
Detecting Leaked Credentials with Identity & Access Intelligence
Stealers are malicious software engineered by threat actors to compromise systems. Comparable to burglars, these trojans covertly exfiltrate sensitive information, posing significant risks to the confidentiality of data.
Stealer logs refer to the data collected by such malicious software. These logs contain the information stolen by the stealer, organized in a way that allows the attacker to extract and utilize it for various malicious purposes, such as data or identity theft, initial access to the systems, fraud, and many others. The threat actors behind those stealers can also sell the logs on hacker forums or Telegram channels.
SOCRadar has been following and collecting data from these stealers and their logs for years. With our deep knowledge of this domain, we thought it was time to reveal an important intelligence tool that will shape the future of the Identity Intelligence branch of the CTI world. To learn more about how Stealers work, you can check our article here.
We will start with the history of Identity and Access tools and then introduce our new intelligence tool that will help you protect your organization.
Identity and Access Management
As organizations continue to expand, their digital footprints grow with them. Due to this increase, the complexity of managing user identities and access rights is turning into a hassle. This is where Identity and Access Management (IAM) tools come into play. These tools ensure that the right individuals have the right access to the right resources at the right times.
Identity is the information about an individual or entity, allowing recognition and authentication within a system. This includes components such as a username or user ID, personal attributes like name, email, and phone number, as well as credentials such as passwords, biometrics, or security tokens, which are utilized for authentication purposes.
On the other hand, access is about the permissions or privileges given to an individual or entity for executing actions within a system or accessing resources. These permissions allow the user to read, write, or execute certain files and access the information they need. These roles are given to each user according to their responsibilities and their roles within an organization.
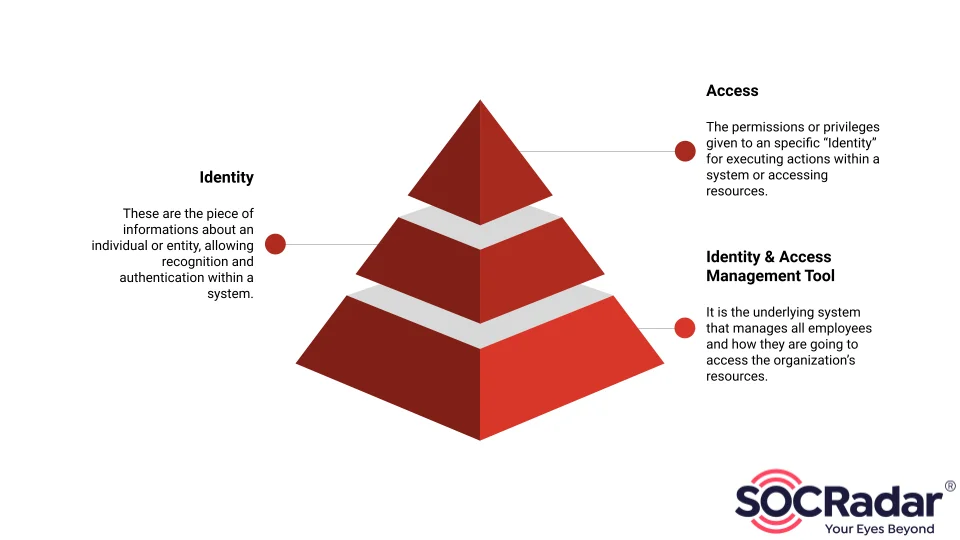
A diagram about the Identity & Access
In an organization where hundreds of people work, it is a challenge to control all the employees’ identity information and access rights. Identity and Access Management systems are utilizing policies and technologies to ensure that the right individuals have the appropriate access to the right resources.
What is Identity Intelligence?
Hundreds of leaks are shared daily on hacker forums and Telegram channels and a vast amount of personal information can be easily found online due to this abundance. Threat actors can access the identity information of your employees and use their passwords to log into your systems. The worst part is that your security systems might not even detect these intrusions, as they will appear as if your employees are accessing your systems from a coffee shop instead of their desks.
