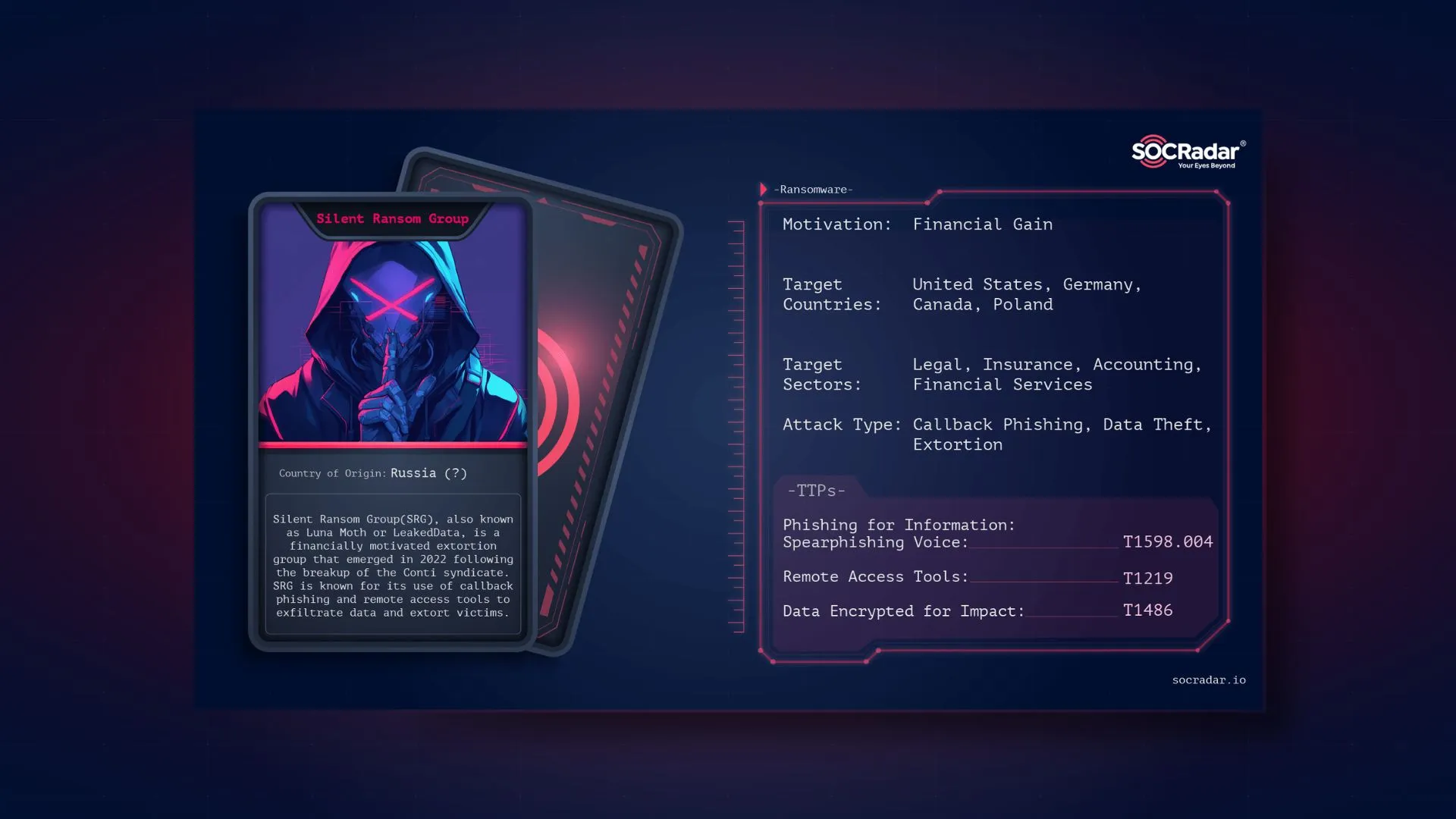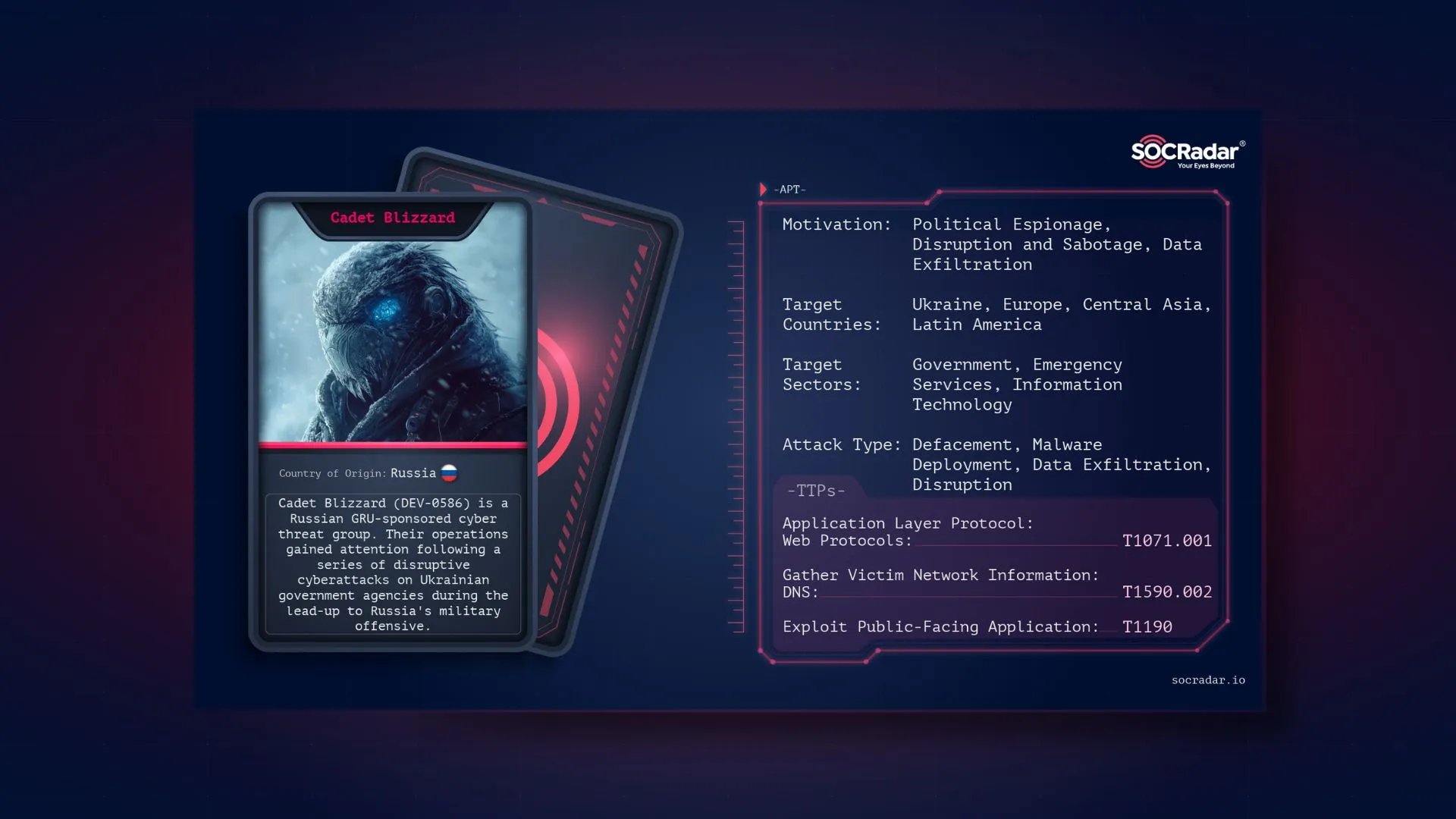
Dark Web Profile: Cadet Blizzard
Cadet Blizzard (DEV-0586) is a Russian GRU-affiliated cyber threat group first tracked by Microsoft in early 2022, following a series of disruptive cyberattacks on Ukrainian government agencies amidst rising military tensions. These attacks, including website defacements and the deployment of the WhisperGate malware, foreshadowed further activity from the group, aligning with Russia’s military invasion of Ukraine.
While primarily targeting government and IT sectors in Ukraine, Cadet Blizzard has expanded its operations to include organizations in Europe and Latin America. The group has maintained a persistent presence since at least 2020, exfiltrating data before executing disruptive actions, with activity peaking between January and June 2022. After a period of reduced activity, Cadet Blizzard resumed operations in January 2023, launching further attacks against Ukrainian and European entities, including the re-emergence of their “Free Civilian” Telegram channel. This group remains active, with a focus on targeting NATO member states involved in aiding Ukraine, operating primarily during European off-business hours.
Who Is Cadet Blizzard?
