
Dark Web Profile: KillSec
In today’s rapidly evolving cyber landscape, threat actors are continuously refining their tactics, techniques, and procedures (TTPs) to exploit vulnerabilities across various industries. This article delves into the activities of KillSec, a highly active entity known for its involvement in ransomware attacks and data breaches. Their first Telegram message appeared in October 2023, and since then, this actor has steadily increased its presence by targeting organizations across sectors.

Threat actor card of KillSec
Looking at their allegations, KillSec has been responsible for several high-profile incidents, including Ping An, a conglomerate from China, and Yassir, a super app for ride-hailing, food delivery, and grocery shopping. By understanding the actor’s motivations, TTPs, and affiliations, this article aims to provide actionable intelligence to help organizations strengthen their defense mechanisms and mitigate future threats.
Who is KillSec?
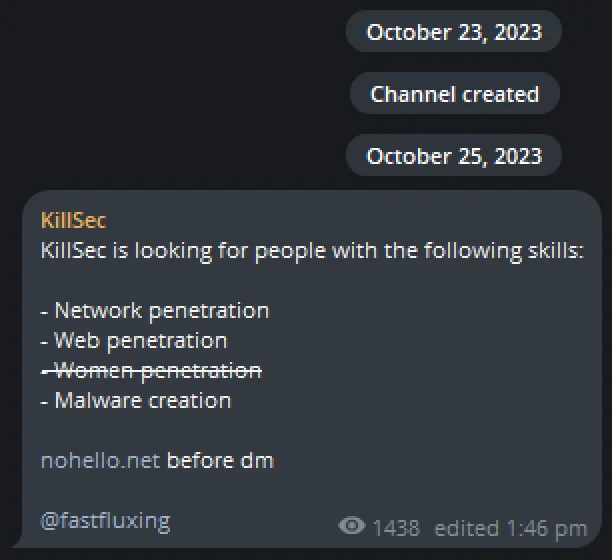
First message on the Telegram channel
According to the Telegram channel, the group’s activities appear to have begun in October 2023. In their first public message, they openly invited individuals with specific skills, including “network penetration,” “web penetration,” and “malware creation.” These areas indicate a clear focus on offensive cyber operations, with an emphasis on compromising networks and websites. Additionally, the needs stated in this message were an indication that this threat actor would go beyond hacktivism, contrary to the allegations made about it.
These predictions paid off in June 2024, approximately 1 year after the founding of the Telegram channel, when the threat actor presented the news about the new RaaS “service”.
Based on the topics, languages and ideas discussed in the threat actor’s group and the information on the threat actor’s website, it is possible to say that this threat actor emanates from the Eastern Europe-Russia region.
KillSec’s main Telegram channel has not been available since November 2024 but the threat actor is still active and sharing their alleged cyber attacks via their back-up Telegram channel and website.
What are KillSec’s Services and Criminal Offerings?
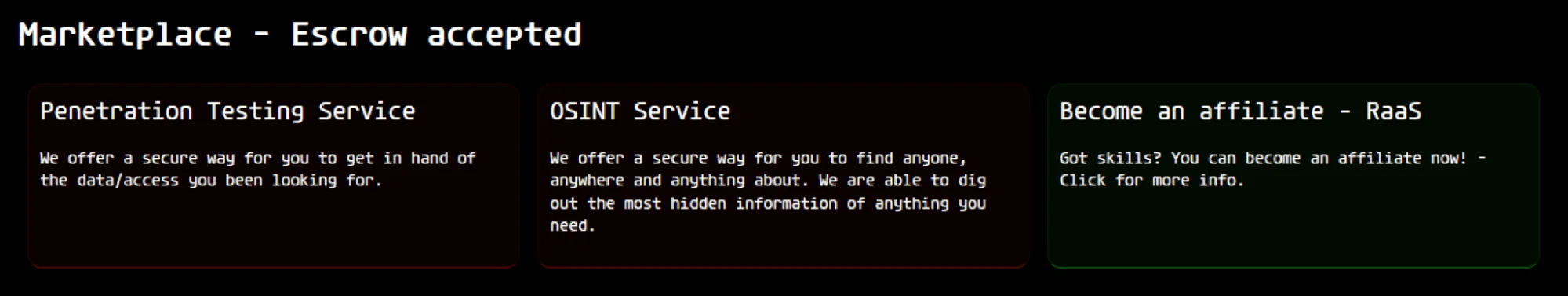
Services offered by KillSec
According to their website, KillSec operates across three distinct domains:
Penetration Testing Service
They market their “penetration testing” as a means of gaining unauthorized access to systems or data. Unlike legitimate penetration testing, which is aimed at identifying and remedying security vulnerabilities for organizations, KillSec’s service is promoted as a method for clients to achieve illegal entry into specific networks or steal sensitive information. This service underscores the group’s willingness to exploit security weaknesses for criminal gain, and their advertisement of “secure methods” suggests they may offer tools or techniques designed to minimize detection by defensive mechanisms.
