
Dark Web Profile: dAn0n Hacker Group
Global law enforcement agencies have ramped up their efforts against ransomware, leading to the weakening of groups and even dethroned the long ruled LockBit. However, following these operations, many small groups emerged.
In April, 2024, a group calling themselves the dAn0n Hacker Group emerged. Although various sources label them as a ransomware group, they appear to function more as a data broker group. They have announced multiple victims from March 2024 to the end of May, and both their clearnet and TOR data leak sites are operational. Thus, this article serves as a preliminary research on the group.

The group uses simple typography text rather than an actual logo.
Who Is dAn0n Hacker Group
The group emerged at the end of April and has since posted information about 13 victims on their data leak site. Their DLS lacks in many aspects and just shows the victims and an e-mail address; there isn’t much detail in general.

A depiction image, created by Bing AI
Some sources have reported that the dAn0n group sets itself apart by engaging in both data brokerage and ransomware attacks. To gain initial access, the group uses phishing emails and then deploys custom ransomware binaries and obfuscated scripts to execute their payload. They employ tactics such as privilege escalation and defense evasion to maintain persistence and avoid detection.
However, so far we have not found any trace of ransomware or techniques to support these claims. Of course, we should also add that the term ransomware group can be used interchangeably by the cyber security community instead of data brokers or extortion groups.
Victimology
As stated above, there are currently 13 companies listed on Data Leak Sites (DLS), all of their data is published and out of 13 victims, 12 are based in the United States, only other country targeted is Ireland.
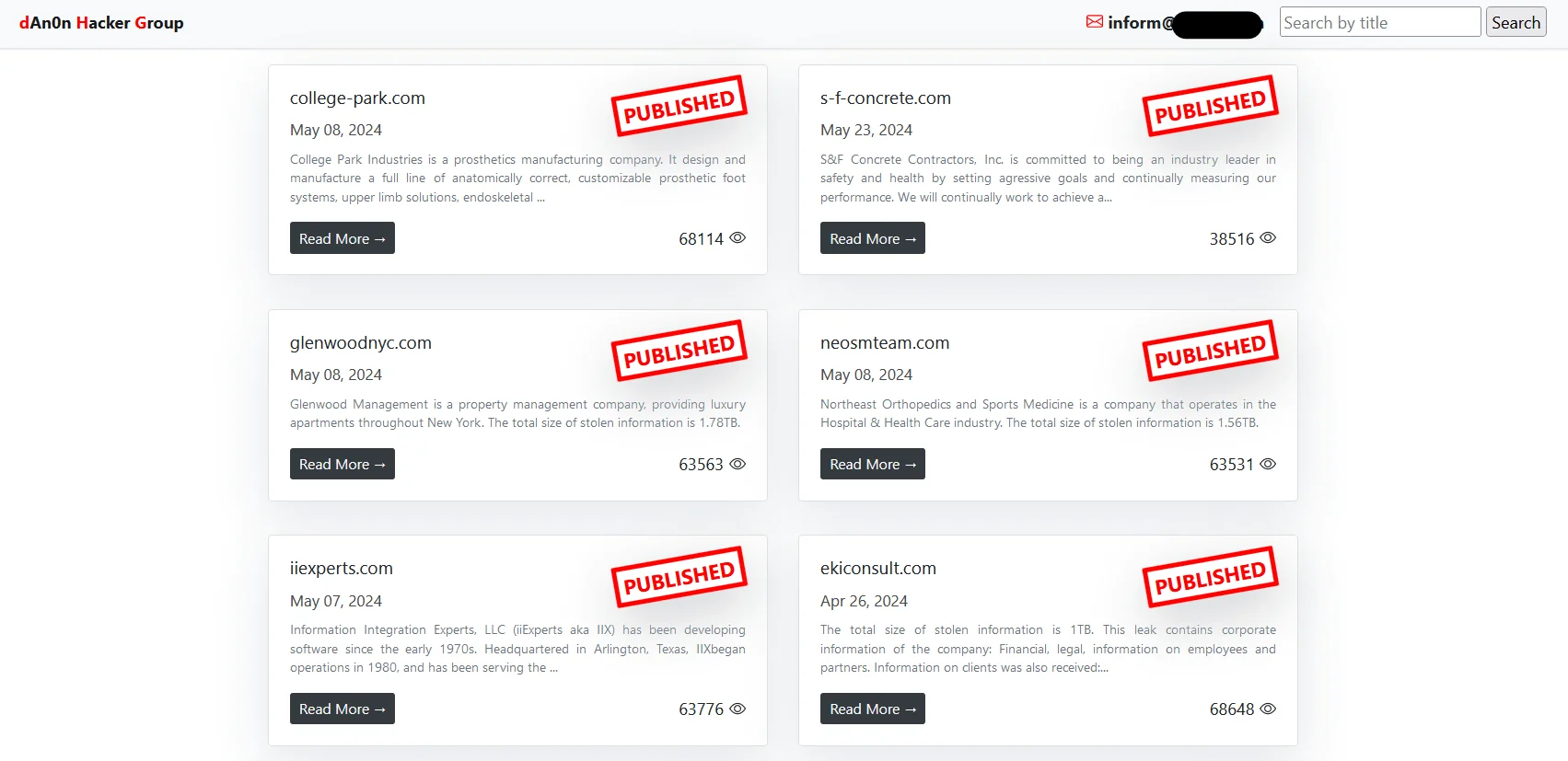
Main page of dAn0n’s DLS
An interesting detail about the group is that they provide status updates about their victims and negotiations.
