
How Tariffs Impact Supply Chain Security and Strategies to Mitigate Risks
Recent announcements regarding new tariffs on China, Mexico, and Canada highlight a looming shift in global trade dynamics. With plans for tariffs of up to 25% on key trading partners, businesses face an urgent need to reevaluate their supply chains. These changes often lead to reshoring or nearshoring strategies, disrupting established processes and creating unforeseen risks.
Tariffs not only increase costs but also pose logistical challenges. Companies are pushed to onboard new suppliers, modify shipping routes, or relocate production facilities – decisions that can inadvertently introduce new vulnerabilities. Among these are cybersecurity threats, which become especially prevalent during transitions when systems are updated, and new third-party relationships are formed.

“How do tariffs affect supply chains?”, illustrated by DALL-E
Cyber Threat Intelligence (CTI) is a critical tool for navigating this landscape. By identifying vulnerabilities and providing actionable insights, CTI enables businesses to anticipate and mitigate the security risks tied to supplier transitions. Whether you’re reassessing sourcing strategies or adapting to tariff-driven operational changes, leveraging CTI can ensure resilience against emerging threats and reduce overall security exposure.
This blog article will delve into the far-reaching impact of tariffs on supply chains, the cybersecurity challenges they introduce, and the actionable strategies you can implement to stay ahead.
Tariffs and Supply Chain Disruption: What’s at Stake?
Tariffs disrupt sourcing, shipping, and manufacturing operations, forcing businesses to reevaluate their supply chains. These adjustments – reshoring, nearshoring, or onboarding new suppliers – bring challenges that extend beyond logistics and costs, creating heightened cybersecurity vulnerabilities.
Key disruptions to supply chain operations include:
- Supplier Shifts: Businesses may need to onboard new suppliers unfamiliar with their security protocols, which can lead to weak cybersecurity postures and vulnerabilities.
- Geopolitical Instability and Potential Violation of Trade Agreements: Regions impacted by tariffs often experience heightened geopolitical tensions. This could lead to violation of trade agreements like the USMCA. Retaliatory measures, including counter-tariffs, add complexity to supply chains, potentially destabilizing operations and amplifying security risks.
- Third-Party Risks: Expanding supply chains to new suppliers or logistics partners creates additional entry points for attackers, increasing the risk of breaches.
- Regulatory Hurdles: Shifting operations may expose companies to compliance risks, as they must navigate varying data protection regulations in different regions.
In result, here’s how tariffs could introduce cybersecurity risks:
- Weak Supplier Security Measures: Newly onboarded suppliers may lack strong cybersecurity measures, increasing exposure to cyberattacks.
- Exploitation of Geopolitical Tensions: Adversaries may target companies tied to regions affected by tariffs, leveraging the instability for cyberattacks.
- Compliance Pressures: Operating in new jurisdictions could require compliance with unfamiliar regulatory frameworks, increasing the risk of oversight.
There’s also the fact of financial pressure:
Economic challenges stemming from tariffs further exacerbate these vulnerabilities. For instance, a study by the National Retail Federation estimates that proposed tariffs could reduce U.S. consumer spending power by $46 billion to $78 billion annually.

Tariffs could lead to significant pressure on U.S. consumers spending power, according to NRF
Such pressures may compel businesses to rush decisions regarding sourcing and logistics, often overlooking critical cybersecurity considerations.
Using Cyber Threat Intelligence (CTI) to Mitigate Supply Chain Risks
The global trade environment, influenced by tariffs and geopolitical tensions, creates opportunities for cyber adversaries to exploit supply chains. The reliance on tariffs during previous administrations caused widespread disruptions in sourcing, shipping, and manufacturing processes. Learning from these challenges, organizations can use Cyber Threat Intelligence (CTI) as a proactive defense mechanism to mitigate risks.
CTI empowers organizations to navigate the uncertainty of tariff-driven supply chain changes by:
- Anticipating Evolving Threats: CTI provides actionable intelligence on emerging risks tied to geopolitical tensions, compromised suppliers, and targeted regions. For instance, phishing campaigns or ransomware attacks targeting new supply chain partners can be detected early.