Identity intelligence gives you information about these leaks and allows you to take the necessary steps, such as changing the leaked credentials to prevent malicious intrusions into your systems.
What is SOCRadar’s Identity & Access Intelligence?
As we mentioned before, identity intelligence allows organizations to protect their organizations by detecting leaks and informing them about the leaked credentials so the organization can take the necessary steps and change those credentials before any intrusions happen.
However, the majority of those leaks happen due to stealers. These trojans collect a variety of information from the victims’ systems once they are infected. They can collect information such as usernames, passwords, cookies, or token information from browsers, login credentials, and so on.
If a stealer trojan is still on the machine, changing the credentials won’t be beneficial because your employee, whose credentials are leaked, will use the fresh and secure credentials on the infected machine and give them to the threat actor in plain text.
At this point, access intelligence comes into play.
This type of intelligence allows you to know about the access information of these stealer trojans and helps you get rid of them completely. After that, you can change the passwords and make sure that your employee credentials are safe. SOCRadar’s Identity & Access Intelligence Module can give you critical information about your credentials.
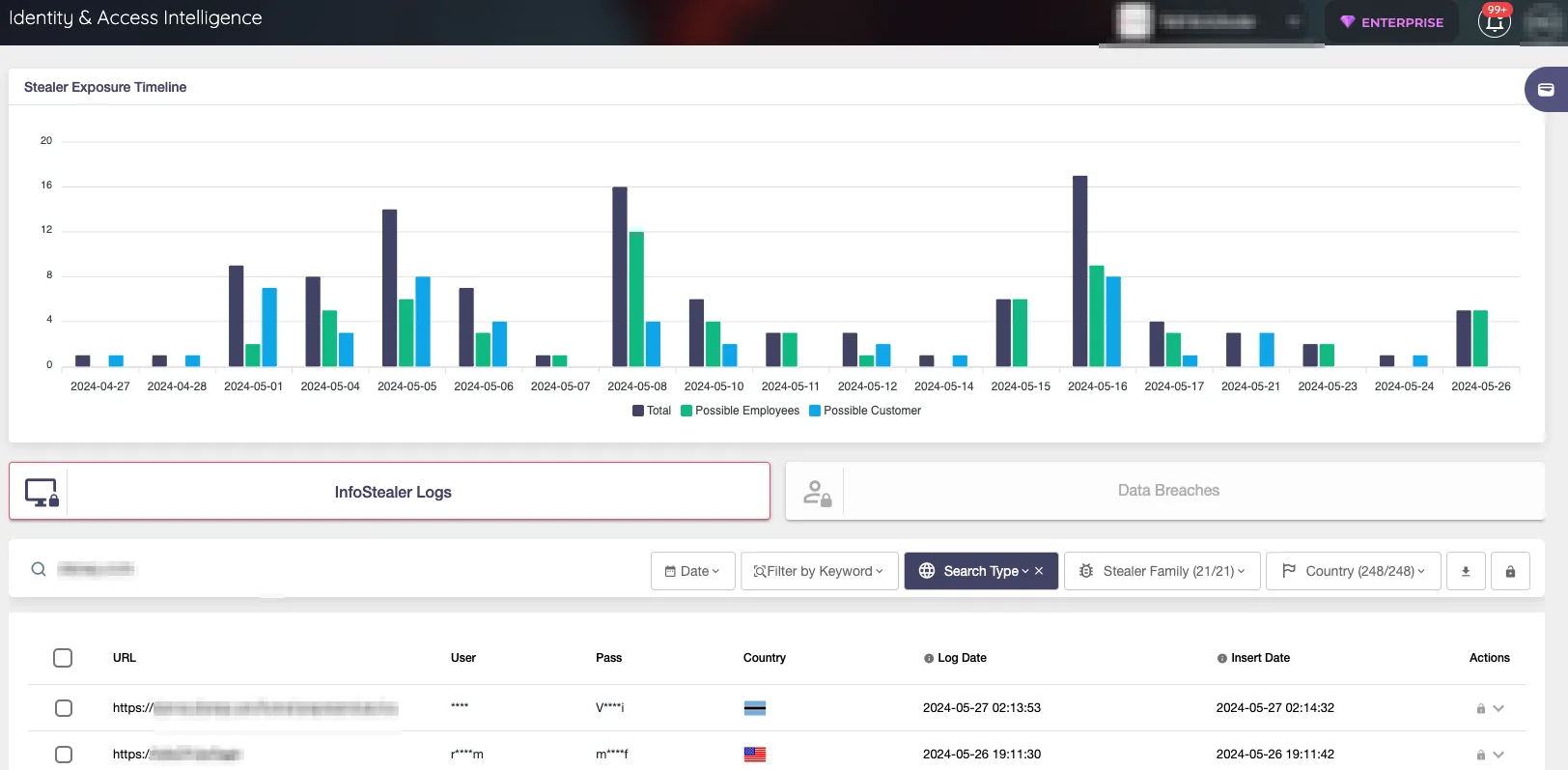
SOCRadar Identity & Access Intelligence Module
Simply changing certain credentials based on identity intelligence is not enough to eliminate a persistent threat. If the threat remains, merely looking at the intelligence and updating passwords won’t suffice. You need to completely eradicate the threat and remove its access; otherwise, you risk handing the attacker new credentials.
Use Cases of SOCRadar’s Identity & Access Intelligence
Below, you will find two short stories about how SOCRadar’s Identity & Access Intelligence module is different than regular Identity Intelligence tools.
You started using SOCRadar’s Identity & Access Intelligence module and received a notification about leaked credentials found in stealer logs. Upon checking the intelligence, you discovered that the username and password were collected by something called “Lumma Stealer” which you don’t know anything about.
After a short research, you discovered that the Lumma Stealer utilizes a user agent named as “TeslaBrowser/5.5,” which was being used to exfiltrate data via HTTP POST requests. Additionally, you found YARA rules specific to Lumma Stealer. By implementing the necessary detection rules, you protected your organization from this trojan.