OSINT (Open Source Intelligence) Service
The group’s OSINT service targets individuals or organizations seeking to uncover detailed and often private information. While OSINT itself is a legitimate practice used in both cybersecurity and investigative fields, KillSec repurposes it for malicious intent. This service may attract clients interested in doxxing, corporate espionage, or targeted attacks, making it a significant threat to privacy and security.
Ransomware-as-a-Service (RaaS) – Affiliate Program
KillSec also promotes a Ransomware-as-a-Service (RaaS) affiliate program, offering a platform for cybercriminals to deploy ransomware attacks in exchange for a share of the proceeds from successful extortion campaigns. Although the posts published by the threat actor group often show extortion rather than utilizing ransomware, the threat actor group also published a message promoting its RaaS initiative. This RaaS model will allow less technically skilled individuals to carry out ransomware attacks, expanding their reach by leveraging affiliates to distribute malware.
What is KillSec’s Affiliate Program?
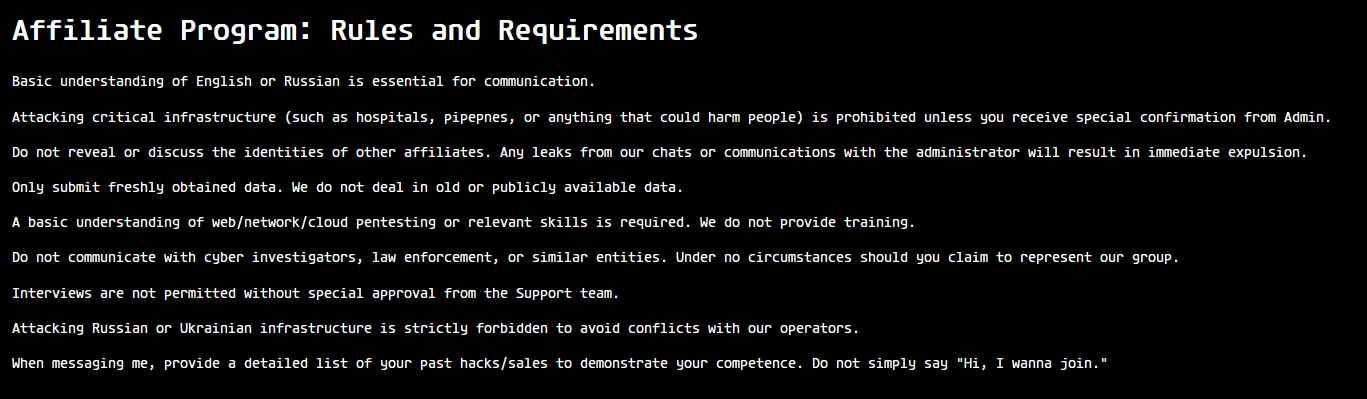
Rules and requirements for the affiliate program of KillSec
The rules and requirements for KillSec’s affiliate program, as outlined on their website, reveal important insights into the group’s operational strategy and contradictions between their stated policies and observed behavior. Two of these standout:
- Language Requirements and International Targeting
The affiliate program requires participants to have a basic understanding of English or Russian for communication purposes. While Russian is often associated with many cybercriminal groups, KillSec’s use of English on their recruitment page as well as on other sources is important. This suggests that they are not interested in forming a localized, unified group but instead aim to attract an international pool of affiliates. By engaging participants from various nationalities and language groups, the group can extend its reach and potentially gain more notoriety across different regions.