- Enhancing Supplier Onboarding and Risk Management: CTI enables businesses to evaluate new suppliers’ cybersecurity postures, identify vulnerabilities, and streamline vendor risk assessments to minimize exposure.
- Protecting Sensitive Data and Operations: By monitoring for Indicators of Compromise (IoCs) and threats tied to industry-specific risks, CTI ensures operational disruptions are minimized, and critical data remains secure.
By implementing CTI, organizations gain the strategic ability to foresee and counteract cyber risks associated with tariff-related supply chain adjustments, ensuring business continuity and resilience.
CTI can be implemented effectively in seven steps to help reduce your security exposure:
1. Proactively Assess Risks When Onboarding Suppliers
Onboarding new suppliers introduces potential cybersecurity risks, especially during tariff-driven supply chain transitions. Conducting cybersecurity due diligence is essential to ensure your suppliers meet stringent security requirements. Evaluate their breach history, compliance with data protection regulations like GDPR or CCPA, and overall security posture.
In addition, perform a threat landscape analysis to identify region-specific or industry-specific risks, such as state-sponsored cyberattacks targeting sectors or countries affected by tariffs. Geopolitical tensions and retaliatory measures often amplify these threats, increasing vulnerabilities for organizations operating in impacted regions.
CTI plays a critical role in this process by providing actionable insights into emerging risks and compromised suppliers. With CTI, you can assess vulnerabilities, evaluate supplier reliability, and diversify your network to avoid over-reliance on high-risk regions or partners, defending your operations against evolving threats.
Tariff-driven disruptions and evolving cyber threats can expose vulnerabilities across your supply chain, from insecure suppliers to overlooked risks in critical dependencies. SOCRadar’s Supply Chain Intelligence module provides you with actionable insights into your supply chain, helping you proactively secure your operations.
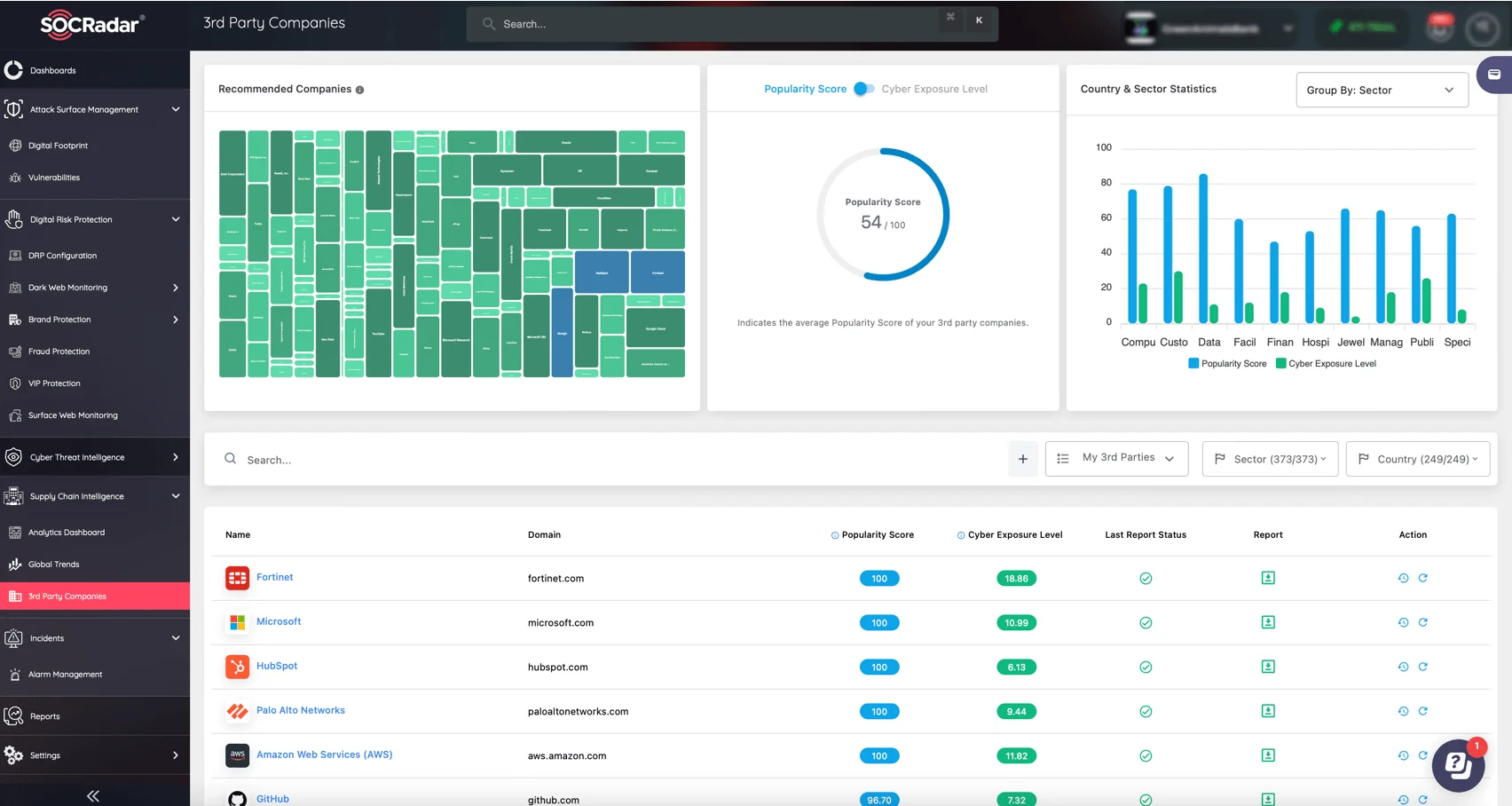
With SOCRadar, you can analyze, monitor, and protect your supply chain in real-time, ensuring resilience against emerging threats and operational risks.
Its key capabilities include:
- Monitoring the cyber exposure of companies in your supply chain to identify and address risks before they impact your business.
- Actionable threat intelligence to address weaknesses and mitigate cyber risks tied to third-parties.
- Risk insights to prepare for regional challenges and avoid disruptions.
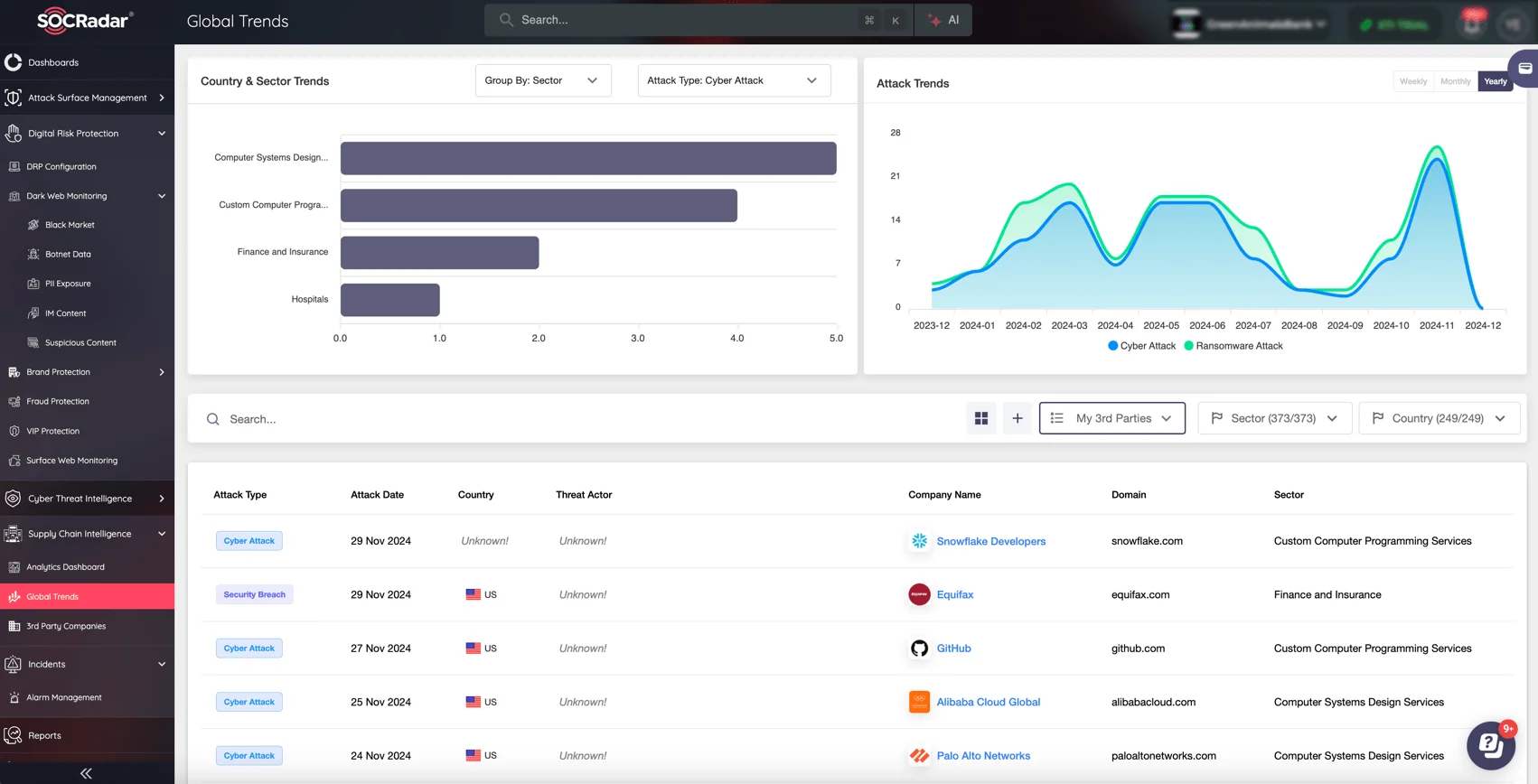
SOCRadar’s Supply Chain Intelligence module, Global Trends
2. Monitor for Emerging Threats in Your Supply Chain
Proactive monitoring of supply chain threats is vital to minimize risks during tariff-related transitions. Threat feed integration powered by CTI enables you to track compromised suppliers and relevant Indicators of Compromise (IoCs). Setting up alerts for supplier-specific domains, IP addresses, and IoCs ensures you stay informed about threats targeting your network.
