Dark Web Profile: Fog Ransomware
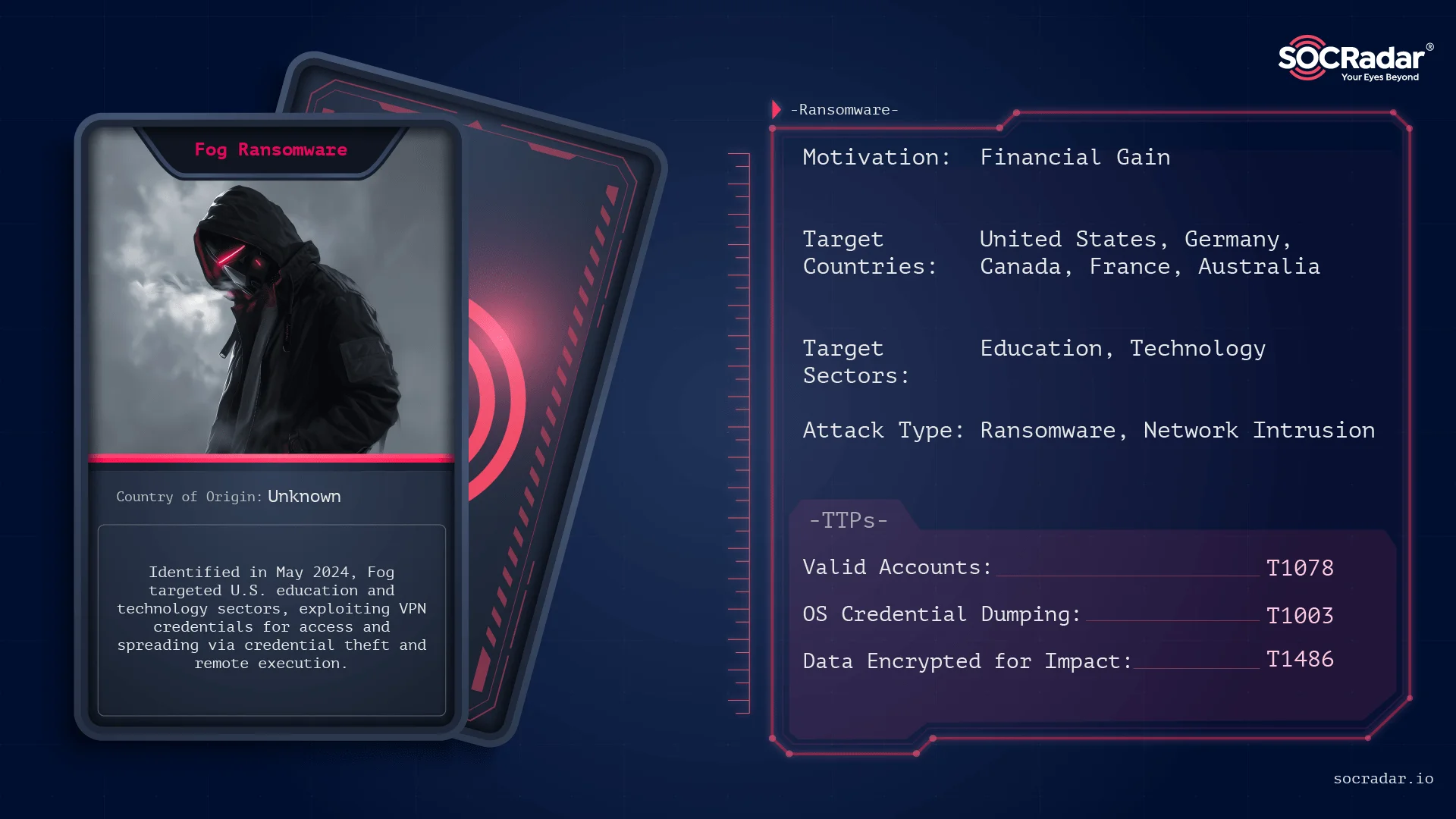
Fog Ransomware emerged in April 2024, was first detected in the wild in early May, primarily targeting US based educational institutions targeting both Windows and Linux endpoints. It operates as a multi-pronged extortion campaign, utilizing a TOR-based data leak site (DLS) to list victims and host stolen data for those who refuse to comply with ransom demands.
