
Dark Web Profile: FunkSec
[Update] January 4, 2024: “Update: FunkSec Expands Their Operation and Teams Up With Other Cyber Criminals”
A new ransomware group, FunkSec, has gained attention after taking responsibility for attacks on numerous victims in December 2024. By January 2025, the group continued to target new victims, with the total number surpassing 100. FunkSec seems to be engaged in both hacktivism and ransomware/extortion, with its members likely being relatively inexperienced threat actors aiming to establish their presence and gain recognition.

Threat actor card of FunkSec
Who is FunkSec?
FunkSec, a new ransomware group, emerged in December 2024 and claimed responsibility for attacks on multiple victims. By the time of writing the number of victims reached 129. The group appears to be involved in both hacktivism and ransomware, with members likely inexperienced and seeking recognition.

FunkSec Ransomware’s DLS
Researchers suggest that the file-encrypting malware, written in Rust, was likely developed by an inexperienced malware creator from Algeria with the assistance of AI. The developer also uploaded parts of the ransomware’s source code online. Operating under the Ransomware-as-a-Service (RaaS) model, FunkSec engages in double extortion, threatening to release stolen data to coerce victims into paying the ransom.
Researchers found that FunkSec’s members have linked their ransomware development to AI in public communications. They released an AI chatbot based on Miniapps to support their operations. Publicly available scripts from the group include detailed code comments in flawless English, which researchers believe were likely generated by a Large Language Model (LLM).
