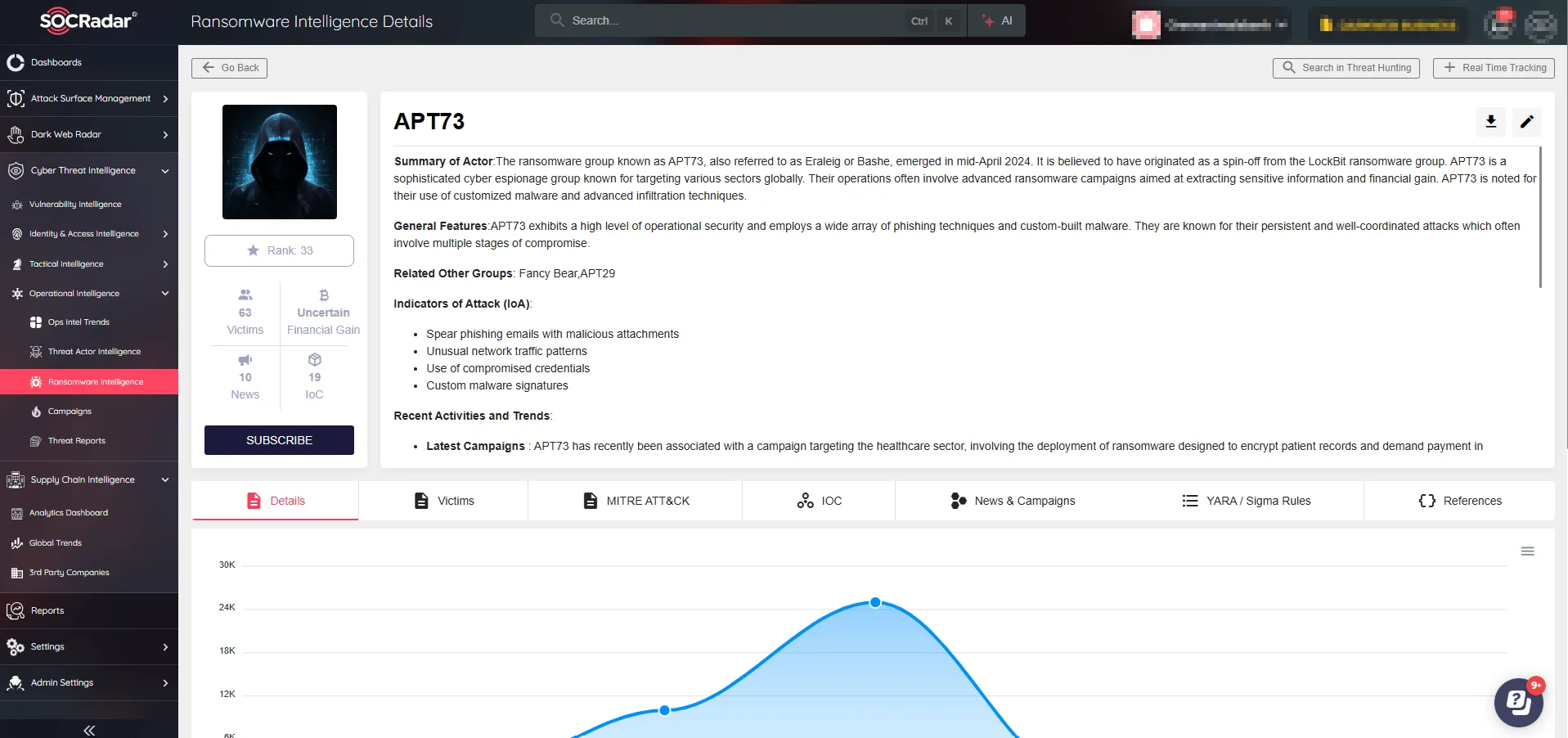
Dark Web Profile: Bashe (APT73)
Bashe, previously known as APT73 or Eraleig, is a ransomware group that emerged in 2024, employing tactics reminiscent of LockBit to target critical industries across developed nations. Operating through a TOR based Data Leak Site (DLS), Bashe engages in data extortion to pressure victims into compliance.

