How DNS Sinkholing Works?
What is a Domain Name System (DNS)?
The Domain Name System, or DNS, is a naming database that locates and translates internet domain names into IP addresses, similar to a phone’s contact list.
Web browsing and other internet activities depend upon DNS to quickly locate an IP address to attach and access the content. The DNS directory is distributed worldwide to account for the various domain names listed and accessed each day. Because more than one person can look for an identical website simultaneously, a domain name can correspond to more than one IP address.
For instance, if 100 people look for “greenanimalsbank.com,” they’ll receive a unique IP address from different servers. Otherwise, if a domain name only had one server and one IP address, those 100 people would all be waiting in line for their turn to access the location.
DNS can help improve web performance by saving IP addresses for a set amount of time. For instance, if everyone within the office must access the same training video on the same day, the local DNS server will only find the name once and serve future requests out of its cache.
However, DNS is at risk of vulnerabilities like cache poisoning and malicious creation of misleading domain names for phishing attacks.
What is DNS Sinkholing?
DNS Sinkholing is a mechanism that prevents users from accessing certain websites or domains by returning a false or misleading IP address. The DNS server that accepts the request is then turned into a sinkhole.
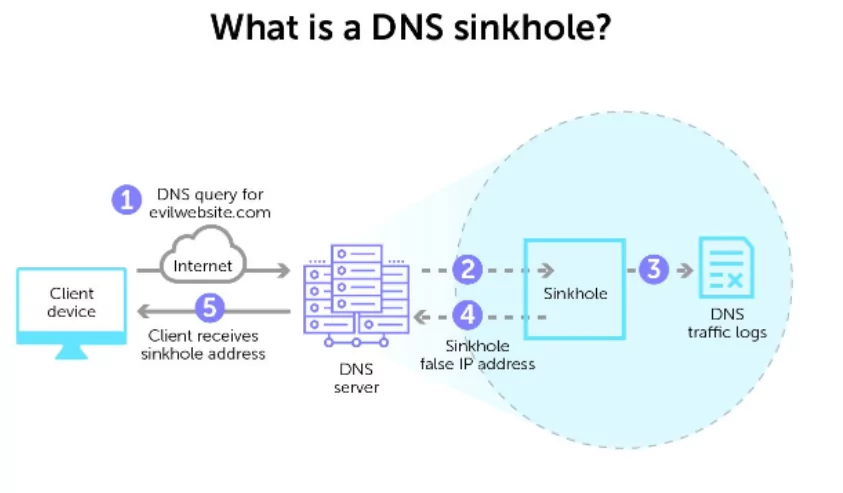
This technique prevents hosts from communicating with known malicious servers. At the level of ISPs and domain registrars, sinkholes are used to protect their clients from unauthorized domain names. There are various ways to implement this technique, such as creating a DNS sinkhole server and modifying the host file.
Sinkholing can also identify compromised hosts by analyzing the logs. For instance, if a machine is constantly trying to connect to a server, but the requests are being redirected to a malicious domain, then it’s a good chance that the device is infected with bots.
How DNS Sinkholing Works?
DNS relies on the usage of both the UDP-53 and the TCP-53 protocol. UDP is preferred for DNS queries and shorter answers.
Whereas UDP is considered the first choice for every DNS query within the shorter answering times, TCP is meant for larger data transmissions to avoid cut UDP answering packets, e.g., zone transfers between name servers (DNSs). TCP-53 is also used as a fallback strategy in case of communication problems via UDP.
DNS sinkholing depends on intercepting DNS queries through single UDP packets because the transmitted requests can easily be verified against configured entries in a very block list before the request hits a DNS. This blocklist can either be configured locally on some firewall products or may be a part of an ATP cloud block list that needs a sound ATP license.
When the client tries to access this fake IP later, another access rule blocks the traffic to the current fake IP address and sends an appropriate response to the client.
To stop circumvention by an interposed DNS on a LAN, which could eventually transform the client PC UDP-53 query into a question via a zone transfer, TCP-53 must be blocked before enabling DNS sinkholing. Also, the caches on the internal DNS must be cleaned.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.