
Critical Microsoft Power Platform Vulnerability: Proactive Security Methods to Prevent Exploitation
Microsoft fixed a critical vulnerability in its Power Platform after facing criticism for the delayed response. Tenable reported the vulnerability to Microsoft on March 30, 2023, and an official fix was issued in August. The security vulnerability specifically impacts Power Platform Custom Connectors that utilize Custom Code, enabling customers to write code for their custom connectors.
What is the potential impact of Microsoft Power Platform vulnerability?
Microsoft explained that the vulnerability could potentially allow unauthorized access to Custom Code functions used for Power Platform custom connectors. If sensitive information or secrets were embedded in the function, it would pose a risk of information disclosure.
According to Tenable, the vulnerability could permit limited, unauthorized access to cross-tenant applications and sensitive data, including authentication secrets.
What causes the vulnerability in Microsoft Power Platform? How does an exploit work?
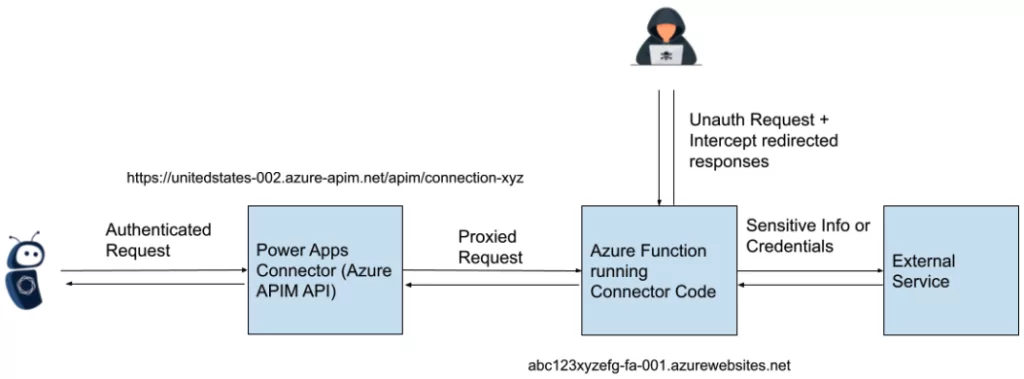
Tenable states that the problem was caused by insufficient access control to Azure Function hosts, which are launched as part of creating and operating custom connectors in Microsoft’s Power Platform.
Certain connectors in the Power Platform connect to and communicate with other services using custom C# code. This code is deployed as an Azure Function with an HTTP trigger, managed by Microsoft. Despite most customer interactions with custom connectors occurring through authenticated APIs, the API endpoints facilitated requests to the Azure Function without requiring authentication. This enabled attackers to intercept OAuth client IDs and secrets by exploiting unsecured Azure Function hosts.
Are there any reports of exploitation?
Microsoft clarified that there is no active exploitation of the vulnerability in the wild. Their investigation revealed anomalous access only by the security researcher who reported the incident.
Is there an available Proof-of-Concept (PoC) exploit code?
Tenable has released a PoC, which allows for finding vulnerable connector hostnames and crafting POST requests to interact with unsecured API endpoints. To see the PoC, click here.
Microsoft-Tenable Dispute: Delayed Fix Raises Concerns
On July 6, 2023, Microsoft informed Tenable that they had fixed the issue. However, on July 10, 2023, Tenable informed Microsoft that the fix was incomplete.
On August 2, 2023, Microsoft implemented a fix for the previously affected hosts.
Tenable CEO Amit Yoran accused Microsoft of demonstrating “gross irresponsibility, if not blatant negligence” due to the delay in addressing this critical flaw.
Yoran expressed concerns about Microsoft’s lack of transparency and their culture of toxic obfuscation, questioning whether they can be trusted to act responsibly and protect their customers. According to Yoran, Microsoft’s track record raises significant risks for everyone involved.
Microsoft responded by acknowledging that not all fixes can be implemented quickly and highlighted their commitment to swiftly respond to any active exploit in order to safeguard their customers. They emphasized their dedication as both a service provider and a security company, working within an ecosystem of organizations prioritizing customer protection above all other objectives.
What are recommendations to protect against the Microsoft Power Platform vulnerability?
Such situations can occur from time to time, but we must recognize that security is of utmost importance and cannot be solely entrusted to providers/vendors. Security is not just a product but a continuous process. Therefore, we must adopt a defense-in-depth approach and take appropriate measures.
SOCRadar’s platform excels in safeguarding all your organization’s digital assets, including cloud-based resources. With real-time monitoring, we swiftly alert you to any unusual activities or security threats in cloud systems. Our platform ensures compliance with regulations and industry standards, offering clear visibility into your security posture and identifying vulnerabilities.
Additionally, our dedicated Cloud Security Module keeps you informed about newly discovered cloud buckets and changes, enabling you to proactively implement protection. Elevate your cloud security with SOCRadar’s robust solutions and gain peace of mind in an ever-evolving digital landscape.
