
Dark Web Monitoring with Open-Source Tools and Services
The Dark Web, intentionally hidden on the internet, is accessible only through specialized browsers or technologies. Defenders monitor it for clues on potential cyber threats, leveraging various tools, from CTI platforms to community-driven open-source services.
But why is the Dark Web so significant for cybersecurity? Some critical threat information analysts can find includes:
- Data leaks or sale posts with names, email addresses, passwords, financial and corporate information, and more.
- Exploits for security vulnerabilities, including zero-days.
- Administrator access sales to specific technologies and systems, especially VPN and firewalls.
- Sale of hacking campaign tools like phishing kits, stealers, and ransomware services (check specifics about RaaS).
- Cyber attack campaigns announced by attackers or still in planning phases.
Monitoring the Dark Web is increasingly critical, as recent insights from SOCRadar’s Dark Web Report 2024 highlight ongoing cyber threats that organizations face globally. The report identifies the U.S., India, and the U.K. as the most frequently targeted nations, underscoring the broad geographic impact of Dark Web activities. Industries such as manufacturing and professional services are consistently targeted by ransomware attacks, further emphasizing the necessity for vigilant monitoring. Additionally, alarming numbers demonstrate the urgent need for effective monitoring solutions: over 1.6 million email-password credentials and 75,000 credit card details were exposed worldwide.
To address these risks, organizations may often leverage open-source tools. Using open-source tools in pursuit of Dark Web Monitoring has several advantages, including accessibility, customization, cost-effectiveness, and flexibility. These tools enable organizations to gain insights with peace of mind, as they can inspect the code of these tools and services and integrate them accordingly with their infrastructure and security needs.
In this blog post, we will explore five of the top open-source tools for Dark Web monitoring to help you scan, inspect, and identify threats effectively.
1. OWASP TorBot
OWASP TorBot is a Python-based, open-source Dark Web monitoring tool designed specifically for crawling hidden websites with “.onion” addresses. The project’s source code is fully accessible on GitHub.
TorBot – Open Source OSINT Tool for Dark Web Monitoring
Its primary functionalities include actively retrieving page titles and addresses with brief descriptions, storing crawl data in JSON format, scanning custom domains, and verifying the live status of links.
As TorBot performs active scanning – directly querying hidden services over the Tor network – users should remain aware that such interactions, although anonymized, may still be logged or observed by dark web operators, introducing potential operational risks.
TorBot streamlines darknet surveillance and OSINT operations, providing users with a clear, user-friendly interface. Its comprehensive yet straightforward approach helps cybersecurity teams efficiently gather critical information and mitigate potential threats on Dark Web pages.
2. MISP (Malware Information Sharing Platform)
Malware Information Sharing Platform (MISP) is a widely recognized open-source tool focusing on Dark Web threat intelligence and cybersecurity threat monitoring.

MISP – Malware Information Sharing Platform
MISP is highly versatile, allowing deployment in data centers or across various cloud platforms. Its use of open-source protocols and data formats ensures easy integration with existing security infrastructure.
While MISP’s intelligence streams might lack the curated insights of commercial alternatives, it serves as a highly cost-effective solution for organizations to establish internal Dark Web risk management. Its interoperability significantly enhances threat intelligence capabilities, supporting integrations with other cybersecurity solutions.
Organizations can customize MISP to share and receive specific threat intelligence data, including insights into Dark Web activities, by selecting preferred risk levels, data frequency, and event tags.
3. OnionScan
OnionScan is another powerful open-source Dark Web tool that facilitates secure and detailed exploration of hidden web services.

Explore more about OnionScan on GitHub
Despite ongoing improvements in anonymity and privacy technologies, human errors continue to pose significant cybersecurity risks. OnionScan targets these vulnerabilities, helping security experts identify misconfigurations and potential risks in Dark Web services, promoting the secure utilization of the Dark Web.
Its primary objectives include assisting hidden service operators to secure their platforms and aiding security researchers in monitoring Dark Web sites effectively.