Who is Fog Ransomware?
According to Arctic Labs, their incident response team began investigating cases involving the deployment of Fog ransomware against US organizations in the education and recreation sectors starting in early May.
Researchers classify Fog as a ransomware variant rather than a ransomware group, distinguishing between the entities responsible for developing the encryptor software and those carrying out hands-on-keyboard attacks. This distinction is crucial, as ransomware groups often present themselves as unified entities when, in reality, they operate through independent affiliate groups. At this time, the organizational structure behind the deployment of Fog ransomware remains unknown.
Threat actor card for Fog Ransomware
What are Fog Ransomware’s Targets?
Fog ransomware has rapidly emerged as a significant cyber threat, affecting a wide range of industries and geographic locations. The ransomware group’s attack patterns indicate a strong preference for targeting businesses, educational institutions, and technology firms, with a particularly heavy focus on victims in the United States.
Geographic Targeting
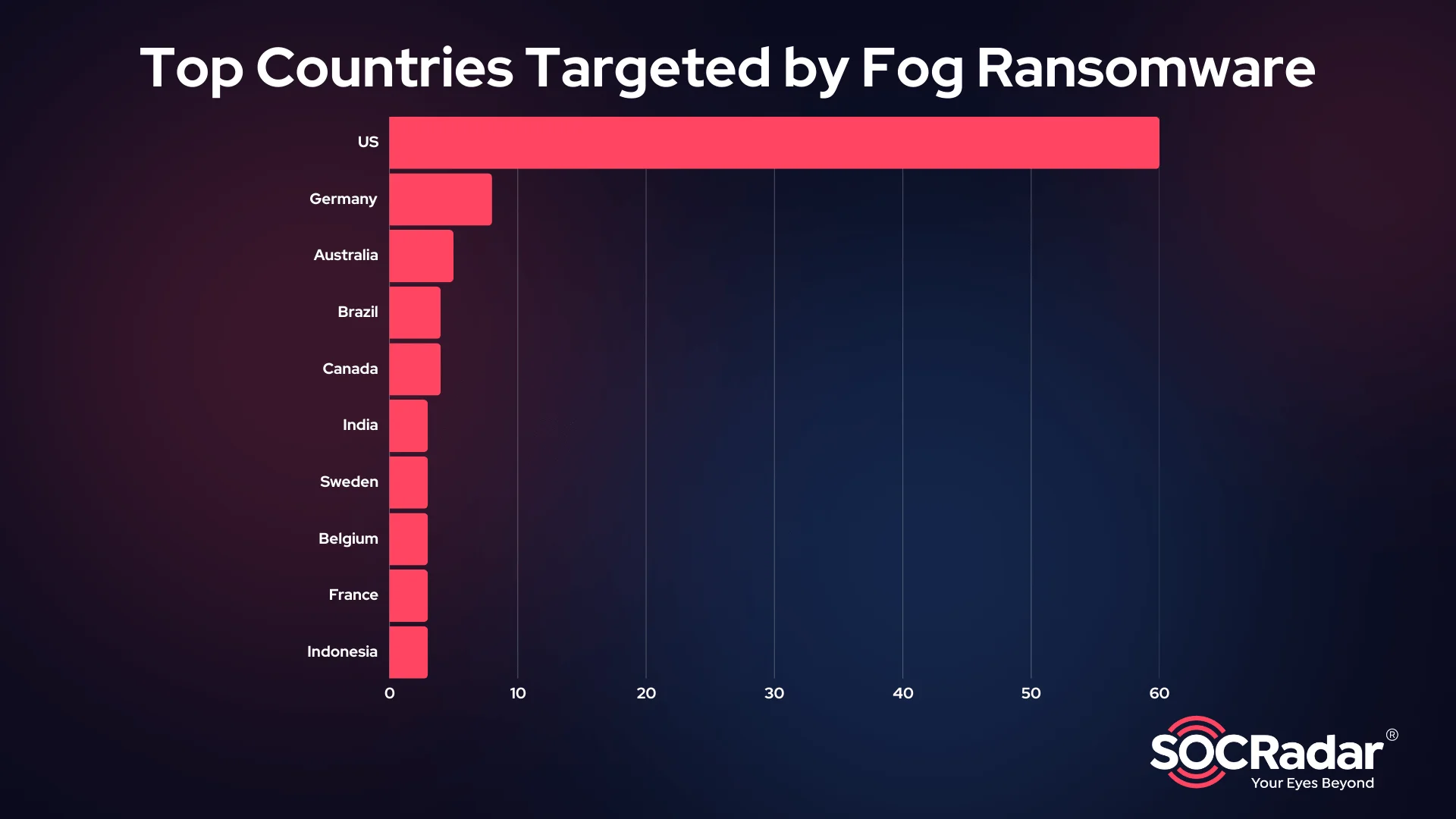
The United States is overwhelmingly the most affected country, with 60 out of 118 recorded victims—accounting for half of all known attacks. This dominance suggests that Fog ransomware operators may either be strategically focusing on North American organizations or that these victims are more transparent in reporting incidents.