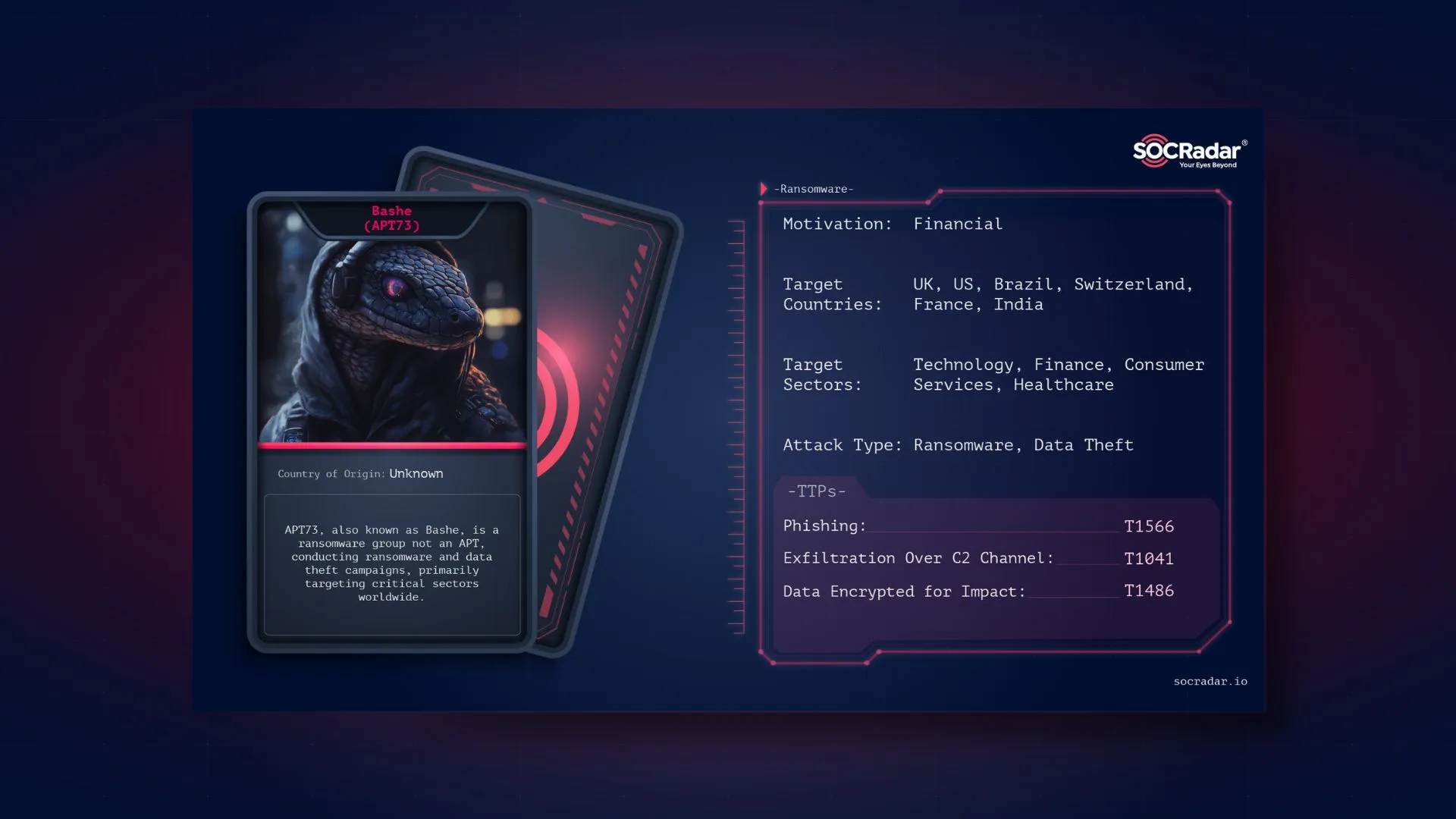
Threat actor card for Bashe (APT73)
Who is Bashe?