Additionally, mapping dependencies in your supply chain helps identify critical nodes vulnerable to cyberattacks. Monitor upstream and downstream suppliers for security gaps or breaches that could cascade into your operations. These measures reduce the risk of third-party vulnerabilities disrupting your business.
With the right CTI tools, you can effectively pinpoint high-risk areas, enabling rapid response to emerging threats and safeguarding operational continuity across the supply chain.
3. Improve Cyber Hygiene Among Suppliers
Ensuring strong cyber hygiene among suppliers is a foundational element of supply chain security. Start by implementing risk-based supplier tiers, categorizing suppliers based on their cyber risk and service criticality. High-risk or critical suppliers should adhere to stricter cybersecurity requirements and undergo continuous monitoring to reduce vulnerabilities.
Incorporate strict cybersecurity standards into supplier contracts to enforce best practices, such as those aligned with NIST or ISO 27001 frameworks. These standards mandate strong measures like encryption, regular vulnerability assessments, and incident reporting protocols, to ensure your suppliers meet your security expectations.
By embedding these practices into contracts, you establish a secure foundation for your supply chain and mitigate risks tied to supplier security oversight.
4. Detect Phishing and Fraud Threats Early
Early detection of fraud and cyber threats can prevent significant disruptions to your supply chain. Dark Web monitoring allows organizations to track mentions of suppliers, leaked credentials, or intellectual property, providing critical insights into potential breaches before they escalate.