Top countries targeted by Fog Ransomware
Beyond the U.S., Germany (8 victims), Australia (5 victims), and Brazil (4 victims) also show notable activity. Other affected nations include Canada, India, Sweden, Belgium, France, and Indonesia, each with at least three recorded incidents. The wide distribution of victims across Europe, North America, and parts of Asia-Pacific suggests a broad, almost non-geographically constrained attack strategy. However, like many ransomware groups, Fog Ransomware didn’t target Russia, CIS countries and China. Suggesting that the group might be Russia-based(?).
Industry Targeting
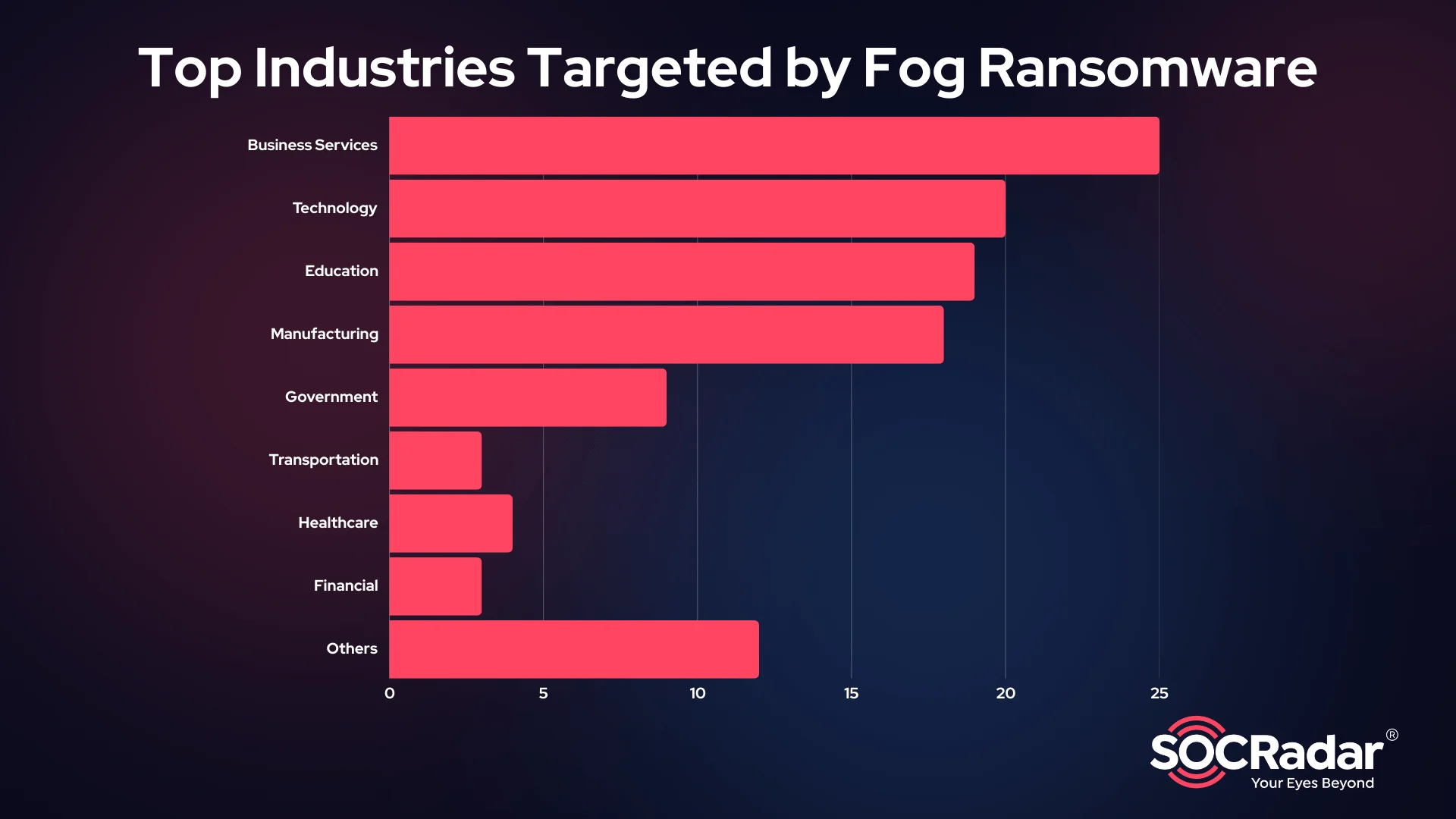
Fog ransomware does not limit itself to a single industry but shows a clear preference for business services, technology firms, and educational institutions.
Top industries targeted by Fog Ransomware
The most affected sectors include:
- Business Services (25 victims): This sector is particularly attractive due to the vast number of third-party integrations and client data these firms handle. A successful attack on a service provider can impact multiple organizations downstream.
- Technology (20 victims):Targeting IT companies suggests potential supply chain attacks, where compromising one organization could provide access to multiple others and can be lucrative for threat actors.
- Education (19 victims): Schools and universities are commonly targeted, likely due to weaker cybersecurity defenses and the presence of sensitive student and faculty data.
- Manufacturing (18 victims): The attacks on industrial firms indicate that Fog ransomware may be interested in operational disruption. Due to the nature of the business, production disruption in manufacturing could lead to ransomware payment.
- Government (9 victims): With several municipalities, school districts, and agencies on the victim list, public sector organizations remain a notable target.
Other affected sectors include transportation & logistics, agriculture, healthcare, and financial services, further showcasing Fog ransomware’s broad impact.
Key Observations