Cadet Blizzard, part of Unit 29155, is a highly secretive and sophisticated cyber warfare group with strong ties to the Russian military intelligence agency GRU. Formed as part of the GRU’s broader efforts to disrupt global systems, the group is primarily known for its cyber-espionage and sabotage campaigns, often targeting critical infrastructure across the world. Although its existence was initially veiled in secrecy, investigations have unveiled the group’s involvement in various state-sponsored cyberattacks and physical sabotage operations.

Threat Actor card for Cadet Blizzard
The name “Cadet Blizzard” is one of several associated cyber warfare groups of Unit 29155. Unit 29155 is believed to have been established around 2010, though it gained international attention in recent years due to its direct involvement in high-profile cyberattacks, including the 2016 U.S. presidential election interference and the cyberattacks during Russia’s 2022 invasion of Ukraine. The group’s activities span a wide range of malicious operations—from data exfiltration and credential theft to sophisticated manipulation of industrial and governmental systems.
For a more comprehensive understanding of Unit 29155, check CISA’s advisory.
What Are Their Targets?
According to Microsoft, Cadet Blizzard primarily targets government organizations and entities involved in critical infrastructure, with a special focus on military and defense sectors. The group’s operations are often politically motivated, aligning with Russia’s strategic goals. In addition to government agencies, Cadet Blizzard also targets sectors that support military operations, such as technology providers, supply chain partners, and other institutions critical to national security.
The group has been particularly active in Ukraine, where it has targeted Ukrainian government websites and critical services, using techniques such as website defacements and deploying custom malware like WhisperGate. This activity intensified alongside Russia’s military actions, indicating that the cyber operations are coordinated with broader geopolitical objectives.
Their targets are not limited to Ukraine alone; they have also extended their operations to Europe, particularly NATO member states involved in supporting Ukraine’s defense. The goal appears to be to disrupt, steal sensitive data, and create destabilizing effects on these nations’ infrastructure and security frameworks. The group’s activities are ongoing, with observed bursts of operations timed to cause maximum disruption, often during off-business hours of the targeted entities.
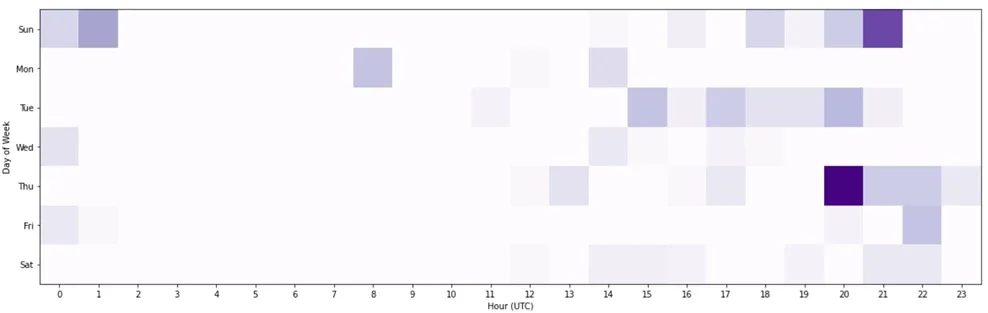
Cadet Blizzard’s operating hours according to Microsoft
How Do They Operate?
Cadet Blizzard follows a complex and calculated cyber kill chain to conduct their operations. This multi-step process enables them to infiltrate, manipulate, and disrupt targeted systems effectively.