OnionScan thoroughly scans .onion sites for vulnerabilities and data leaks, including sensitive metadata within images, inadvertently exposed server pages revealing IP addresses, and shared encryption keys indicating site connections. Its detailed reports range from simple risk summaries to detailed verbose and JSON formats, ideal for integration with other tools.
4. Ahmia.fi
Ahmia.fi, born out of the Tor Project by Juha Nurmi, addresses the unique challenge of navigating the TOR Network’s architecture.
Ahmia.fi search page
Unlike traditional search engines, Ahmia specializes in indexing .onion URLs from the Tor network, providing one of the most extensive deep web indexes available.
By aggregating these URLs, Ahmia grants users simplified access to typically hidden Dark Web content. Its open-source nature enables cybersecurity teams and researchers to access its source code on GitHub, allowing customized index-building and personalized darknet surveillance.
For additional context and insights into various Dark Web tools and services, explore our article on the “Top 10 Dark Web Search Engines in 2025,” where we further highlighted Ahmia’s capabilities.
5. Deep Search
Deep Search stands out as a specialized open-source tool crafted explicitly for precise exploration of hidden onion domains within the Tor network. Designed to tackle common issues such as irrelevant results, it emphasizes accurate, high-quality results to improve the effectiveness of Dark Web monitoring.

Deep Search Search Engine