Bashe surfaced in mid-April 2024, initially self-identifying as an “Advanced Persistent Threat” (APT), a term typically reserved for highly sophisticated cyber actors. This self-designation appears to be a strategic move to market itself as a credible threat. The group was previously known as APT73 or Eraleig but they got rebranded after a break of months with new domains.
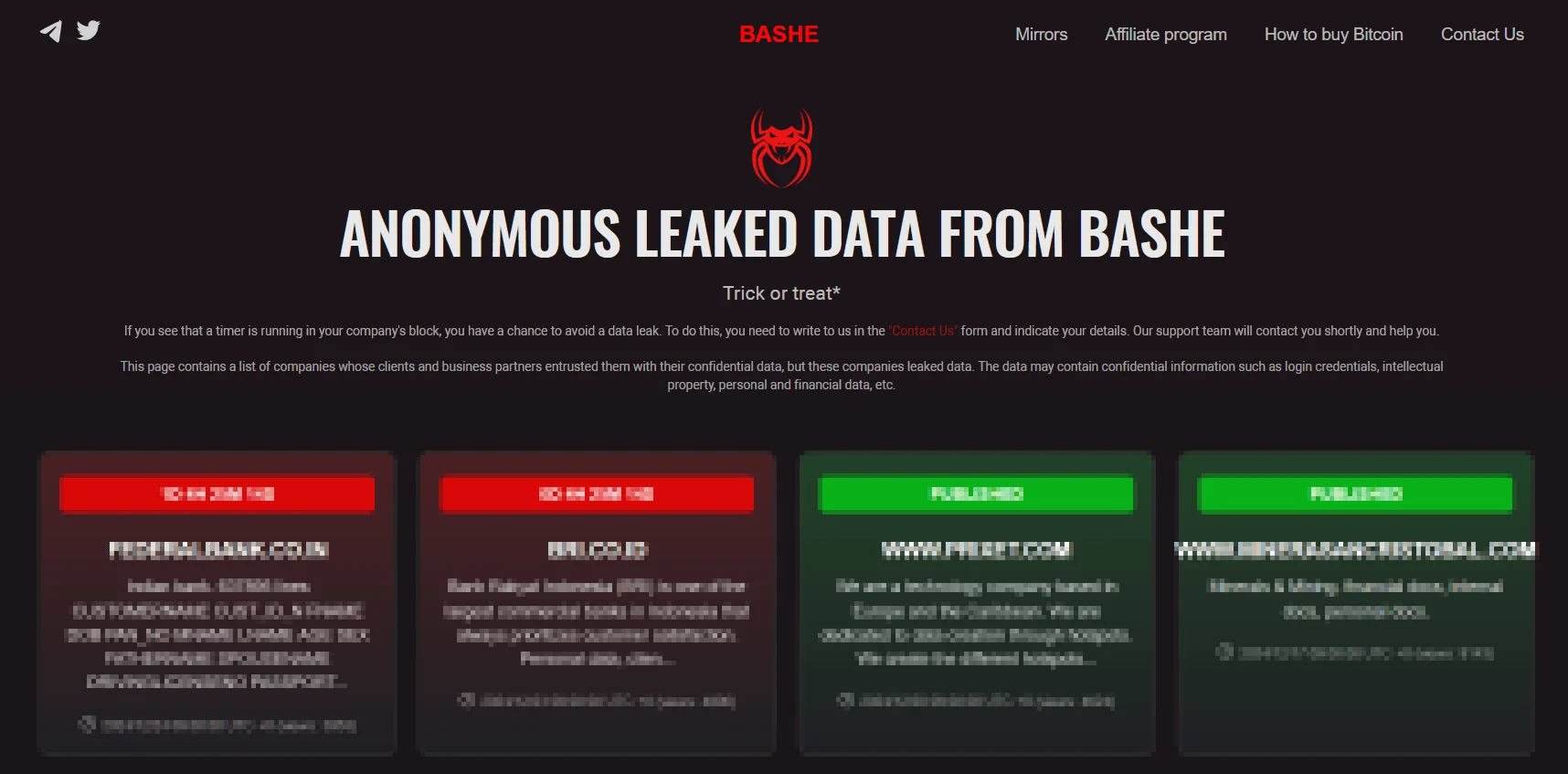
Bashe’s DLS
At first look, their DLS suggests that Bashe is a spin-off from the LockBit ransomware group, as indicated by the similarities between their DLS structures, including sections like “Contact Us,”“How to Buy Bitcoin,”“Web Security Bug Bounty,” and “Mirrors,” which are identical to those seen in LockBit’s setup.