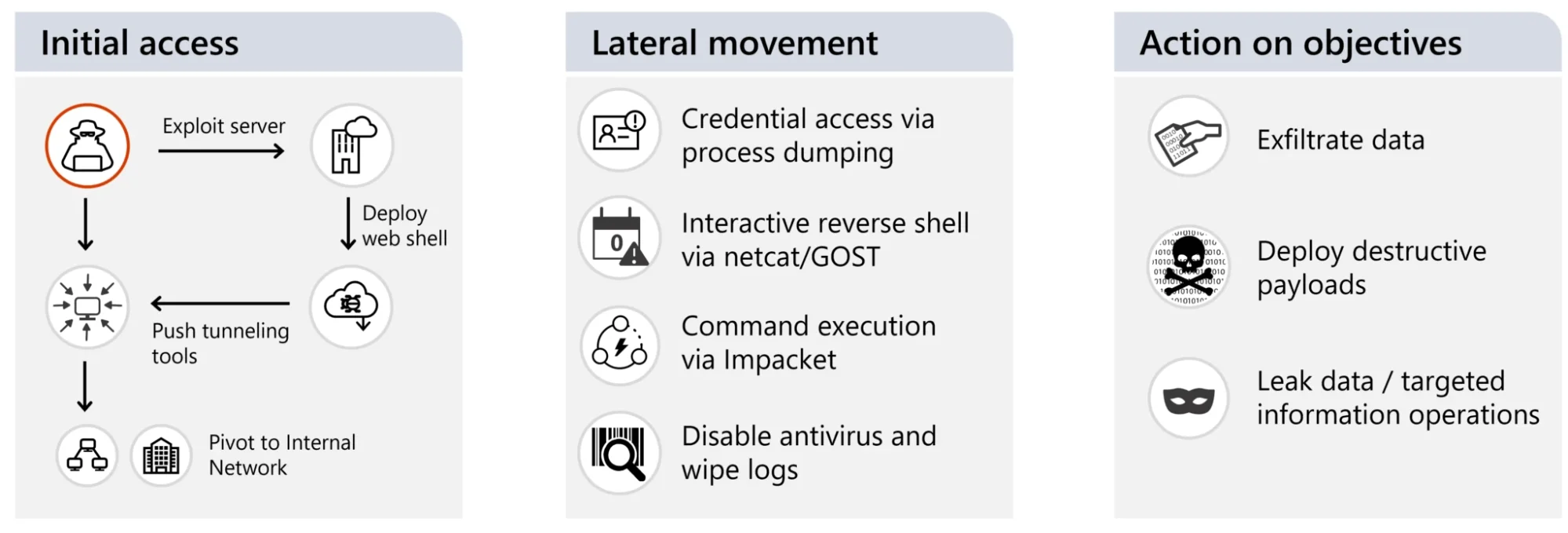
Cadet Blizzard’s normal operational lifecycle (Microsoft)
Initial Access
Cadet Blizzard frequently gains initial access by exploiting vulnerabilities in web servers situated on the network perimeter or in DMZs. Known vulnerabilities include CVE-2021-26084 (Confluence servers) and CVE-2022-41040 and ProxyShell (Exchange servers). The group is also known to exploit weaknesses in open-source platforms, such as content management systems, to gain entry.
Persistence
After gaining access, Cadet Blizzard ensures long-term access to the network by deploying commodity web shells like P0wnyshell, reGeorg, PAS, and custom versions from publicly available exploit kits. These shells act as backdoors, allowing for tunneling or commanding, ensuring that the group can maintain persistent control over the compromised systems.
Privilege Escalation and Credential Harvesting
To escalate their access and control over the network, Cadet Blizzard utilizes living-off-the-land techniques, such as dumping credentials from the LSASS process with tools like procdump (which is often renamed, for example, as dump64.exe). Additionally, they extract registry hives to obtain critical credential information, further enabling their ability to move across the network undetected.
Lateral Movement
Once in possession of valid network credentials, Cadet Blizzard moves laterally through the network using tools like Impacket and PowerShell commands. For example, they use PowerShell’s get-volume command to enumerate device volumes and the DownloadFile command to retrieve malicious files from their infrastructure. Cadet Blizzard may also create scheduled tasks or reverse shells to facilitate command execution across the network.
Command and Control (C2)
To maintain control over compromised systems, Cadet Blizzard utilizes tunneling tools like NetCat and GOST (which are sometimes renamed to blend in with the system’s native tools). These utilities enable reverse shell connections, allowing the group to remotely execute commands. While their use of Meterpreter is limited, it has been deployed in some operations.
Operational Security
To obscure their activities and evade detection, Cadet Blizzard leverages tools like IVPN, SurfShark, and Tor, which anonymize their communications and make it more difficult to trace their actions back to them.
Anti-Forensics
To cover their tracks and hinder forensic investigations, Cadet Blizzard extracts system logs using the Win32_NTEventlogFile command in PowerShell, then deletes them to erase traces of their activity. They also disable Microsoft Defender Antivirus by using tools like the NirSoft AdvancedRun utility and registry modifications to stop the WinDefend service.
Impact
Cadet Blizzard’s operations are designed not only for intelligence gathering but also for disruption. The group exfiltrates large volumes of data, including sensitive credentials and communication logs, and often leaks this data on platforms like Tor or Telegram. Their destructive actions, such as using WhisperGate malware to erase data and disrupt systems, demonstrate their broader objectives of creating chaos and signaling geopolitical messages. Through these tactics, Cadet Blizzard blends espionage and high-impact disruptions, ensuring that their operations leave a significant mark on targeted entities.