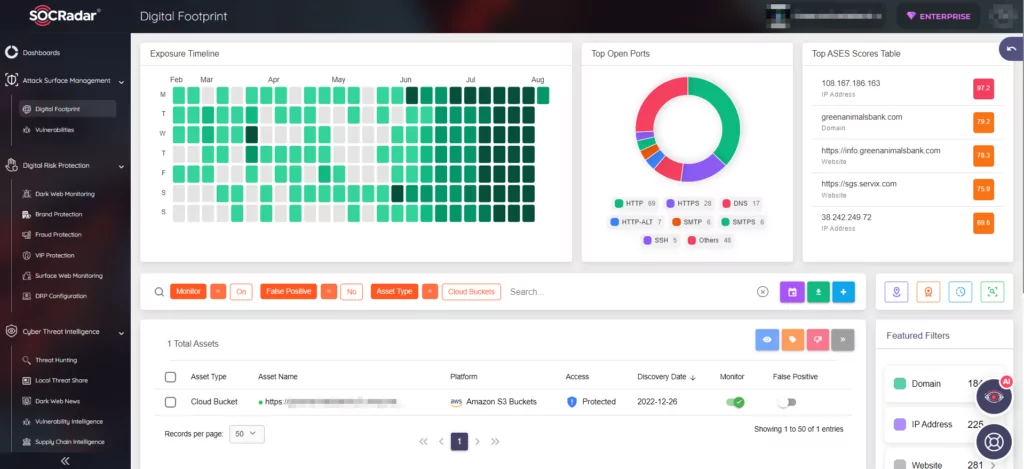
By staying informed about the critical Microsoft Power Platform vulnerability and adopting proactive security practices, you can fortify your system’s defenses and safeguard your valuable data and resources.
- Ensure that your Microsoft Power Platform and associated components are up to date with the latest patches and security fixes. Regularly check for updates and install them promptly. Also set up robust monitoring systems to detect any suspicious activities or unauthorized access attempts.
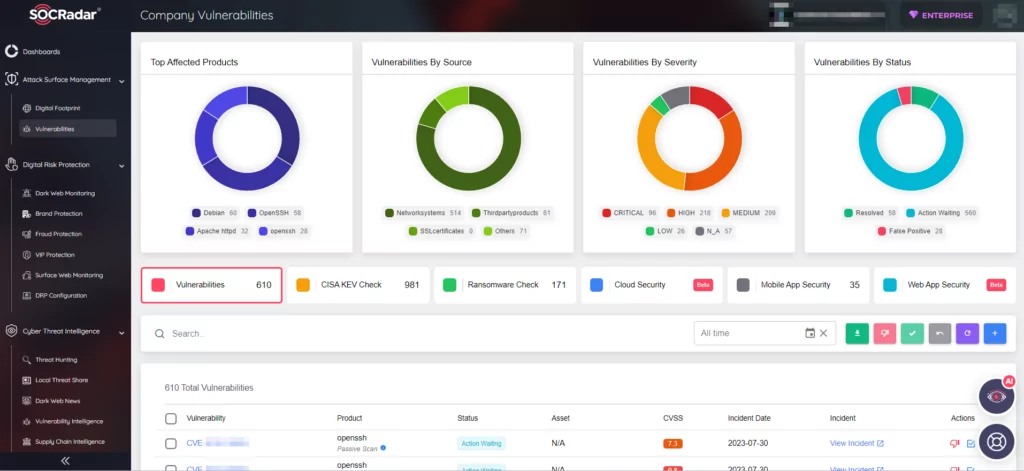
SOCRadar’s Attack Surface Management (ASM) module offers continuous monitoring of your digital assets, providing timely alerts in case of any emerging vulnerabilities or security threats. With ASM, you gain better insights into which vulnerabilities require immediate attention, and can implement a more effective patch management strategy.
- To enhance the security of your Azure Function hosts, implement stringent access control measures that allow only authorized personnel to interact with them. Designing your systems in accordance with the least privilege principle is essential in ensuring safety. Additionally, segregating duties, and use of Multi-Factor Authentication (MFA) can provide an added layer of protection. These proactive measures play a vital role in safeguarding your infrastructure from potential threats and unauthorized access attempts.
Also check the guide provided by Microsoft: How to implement authentication in custom connecters
The SOCRadar Cloud Security Module proves to be a highly valuable solution in this context. It can effectively detect and provide alerts for cloud assets that are publicly accessible and potentially vulnerable to security threats. This enables you to address potential risks promptly with appropriate access controls.
To gain a deeper understanding of the importance of cloud security measures, we invite you to read our blog on the BlueBleed incident.



