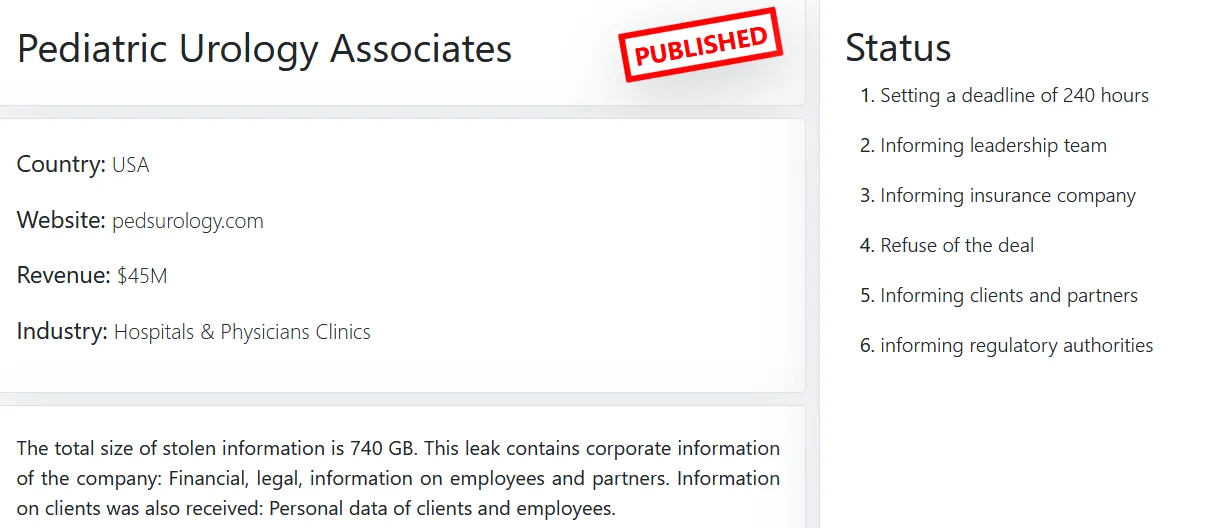
First victim of the dAn0n
As stated on their DLS the targeted sectors are as follows:
- Hospitals & Physicians Clinics – 1
- Law Firms & Legal Services – 2
- Insurance – 1
- Specialty Trade Contractors – 1
- Electronics – 1
- Architecture, Engineering & Design – 2
- Software – 1
- Healthcare – 1
- Real Estate – 1
- Commercial & Residential Construction – 1
- Medical Devices & Equipment – 1
Like many new and novice data broker groups, they share the leaked data on clear web file sharing sites, and files with over 60 thousand views are still available for download.
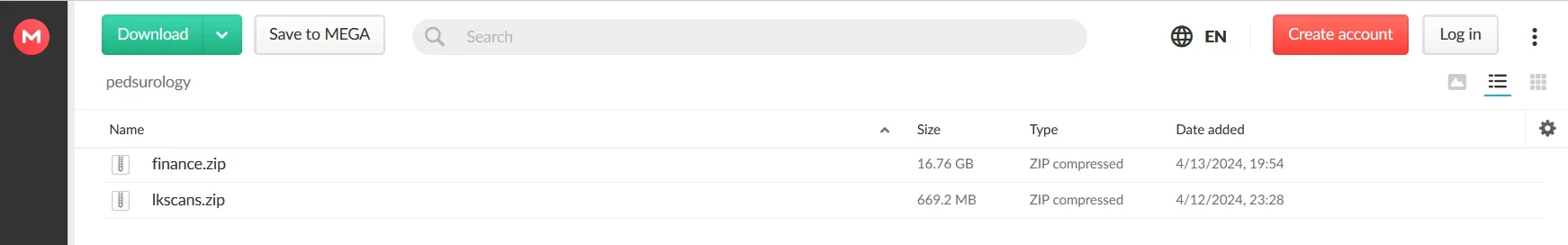
Uploaded files of a victim in a file sharing website
Furthermore, in the alleged data publish posts, they typically attempt to verify the data by providing images, such as invoice information or a hand-signed bill belonging to the company.