Phishing and fraud campaigns have long targeted supply chains, with tactics such as counterfeit invoices or phishing attempts aimed at suppliers and employees. With CTI, organizations can identify and neutralize these threats promptly, protecting sensitive data and maintaining operational integrity.
By proactively addressing these risks, you can strengthen your defense against evolving cyber threats, reducing the likelihood of costly disruptions.
The Dark Web remains a hub for threats targeting supply chains – leaked credentials, stolen intellectual property, and supplier compromises can escalate quickly if left unchecked. SOCRadar’s Dark Web Monitoring provides early warning systems to help you detect:
- Leaked credentials of your suppliers or employees.
- Stolen intellectual property tied to your organization.
- Supplier vulnerabilities that could compromise your supply chain security.
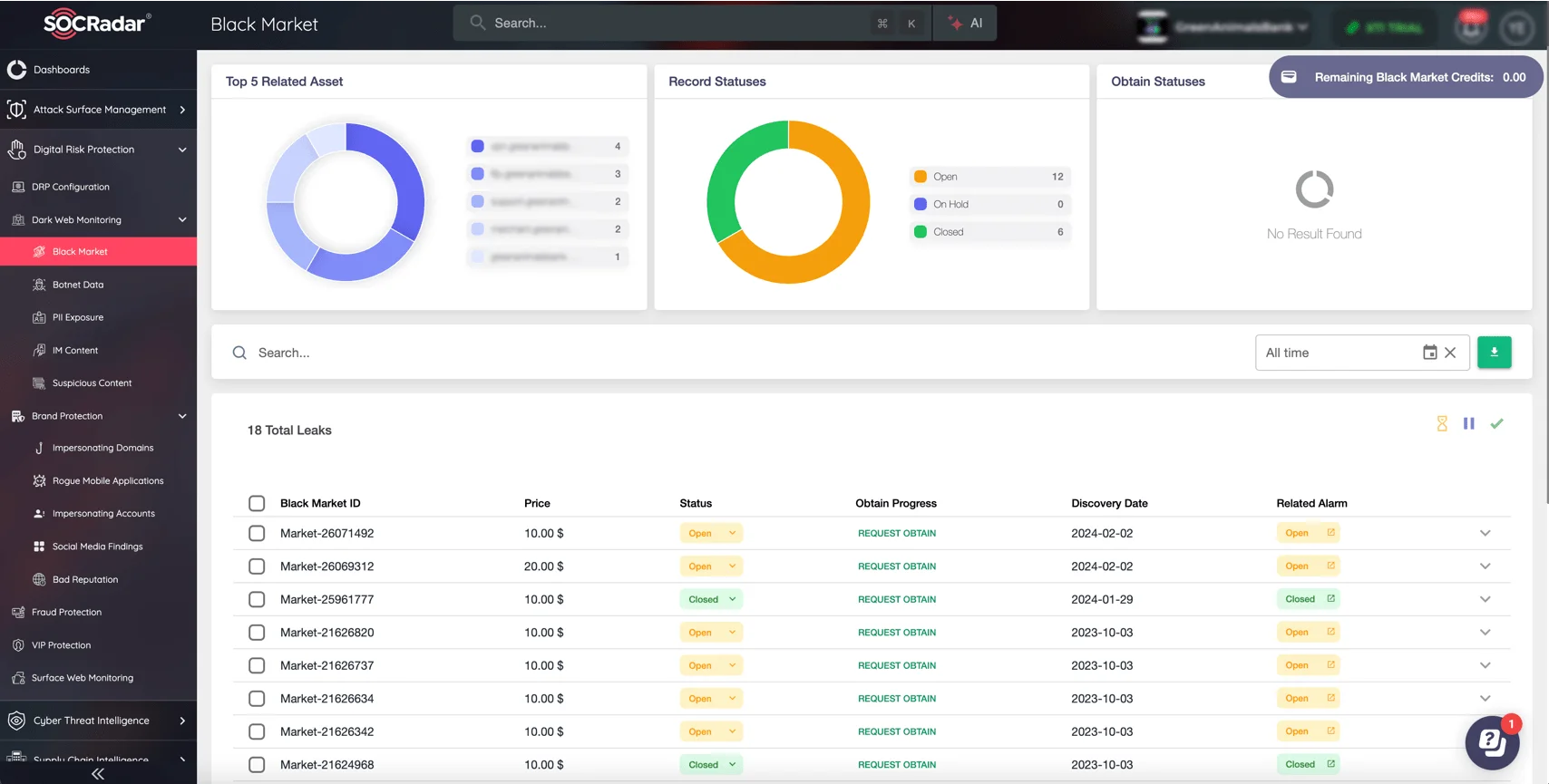
SOCRadar’s Dark Web Monitoring
By tracking mentions of your suppliers, sensitive data, and organizational assets on the Dark Web, SOCRadar ensures you stay one step ahead of potential threats, allowing you to act before risks materialize.