This approach reflects the group’s strategy of using existing tools and services to maintain access and execute high-profile, disruptive operations while minimizing their digital footprint.
How Can You Defend Against Cadet Blizzard and Similar APT Attacks?
Defending against Cadet Blizzard and similar APT groups requires a multi-layered, proactive defense strategy. Given the group’s sophisticated tactics and focus on both data exfiltration and disruption, organizations must ensure robust security measures across several key areas:
- Email and Web Filtering
Since Cadet Blizzard often gains initial access via spear-phishing emails and malicious attachments, robust email filtering is essential. Implementing security measures like anti-phishing tools and URL filtering can significantly reduce the risk of this entry point. Additionally, training employees to recognize and report suspicious emails can help mitigate these risks. - Endpoint Detection and Response (EDR)
Maintaining strong endpoint defenses is critical for detecting malware and unauthorized access early. Cadet Blizzard uses malware like WhisperGate to establish persistence and escalate privileges. EDR solutions capable of detecting these types of threats can identify unusual behavior, such as the deployment of unfamiliar software or abnormal network traffic, allowing defenders to respond quickly. - Network Segmentation and Zero Trust Architecture
To limit lateral movement across the network, organizations should implement network segmentation and adopt a Zero Trust architecture. These approaches reduce the attack surface by ensuring that no system or user is trusted by default, even if they have already gained access. Monitoring tools should track internal communications for anomalous activity to detect early signs of lateral movement. - Credential Management and Multi-Factor Authentication (MFA)
As Cadet Blizzard frequently escalates privileges by exploiting stolen credentials, effective credential management is crucial. Organizations should implement MFA across all critical systems and enforce strong password policies. Monitoring for suspicious login attempts and using advanced authentication methods like biometrics or hardware tokens can further minimize credential-related attacks. - Threat Intelligence and Continuous Monitoring
Given the group’s persistence and focus on gathering intelligence, integrating threat intelligence into your security posture can help detect signs of early-stage attacks. Regular monitoring of threat actors’ tactics and techniques, especially those employed by groups like Cadet Blizzard, allows organizations to stay ahead of evolving threats. Real-time alerts on emerging threats or changes in attack patterns are vital for proactive defense. - Incident Response and Data Recovery
Having a well-prepared incident response (IR) plan can make a difference when facing a destructive attack. Cadet Blizzard often uses wiper malware to disrupt systems. A clear IR plan, backed by regular backups and data recovery procedures, ensures that organizations can recover quickly from system destruction and continue operations without significant downtime.
How SOCRadar Can Help in Defending Against APT Groups
SOCRadar offers several key features to help organizations defend against APT groups like Cadet Blizzard by providing real-time visibility, monitoring, and proactive threat intelligence:
- Cyber Threat Intelligence
SOCRadar’s Cyber Threat Intelligence platform continuously monitors global dark web and surface web activities to detect early signs of APT attacks. By identifying Cadet Blizzard’s Tactics, Techniques, and Procedures (TTPs), SOCRadar can provide valuable intelligence on emerging threats. Alerts can help security teams prepare for potential attacks, understand adversary objectives, and better align their defenses. - Dark Web and Deep Web Monitoring
As part of its monitoring capabilities, SOCRadar tracks malicious activities and data leaks across the dark web. Since Cadet Blizzard often exfiltrates sensitive data and leaks it online (such as on Telegram), SOCRadar’s dark web search engine and alerting features can notify organizations of any potential breaches or leaked data related to their organization. This allows security teams to take immediate action and mitigate any further harm. - Vulnerability Management
To prevent privilege escalation and lateral movement, it is essential to patch vulnerabilities regularly. SOCRadar’s Vulnerability Management platform integrates vulnerability scanning tools that track known vulnerabilities associated with the techniques used by Cadet Blizzard. Timely patching and remediation of these vulnerabilities can significantly reduce the group’s ability to escalate privileges or move laterally within a network. - 24/7 Alerting and Incident Management
Given Cadet Blizzard’s tendency to target organizations at off-business hours, SOCRadar offers continuous monitoring for every digital asset with 24/7 alerting. This ensures that security teams are informed of suspicious activity, no matter the time of day. Quick action can be taken to block threats, prevent exfiltration, and minimize damage.
