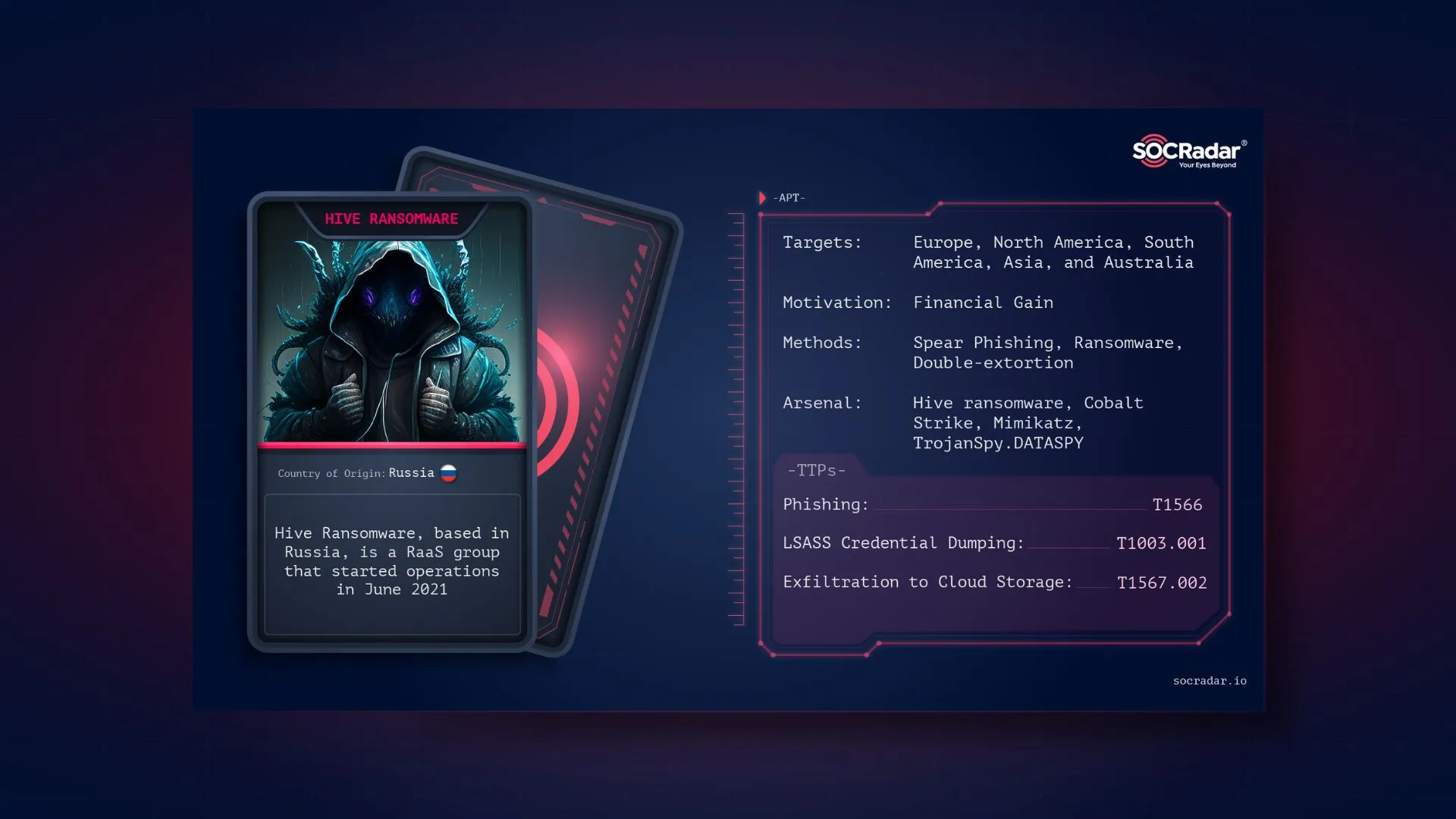
Dark Web Profile: Hive Ransomware Group
by SOCRadar Research
[Update] November 14, 2023: See the subheading: “New Era of Hive Ransomware Under Hunters International.”
On November 8, 2021 electronics retail giant Media Markt has suffered a ransomware attack with an initial ransom demand of $240 million, causing IT systems to shut down and store operations to be disrupted in Netherlands and Germany. It was the Hive ransomware group that carried out the attack.