What are Their Targets?
APT73 has demonstrated a strategic approach to its ransomware campaigns, focusing mostly on developed nations and industries where data sensitivity and operational disruption are most impactful. By leveraging double extortion tactics, the group not only encrypts victims’ files but also threatens to expose stolen data on its DLS to maximize financial gain and coerce compliance.
The group’s operations span several countries, with victims identified in the United States, United Kingdom, France, Germany, India, and Australia. In the United States, APT73 has primarily targeted the technology, healthcare, and financial services sectors, exploiting their reliance on sensitive data and operational continuity.
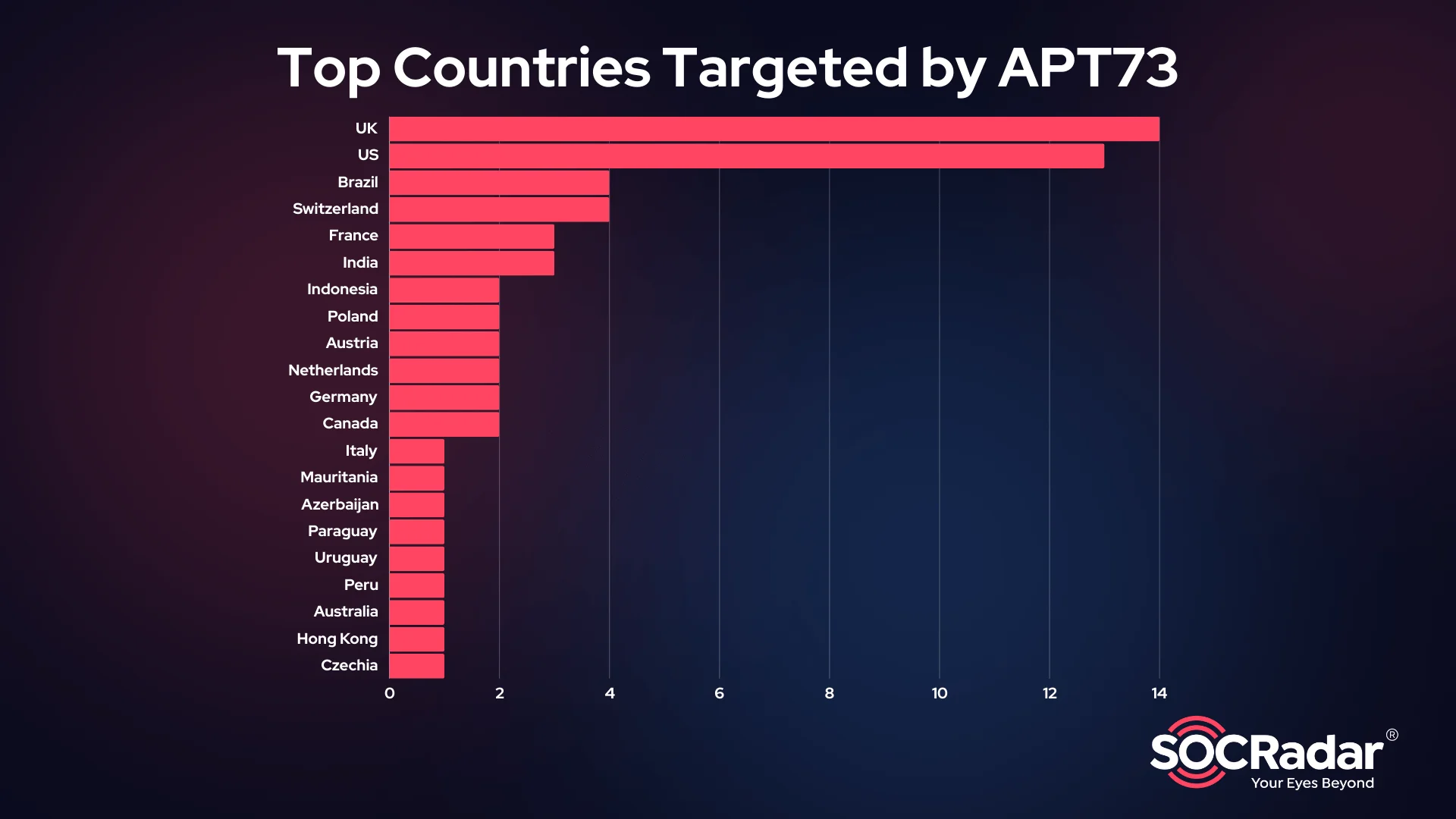
Top countries targeted by APT73
In the United Kingdom, business services and consumer industries have been the primary focus, while in France and Germany, the group has directed its efforts toward manufacturing, logistics, and industrial sectors. India has seen attacks on IT services and business process outsourcing firms, while Australia has reported incidents within its transportation and construction industries.