- Prohibition on Attacking Critical Infrastructure vs. Actual Behavior
Interestingly, one of the rules prohibits affiliates from attacking critical infrastructure. However, upon reviewing their activity, we saw that approximately %20 of KillSec’s operations directly targeted organizations in the healthcare industry including hospitals.
As far as we can see from their activity on Telegram and on their website, the threat actor is not directly targeting the parts responsible for providing care. However, this discrepancy highlights a potential gap between the rules they promote to affiliates and the actions they are willing to endorse or execute themselves. It is also important to note that it is not clear if these malicious actions were carried out by affiliates or KillSec itself. This divergence between their public rules and real-world actions suggests that KillSec may impose these limitations on paper for external appearances.
An alleged victim on KillSec’s website
What is KillSec’s Ransomware-as-a-Service Model?
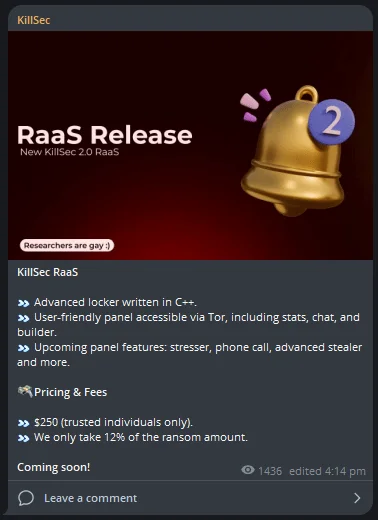
RaaS release message by KillSec
In June 2024, an “advanced locker” written in C++ was advertised, aiming to attract cybercriminals to its ransomware-as-a-service model. The threat actor highlights the user-friendly nature of their control panel, which is accessible through the Tor network. This panel includes features such as real-time stats, a chat function, and a builder tool, enabling affiliates to easily customize and deploy their own ransomware campaigns.
The intuitive nature of the panel lowers the technical barrier to entry, allowing less skilled cybercriminals to participate in ransomware operations, further broadening KillSec’s affiliate network.
In addition to their ransomware offering, the threat actor teases several upcoming features that expand their service suite. These include a stresser tool, likely intended for Distributed Denial of Service (DDoS) attacks; phone call functionality, which may be used for social engineering or harassment; and an advanced stealer, likely designed to extract sensitive information such as login credentials, financial data, or personal files from compromised systems. These forthcoming features suggest that KillSec aims to expand its operations, offering services beyond ransomware. The threat actor’s allegations don’t include any details about any type of encryption so far. Rather, we see extortion-oriented posts about the alleged victims.
KillSec sets the entry price for their RaaS program at $250 but limits participation to “trusted individuals,” indicating that they are selective about their affiliate partners. They further outline a 12% commission on any successful ransom payments, a relatively low cut compared to some other RaaS operators, which may make the program more appealing to potential affiliates. This structure might be KillSec’s commitment to scaling its operations by incentivizing affiliates with favorable profit-sharing terms.
Who Are KillSec’s Targets?