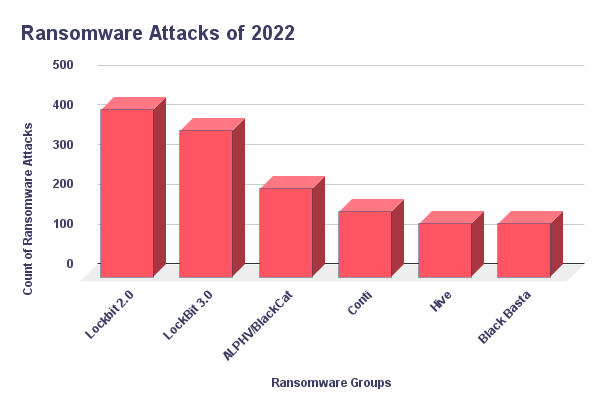
According to SOCRadar Ransomware feed, Hive conducted 5.5% of all observed Ransomware attacks in 2022. This put Hive Ransomware among the top 5 most active Ransomware for the year.
Who is ‘Hive’?
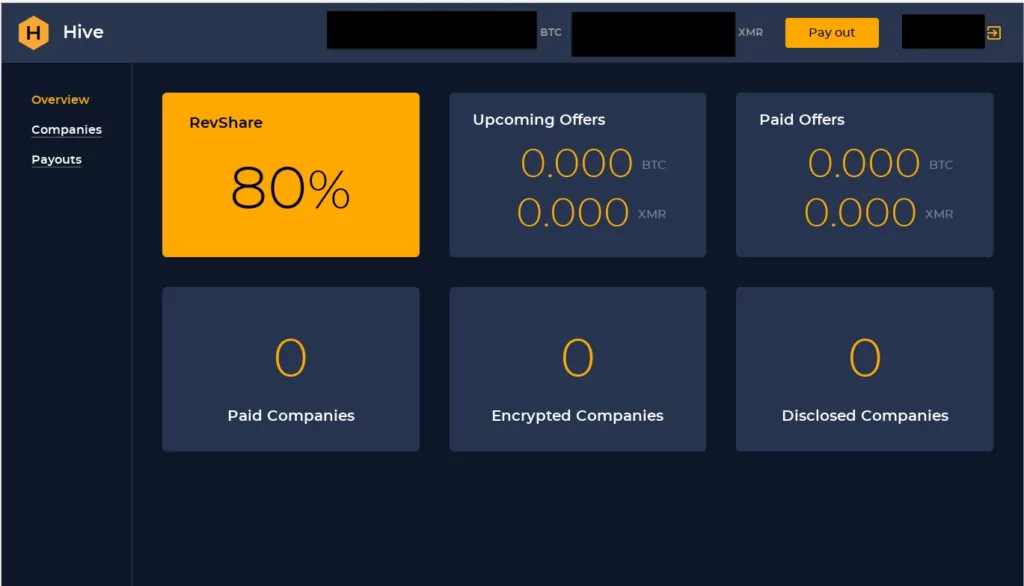
With a statement from FBI officials on August 25, 2021 it was said that a newly formed ransomware group Hive ransomware group is attacking the health system in the USA. The Hive ransomware gang crashed the IT systems at Memorial Health System, disrupting healthcare and putting the lives of several patients at risk. First observed in June 2021, Hive Ransomware is a RaaS (Ransomware as a Service) group leveraging double-extortion that started operations. The group also exfiltrates sensitive data before encrypting it for ransom. They operate with an affiliate system and provide an admin panel for affiliates to manage attacks.
They are believed to be a Russian-based organization. It is reported that around May 2022, some of its affiliates migrated to Hive as the Conti group took down its attack infrastructure. The belief stems from the fact that Conti and Hive have leaked the same victims on both their leak sites simultaneously on multiple occasions, such as the attack on Costa Rican government infrastructures. However, Hive refuted the connection with Conti in their TOR leak site in numerous instances.
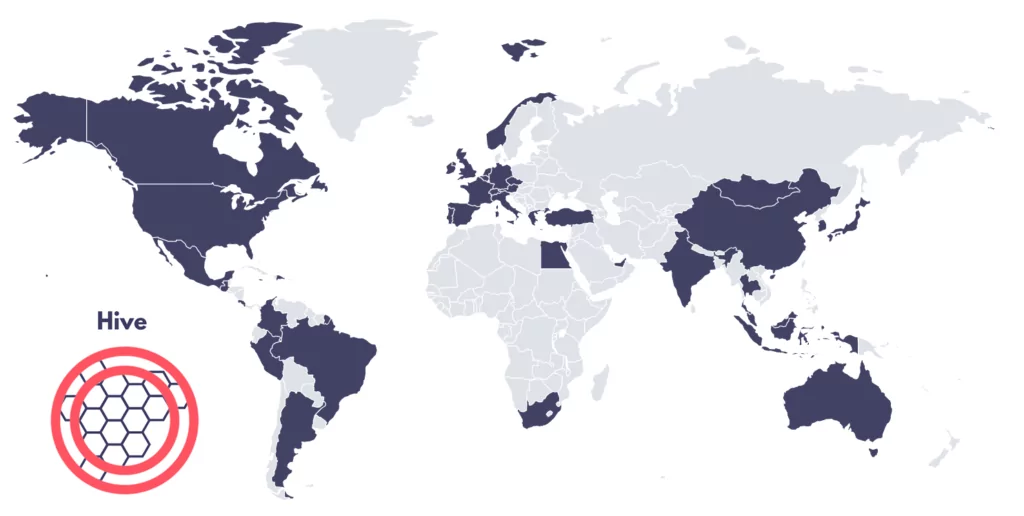
Hive Ransomware targets vary greatly, ranging from the far west, the USA, to the far east, Japan. Since their emergence, institutes from more than 20 countries have faced Hive Ransomware attacks, according to the Hive TOR leak site.