- Strong Focus on the US: The sheer volume of American victims suggests that either Fog ransomware has a particular interest in US-based businesses or that American companies report cyber incidents more frequently than those in other countries.
- Data-Driven Targeting: The ransomware group’s preference for business services and technology firms aligns with data exfiltration and extortion tactics.
- Opportunistic Industry Selection: The variety of industries affected suggests that Fog ransomware does not discriminate between targets. Instead, it likely exploits vulnerabilities and access opportunities as they arise.
- High-Risk Sectors: Organizations in education, manufacturing, and government should focus on cybersecurity, as these sectors remain prime and susceptible targets.
Fog ransomware has demonstrated an aggressive, widespread, and financially motivated attack strategy, with a clear emphasis on business services, technology firms, and educational institutions. The group’s heavy focus on US organizations and data-rich industries suggests that they prioritize extortion and operational disruption over purely destructive attacks.
What are Fog Ransomware’s Tactics?
Fog Ransomware follows a multi-stage attack process, employing a combination of data encryption and extortion techniques to maximize its impact on victims. This ransomware variant has been actively targeting Windows and Linux systems, with a strong focus on US based organizations in the education and business sectors. Its attack pattern suggests a double extortion model, where both file encryption and data theft are used to pressure victims into compliance.
Initial Access & Compromise
The attack begins with gaining initial access to the victim’s network. Fog operators exploit vulnerabilities in public-facing applications, weak Remote Desktop Protocol (RDP) configurations, phishing emails, or stolen credentials to infiltrate target environments. The group appears to adopt opportunistic targeting, rather than focusing on specific industries or geographic locations, though U.S. organizations have been disproportionately affected.