Country Analysis of KillSec’s Targets
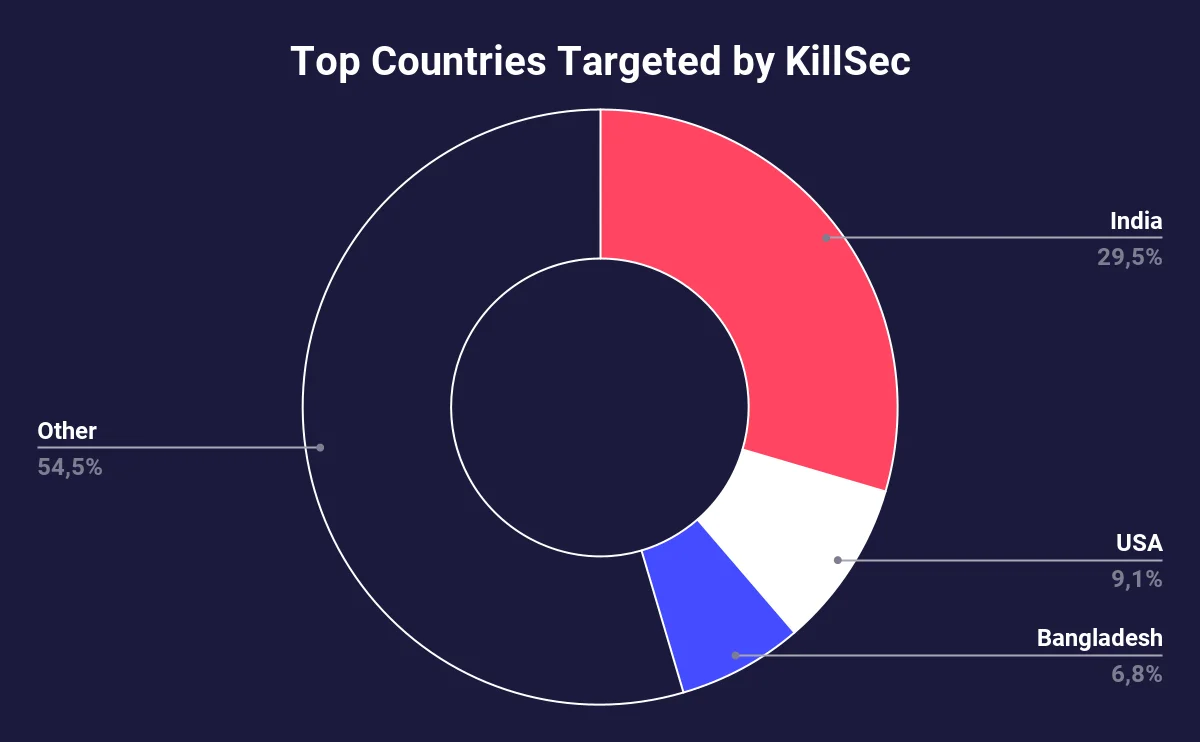
Targeted countries
KillSec exhibits a strong focus on India, with 29.55% of their alleged attacks targeting organizations from the country. This indicates a concentrated effort to exploit vulnerabilities in the region. Meanwhile, 9.09% of their activity is directed towards the USA. Bangladesh also features in their operations, with 6.82% of victims originating there.
The remaining 54.55% of attacks are distributed across various other nations, with Asian countries comprising almost half of them.
Based on the allegations of the threat actor, we can state that when it comes to target selection, KillSec differs from other Eastern European/Russian threat actors. While the allegations include Western organizations, the dominant portion of the posts are related to organizations outside of Europe or America (both North and South).
As of today, there is no specific hatred towards the targeted regions or nationalities. KillSec doesn’t share any information about the way they select their targets.