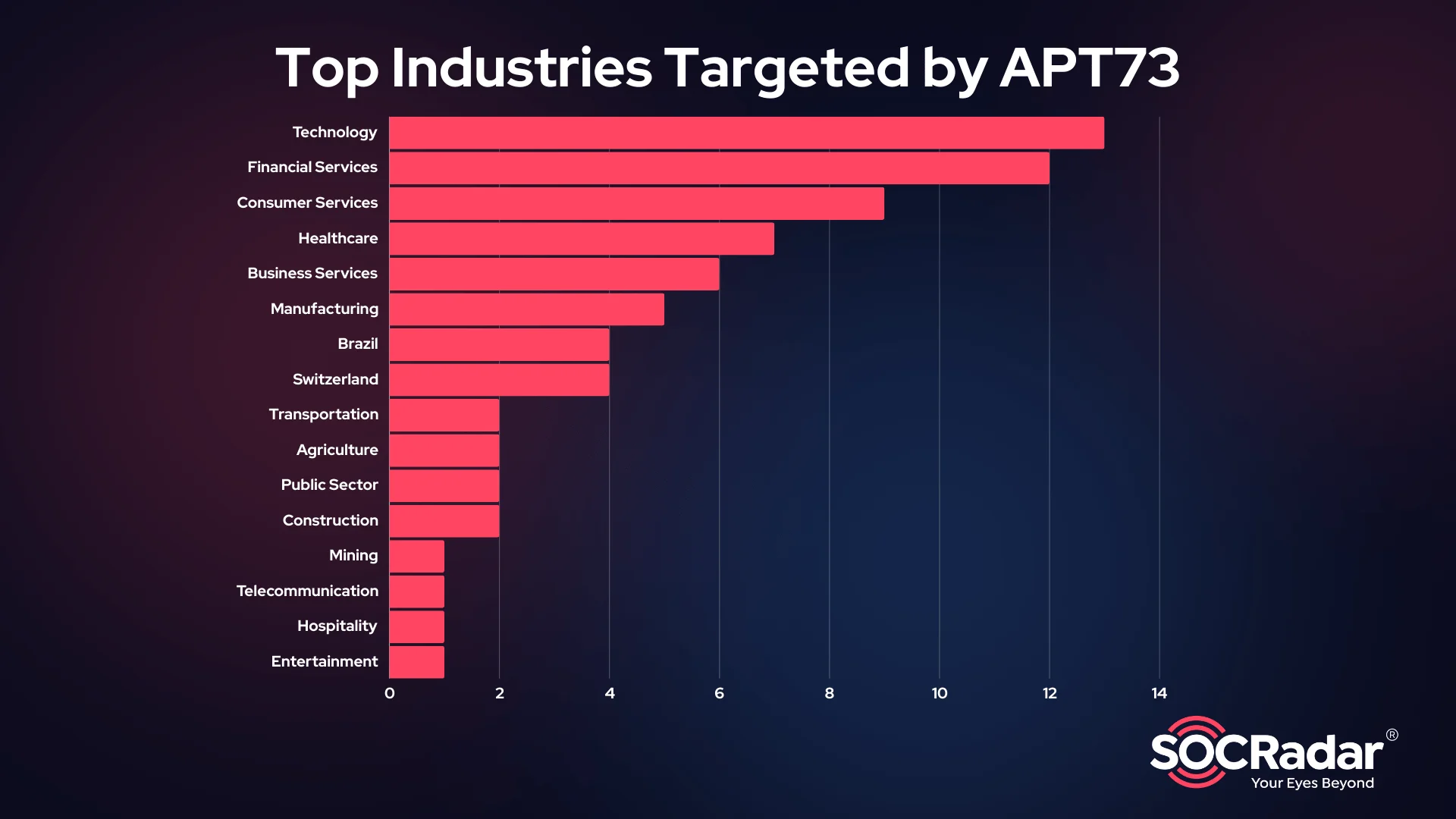
Top industries targeted by APT73
APT73’s industry-specific focus underscores its methodical approach to victim selection. Technology companies are targeted for their valuable intellectual property, healthcare organizations for critical patient data, and financial institutions for sensitive records and transactional data. The group also disrupts supply chains in manufacturing and logistics, exploits operational systems in transportation, and capitalizes on large-scale investments in construction projects.
As of December 23, 2024, APT73, also known as Bashe, has claimed 63 victims across various countries.
How does APT73 Operates?
Bashe uses a variety of key attack methods that make its operations both effective and difficult to trace. The group primarily launches attacks through phishing, exploiting vulnerabilities in public-facing applications. Their phishing tactics often involve spear-phishing, where malicious documents or URLs are disguised as legitimate business communications and aimed at employees of high-value organizations.
Once they gain access, Bashe typically engages in data exfiltration and double extortion. After encrypting the victim’s systems, the group exfiltrates sensitive data, using it as leverage in their extortion efforts. They threaten to release this stolen data on their dark web site unless ransom demands are met, combining encryption with the threat of data exposure to put added pressure on the victim.
Bashe’s data leak site (DLS) is hosted on the dark web and accessible only through Tor. However, compared to more established ransomware groups like LockBit, the site is still in its early stages. It has no active mirrors, and only a single victim’s data has been leaked so far, indicating that Bashe is in the early phase of its ransomware operations.
