
Eternity Threat Group Distributing Multifunctional LilithBot Malware
LilithBot, a multipurpose malware sample, was found by ThreatLabz. Further investigation indicated that malware was connected to the Eternity group (also known as EternityTeam or Eternity Project), a threat organization related to the Russian Jester Group.
Various Eternity malware modules, such as stealer, miner, botnet, ransomware, worm+dropper, and DDoS bot, are distributed via hacker forums for subscription as malware-as-a-service (MaaS).
LilithBot’s services were spread via a Telegram channel and a Tor URL for these numerous payloads. It contained a built-in miner, stealer, and clipper in addition to its main botnet activity.
How Does it Affect?
Per the attack pattern, the threat actor adds the user to its botnet and then uses the Tor network to upload files and user data to the command-and-control (C2) server.
Registration of the LilithBot is the first step in the process. The malicious software first verifies a Mutex called “8928a2d3-173b-43cb-8837-0e2e88b6d3b1” before looking for a file in the Startup folder.
The filename is given the .exe extension and entered in the Startup path, successfully registering the bot.
It was also observed that the malware utilizes its own decrypting technique so that it cannot be manually decoded; it also uses fake Microsoft-signed certificates to avoid detection.
How Do They Distribute?
Eternity promotes LilithBot and other toolkits via their Tor page and a Telegram channel owned by “@EternityDeveloper,” both of which they keep updated. Threat actors also offer custom malware for sale and accept payments in various cryptocurrencies, including BitCoin, Ethereum, Monero (XMR), and Doge.
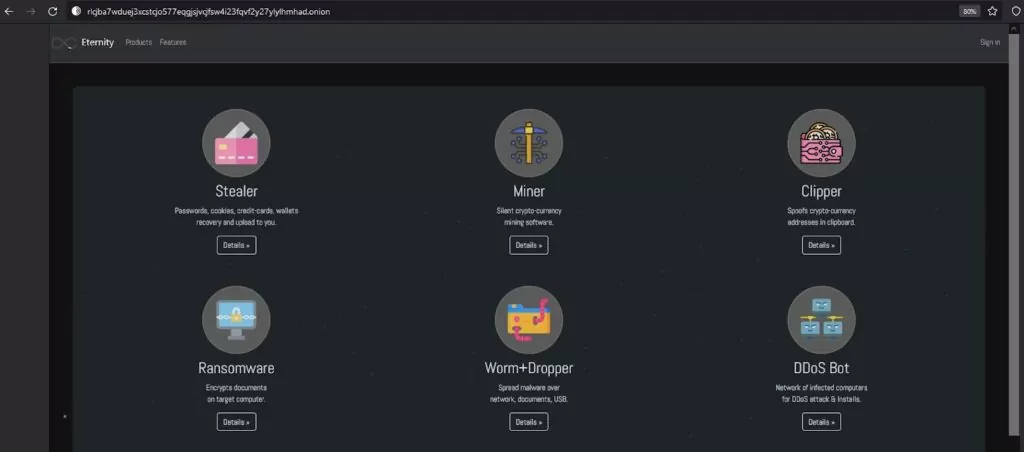
Ransomware is Eternity’s most expensive service; a video on how to create the ransomware payload is available on the Tor page.
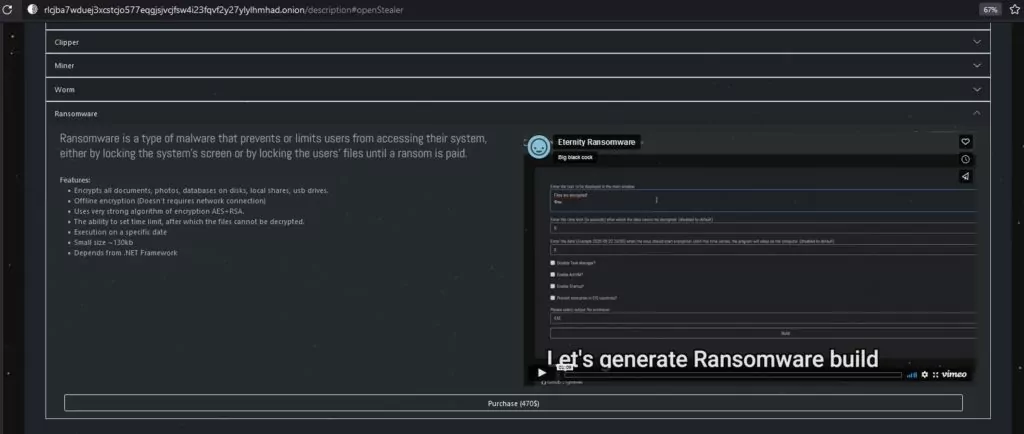
LilithBot Evolved
The primary function varies in different releases of LilithBot malware. The latest variant lacks some commands that were included in earlier variants:
- Iterating through an arraylist to check for different DLLs (related to virtual software like Sandboxie and 360 Total Security)
- Ensuring there is a physical connection rather than a virtual machine by checking for Win32_PortConnector.
These tasks are probably still carried out by Eternity, albeit in more advanced ways, like using encrypted code.
LilithBot IOCs
Executables:
- 0ebe8de305581c9eca37e53a46d033c8
- 1cae8559447370016ff20da8f717db53
- e793fcd5e44422313ec70599078adbdc
DLL:
- 65c0241109562662f4398cff77499b25
C2 Servers:
- 77.73.133.12
- 45.9.148.203
- 91.243.59.210
- 195.2.71.214
TTPs and thorough technical analysis of malware is available here.




