SOCRadar Attack Surface Management
Proactive Defense with SOCRadar
By combining the insights provided by SOCRadar with the defense strategies outlined above, organizations can build a robust defense against Cadet Blizzard and similar APT groups. SOCRadar’s real-time threat intelligence and comprehensive monitoring tools ensure that security teams are always informed of the latest threats and can act swiftly to mitigate potential risks. Together, these measures help organizations stay one step ahead of adversaries and protect critical assets.
For further readings, please refer to the CISA’s advisory and Microsoft’s blog.
What Are Their MITRE Techniques?
According to CISA’s advisory:
| Tactic | Technique | ID | Description |
| Reconnaissance | Gather Victim Network Information: DNS | T1590.002 | Used Amass and VirusTotal to gather DNS info for subdomains of target websites. |
| Active Scanning | T1595 | Utilizes open-source tools for active scanning during targeting. | |
| Active Scanning: Scanning IP Blocks | T1595.001 | Scans IP ranges using public tools to find victim IPs. | |
| Active Scanning: Vulnerability Scanning | T1595.002 | Scans for exploitable vulnerabilities in IoT devices using tools like Acunetix. | |
| Search Open Technical Databases: Scan Databases | T1596.005 | Uses Shodan to discover internet-connected hosts. | |
| Resource Development | Acquire Infrastructure: Virtual Private Server | T1583.003 | Uses VPS to host tools, perform recon, exploit, and exfiltrate data. |
| Obtain Capabilities: Malware | T1588.001 | Obtains publicly available malware for operations, like Raspberry Robin. | |
| Obtain Capabilities: Exploits | T1588.005 | Uses exploit scripts from GitHub to attack victim infrastructure. | |
| Initial Access | Valid Accounts: Default Accounts | T1078.001 | Uses default usernames and passwords to access IP cameras. |
| Exploit Public-Facing Application | T1190 | Exploits vulnerabilities in public-facing apps like CVE-2021-33044. | |
| Execution | Command and Scripting Interpreter: PowerShell | T1059.001 | Executes commands and operational tasks via PowerShell. |
| Persistence | Server Software Component: Web Shell | T1505.003 | Deploys web shells for persistent access. |
| Credential Access | OS Credential Dumping: LSASS Memory | T1003.001 | Exfiltrates LSASS memory dumps to retrieve credentials. |
| OS Credential Dumping: Security Account Manager | T1003.002 | Dumps usernames and hashed passwords from the SAM. | |
| Brute Force: Password Spraying | T1110.003 | Uses password spraying on Microsoft OWA infrastructure to collect credentials. | |
| Unsecured Credentials: Credentials in Files | T1552.001 | Dumps configuration files from IP cameras to collect credentials. | |
| Discovery | Network Service Discovery | T1046 | Uses Nmap scripts to discover and scan other machines in the network. |
| Log Enumeration | T1654 | Enumerates and exfiltrates SYSTEM and SECURITY logs. | |
| Lateral Movement | Use Alternate Authentication Material: Pass the Hash | T1550.002 | Uses Pass-the-Hash for SMB authentication. |
| Collection | Email Collection | T1114 | Compromises mail servers to exfiltrate emails. |
| Video Capture | T1125 | Exfiltrates images from IoT devices like IP cameras. | |
| Data from Information Repositories: Confluence | T1213.001 | Leverages Through the Wire to target Confluence servers. | |
| Archive Collected Data | T1560 | Compresses data to exfiltrate files or system information. | |
| Command and Control | Proxy: Multi-hop Proxy | T1090.003 | Uses ProxyChains for multi-hop proxy to anonymize traffic. |
| Application Layer Protocol: Web Protocols | T1071.001 | Sends payloads via POST requests over HTTP. | |
| Application Layer Protocol: DNS | T1071.004 | Uses DNS tunneling (e.g., dnscat/2, Iodine) for communication. | |
| Non-Application Layer Protocol | T1095 | Uses reverse TCP connection for communication. | |
| Ingress Tool Transfer | T1105 | Transfers Meterpreter payload for command execution. | |
| Protocol Tunneling | T1572 | Uses OpenVPN and GOST for traffic tunneling to anonymize activities. | |
| Exfiltration | Exfiltration Over Web Service: Exfiltration to Cloud Storage | T1567.002 | Exfiltrates data to cloud storage services like MEGA using Rclone. |
| Impact | Data Destruction | T1485 | Destroys data as part of their disruptive operations. |