Once inside, Fog Ransomware establishes persistence by modifying system configurations, such as adding registry keys, creating scheduled tasks, or deploying PowerShell scripts. This ensures that even if the system reboots or partial remediation efforts are made, the malware remains active.
Privilege Escalation & Lateral Movement
After securing a foothold, the ransomware attempts to escalate privileges to gain administrative control over the infected system. By leveraging tools such as Mimikatz, LSASS memory dumping, or exploiting unpatched system vulnerabilities, attackers can obtain credentials that allow them to move across the network.
With elevated privileges, Fog ransomware moves laterally, identifying high-value systems, file servers, and backup storage locations. The malware may also disable security tools, terminate Endpoint Detection and Response (EDR) services, and delete system logs to evade detection.
Data Exfiltration & Double Extortion Tactics
Unlike traditional ransomware strains that only encrypt files, Fog operators employ a double extortion strategy. Before initiating encryption, the malware exfiltrates sensitive files from compromised systems and uploads them to attacker-controlled servers. This stolen data often includes financial records, customer information, and internal documents, which are later used to pressure victims into paying the ransom.
Fog ransomware utilizes a TOR-based data leak site (DLS) to list non-compliant victims and publish stolen data if the ransom is not paid. This approach increases the psychological pressure on organizations, as public exposure of sensitive data can lead to regulatory penalties, reputational damage, and further legal consequences.
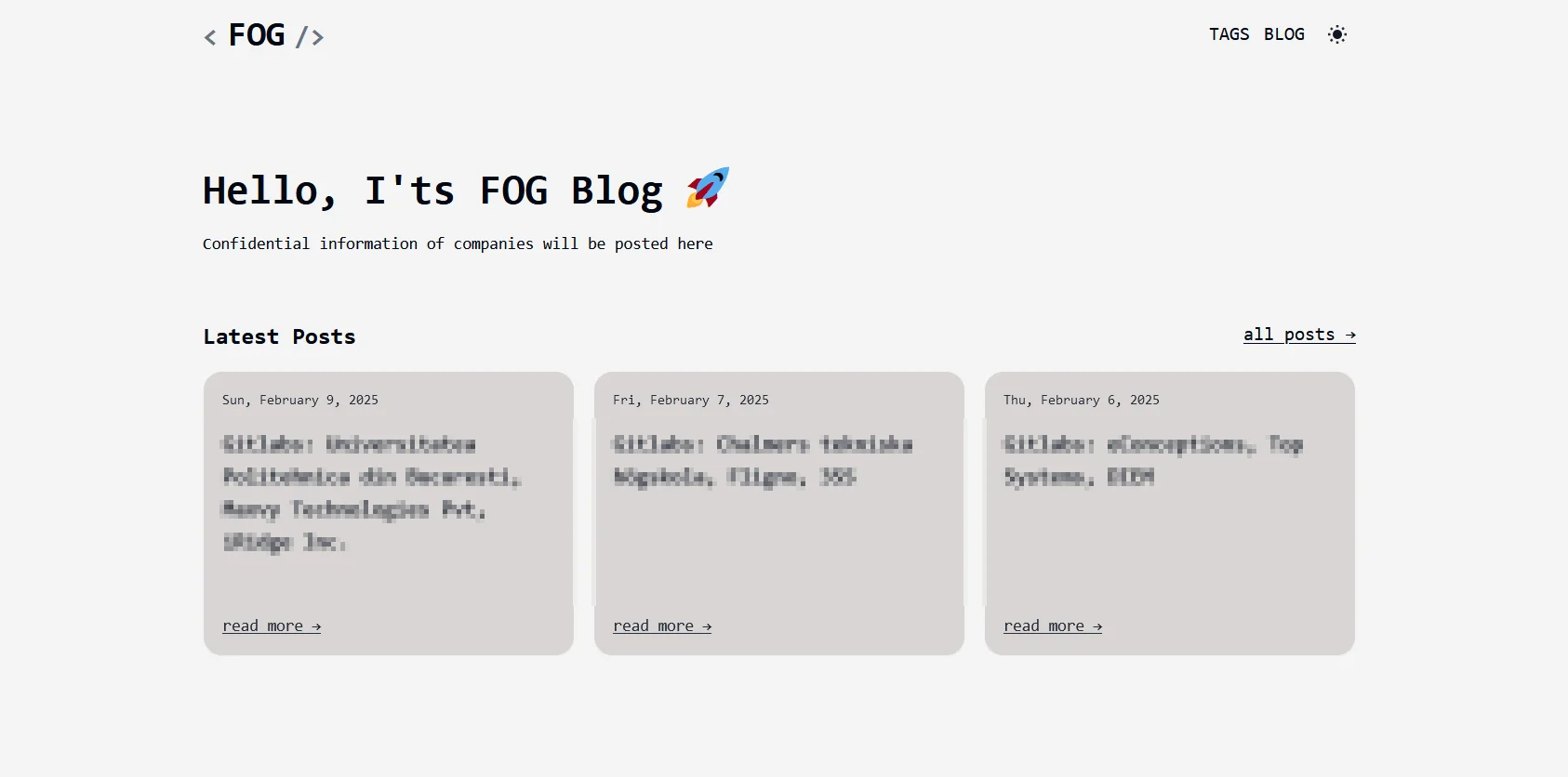
Fog Ransomware’s DLS
File Encryption & Ransom Demand
Once the exfiltration process is complete, the ransomware proceeds with encrypting files across the victim’s network. Fog ransomware is designed to encrypt documents, databases, and backups, effectively locking the victim out of critical operational data. The encryption algorithm is strong enough to make recovery without a decryption key nearly impossible.
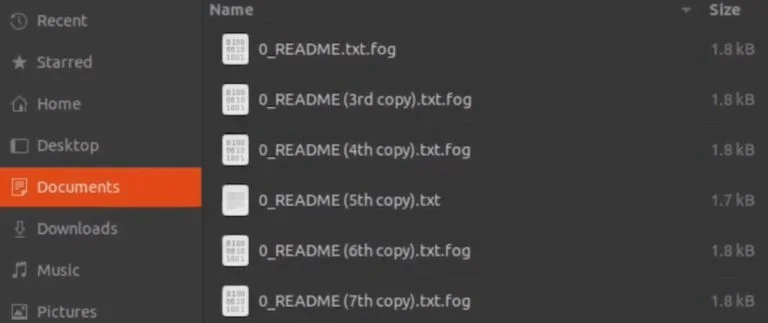
During the encryption the extensions .fog, .Fog or .FLOCKED are appended to the affected files (SentinelOne)
After encryption, a ransom note is dropped on the infected system, typically containing:
- Instructions on how to contact the attackers.
- The amount of ransom demanded, usually in cryptocurrency.
- Threats to leak stolen data if payment is not made within a specified timeframe.
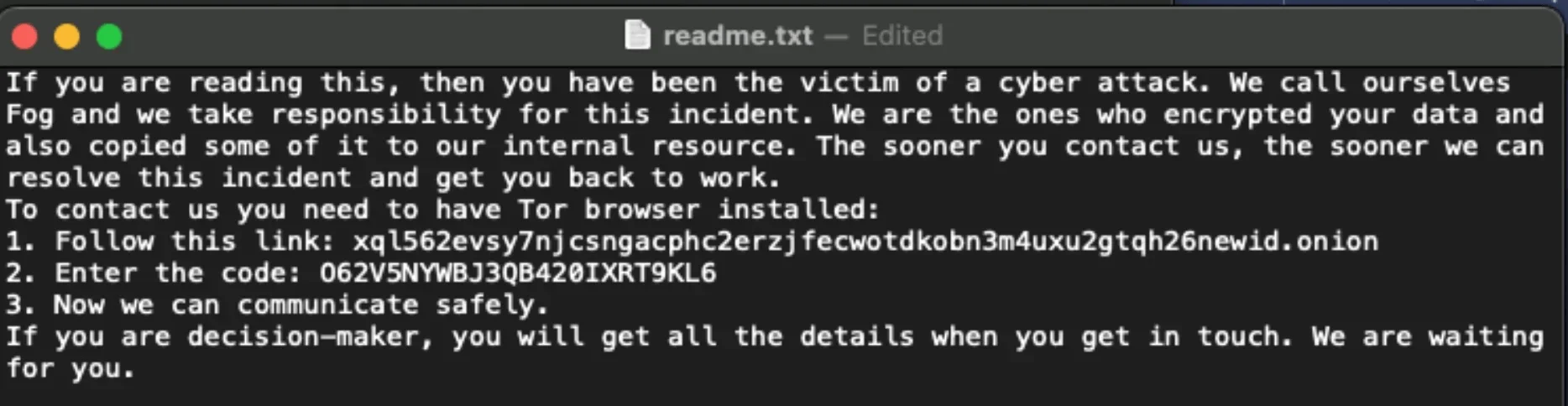
Ransom note (SentinelOne)
Victims are directed to the TOR-based leak site, where attackers post updates on leaked data as an additional coercion tactic. Some cases indicate that Fog may engage in direct negotiations with victims, adjusting ransom demands based on the organization’s perceived ability to pay.