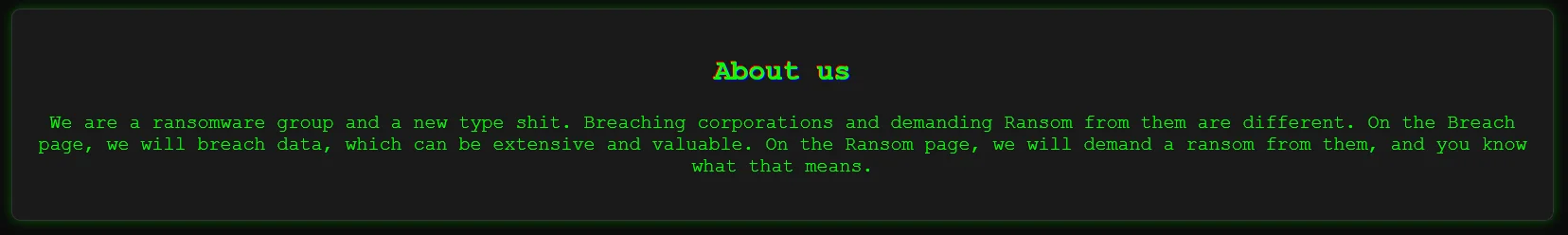
FunkSec’s DLS, “About us” section: “We are a ransomware group and a new type shit. Breaching corporations and demanding Ransom from them are different. On the Breach page, we will breach data, which can be extensive and valuable. On the Ransom page, we will demand a ransom from them, and you know what that means.”
Thus, as stated above, since December 2024, FunkSec has been adding victims to a data leak site, which also hosts a custom DDoS tool, a smart password generation and scraping tool, and a Hidden Virtual Network Computing (hVNC) module that the group claims is fully undetected.
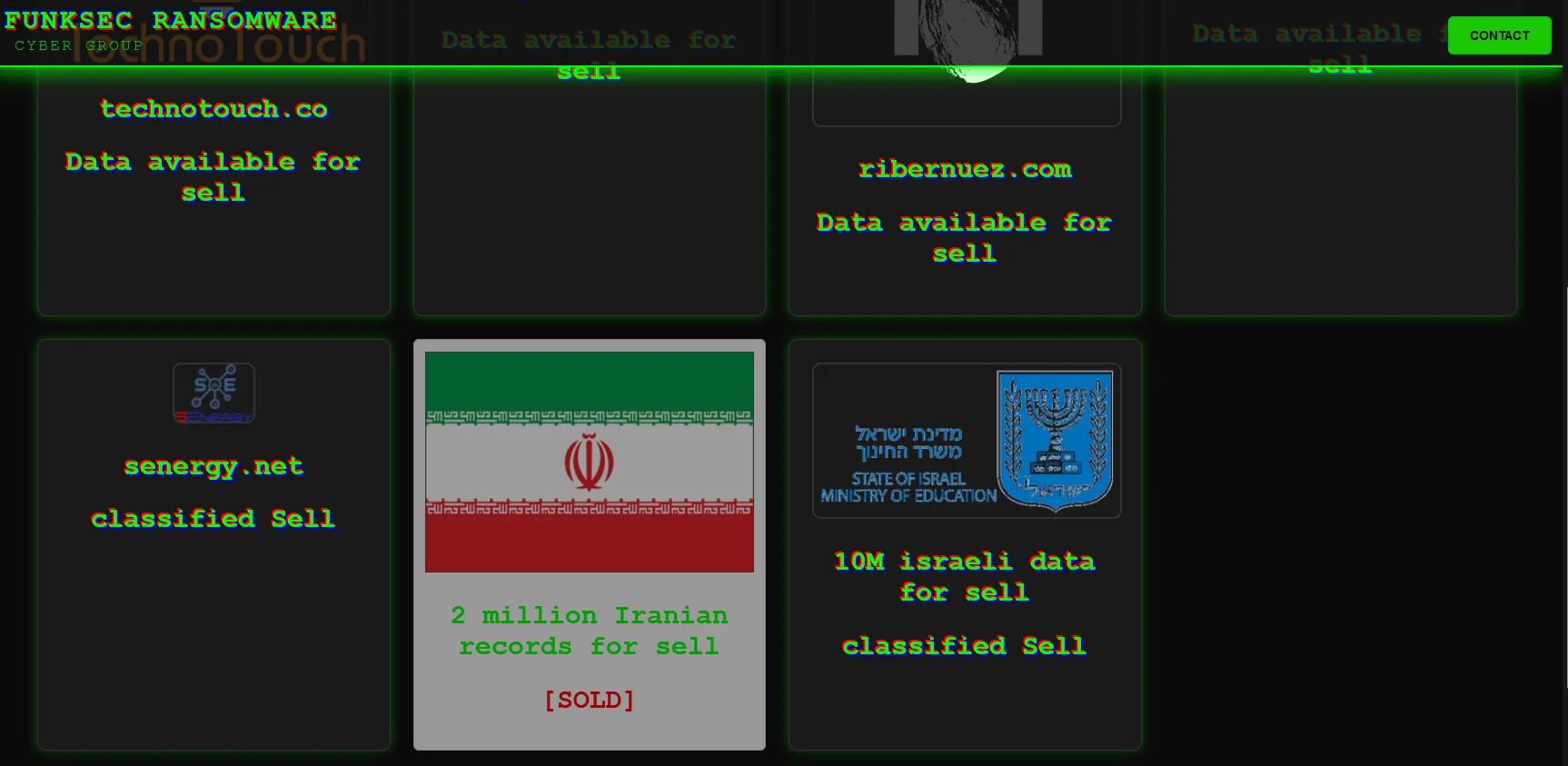
Their DLS also has a marketplace section for alleged stolen data
In December, FunkSec gained attention for its aggressive victimization, claiming over 80 victims in just over a month. The group demanded low ransoms and sold stolen data at reduced prices. Analysis of their operations suggests a mix of hacktivism and cybercrime motivations. Some members, with a history in hacktivism, add complexity to their objectives, making FunkSec an intriguing case for further investigation.
According to researchers, FunkSec’s name first appeared back in October 2024, used by a threat actor known as Scorpion or DesertStorm, and later promoted by an associate named El_Farado. Other threat actors, such as XTN, Blako, and Bjorka, are believed to be connected to Scorpion and FunkSec.
What are FunkSec’s Targets?