In terms of technical characteristics, Bashe’s DLS is basic, reflecting the group’s developmental stage. It is far less sophisticated than the platforms of more established groups, with minimal data leaks and no active mirrors. The group relies heavily on the Tor network for hosting and data leaks, ensuring anonymity and complicating any efforts to trace their activities.
When compared to LockBit, Bashe’s tactics and methods show notable similarities. Their DLS structure and attack techniques, including encryption and data exfiltration, closely resemble those of LockBit. The two groups use similar layouts for their data leak sites, which may suggest Bashe is either trying to emulate LockBit or sharing resources with the group to establish credibility among lower-level cybercriminals.
How to Defend Against APT73 and Similar Ransomware Attacks?
To defend effectively against ransomware attacks like those executed by APT73, organizations must implement a multi-layered security strategy. Below are key measures to minimize the risk of such attacks:
Preventing Initial Access
- Patch Management: Regularly update and patch systems, particularly public-facing applications, to address vulnerabilities attackers might exploit.
- Network Segmentation: Isolate sensitive systems and critical data to limit lateral movement within the network.
- Access Controls: Use firewalls, Intrusion Prevention Systems (IPS), and secure VPNs to monitor and control access to remote services.
Strengthening Identity Security
- Multi-Factor Authentication (MFA): Implement MFA across critical systems to protect against unauthorized access and brute-force attacks.
- Strong Password Policies: Enforce complex, unique passwords that are rotated regularly and managed securely with password managers.
- Employee Training: Educate users on phishing risks and secure password practices to prevent credential-based attacks.
Monitoring and Protecting Credentials
- Dark Web Monitoring: Regularly track credential dumps and leaks on the Dark Web to identify exposed data early.