5. Build a Coordinated Incident Response Plan
An effective incident response plan is vital for minimizing the impact of supply chain disruptions. Begin by fostering shared intelligence with your suppliers, exchanging relevant threat information to enhance collective awareness and preparedness.
Develop incident playbooks tailored to supply chain risks, outlining clear response protocols for both internal teams and external suppliers. These playbooks should address scenarios like data breaches, ransomware attacks, and operational outages, enabling swift and coordinated action during a crisis.
Collaboration and preparedness ensure that your organization and its partners can respond to threats efficiently, maintaining resilience in the face of potential disruptions.
6. Mitigate Geopolitical and Trade-Driven Risks
Tariffs and geopolitical tensions can introduce significant vulnerabilities to supply chains, from trade restrictions to state-sponsored cyberattacks targeting specific regions.
To navigate these challenges, organizations should leverage CTI to monitor policy changes and trade developments, allowing them to anticipate risks tied to evolving geopolitical conditions.
Additionally, relying on vendors from a single high-risk region increases exposure; on the other hand, diversifying supplier networks based on insights can strengthen resilience and reduce reliance on unstable areas.
7. Reduce Insider and Social Engineering Threats
Periods of supply chain change often see an uptick in insider risks and social engineering attacks, with threat actors looking to exploit human vulnerabilities. Educating employees and suppliers on identifying and responding to social engineering tactics, such as phishing or impersonation, is a must.
Complementing training efforts, implementing a zero-trust architecture can provide an added layer of security by limiting access to critical systems and verifying all users and devices.
These combined measures significantly reduce the chances of unauthorized actions or breaches, maintaining the integrity of the supply chain.
Conclusion: Adapting Supply Chain Strategies in a Volatile Landscape
Tariff-related disruptions demand a proactive approach to securing supply chains against emerging risks. Integrating Cyber Threat Intelligence (CTI) equips organizations with the tools to anticipate and counteract vulnerabilities, ensuring business continuity and resilience. By leveraging CTI, businesses can mitigate risks tied to geopolitical shifts, regulatory challenges, and cyber threats.
At SOCRadar XTI, we offer a comprehensive Supply Chain Intelligence module designed to assist organizations in managing their supply chain security effectively. This module enables you to:
- Monitor over 50 million companies for cyber risks and vulnerabilities.
- Gain data-driven insights with dynamic scoring to make informed decisions.
- Prioritize high-risk suppliers with customizable alerts and recommendations.
The Supply Chain Intelligence module provides real-time visibility into your entire supply chain network, empowering you to proactively identify and mitigate security threats. With advanced scoring systems, including the Cyber Exposure Level and Popularity Score, you can assess the security posture of your suppliers and respond swiftly to potential incidents.
For more details on how SOCRadar’s Supply Chain Intelligence can enhance your cybersecurity strategy, please visit our Supply Chain Intelligence page.



