Login screen for victims
How to Defend Your Organization Against Fog Ransomware and Other Ransomware Threats?
Defending your organization against Fog Ransomware and similar threats requires a comprehensive, multi-layered security strategy.
By implementing the following measures, you can significantly reduce the risk of infection and enhance your organization’s resilience against ransomware attacks:
- Implement Multi-Factor Authentication (MFA): Enforce MFA across all user accounts, especially for remote access services like Virtual Private Networks (VPNs). This additional layer of security helps prevent unauthorized access, even if credentials are compromised.
- Regularly Update and Patch Systems: Keep all software, including operating systems and applications, up-to-date with the latest security patches. Regular updates help close vulnerabilities that ransomware exploits to gain access.
- Conduct Employee Training and Awareness Programs: Educate employees on recognizing phishing attempts and the importance of cybersecurity best practices. Regular training sessions can reduce the likelihood of successful social engineering attacks.
- Deploy Advanced Endpoint Detection and Response (EDR) Solutions: Utilize EDR tools capable of identifying and responding to malicious activities, such as lateral movement and data exfiltration. These solutions can detect and block ransomware before it causes significant damage.
- Implement Network Segmentation and Zero Trust Architecture: Divide your network into segments to contain potential infections and limit lateral movement. Adopting a Zero Trust model ensures that all users and devices are continuously authenticated and authorized.
- Regularly Back Up Data and Secure Backups: Perform regular backups of critical data and store them in secure, offline locations. Ensure that backups are protected from unauthorized access and cannot be altered or deleted by ransomware.
- Monitor Network Traffic for Anomalies: Continuously monitor network traffic to detect unusual patterns or communications with known malicious servers. Early detection of anomalies can help prevent data exfiltration and other malicious activities.
- Restrict the Use of Administrative Privileges: Limit administrative privileges to essential personnel and implement the principle of least privilege. Regularly review and revoke unnecessary access rights to reduce the risk of privilege escalation by attackers.
- Develop and Test an Incident Response Plan: Establish a comprehensive incident response plan that outlines procedures for detecting, containing, and recovering from ransomware attacks. Regularly test and update the plan to ensure its effectiveness during an actual incident.
- Utilize Advanced Security Technologies: Consider deploying solutions such as AI-driven analytics, Extended Detection and Response (XDR), and Security Information and Event Management (SIEM) systems to enhance threat detection and response capabilities
By proactively implementing these strategies, organizations can strengthen their defenses against Fog Ransomware and other evolving ransomware threats, minimizing potential disruptions and safeguarding critical assets.
How Can SOCRadar Help?
SOCRadar provides comprehensive threat intelligence and security solutions to help organizations detect, prevent, and respond to ransomware threats like Fog Ransomware. By leveraging SOCRadar’s Extended Threat Intelligence (XTI) platform, security teams can gain real-time insights into ransomware activities and take proactive measures to protect their infrastructure.
1. Dark Web Monitoring & Threat Intelligence
SOCRadar’s Advanced Dark Web Monitoring continuously scans underground forums, ransomware leak sites, and marketplaces for stolen data, threat actor discussions, and potential attack indicators. Organizations can receive early warnings if their data appears on Fog Ransomware’s TOR-based leak site, allowing them to respond before further damage occurs.