How Does the Hive Group Work?
The FBI noted that the Hive gang used multiple tactics, techniques, and procedures (TTP) to compromise targeted networks. According to the report, the ransom group leverage phishing in their attacks for initial access. This is in trend with most cyber attacks. According to Verizon, 82% of all breaches involve the human element. The group is known to exploit various phishing traps with malicious attachments to access critical systems and use Remote Desktop Protocol (RDP) to move horizontally across the network.
The Korea Internet & Security Agency (KISA) has released a public decryptor for the victims of Hive Ransomware. The tool can only be used for versions 1 to 4. However, Hive moved on to new technologies to target new victims. Early versions of the Hive variants were developed in GoLang. Possibly, with the release of the public decryptor around mid-2022, they turned to Rust language, specifically with version 5, to develop new variants for their Ransomware.
After encrypting critical files, Hive ransomware distributes two malicious scripts (hive.bat and shadow.bat) to perform cleanup after encryption. The group then threatens to leak the information it obtains on the dark websites HiveLeaks.
“After compromising a victim network, Hive ransomware actors leak data and encrypt files on the network. The actors leave a ransom note on each affected directory on the victim’s system, which provides instructions on how to purchase the decryption software,” the FBI said in a statement.
According to an analysis of the Hive group, they use spear-phishing emails with attachments to gain a foothold in the victim’s network. After Hive obtains the user’s network credentials, it laterally infects the network using Remote Desktop Protocol (RDP).
To avoid anti-malware, Hive terminates computer backup and restore, antivirus and antispyware, and file copying. After encrypting files and saving them with a .hive extension, Hive creates batch files hive.bat and shadow.bat, which contain commands for the computer to delete the Hive executable, disc backup copies, or snapshots, and the batch files. This is a common technique used by malware to reduce available forensic evidence.
Hive drops a ransom note, HOW_TO_DECRYPT.txt, into each affected directory. The notice explains that encrypted files are not decryptable without the master key, which is in the actors’ possession. In addition, the note contains the login details for the TOR website that the victim can use to pay the ransom, and it threatens to leak the victim’s sensitive data on the HiveLeaks TOR website.
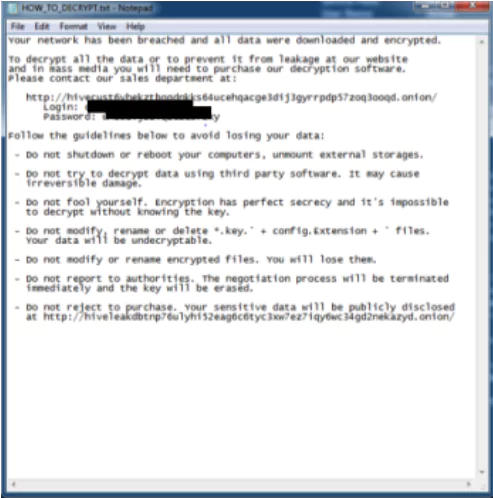
The message left by the attackers:
“Your network has been breached, and all data was encrypted. Personal data, financial reports, and important documents are ready to disclose. To decrypt all the data or prevent exfiltrated files from being disclosed at
http://hiveleakdbtnp…….onion/, you will need to purchase our decryption software.”
They are also one of the Ransomware groups that widened their foothold by developing Ransomware for Linux-based systems.
For all variants of Hive Ransomware, you can refer to this GitHub repo.
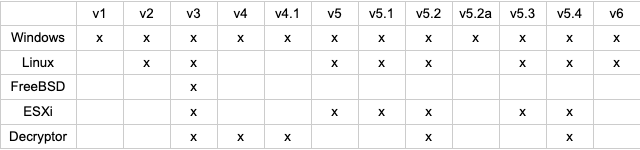
Hive Ransomware Rust Variant Analysis
Analyzed Sample: SHA-256: f4a39820dbff47fa1b68f83f575bc98ed33858b02341c5c0464a49be4e6c76d3
As SOCRadar Research Team, we analyzed the v5 of the Rust variant of Hive Ransomware. It uses string encryption, making it more evasive. Strings reside in the .rdata section and are decrypted during runtime by XORing with constants. The constants used to decrypt the same string sometimes differ across samples, making them an unreliable basis for detection.
