
How to Protect Yourself Against Shodan, BinaryEdge and ZoomEye?
Have you ever wondered how hackers find the IPs, ports, and services required for their attacks? Some attacks need thousands of host computers to find the vulnerable ones. Hackers do not require sophisticated tools to scan the Internet to find potential victims. Tools like search engines are open to everyone, indexing and enumerating for devices and systems.
Let’s look at the famous search engines doing that and how to protect yourselves.
Shodan
Shodan (Sentient-Hyper-Optimized-Data-Access-Network) is mainly a search engine, but it serves a distinct role from other search engines.
Shodan is a search engine that uses multiple criteria to find several computer-based systems. Shodan allows you to scan the Internet for open systems, devices, and devices (desktops, switches, routers, servers, and so on) and classify the results you find depending on their port, type, location, and service information.
BinaryEdge
BinaryEdge essentially collects internet data and makes it searchable on their search engine, similar to Shodan and others. BinaryEdge uses a custom-built platform to scan, gather, and analyze public Internet data, combining Machine Learning and Cybersecurity approaches. This platform scans the entire public Internet and generates real-time threat intelligence streams and reports for your business.
ZoomEye
ZoomEye is the global leader in cyberspace mapping, China’s first and most well-known cyberspace search engine, powered by Knownsec’s 404 Laboratory, and a world-famous cyberspace search engine.
It can continually scan and identify numerous service ports and protocols 24 hours a day and finally map the entire or local cyberspace, thanks to a massive number of global surveying and mapping nodes that use worldwide IPv4, IPv6 address, and website domain name databases. You can also check the vulnerability impact assessment and search for specific themes. Databases, industries, Blockchain, firewalls, routers, network storage, cameras, printers, WAFs, network storage, and other topics are covered in detail in the reports.
How and From Which IPs Do They Scan?
Although Shodan and Google are essentially the same, several differences distinguish data from Google. If it can be evaluated and done, the port that can detect and obtain them (paid). Shodan allows us to access open hidden cameras, SSH servers, online applications, network applications, SCADA and PLC systems, and more.