Conclusion
Although there may not be much to conclude at present, it is evident that the landscape of ransomware and data brokerage is continually changing. A big factor is the intensified efforts of global law enforcement agencies. These efforts have severely weakened established groups like LockBit but have also paved the way for the emergence of new players such as the dAn0n Hacker Group.
While initially labeled as a ransomware group, dAn0n seems to operate more as a data broker group based on preliminary research. Their method of operation involves phishing emails, custom ransomware binaries, and obfuscated scripts, although evidence of ransomware activities is yet to be fully substantiated. Their data leak site showcases a growing list of victims predominantly from the United States and Ireland, spanning various sectors.
Data Protection Focus: Mitigating Risks Posed by dAn0n and Similar Threat Actors
To combat threats like dAn0n and other Data Broker groups, organizations need a robust mitigation strategy centered on data protection. Here’s a condensed approach to mitigating risks:
- Data Classification and Encryption
Classify sensitive data (customer info, financial records) and encrypt it at rest and in transition, using strong algorithms to prevent unauthorized access.
- Access Control and Least Privilege
Enforce strict access controls based on the principle of least privilege to limit data access to essential roles.
- Network Segmentation and Monitoring
Segment networks to contain breaches and deploy robust monitoring tools to detect and respond to suspicious activities.
- Employee Training and Awareness
Conduct regular cybersecurity training to educate employees about threats like phishing and foster a culture of security awareness.
- Incident Response Plan
Develop a comprehensive incident response plan tailored for data breaches and extortion attempts by groups like dAn0n.
- Backup and Recovery
Implement a reliable backup strategy and regularly test backup systems to ensure data availability in case of attacks.
- Vendor and Third-Party Risk Management
Evaluate vendors’ security posture, establish contractual agreements with security requirements, and mitigate third-party risks effectively.
Evaluate vendors’ security posture, establish contractual agreements with security requirements, and mitigate third-party risks effectively.
By implementing these measures, organizations can bolster their defenses against data extortion threats from groups like dAn0n. Continuous monitoring, testing, and refinement of these strategies are crucial to adapt to evolving cyber threats effectively.
Additionally, SOCRadar offers advanced capabilities for detecting and mitigating data breaches and credential compromises, enhancing your organization’s resilience against cyber threats. SOCRadar provides early threat detection, real-time alerts, comprehensive threat intelligence, intellectual property protection, and resource optimization to strengthen your cybersecurity posture.
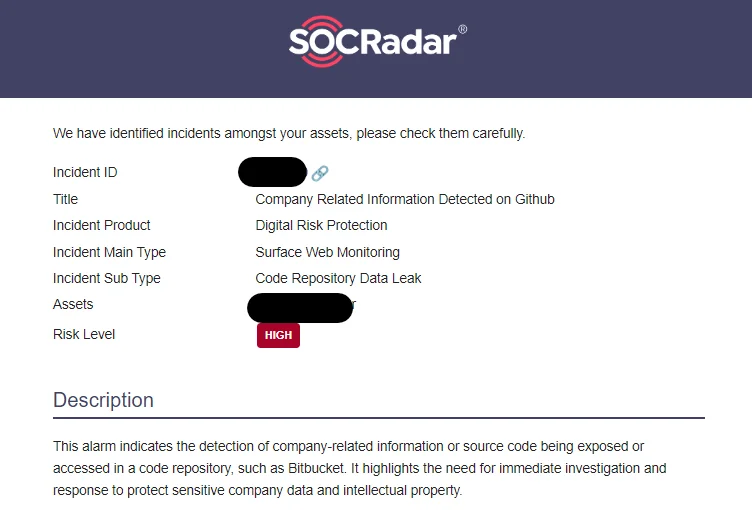
One such alert example of SOCRadar



