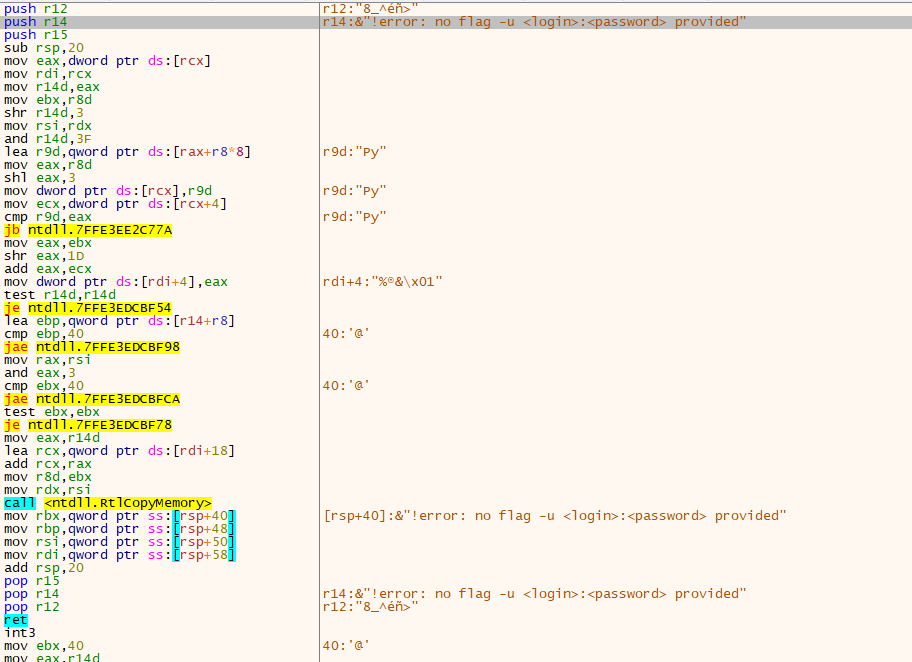
The credentials are provided on the command line under the “-u” parameter, which means it cannot be obtained by analysts from the sample itself. An attacker can choose to encrypt files on remote shares or local files only or choose a minimum file size for encryption.
In the Rust variant of Hive Ransomware, attackers need to know the parameters beforehand. With this development, finding parameters for the researcher and analyst teams in encrypted strings is difficult. Another typical result we observed while monitoring the processing activity is using “vssadmin.exe” to clean the backup with “delete shadows /all /quiet” parameters.
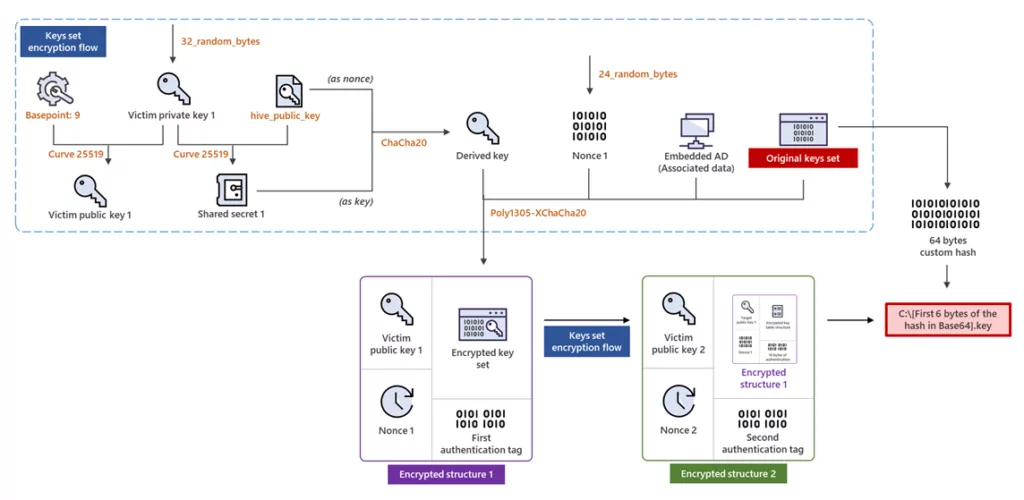
In another finding during the analysis, it is observed that different algorithms are used in the Rust variant: Elliptic Curve Diffie-Hellmann (ECDH) with Curve25519 and XChaCha20-Poly1305 (authenticated encryption method with ChaCha20 symmetric cipher)
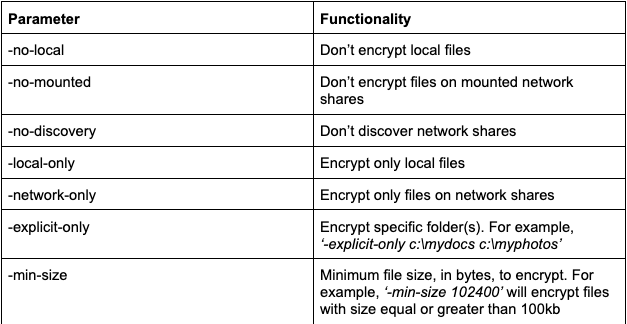
The following file extensions are excluded from encryption by the Rust variant.
