Grafana Fixes Critical Auth Bypass, CISA Warns for VMware Vulnerabilities
Grafana and VMware have recently released security updates for their products in response to high severity vulnerabilities. These vulnerabilities have the potential to allow attackers to gain control over user accounts or systems.
It is crucial to apply the provided patches in a timely manner to avoid exploitation.
Critical Auth Bypass in Grafana Can Lead to Account Takeover (CVE-2023-3128)
Grafana patched a critical vulnerability in its application, which could lead to account takeover. The vendor has made the patch available for several versions of the application.
Grafana is a popular open-source analytics and data visualization app that is frequently integrated with other apps. Among the companies that use the app are Shell, Uber, eBay, PayPal, Bloomberg, and JP Morgan Chase.
The vulnerability, tracked as CVE-2023-3128 (CVSS score: 9.4, Critical), allows authentication bypass and affects Grafana accounts using Azure Active Directory (AD) for authentication.
How Does the CVE-2023-3128 Vulnerability Work?
The CVE-2023-3128 vulnerability arises from the application’s authentication process, which relies on the email address in the profile email setting. This setting, however, is not unique across all Azure AD tenants.
By exploiting CVE-2023-3128, attackers can create Azure AD accounts with the same email addresses as legitimate Grafana users, thereby gaining unauthorized access to those accounts.
Grafana’s advisory emphasizes that this authentication bypass and account takeover scenario occurs specifically when configuring Azure AD OAuth with a multi-tenant application.
Which Versions of Grafana Are Affected by CVE-2023-3128?
Grafana versions from 6.7.0 onwards are vulnerable to CVE-2023-3128; the impact of the issue extends to all Grafana deployments that utilize Azure AD OAuth with a multi-tenant Azure application and lack restrictions on user groups allowed to authenticate (allowed_groups).
It is recommended that you upgrade to the versions listed below, based on the branch you use:
- Grafana 10.0.1 or later
- Grafana 9.5.5 or later
- Grafana 9.4.13 or later
- Grafana 9.3.16 or later
- Grafana 9.2.20 or later
- Grafana 8.5.27 or later
Is There a Mitigation Available for CVE-2023-3128?
The Grafana advisory provides the following mitigation methods for users who are currently unable to update their applications:
- Register a single tenant application in Azure AD to prevent external login attempts.
- Limit sign-in attempts to a whitelist by adding an allowed_groups configuration to Azure AD.
Refer to the Grafana advisory for more information about the update.
VMware Fixes Multiple Vulnerabilities in vCenter Server
VMware has addressed multiple memory corruption vulnerabilities discovered in the virtual infrastructure management platform vCenter Server and the VMware Cloud Foundation.
The Cybersecurity and Infrastructure Security Agency (CISA) advises users and administrators to apply the necessary updates, as successful exploitation of the vulnerabilities could enable attackers to gain control of affected systems.
Vulnerability Details
VMware’s update resolves a total of five vulnerabilities, with their CVSS scores ranging from 5.9 to 8.1. The vulnerabilities exist in the products’ DCE/RPC protocol implementation. The DCE/RPC protocol, which stands for Distributed Computing Environment/Remote Procedure Calls, is used in distributed software development to enable remote procedure calls.
The high severity vulnerabilities covered in VMware’s advisory are detailed below:
CVE-2023-20892 (CVSS score: 8.1, High): vCenter Server is susceptible to a heap overflow vulnerability caused by uninitialized memory usage. An attacker with network access can exploit the issue to execute arbitrary code on the operating system.
CVE-2023-20893 (CVSS score: 8.1, High): An attacker with network access to vCenter Server can exploit this use-after-free vulnerability to execute arbitrary code on the underlying operating system.
CVE-2023-20894 (CVSS score: 8.1, High): By sending a specially crafted packet, a malicious actor with network access to vCenter Server can trigger an out-of-bounds write, leading to memory corruption.
CVE-2023-20895 (CVSS score: 8.1, High): An attacker with network access to vCenter Server can exploit this vulnerability, potentially bypassing authentication and causing memory corruption.
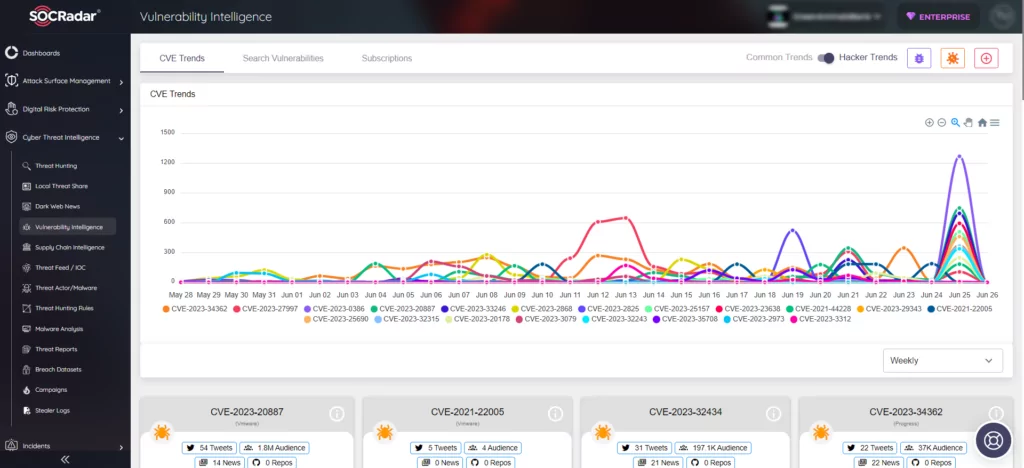
Prioritize Patches With SOCRadar
SOCRadar ensures continuous monitoring of organizations’ digital assets, delivering timely updates and alerts regarding the latest security threats and vulnerabilities. The platform presents alarms in a manner conducive to decision-making and provides actionable intelligence for resolving security issues.
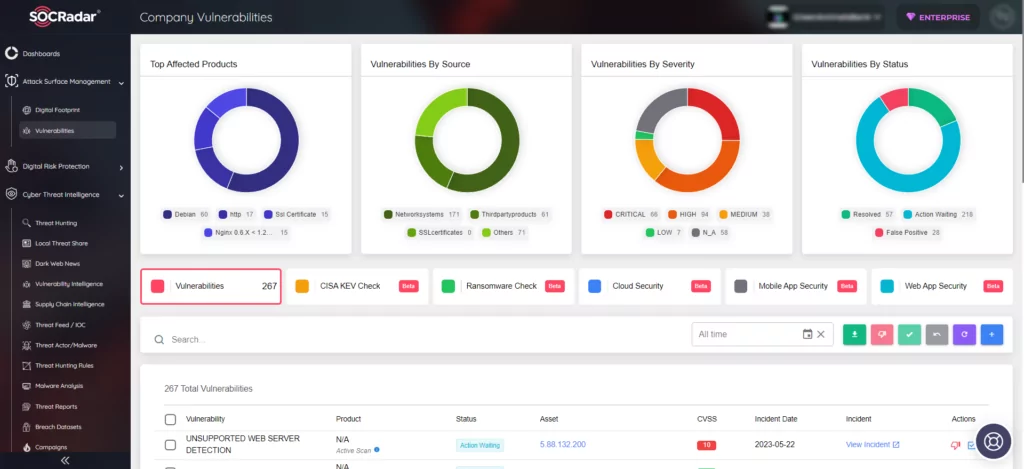
Leveraging SOCRadar’s proficient assistance in Vulnerability Management allows organizations to better prioritize the necessary patches, bolstering their defenses against potential attackers at all times.