According to their Data Leak Site (DLS), FunkSec has been responsible for targeting organizations across various industries and geographic regions. Their attacks, as documented, provide insight into their operational focus and victim preference
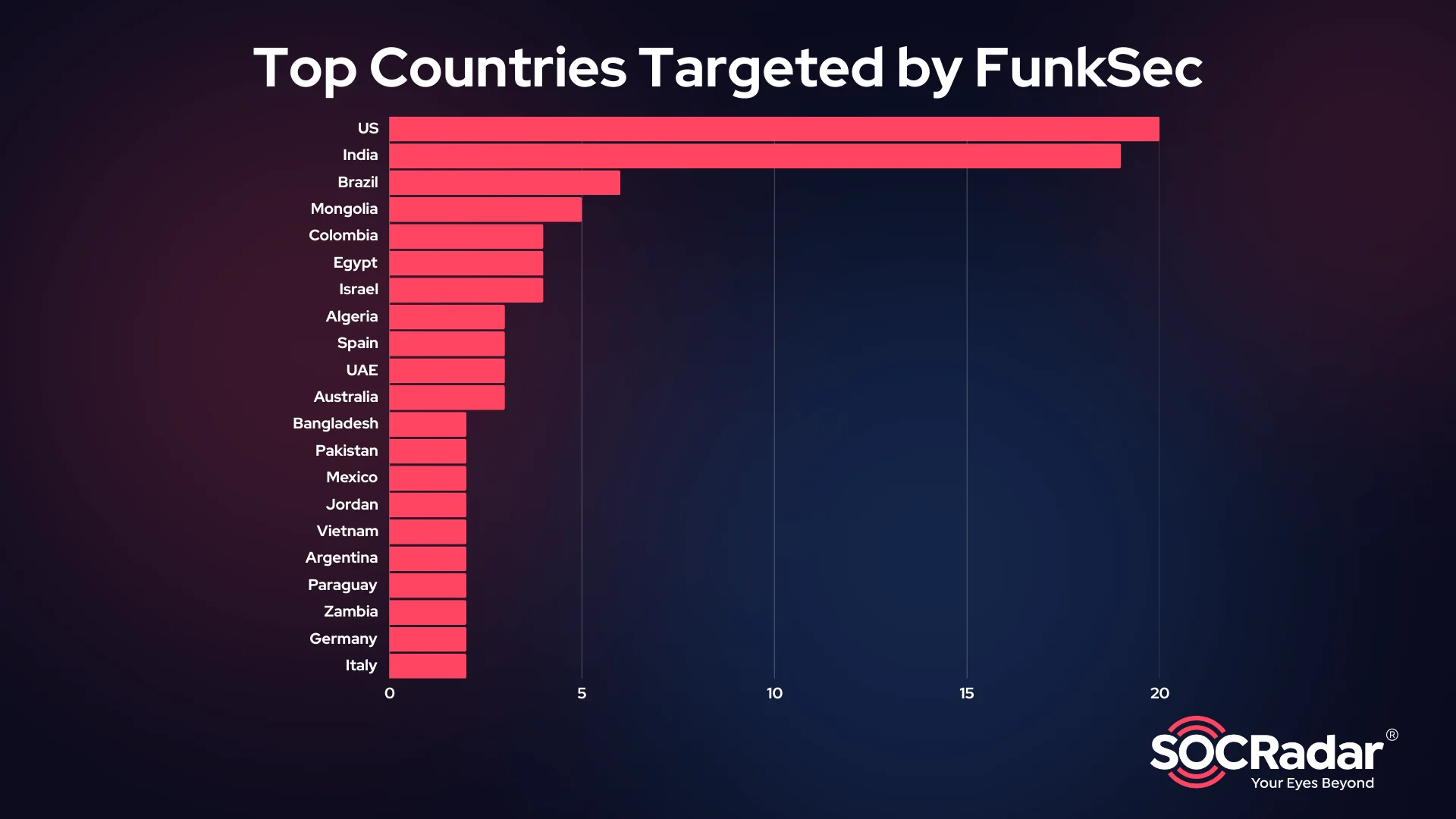
Most targeted countries by FunkSec
Geographic Distribution
The group has affected victims in 47 countries, demonstrating a global reach. The most targeted nations include:
- United States: 20 victims, making it the primary focus of attacks.
- India: 19 victims, indicating a strong presence in South Asia.
- Brazil, Mongolia, Colombia, Egypt, and Israel: With 3 to 6 victims each, these countries also face notable activity.
Single victim occurrences are associated with the following countries: Russia, Morocco, Greece, Malaysia, Indonesia, Laos, Nepal, Lebanon, British Virgin Islands, Turkiye, Singapore, Cambodia, Poland, Chile, Canada, Taiwan, Spain, Nigeria, Kenya, North Macedonia, Netherlands, Japan, Switzerland, Uzbekistan, Costa Rica, Qatar, Thailand, Hong Kong, Gabon, France, Tunisia.
This level of extreme geographic diversity indicates that FunkSec does not limit its operations to specific regions, potentially exploiting vulnerabilities irrespective of location.
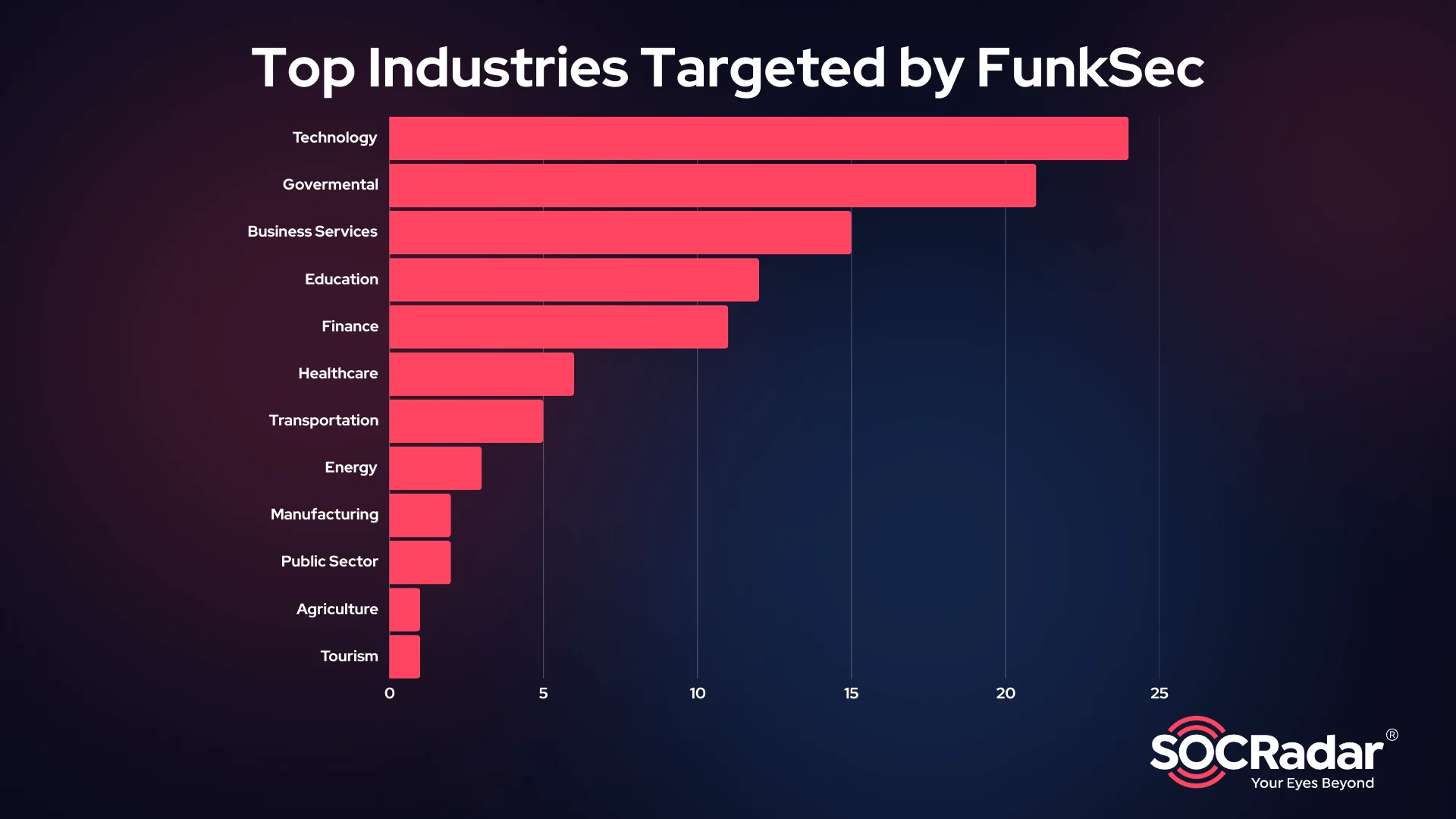
Most targeted sectors by FunkSec
Industries Targeted
The group exhibits a clear focus on industries critical to infrastructure and services:
- Technology: 24 victims, representing the highest sectoral targeting. This may suggest an interest in intellectual property, operational disruption, or ransom profitability in a tech-dependent economy.