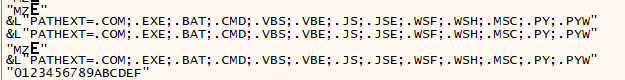
When we analyze the function call made at the “00000000004613AF” address, inside it, we found that the NtTerminateProcess API call was made at the address “000000000047867B“. It is possible to bypass anti-analysis at these addresses by changing the RIP. Otherwise, process termination occurs, and the analysis stops.
The following file extensions are excluded from encryption by the Rust variant.
When we analyze the function call made at the “00000000004613AF” address, inside it, we found that the NtTerminateProcess API call was made at the address “000000000047867B“. It is possible to bypass anti-analysis at these addresses by changing the RIP. Otherwise, process termination occurs, and the analysis stops.
The following file extensions are excluded from encryption by the Rust variant.
Hive Group’s Previous Attacks
Their attack on the healthcare system was not the first act of the Hive Group. On June 14, 2021 Altus Group, a commercial real estate software solutions company, announced that its data was breached. The day before the announcement, the Altus group was affected by a cybersecurity breach. Communication systems such as the IT back office and email were taken offline at the time. Throughout subsequent updates, the company has yet to reveal whether any information has been leaked.
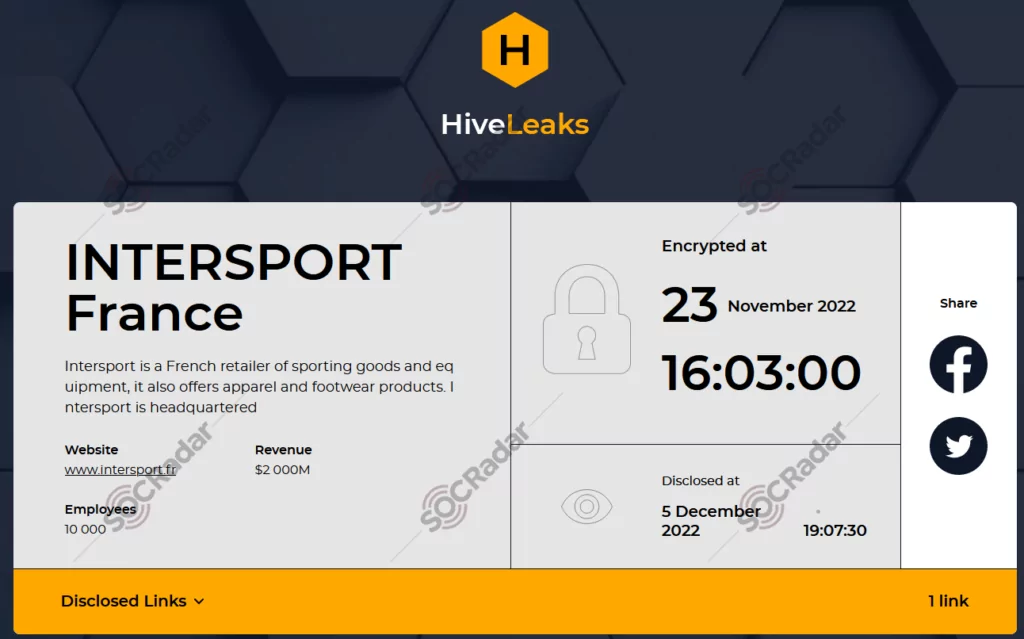
On 5 December 2022, Hive Ransomware listed a ransom countdown regarding the French sports retailer Intersport. The group posted a portion of Intersport data, allegedly including passport details of Intersport staff, pay slips, a list of former and current employees, and their Social Security numbers, on its TOR leak site. Apparently, the attack occurred during Black Friday sales and affected the operations.