You can find the IPs below:
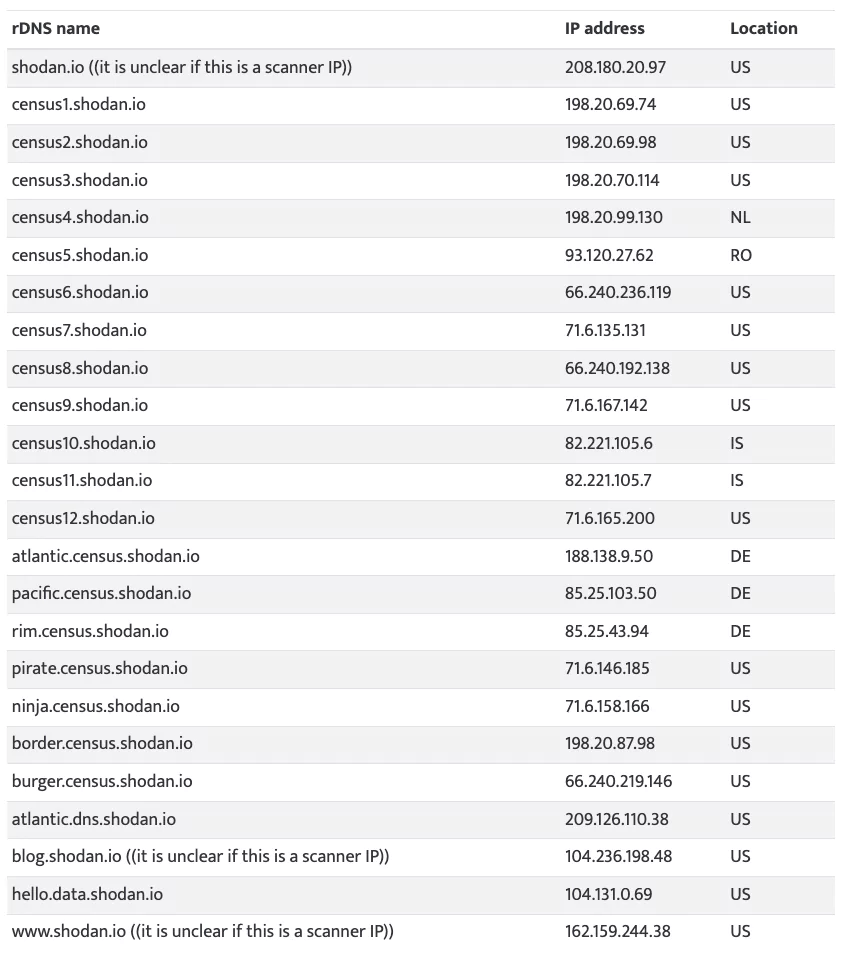
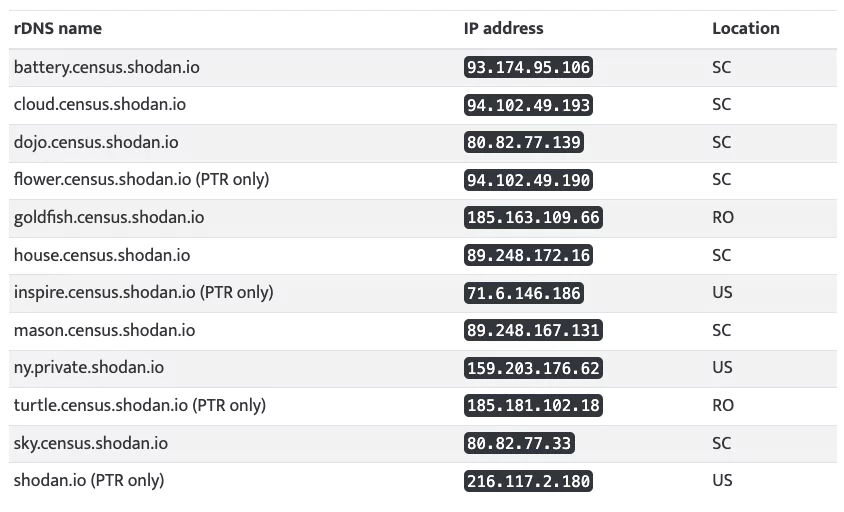
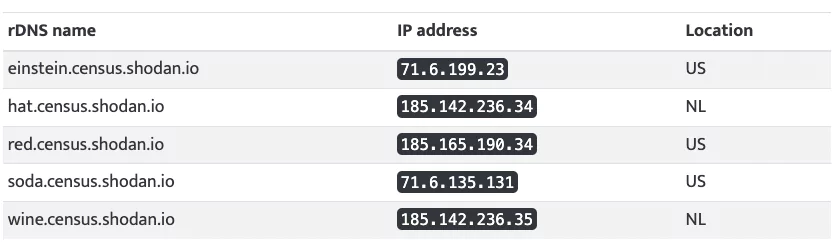
The truth is that neither Shodan, BinaryEdge, ZoomEye, nor other tools endanger businesses. By leaving devices exposed, companies put themselves at risk. Penetration testing tools like these can be mitigated or eliminated with solid security policies.
Users and Servers That are Open to the Public Should be Restricted
Shodan’s, BinaryEdge’s, and ZoomEyes’s methods are systematic, and users should never have looked at the Internet in the first place. Do you require a printer connected to the Internet for your networks, webcams, or file servers? Is it only your internal LAN?
It’s just a matter of network hardware limiting particular hardware and devices. It could also be a network firewall for your incoming system.
External Applications Can Be Accessed Via a VPN or IP Filters
What is the best way to design webcams? To go even further, you’ll need a VPN. This will put your devices in front of browsers like these.
Update Their Password Regularly
It comes with ready-to-use software that you may use as a special offer or acquire your server in this manner. When attackers look at the make and model of references, they also look at their own. It will only be possible to do so in these search engines by creating a default password.
Discounts are Suppressed or Reduced
Some server software allows you to view incoming connections how you’re used to. It will not be stated how much information is taken into account. You can use the information in a topic like version and installation to work on exposing and exploiting attackers’ weaknesses.
Shodan only indexes banners, so keep that in mind. Even if your device is turned on, the user in these is aware of how many of your options banners are for them.
Compete Against Yourself in Shodan, BinaryEdge, and ZoomEye
These search engines’ IP brains are available for use. Despite the dangers they present, avoiding the evils of these search engines is possible by using the ways above.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.



