- Government: 21 victims, highlighting a significant risk to public sector entities.
- Business Services: 15 victims, reflecting an impact on enterprises providing operational and consulting services.
- Education (12 victims), Financial Services (10 victims), and Healthcare (6 victims) also show substantial targeting, potentially exploiting these sectors’ reliance on sensitive data and continuous availability.
- Other industries include Energy, Manufacturing, Transportation/Logistics, Hospitality, and Agriculture, indicating a broad operational scope.
To sum up, the group appears to focus on sectors where downtime and data loss have immediate consequences, making victims more likely to pay ransoms. Their targeting of governmental and educational institutions also suggests a willingness to disrupt societal operations for monetary gain.
What are FunkSec’s Tactics?
FunkSec’s operations center around a rapidly evolving set of malicious tools, with a primary focus on ransomware, then DDoS tools, and various hacking utilities. The group’s activities reveal a hybrid blend of ransomware operations and hacktivist-style campaigns, showcasing both technical ambition and strategic messaging.
Ransomware Operations
FunkSec’s ransomware is a significant part of their arsenal. The operators boasted about their malware’s low detection rates, promoting new versions via their website, which has seen frequent updates as new features are integrated. For instance, their version 1.5 was highlighted for having a minimal detection rate, with only three antivirus engines flagging it during its release. The operators upload their samples to Virus Total to prove this, and the rest of the technical analysis is revealed through this variant.
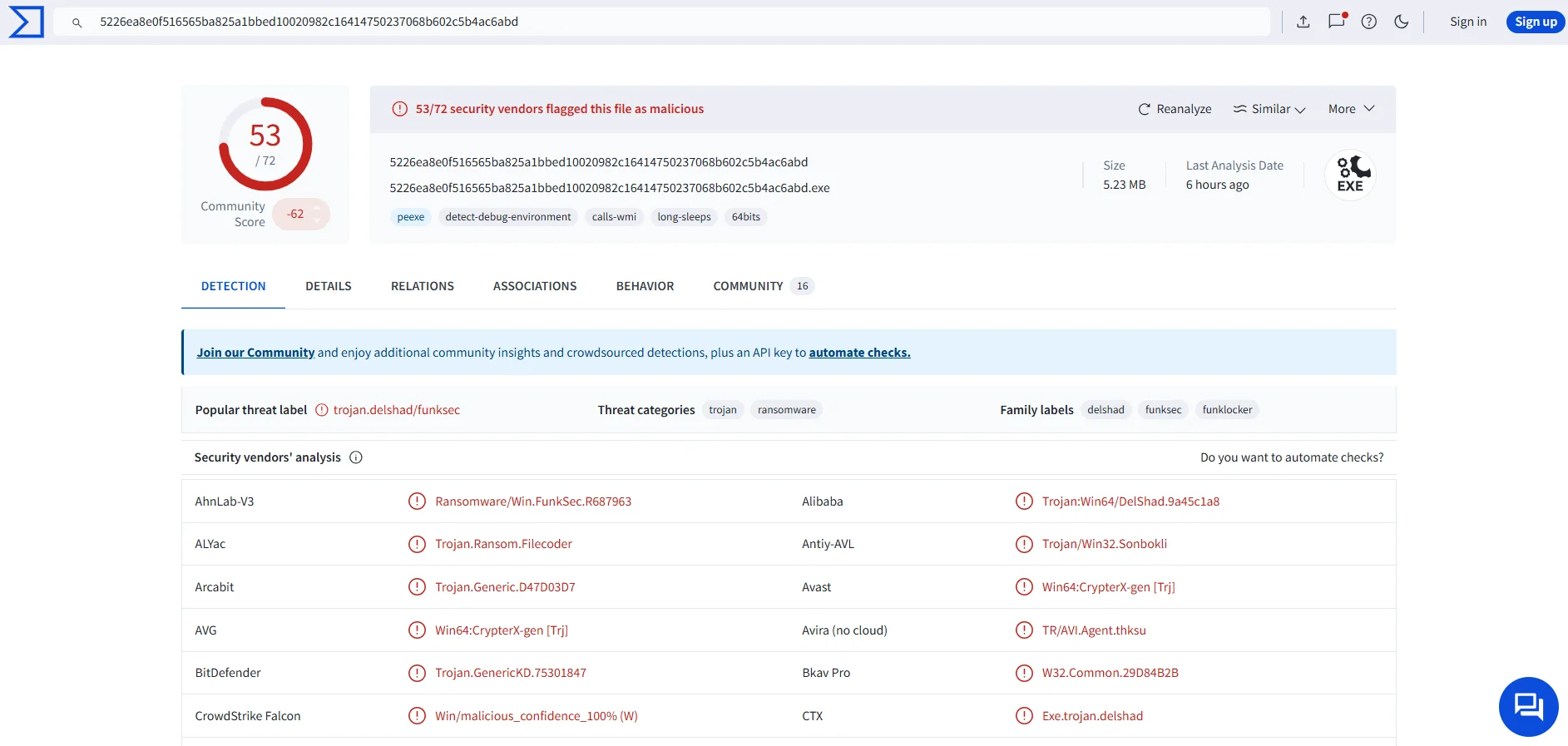
Uploaded sample to VirusTotal, Hash value: 5226ea8e0f516565ba825a1bbed10020982c16414750237068b602c5b4ac6abd
According to CheckPoint researchers, the ransomware itself, compiled in Rust, encrypts files using both RSA and AES encryption, leaving victims with the encrypted files in a new format (.funksec) while deleting the originals. The malware also leaves behind a ransom note with instructions for payment, further signaling the group’s extortion motives. Additionally, FunkSec’s operational code includes steps to check for administrative privileges before executing its payload and modify system settings, such as changing the desktop background to black.
The group’s ransomware has undergone multiple iterations, indicating continuous development, possibly by relatively inexperienced authors. Many versions were traced to Algeria, suggesting a local origin for the attackers. This, combined with clues in the ransom notes (referencing both FunkSec and another local group, Ghost Algeria), implies the attackers’ identity and geographical ties.
Notably, FunkSec’s development process appears to be assisted by AI, which may help streamline their code creation. They have even shared parts of their source code, providing an insight into how the ransomware operates and how their use of AI might contribute to its evolution.