Afterward, you isolated the device and reset the passwords for all accounts associated with it. Additionally, you instructed the employee using the device to immediately enable Two-Factor Authentication (2FA). Furthermore, you installed an endpoint security product on the device to enhance its protection.
Here is another story on how you can utilize SOCRadar’s Identity & Access Intelligence:
One day, while hanging out in the IT room, you saw a notification from your regular vendor’s identity intelligence module. It detected an employee’s credentials from your company. You thought, “Wow, what a useful service. Let’s inform that employee so he will change his credentials.”
Despite this, your systems were breached again one month later.
After conducting an analysis, you discovered that the breach originated from the same machine that had been compromised previously. The breach occurred due to the same employee’s credentials being exploited on that machine again. But you just changed the passwords a month ago?
You then decided to work with SOCRadar XTI for its Identity & Access Intelligence module. Utilizing SOCRadar’s expansive stealer log database, you quickly identified that your leaked credentials were logged on the same day they were compromised. SOCRadar’s Identity & Access Intelligence module not only provided you with the leaked credentials but also detailed information about the stealer and its location on the victim machine.
With this intelligence, you got rid of the stealer right away, changed the compromised credentials, and strengthened your security posture, preventing future breaches and ensuring a secure environment.
Conclusion
Threats emerge every day, and this dangerous landscape requires new solutions. Identity & Access Management tools were seen enough when they were first released. After a while, we started to see products that increased the security measures around identity. They were called Identity Intelligence tools. But now we see that those tools are not enough anymore. Changing passwords after a breach does not fix the problem. If your machines are already breached, you will be sharing your new and extra secure password with the hackers directly. We need better solutions, and that’s where SOCRadar’s Identity & Access Intelligence comes in.

A whitepaper from SOCRadar on Stealer Logs
The data we provide has been collected over many years, and our analysts are working on the data diligently to create the most impactful intelligence possible. Years of experience increased the quality of our data and now we are presenting it to our customers. For additional information about Stealer Logs, you can check our whitepaper here.


