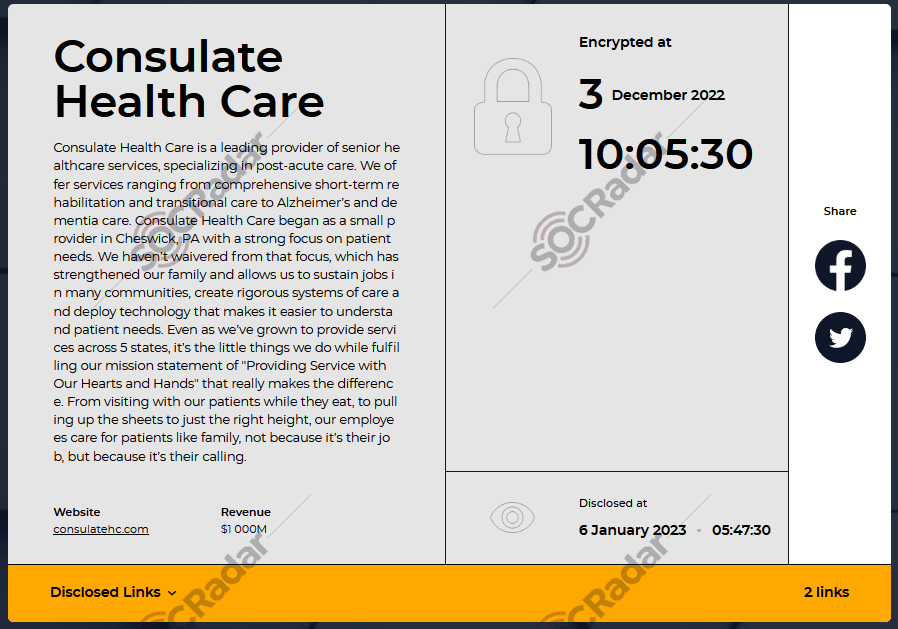
On January 6, 2023, Hive Ransomware listed a ransom countdown regarding Consulate Health Care on its TOR leak site. With the breach becoming public news, the Consulate of Health Care confirmed the attack with an announcement. It was due to a third-party vendor facing a breach in their network. According to the institute, the ransom was far more than they could pay. Because of this, Hive released 550GB of Health Care customer and employee PII data before the deadline.
Finally, US and international law enforcement authorities have taken action against the Hive ransomware group, including the seizure of at least two leak sites.
On January 26, 2023 morning, two of the group’s sites on the dark web used for extorting victims and leaking data for non-paying businesses were replaced with a notice indicating in both English and Russian that the site had been seized in international law enforcement operation involving the U.S. Department of Justice, the FBI, Secret Service, Europol, and other European countries.

Which Countries and Industries are Hive’s Targets?
Hive has a TOR leak site to share countdowns for their victims. On this site, they only share victims who did not oblige and pay the ransom they demanded. As a side note, in research conducted at the end of 2021, it was observed that Hive targets, on average, three organizations in a day. The research also found that Hive compromised 355 organizations, and only 55 victims shared in their TOR leak site. Considering this not-so-recent data, we will examine Hive’s targets according to the data they shared on their leak site to avoid speculating on any unconfirmed information.
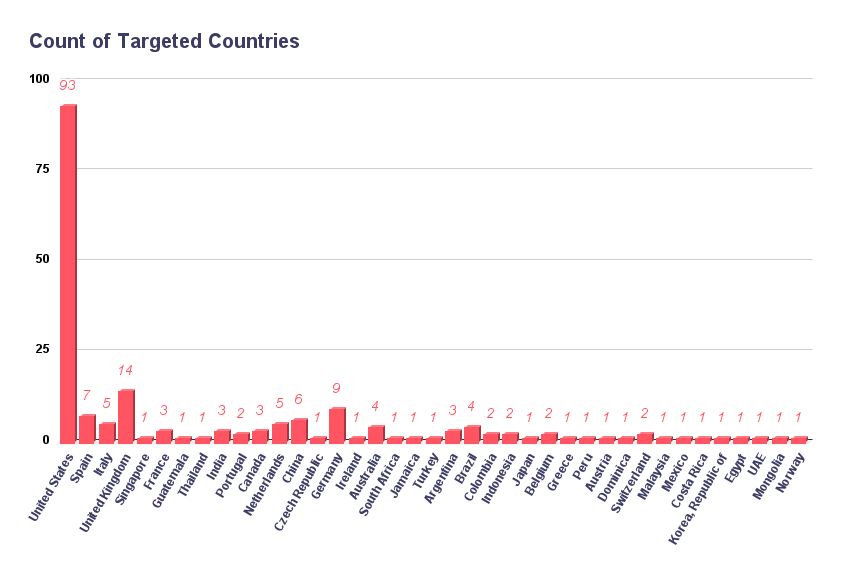
In the observed attacks of the Hive Ransomware from its TOR leak site, nearly 30 countries are affected. The USA is a top target when we look closely at the targeted countries. With 93 attacks, the USA comprises almost half of all the attacks conducted by Hive Ransomware.