Hacktivist Ties and Tools
In addition to ransomware, FunkSec markets tools more commonly associated with hacktivist groups. Their offering includes FDDOS, a tool used to launch DDoS attacks, and JQRAXY_HVNC, which is designed for remote control of infected systems. FunkSec also features a password generation and scraping tool called funkgenerate, aimed at scraping emails and generating passwords from various online sources.
As revealed by researchers, FunkSec’s activities have been closely associated with several prominent personas. The most notable among them is Scorpion, who has been at the forefront of FunkSec’s public outreach. Scorpion, using aliases like DesertStorm, initially gained attention on cybercrime forums like Breached Forum, where they posted leaks and used a YouTube channel to promote FunkSec’s activities. However, Scorpion’s operational security was compromised when they inadvertently exposed their location to Algeria, leading to suspicion about their true identity.
Another prominent figure is El Farado, who rose to prominence after DesertStorm’s banning. El Farado played a pivotal role in promoting FunkSec, ensuring its visibility across multiple forums. His activity is marked by inconsistency and inexperience, evident from his basic inquiries about hacking, suggesting a lack of technical depth. His connection to Scorpion is further solidified by a shared Keybase profile registration on the same day.
XTN, a lesser-known associate, is linked to FunkSec’s operations through their involvement in the group’s “data sorting” services. XTN’s ties to FunkSec are clear through their Keybase account and Breached Forum posts, where they mention El Farado and the group’s activities.
Therefore, FunkSec’s public persona has been shaped in part by associations with defunct hacktivist groups, like Ghost Algéria and Cyb3r Fl00d, to bolster their credibility. These associations appear more like efforts to leverage the reputations of well-known groups rather than actual collaborations, designed to further their image as a politically motivated collective.
In conclusion, FunkSec presents itself as both a sophisticated cybercrime group and a politically motivated entity, targeting high-profile countries and organizations with ransomware and DDoS attacks. Their use of AI and hacktivist ties allows them to operate with both technical ambition and strategic messaging, making them a potential notable player in the current threat landscape.
AI-Assisted Capabilities
A key feature of the group’s operation is their adoption of AI-driven tools. The group has made use of AI to assist in both the development of their ransomware and in creating malicious scripts. This integration is apparent in their published materials, where the comments in their code exhibit a high degree of sophistication and fluency, likely generated by AI models. Additionally, FunkSec has used AI-driven platforms like Miniapps to create chatbots that support their operations, further enhancing their capabilities in the cybercrime domain.