2. Attack Surface Management
SOCRadar’s Attack Surface Management (ASM) identifies exposed assets, vulnerabilities, and misconfigurations that ransomware groups may exploit. This helps security teams patch weaknesses before attackers can leverage them for initial access.
3. Digital Risk Protection
By monitoring phishing domains, leaked credentials, and impersonation attempts, SOCRadar helps organizations mitigate risks from credential theft and social engineering tactics—common entry points for Fog Ransomware attacks.
SOCRadar’s Ransomware Intelligence
SOCRadar’s comprehensive threat intelligence solutions help organizations stay ahead of ransomware threats by providing early warning systems, attack surface visibility, and dark web monitoring. With SOCRadar’s proactive approach, businesses can identify risks before they escalate, reducing the impact of ransomware attacks like Fog Ransomware.
What are Fog Ransomware’s MITRE TTPs?
(By Arctic Wolf)
| Tactic | Technique | ID | Description |
| Initial Access | Phishing | T1566 | Uses phishing emails to trick users into downloading malicious payloads. |
| Exploitation of Public-Facing Apps | T1190 | Exploits vulnerabilities in internet-facing applications to gain access. | |
| Execution | Command and Scripting Interpreter | T1059 | Uses PowerShell or Bash scripts to execute malicious commands. |
| Persistence | Scheduled Task/Job | T1053 | Creates scheduled tasks to maintain access after a reboot. |
| Privilege Escalation | Abuse Elevation Control Mechanism | T1548 | Exploits vulnerabilities or misconfigurations to gain admin privileges. |
| Defense Evasion | Obfuscated Files or Information | T1027 | Uses packing, encryption, or other methods to evade detection. |
| Credential Access | Credential Dumping | T1003 | Uses tools like Mimikatz to steal credentials from memory. |
| Discovery | System Information Discovery | T1082 | Gathers information about the infected system. |
| Lateral Movement | Remote Services (RDP, SMB) | T1021 | Uses compromised credentials to move laterally within the network. |
| Collection | Data from Local System | T1005 | Gathers sensitive files before exfiltration. |
| Exfiltration | Exfiltration Over Web Service | T1567 | Sends stolen data to attacker-controlled servers. |
| Impact | Data Encrypted for Impact | T1486 | Encrypts victim files and demands ransom for decryption. |
Tools Used by Fog Ransomware
| Tool | Function |
| Mimikatz | Extracts credentials from memory for privilege escalation. |
| PowerShell | Executes malicious scripts for persistence and system manipulation. |
| PsExec | Executes commands remotely to facilitate lateral movement. |
| Rclone | Used for data exfiltration to cloud storage services. |
| Cobalt Strike | Provides command-and-control (C2) capabilities for attackers. |
| GMER | Disables security tools and hides malicious activity. |
These techniques and tools highlight Fog Ransomware’s sophisticated attack chain, making early detection and proactive defense critical for organizations.
In Summary
Fog Ransomware has quickly established itself as a significant cyber threat, leveraging double extortion tactics to target a wide range of industries, primarily in the United States. Emerging in April 2024, it was first detected in the wild in May 2024, with a particular focus on educational institutions, business services, and technology firms. Unlike traditional ransomware groups, Fog is classified as a ransomware variant, separating the developers of the encryptor software from the affiliates conducting the attacks.
The United States accounts for over 50% of known victims, followed by Germany, Australia, and Brazil. The ransomware’s broad international reach, coupled with its absence of attacks on Russia, CIS countries, and China, suggests a possible origin linked to Russian-speaking cybercriminals.
To defend against Fog Ransomware and similar threats, organizations must adopt a proactive cybersecurity strategy, including multi-factor authentication (MFA), endpoint detection and response (EDR), network segmentation, and regular security training. SOCRadar plays a crucial role in detecting and mitigating ransomware threats by providing dark web monitoring, attack surface management, and real-time intelligence.
As threats like Fog Ransomware continue to evolve, early detection, robust security practices, and threat intelligence integration will be key to minimizing its impact.





