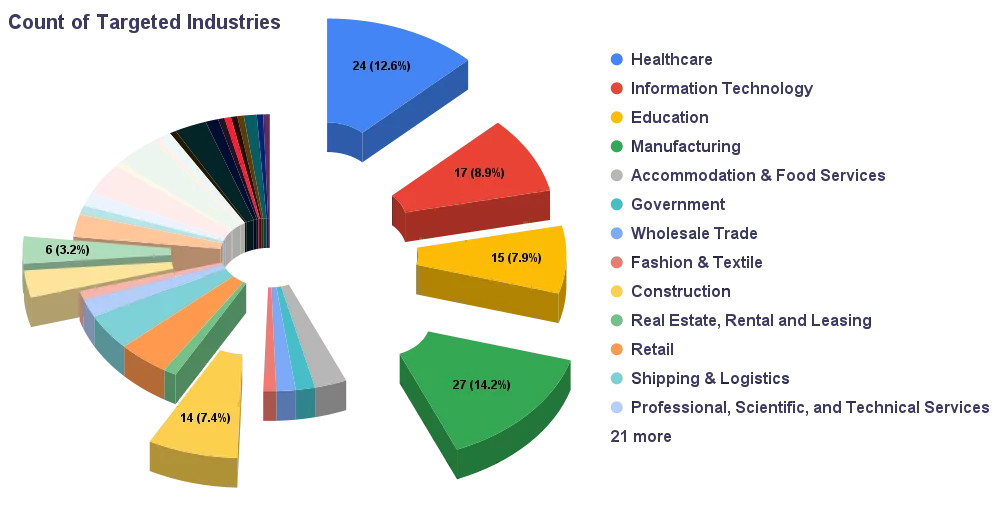
When we look at the statistics for the industries regarding the Hive Ransomware attacks, four industries are more focused than the others. There are over 30 industries observed to be targeted by Hive Ransomware, but Healthcare, Information Technology, Education, and Manufacturing are the top most targeted industries.

Some ransomware groups operating as RaaS claim to refrain from targeting institutes, such as healthcare, to avoid causing harm to people. Such as in the case of LockBit apologizing for its latest attack on a healthcare institute and cutting ties with the responsible affiliate. However, Hive’s attacks against healthcare providers show that the operators behind it have no moral incentive to avoid attacking such organizations.
Hive Ransomware is active, with nearly 200 attacks revealed in their TOR leak site in less than two years. It is likely the result of Hive operating in a RaaS model. They are active, which makes them dangerous, but they are still in the development stages. As the KISA released a public decryptor, which can be considered a massive blow for Hive, there were also contemptuous posts on the dark web regarding Hive Ransomware around mid-2022. In one example, the post was targeting Hive Ransomware’s negligent operation.
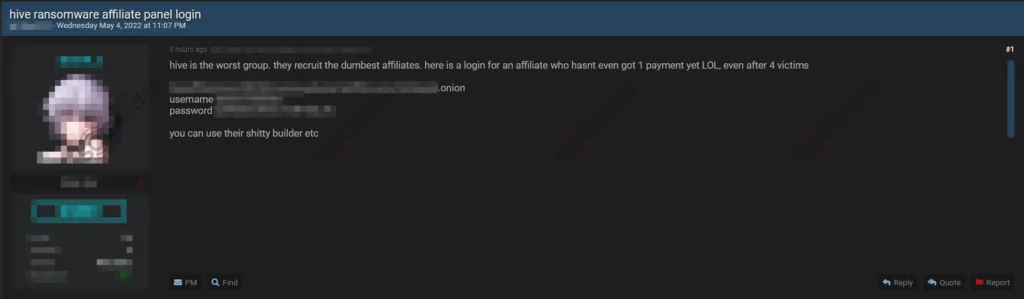
Even though it seems they are still not the most advanced group out there, they are rapidly growing as a threat to organizations worldwide. This can be deduced from the fact that they transitioned from GoLang to Rust quickly after receiving a blow. They already have numerous variants for different systems across the board to negate the released decryptors. Also, in the technical analysis, we found that they are trying to cripple the analysis process for the researchers using evasion techniques.
As a last point, it is clear that Hive does not have any bearing when deciding whom to target. Whether it is a big manufacturing organization or a small healthcare institute, they attack regardless of any parameters. Considering how Hive Ransomware operates, organizations of all sizes should be aware of Hive Ransomware’s existence and take proactive measures accordingly.