However, this capability seems more like a workaround for their limitations than a true enhancement. The ransomware group demands relatively low ransom payments, sometimes as little as $10,000, and has been seen selling the supposedly stolen data to other threat actors at reduced prices. So, they not only request a significantly lower ransom —well below the market average—but also take pride in incorporating artificial intelligence into every aspect of their operations.
How To Protect Your Organization Against FunkSec and Similar Ransomware Threats?
To protect your organization from FunkSec and similar ransomware threats, it’s essential to implement a multi-layered defence strategy:
- Frequent Data Backups: Ensure all critical data is backed up regularly and stored securely, either offline or in isolated cloud storage, to minimize the impact of a ransomware attack.
- Advanced Endpoint Security: Deploy next-gen endpoint security solutions that include behavioral analysis, anti-ransomware protection, and real-time threat detection to identify and block ransomware before it can execute.
- Patch Management: Regularly update operating systems, software, and security systems to close vulnerabilities that ransomware could exploit.
- Employee Training: Conduct continuous awareness programs to educate staff on phishing tactics, suspicious email attachments, and other social engineering techniques used to deploy ransomware.
- Network Segmentation: Segment your network to limit lateral movement within your environment, preventing ransomware from spreading across all systems in the event of an infection.
- Apply the Principle of Least Privilege: Restrict user access to only essential files and systems to prevent attackers from escalating privileges or encrypting critical data.
- Monitor and Detect Suspicious Activity: Implement intrusion detection systems (IDS) and continuously monitor network traffic for unusual behavior, which may indicate ransomware infiltration.
- Multi-Factor Authentication (MFA): Enforce MFA for accessing sensitive systems to reduce the likelihood of unauthorized access or credential theft.
Combining these strategies, organizations can strengthen their defences and minimize the risk of falling victim to FunkSec and similar ransomware threats.
How Can SOCRadar Help?
SOCRadar offers comprehensive solutions to help organizations defend against FunkSec and similar ransomware threats. Here’s how SOCRadar can assist:
- Extended Threat Intelligence: SOCRadar’s real-time threat intelligence platform provides insights into emerging ransomware campaigns like FunkSec, enabling organizations to proactively identify and defend against new tactics and threats.
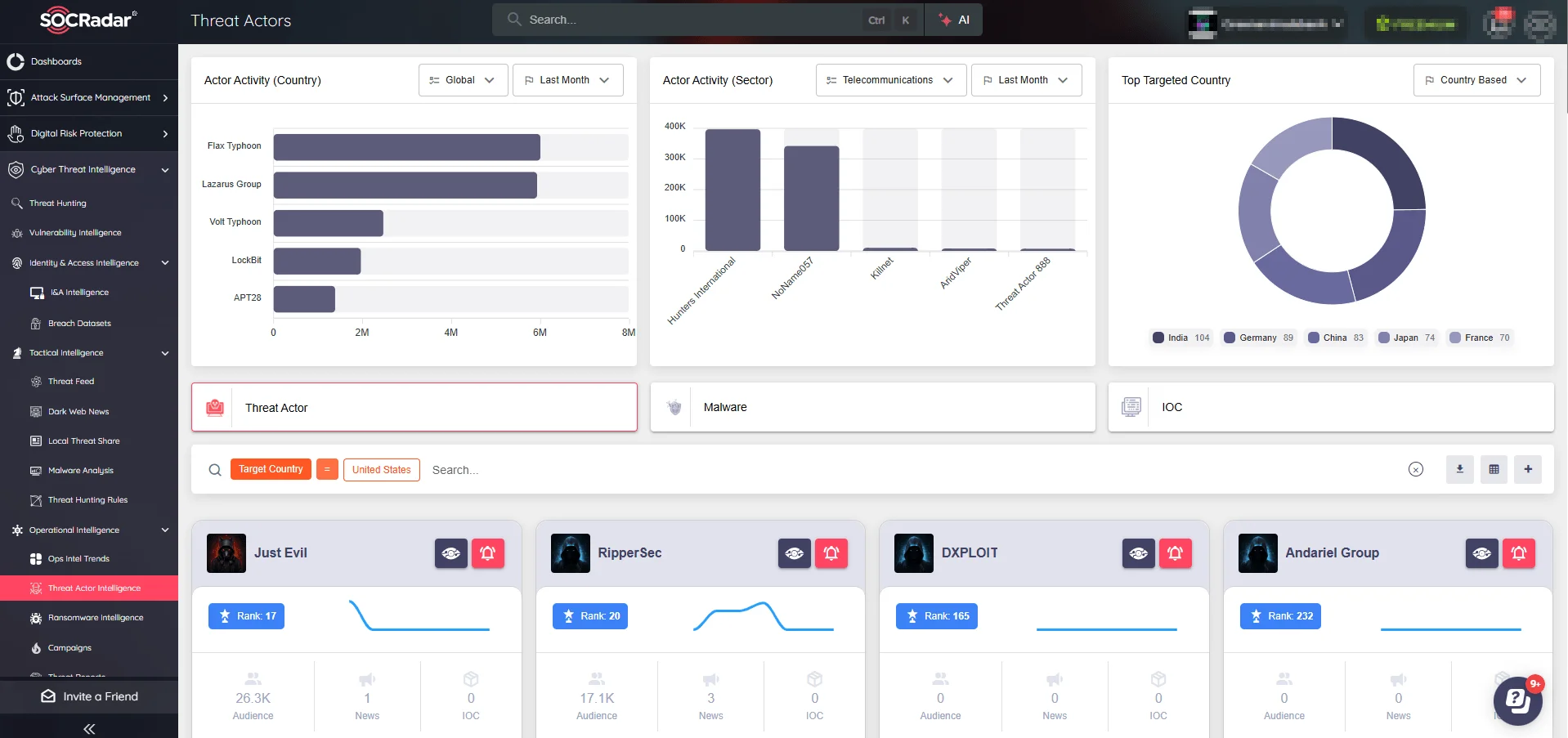
SOCRadar’s CTI Module, Operational Intelligence > Threat Actor Intelligence Tab allows you toaccess detailed profiles of FunkSec and other threat actors, including their motivation, TTPs, IoCs, target sectors, and countries, enabling proactive defense strategies.