Deep Search’s transparent, community-driven model ensures trustworthiness and reliability in darknet surveillance and threat intelligence activities.
Ready to Take Dark Web Monitoring to the Next Level? Meet SOCRadar’s Advanced Toolkit
While open-source Dark Web monitoring tools provide important capabilities for scanning and threat discovery, organizations aiming for deeper protection often seek more advanced, continuous coverage. For security teams aiming to stay ahead of rapidly evolving darknet threats, combining open-source flexibility with enterprise-grade threat intelligence becomes critical.
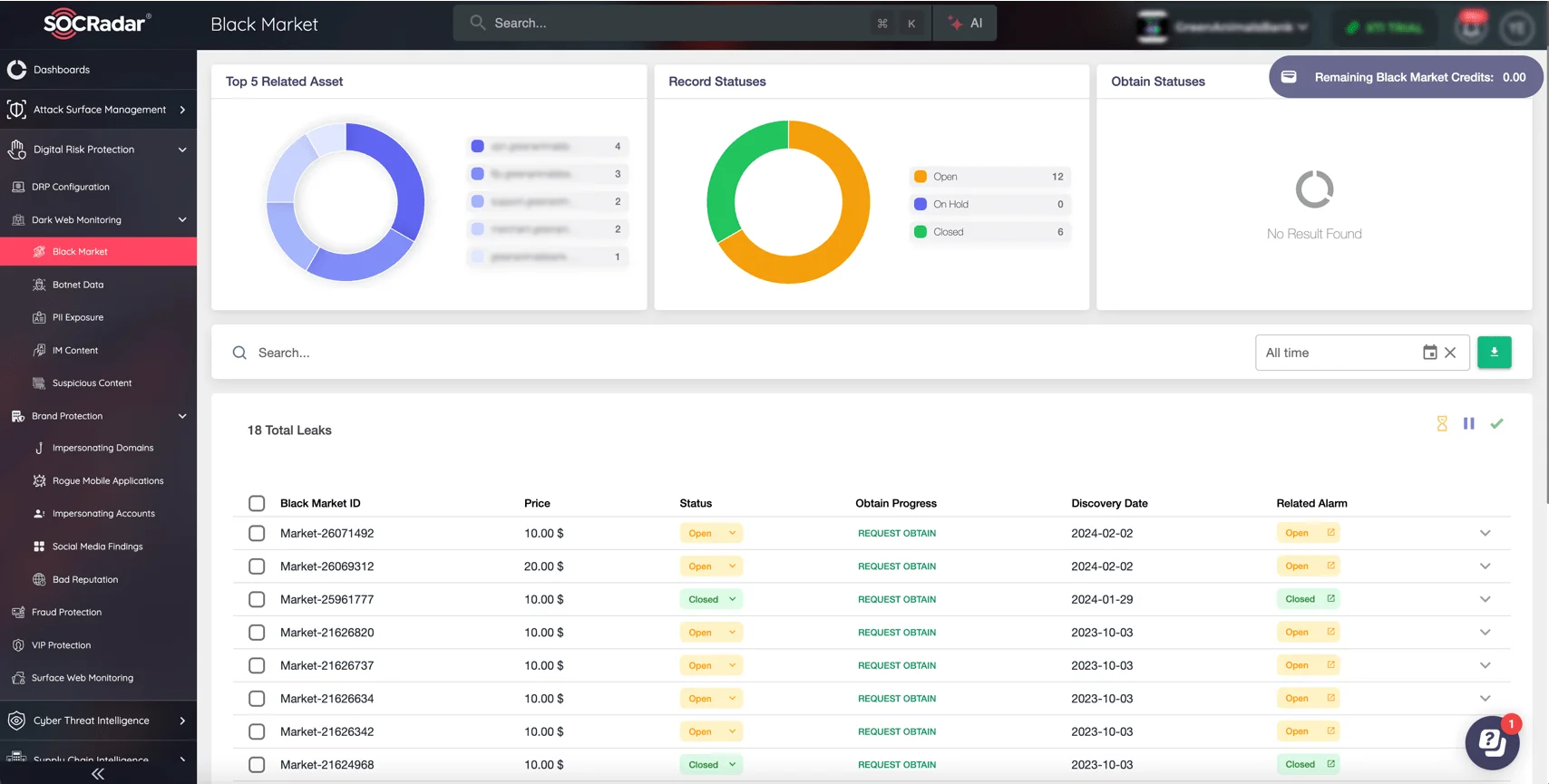
SOCRadar’s Dark Web Monitoring: Monitor Black Markets, PII Exposure, Botnet Data, IM Content & more
This is where advanced platforms like SOCRadar’s Dark Web Monitoring step in. Purpose-built for real-time monitoring and actionable threat detection, SOCRadar enables your organization to:
- Continuously monitor the Dark Web for mentions of employee, customer, or corporate information.
- Detect exposures like stolen credentials, unauthorized data transfers, and underground chatter tied to their brand.
- Access Dark Web News, delivering the latest insights from deep and Dark Web forums, marketplaces, and Telegram channels.
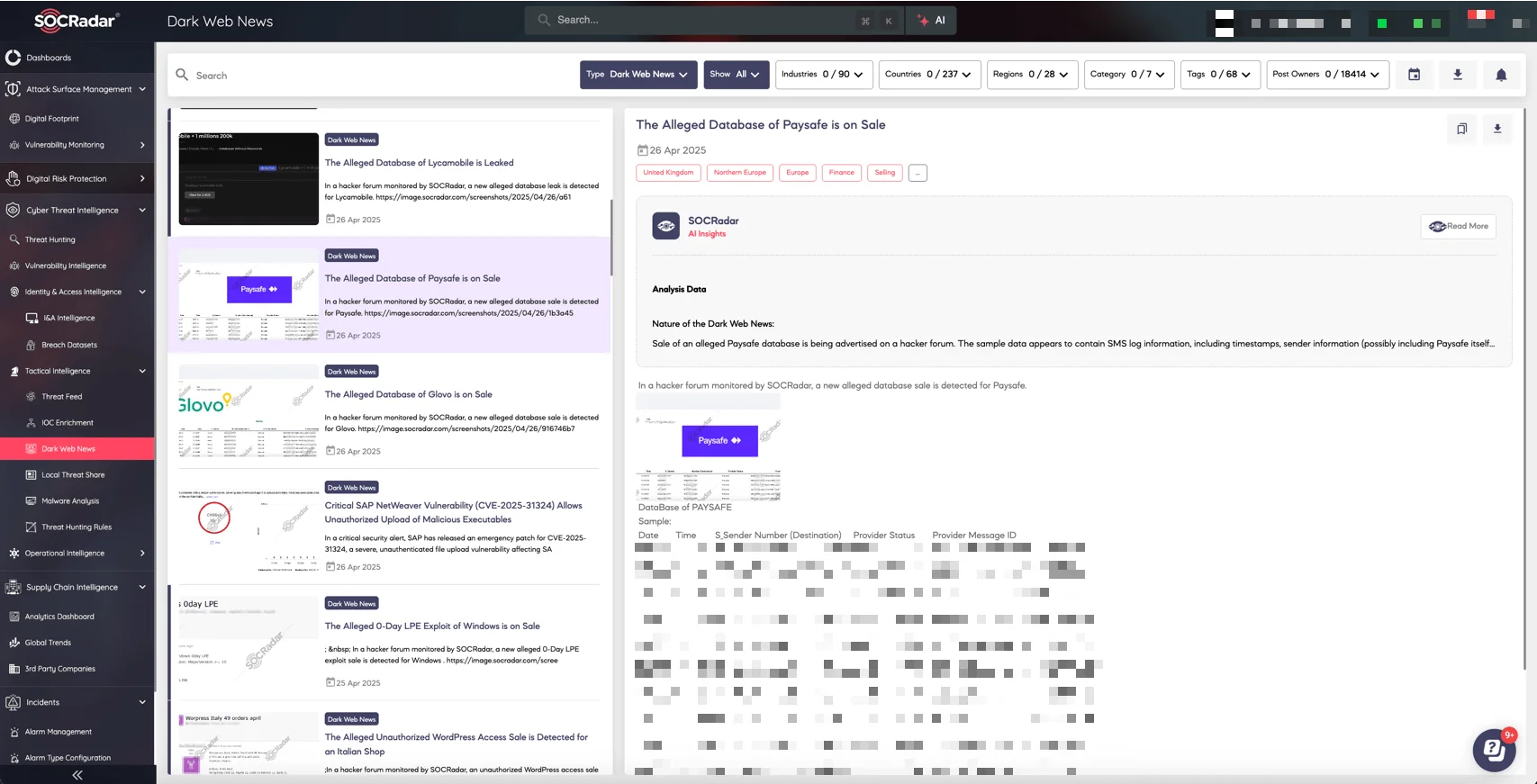
SOCRadar’s Dark Web News
- Investigate exposures through Threat Hunting, filtering stealer logs and other high-volume datasets for actionable findings.
- Integrate Dark Web threat intelligence seamlessly into existing security infrastructure to enhance response capabilities.