New Era of Hive Ransomware Under Hunters International
The Hive ransomware group may have passed its mantle to a new entity, Hunters International. This development follows the FBI’s successful disruption of Hive’s operations months later.
Of course, it’s not exactly the Hive, but the code base is quite similar. Hunters International, emerging with Hive’s sophisticated malware arsenal, marks a fresh threat in the ransomware scene. Unlike Hive’s encryption-centric approach, this group focuses on data exfiltration for extortion, indicating a strategic pivot in their modus operandi. Their attacks, spanning multiple countries, including the US and UK, suggest an opportunistic rather than a targeted strategy.
This transition, analyzed by Bitdefender, reveals the use of logging in the malware, a sign of inheriting and adapting Hive’s code. It reflects the challenges criminal groups face in rebuilding after law enforcement crackdowns, often leading to the sale of their tools as a risk-reduction strategy.
How SOCRadar Can Help?
- As in the case of most Ransomware attacks, Hive also leverages phishing for initial access in their attacks. SOCRadar provides brand protection with its Digital Risk Protection module. With brand protection, you can proactively deny potential phishing campaigns that may arise from impersonating domains.
- Hive affiliates target organizations with malicious documents inside of spam emails. Beware when you receive an email containing documents. Do not open attachments without making sure it is safe.
- Hive also leverages stolen credentials to gain initial access. Demanding the use of MFA for access may prevent the possible entry points from being breached.
- The most crucial suggestion when Ransomware is in question is to keep offline backups. Offline backups shorten the time frame of returning to a functional state and possibly save a considerable amount of organizational resources.
- Hive operates with double extortion, which means if an organization falls victim to a ransomware attack, its data is in the hands of the attackers. In this situation, even offline backup may not be enough not to pay the ransom. Organizations should be aware of any vulnerabilities in the environment to prevent this. SOCRadar provides Attack Surface Management which helps gain visibility into external-facing digital assets. With it, security teams can track the vulnerabilities in the environment. Knowing which vulnerabilities are present in the organization can limit the possible attack surface Ransomware operators may exploit.
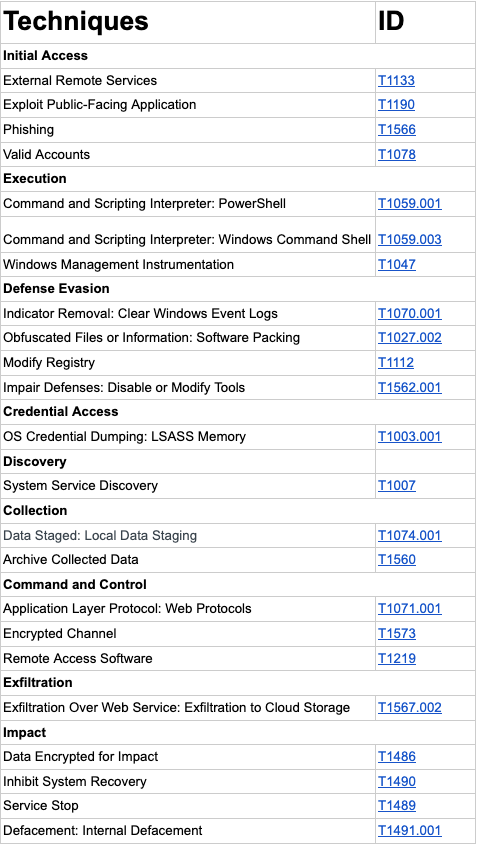
MITRE ATT&CK Techniques
Appendix 1: IOCs of Rust variant of Hive Ransomware v5
- SHA-256: f4a39820dbff47fa1b68f83f575bc98ed33858b02341c5c0464a49be4e6c76d3
- SHA-256: 88b1d8a85bf9101bc336b01b9af4345ed91d3ec761554d167fe59f73af73f037
- SHA-256: 065208b037a2691eb75a14f97bdbd9914122655d42f6249d2cca419a1e4ba6f1
- SHA-256: 33744c420884adf582c46a4b74cbd9c145f2e15a036bb1e557e89d6fd428e724
- SHA-256: afab34235b7f170150f180c7afb9e3b4e504a84559bbd03ab71e64e3b6541149
- SHA-256: 36759cab7043cd7561ac6c3968832b30c9a442eff4d536e901d4ff70aef4d32d
- SHA-256: 481dc99903aa270d286f559b17194b1a25deca8a64a5ec4f13a066637900221e
- SHA-256: 6e5d49f604730ef4c05cfe3f64a7790242e71b4ecf1dc5109d32e811acf0b053
- SHA-256: 32ff0e5d87ec16544b6ff936d6fd58023925c3bdabaf962c492f6b078cb019



