- Dark Web Monitoring: SOCRadar continuously scans the dark web for data leaks and stolen credentials related to your organization. This early detection of compromised data can help prevent ransomware attacks by addressing vulnerabilities before they are exploited.
- Proactive Vulnerability Management: With SOCRadar’s vulnerability detection capabilities, organizations can prioritize patching and remediation of known vulnerabilities that are often targeted by ransomware groups like FunkSec.
- Incident Response Support: SOCRadar’s threat intelligence feeds offer actionable intelligence that supports incident response teams in quickly identifying ransomware attacks, understanding attacker tactics, and mitigating the impact of an incident.
- Ransomware Detection and Alerts: SOCRadar’s platform provides ransomware-specific alerts, helping organizations stay informed about evolving ransomware threats and ransomware-as-a-service (RaaS) operations, such as FunkSec.
By leveraging SOCRadar’s threat intelligence, monitoring, and incident response capabilities, organizations can strengthen their defenses and reduce the risk of falling victim to ransomware groups like FunkSec.
Update: FunkSec Expands Their Operation and Teams Up With Other Cyber Criminals
In a recent blog post, the group revealed a partnership with the FSociety ransomware group to enhance the efficiency of their attacks. While details about the alliance are scarce, their announcement describes how they will work together like wolf packs in pursuit of their targets.
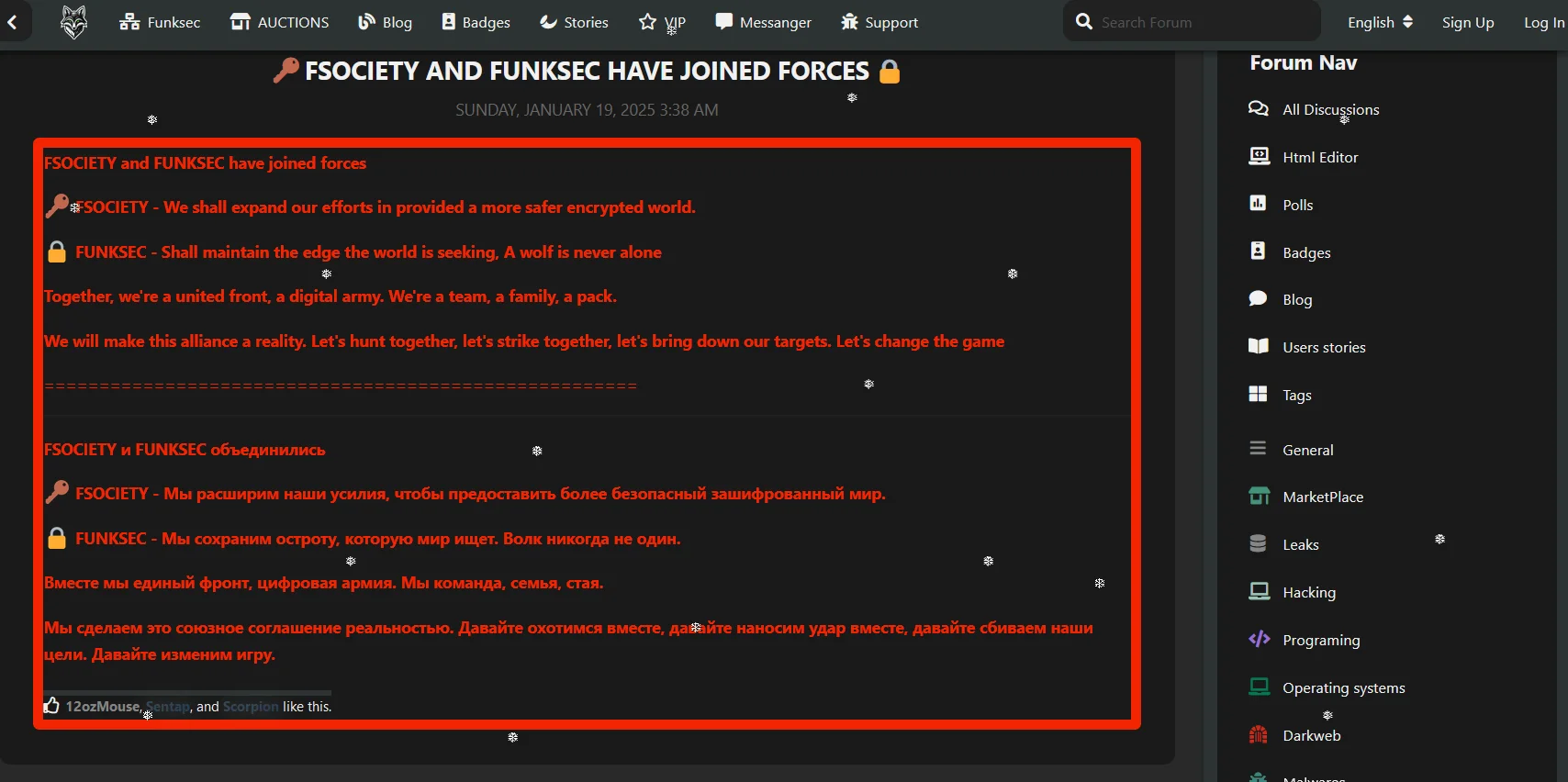
Fsociety and FunkSec have joined forces
However, the group’s activities extend beyond this alliance. In addition to announcing new victims, they have also launched version 2.0 of their ransomware strain.