Beyond detection, SOCRadar transforms raw Dark Web data into curated, contextualized reports tailored to industry-specific risks and geographies. Whether protecting financial services, government agencies, healthcare, or technology enterprises, SOCRadar equips defenders with the intelligence they need to anticipate and counter emerging Dark Web threats.
With its broad coverage, continuous monitoring, and threat contextualization, SOCRadar aims to strengthen your cybersecurity posture and make faster, more informed decisions against Dark Web risks.
Conclusion
Using a combination of open-source tools like OWASP TorBot, MISP, OnionScan, Ahmia, and Deep Search, defenders can better navigate the Dark Web and extract valuable threat intelligence.
The Dark Web continues to serve as a vital source of cybersecurity insights, exposing leaked data, vulnerabilities, administrator access sales, hacking tools, and early signs of cyber attacks. Monitoring this space is crucial for strengthening any organization’s security posture.
Alongside these open-source resources, advanced platforms like SOCRadar’s Dark Web Monitoring service enable organizations to take a more proactive stance. With real-time threat detection, curated intelligence, and continuous monitoring across deep and Dark Web channels, SOCRadar helps security teams transform raw data into actionable defense strategies.
By combining the accessibility of open-source tools with the advanced capabilities of enterprise-grade solutions, businesses can significantly strengthen their cybersecurity measures and stay ahead of evolving Dark Web threats.




