- Account Lockouts: Set thresholds for failed login attempts to prevent brute-force attacks and unauthorized access.
Preventing Malware Execution
- Endpoint Detection and Response (EDR): Deploy tools that can detect unauthorized activities, including suspicious behaviors and new account creations.
- Application Whitelisting: Only allow approved applications to run within the network to reduce the chances of malware execution.
- Behavioral Analytics: Use behavioral monitoring tools to detect anomalous activities indicative of ransomware behavior.
Limiting Persistence and Lateral Movement
- Principle of Least Privilege (PoLP): Regularly review and limit user privileges to minimize attack surfaces.
- Harden Remote Services: Disable unnecessary services like Remote Desktop Protocol (RDP) and restrict Server Message Block (SMB) access.
- Network Traffic Monitoring: Monitor network traffic for signs of lateral movement or command-and-control communications.
Mitigating Ransomware Impact
- Data Backup: Ensure regular offline backups and regularly test restoration procedures to maintain business continuity during an attack.
- Isolated Backup Systems: Keep backups isolated from the main network to protect them from being encrypted during a ransomware attack.
- Incident Response Plan: Develop and maintain an incident response plan to quickly contain, communicate, and recover from ransomware attacks.
Post-Incident Recovery
- Ransomware Decryption Tools: Check for available decryption tools from trusted sources like No More Ransom to recover encrypted files.
- Forensics and Logging: Analyze attack logs to identify attack vectors and improve future defenses.
- Law Enforcement Collaboration: Report ransomware incidents to authorities for broader threat intelligence efforts.
How SOCRadar Can Help Defend Against APT73?
SOCRadar offers advanced tools to help organizations detect, mitigate, and prevent ransomware attacks like APT73. Key capabilities include:
- Threat Intelligence: Get insights into the latest TTPs (tactics, techniques, and procedures) used by APT73 and similar groups, staying ahead of potential attacks.
- Dark Web Monitoring: Detect and respond to leaked credentials, exploits, and ransomware payloads related to APT73 on the Dark Web.
- Vulnerability Intelligence: Receive real-time updates on vulnerabilities exploited by ransomware groups, enabling proactive patching.
- Ransomware Tracking: Monitor ransomware variants and associated tools to stay prepared for new strains.
- Timely Alerts: Receive real-time alerts and detailed reports on ransomware IoCs, attack vectors, and recommended actions to effectively protect your infrastructure.
SOCRadar Ransomware Intelligence
By combining proactive measures with SOCRadar’s advanced cybersecurity tools, organizations can significantly reduce the risk of APT73 and other ransomware infections, enhancing their overall security posture.
What Are Their MITRE ATT&CK Techniques?
| Tactic | ID | Technique Name |
| Initial Access | T1566 | Phishing |
| T1190 | Exploit Public-Facing Application | |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| T1203 | Exploitation for Client Execution | |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| T1547.001 | Boot or Logon AutoStart Execution: Registry Run Keys | |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control (UAC) | |
| Defense Evasion | T1055 | Process Injection |
| T1562.001 | Impair Defenses: Disable or Modify Tools | |
| Discovery | T1018 | Remote System Discovery |
| T1083 | File and Directory Discovery | |
| T1057 | Process Discovery | |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Collection | T1005 | Data from Local System |
| T1074.001 | Data Staged: Local Data Staging | |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage | |
| Impact | T1486 | Data Encrypted for Impact |
In Summary
In conclusion, Bashe (formerly APT73 or Eraleig) is a ransomware group that has rapidly emerged in 2024, targeting critical industries across developed nations with tactics similar to those of established groups like LockBit. Operating via a TOR-based data leak site, Bashe employs double extortion techniques, combining data encryption with threats of public exposure to force victims into compliance. Despite being a relatively new player, the group has already made significant inroads, claiming numerous victims worldwide.
As the group continues to evolve, organizations must adopt comprehensive security measures to defend against Bashe and other ransomware threats, utilizing tools like SOCRadar’s threat intelligence, dark web monitoring, and vulnerability insights to stay ahead of emerging attacks.




