Industry Analysis of Targets
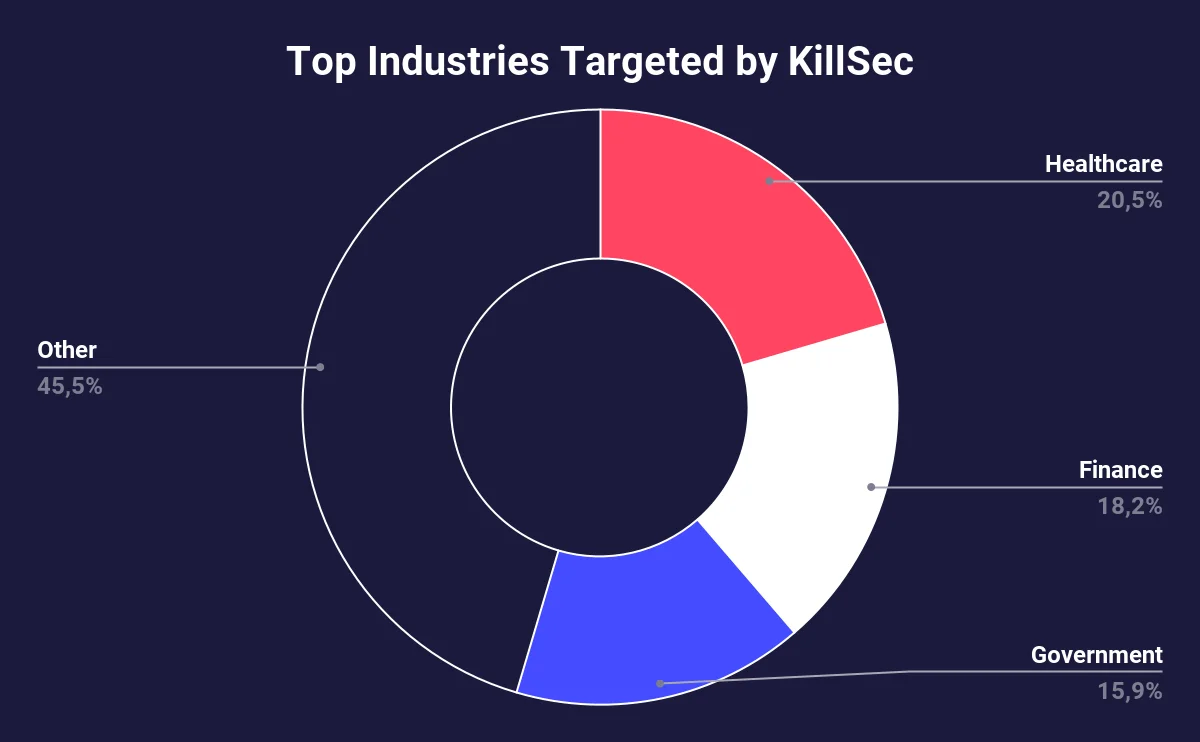
Targeted industries
KillSec has shown a distinct focus on targeting key industries, with healthcare being their primary target, comprising 20.45% of their alleged attacks. The finance sector follows closely, making up 18.2% of the victims. Additionally, government entities account for 15.91% of their activity, indicating a clear pattern of attacks on sectors that manage sensitive data and are critical to national and public interests.
KillSec’s strategy suggests a prioritization of sectors where disruption or unauthorized access could have far-reaching consequences.
Time Analysis of Messages
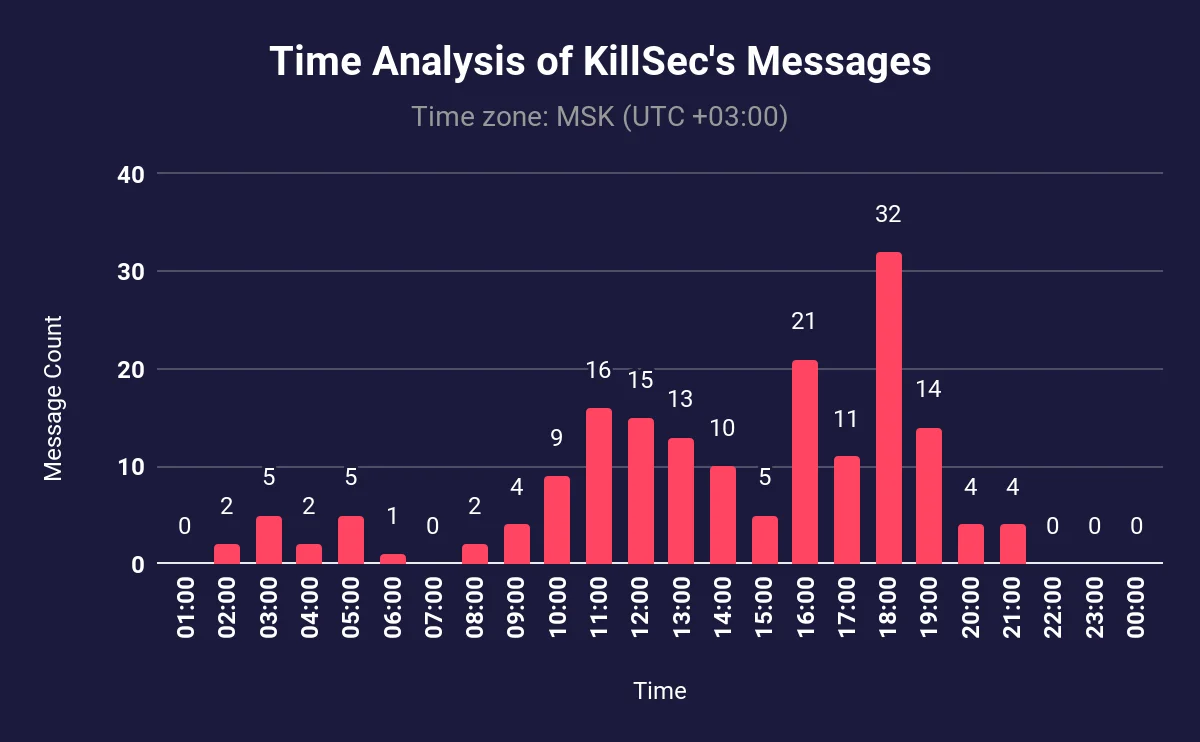
The activity hours of KillSec
KillSec exhibits a distinct pattern in their Telegram activity throughout the day. Their messaging activity intensifies notably between 10 AM and 7 PM based on Moscow time. The most significant spike is observed between 6 – 7 PM, when 32 messages were recorded.
While the most active hours for KillSec’s messaging resemble a shift image, it is not likely that this threat actor is state-affiliated. Their operations, communication style, impact, and stated motivations don’t resemble government support.
Additionally, the specified times reflect KillSec’s messaging activity, indicating that communication during these hours can be outside of their working schedule. However, based on their statements regarding paid ransoms, it is unlikely that the threat actor can sustain operations without additional employment or income sources.
SOCRadar Dark Web Monitoring
Response to breaches, confirmation of claims, and building strong cybersecurity defenses are crucial for reducing the impact of cyber threats. In today’s cybersecurity environment, it’s essential to stay alert and adaptable and work together to protect critical infrastructure, national security, and personal data.