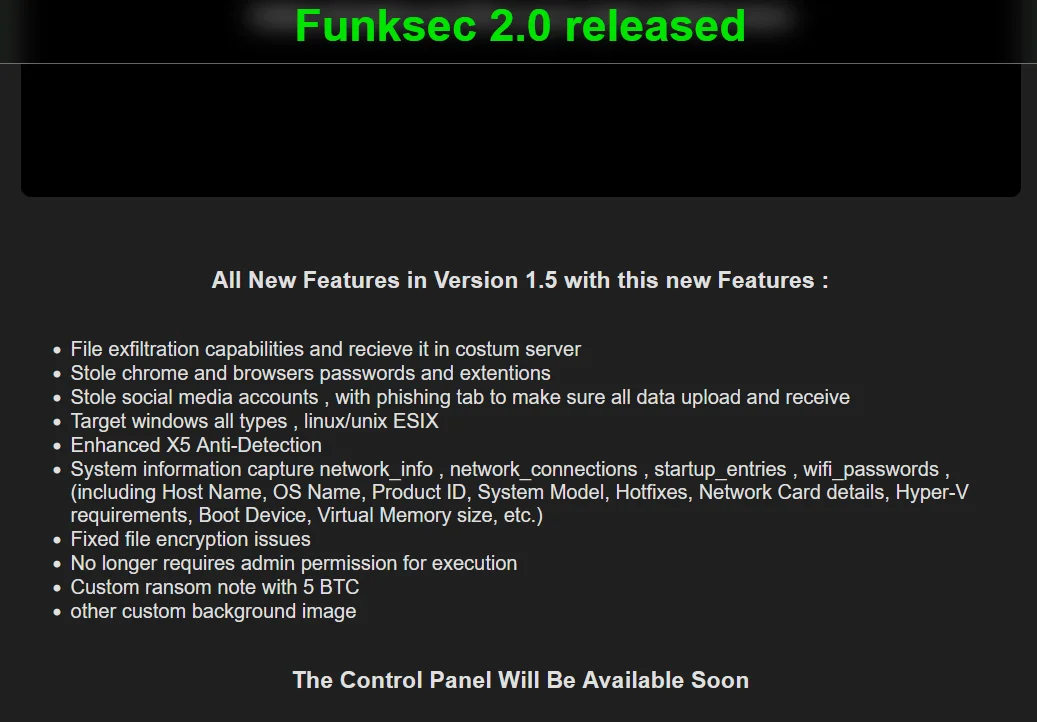
New features of FunkSec’s alleged ransomware
Finally, while we’ve previously discussed their markets, the group continues to expand this area. They’ve even taken the section once hosted on DLS and transformed it into a standalone dark web market on a separate website.
FunkSec’s DWM, FunkBID
FunkSec’s operations continue to grow as they expand their alliance with FSociety to increase attack efficiency while also evolving their ransomware strain and dark web market. These developments signal the group’s ongoing efforts to strengthen their cybercriminal network and infrastructure.
In Summary
FunkSec is a newly emerged ransomware group, active since December 2024, targeting victims across 47 countries and various industries, including technology, government, and business services. Operating under a Ransomware-as-a-Service (RaaS) model, the group uses double extortion tactics, threatening to release stolen data unless a ransom is paid.
![FunkSec’s latest announcement in their DLS:“New routes FunkSec we have new plans we unlisted most of breachs, Now we will start new attacks [ If you need any past breachs you ask in session ] Be Safe”](https://socradar.io/wp-content/uploads/2025/01/funksec-dls-announcement.png.webp)
FunkSec’s latest announcement in their DLS:
“New routes
FunkSec we have new plans we unlisted most of breachs, Now we will start new attacks
[ If you need any past breachs you ask in session ]
Be Safe”
The group combines ransomware with hacktivist tools, leveraging AI to assist in malware development. Despite their inexperience, FunkSec has rapidly gained visibility through their aggressive attacks and online presence and has a potential to be a bigger player in the ransomware scene.





































