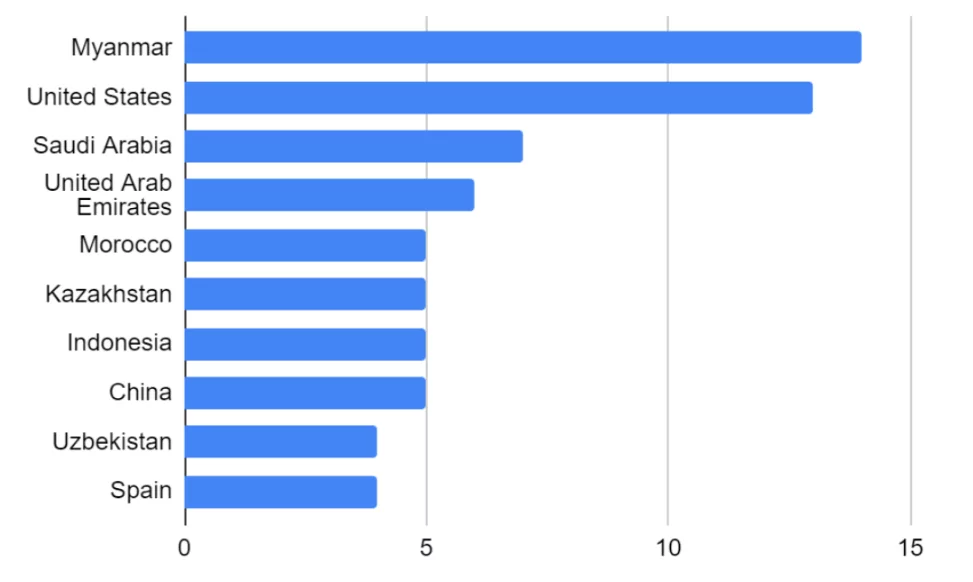
The distribution of the 74 countries by region is as follows:

Also, the Threat Report on the Surveillance-for-Hire Industry 2021 and 2022 by Meta has uncovered the presence of 13 PSOAs, with eight being outside the scope of the commercial entities listed in The Carnegie Endowment dataset. Meta has taken prompt and impactful measures, such as disabling multiple associated accounts and blocking the infrastructures of these entities on their platforms, namely Facebook and Instagram.
As mentioned above, the “ISSWorld Europe Intelligence Support Systems for Electronic Surveillance, Social Media/DarkNet Monitoring, and Cyber Threat Detection” conference is important in the industry. Among the 48 PSOAs mentioned in the Carnegie Endowment and Meta reports, 11 of them are notable sponsors of ‘ISSWorld Europe 2023’. Notably, the Lead Sponsor of the event is the NSO Group. This sponsorship highlights the active involvement and support of these PSOAs in the conference, further underscoring their role in the cyber commercial surveillance industry.
The event features presentations and workshops about the challenges and trends in commercial cyber surveillance and discussions on privacy concerns, legal frameworks, and ethical considerations. ISSWorld Europe 2023 also covers a range of significant topics that offer insights into the current agenda of the surveillance industry. By exploring these topics, it is possible to gain valuable insights into current trends and developments. Here are some key topics of focus at ISSWorld Europe 2023:
- Understanding Advanced Techniques to Defeat (or Work Around) Encrypted Third-Party Services, Bitcoin Anonymity, TOR/HS, and iPhone Encryption
- Exploiting Latest Generation Devices
- Password Cracking in Practice
- Social Network Monitoring, Artificial Intelligence, and Analytics Product Training
- Threat Intelligence Gathering and Cyber Security Product Training
- Investigating DarkWeb, Bitcoin, Altcoin, and Blockchain Transaction
- Mobile Signal Intercept Training and Product Demonstrations
- Electronic Surveillance Training and Product Demonstrations
As another reference for PSOAs, CERT-EU (Computer Emergency Response Team for the EU institutions, agencies, and bodies) monthly cyber brief is a valuable source of timely information and analysis on cybersecurity threats and trends. The briefs cover various topics, including malware, vulnerabilities, cyber attacks, and security recommendations. Some recently mentioned incidents of PSOAs in the monthly cyber briefs of CERT-EU are listed below:
- Israeli PSOA called QuaDream reportedly sells a mobile device surveillance platform called REIGN to governments for law enforcement purposes shutting down in April 2023.
- According to news sources, the Polish intelligence services targeted a member of the opposition, the mayor of the Polish city of Sopot, with the cyberespionage malware Pegasus in March 2023.
- The New York Times reported, on March 20, that an American citizen who worked on Meta’s security and trust team, based in Greece, was targeted with the cyberespionage tool Predator by the Greek intelligence service.
- In January 2023, the US Supreme Court denied NSO Group’s petition to dismiss a lawsuit alleging their exploitation of the communication app WhatsApp in 2019.
- Google Threat Analysis Group (TAG) released a technical analysis on the exploitation framework Heliconia, tied to Spain-based vendor Variston IT, which exploits vulnerabilities in Chrome, Firefox, and Microsoft Defender in November 2022.
- France-based company Avisa Partners is revealed to be involved in misinformation activities and implicated in a cyberattack targeting opponents of the Chadian regime in October 2022.
- NSO Group reportedly claimed to have sold Pegasus spyware to 14 EU governments using export licenses issued by the Israeli government in July 2022.
- In July 2022, Microsoft reported on the activities of Austria-based PSOA DSIRF, which sells Windows and Adobe exploits.
- Journalists and other high-interest individuals in the Middle East were infected with Candiru spyware in July 2022.
- In June 2022, the European Parliament’s committee confirmed the use of NSO Group software by at least five EU countries.
- Italian private-sector offensive actor RCS Labs’ spyware, was used in Kazakhstan in June 2022.
Conclusion
The rapid development of the surveillance industry has outpaced the establishment of adequate legal frameworks for PSOAs. Even in cases where regulations exist, they often lack clarity regarding proper investigative techniques and fail to provide sufficient judicial oversight. Furthermore, the market in which PSOAs operate is unclear, and the procurement, sale, and export of surveillance tools typically occur in opaque conditions that impede effective oversight mechanisms.
Understanding the cyber commercial surveillance industry’s threat landscape is crucial to mitigate the risks posed by PSOAs. Also, it is necessary to prioritize transparency, accountability, and the ethical use of surveillance technologies. All these challenges require ongoing dialogue among stakeholders, including governments, industry leaders, civil society organizations, and the public. By fostering a comprehensive understanding of the challenges and promoting responsible practices, it is possible to balance security and privacy while upholding fundamental rights and democratic principles in the digital age.
Individuals can protect themselves against attacks that exploit simple mistakes victims make, such as clicking on a link, opening untrusted documents, or neglecting device updates, by adopting basic security measures like maintaining awareness, enabling multi-factor authentication, and keeping devices and applications up-to-date. However, PSOAs also employ advanced techniques like zero-day and zero-click exploits that require no victim interaction, enabling surveillance. In response, major big tech companies continue developing counter solutions to enhance security and protect users against sophisticated surveillance threats. For example, Apple introduced ‘Lockdown Mode,’ a feature designed to improve device security for high-risk individuals by limiting functionality. Samsung has developed ‘Samsung Message Guard,’ a security system for Galaxy devices that scans files for malicious code, quarantining and blocking them from accessing the operating system.
Continuous monitoring and proactive measures are needed to mitigate the impact of PSOAs. Actionable cyber threat intelligence solutions like SOCRadar Extended Threat Intelligence provides valuable insights into emerging cyber surveillance threats, enabling individuals and organizations to safeguard their privacy and security.




