SOCRadar Dark Web Monitoring offers comprehensive monitoring across the web’s different layers—surface, deep, and dark web. SOCRadar allows organizations to detect and tackle threats effectively. With our expertise in reconnaissance and threat analysis, we provide practical insights to strengthen your proactive security efforts. Integrating automated cyber intelligence with expert analysts empowers Security Operations Center (SOC) teams to handle threats proactively, extending their defense capabilities.
Conclusion
In conclusion, the KillSec threat actor group, believed to originate from the Eastern Europe-Russia region, operates within a structured framework that includes various services. The requirement for affiliates to communicate in English or Russian indicates a targeted approach to recruitment, while the group’s internal policy against attacking critical infrastructure raises questions about their operational ethics.
However, a concerning aspect of KillSec’s activities is the reported targeting of approximately 20% of their operations in the healthcare sector, which poses significant risks to organizations that play a critical role in public safety. Furthermore, the absence of information regarding encryption in their messages suggests a focus on direct intimidation rather than sophisticated ransomware strategies for now.
MITRE ATT&CK TTP Table
Below are the most possible TTPs for KillSec’s activities. However, it should be remembered again that this is not an incident response and investigation study but has been prepared based on the content of the alleged activities and data.
| Acquire Access | T1650 |
| Valid Accounts | T1078 |
| Web Service | T1102 |
| Remote Services | T1021 |
| Command and Scripting Interpreter | T1059 |
| Peripheral Device Discovery | T1120 |
| File and Directory Discovery | T1083 |
| Data from Information Repositories | T1213 |
| Data from Local System | T1005 |





































