
Importance of Indicators of Compromise (IoCs) in CTI for Actionable Intelligence
Whether in the case of a targeted attack or random mass exploitation, using Indicators of Compromise (IoCs) is a crucial aspect in the ongoing challenge to proactively address potential threats.
IoCs, crumbs of data left behind by a cunning adversary, provide invaluable clues and insights that empower cybersecurity professionals to detect, trace, and counteract nefarious activities within networks and endpoints. Ranging from simple identifiers like IP addresses to more intricate patterns indicating potential security breaches, IoCs play a critical role in proactive threat mitigation.

An AI illustration of ‘IoC search and analysis’ (Bing Image Creator)
Without the presence of these essential markers, defenders would be cast adrift, navigating treacherous waters without a compass or stars to guide their way, rendering their efforts reactive rather than proactive, and potentially leaving critical vulnerabilities unaddressed until it is too late.
Our guide in this blog post is RFC 9424, titled “Indicators of Compromise (IoCs) and Their Role in Attack Defence.” Authored by K. Paine, O. Whitehouse, J. Sellwood, and A. Shaw, this informative document, published in August 2023, integrates into our broader discussion on the Importance of IoCs in CTI for Actionable Intelligence.
RFC 9424, published in August 2023
Beyond a basic understanding of IoCs, our journey aims to uncover their intrinsic value and practical applications as significant components in forging actionable intelligence.
The Role of IoCs in Cyber Defense
At the core purpose, an Indicator of Compromise (IoC) serves as a dynamic piece of information, strategically pinpointing malicious activity within the intricate web of networks and endpoints. Much like a detective following a trail of clues, cybersecurity professionals leverage IoCs as proactive tools that go beyond mere identification.
Imagine an IoC as a digital fingerprint, unique to each threat. It could be a specific file hash, a pattern in network traffic, or even the behavior of a potentially malicious application. The diversity of IoCs allows cybersecurity professionals to build a comprehensive understanding of the threat landscape.
IoCs transcend their role as mere identifiers; they embody a proactive approach that combines historical insights, rapid threat mitigation, and continuous adaptation. By analyzing historical IoCs, cybersecurity professionals can anticipate and fortify defenses against evolving attack vectors. For instance, the identification of a recurring IoC may indicate a persistent adversary, prompting enhanced security measures.
Moving on, let’s explore the myriad opportunities presented by IoCs, emphasizing their scalability, efficiency, and pivotal role in countering diverse threats, as emphasized in RFC 9424.
- IoCs as Defense Pillars: IoCs form the backbone of modern defense-in-depth strategies, influencing multiple security layers. Firewalls, IDSs, IPSs, AV, EDR, and SIEM platforms leverage IoCs to identify and mitigate threats effectively. The strategic deployment of IoCs across different layers ensures a nuanced defense mechanism tailored to specific organizational needs.
- IoCs for Small Entities: IoCs offer a cost-effective and scalable defense mechanism, making them especially valuable for smaller entities with limited resources. Even with basic security measures, small organizations can leverage IoCs to establish baseline protection against known threats. The ease of IoC deployment minimizes the need for extensive training, providing significant benefits across resource capabilities, maturity, and sophistication.
- Multiplying Defense Efforts: IoCs possess a multiplier effect on defense efforts, offering widespread protection that scales efficiently across an organization. Individual IoCs can safeguard thousands of users, and their application extends beyond direct sharing. Collaborative defenses, such as protective DNS filtering services, enhance the effectiveness of IoCs, preventing threats at an early stage and mitigating risks for various parties.
- Seamless Sharing and Time Savings: The ease of sharing IoCs contributes to blanket coverage for organizations, allowing for widespread mitigation in a timely manner. Quick distribution through established channels ensures that individual IoCs may protect thousands of organizations. This seamless sharing not only saves time by avoiding duplication of investigation efforts but also enables automatic deployment at scale, minimizing human intervention and effort.
- Historical Attack Discovery: IoCs facilitate the discovery of historic attacks by enabling network defenders to utilize recently acquired indicators in conjunction with historical data. This retrospective approach helps build a clear picture of past attacks, allowing for proactive mitigation and an enhanced understanding of cybersecurity incidents.
- Attribution to Specific Threats: Contextual information tied to IoCs provides crucial insights for organizations to assess and prioritize risks from identified threats. This contextual information, shared alongside IoCs, allows organizations to focus their defenses on specific risks. While producing this contextual information requires analytical effort, specialist tools, and training, it enhances the technical freedom of organizations in choosing their risk appetite, security posture, and defense methods.
SOCRadar’s Threat Feed & IoC Management module enables cybersecurity teams to find Indicators of Compromise (IoCs) more effectively and lightning-fast. Instead of navigating through multiple threat intelligence sources, security experts can conduct IoC searches from a single, centralized platform.
Furthermore, the module supports bulk searches, allowing users to query multiple IoCs or IPs from a single screen. This functionality proves very useful, particularly when defenders are dealing with newly emerging threats and time is of the essence.
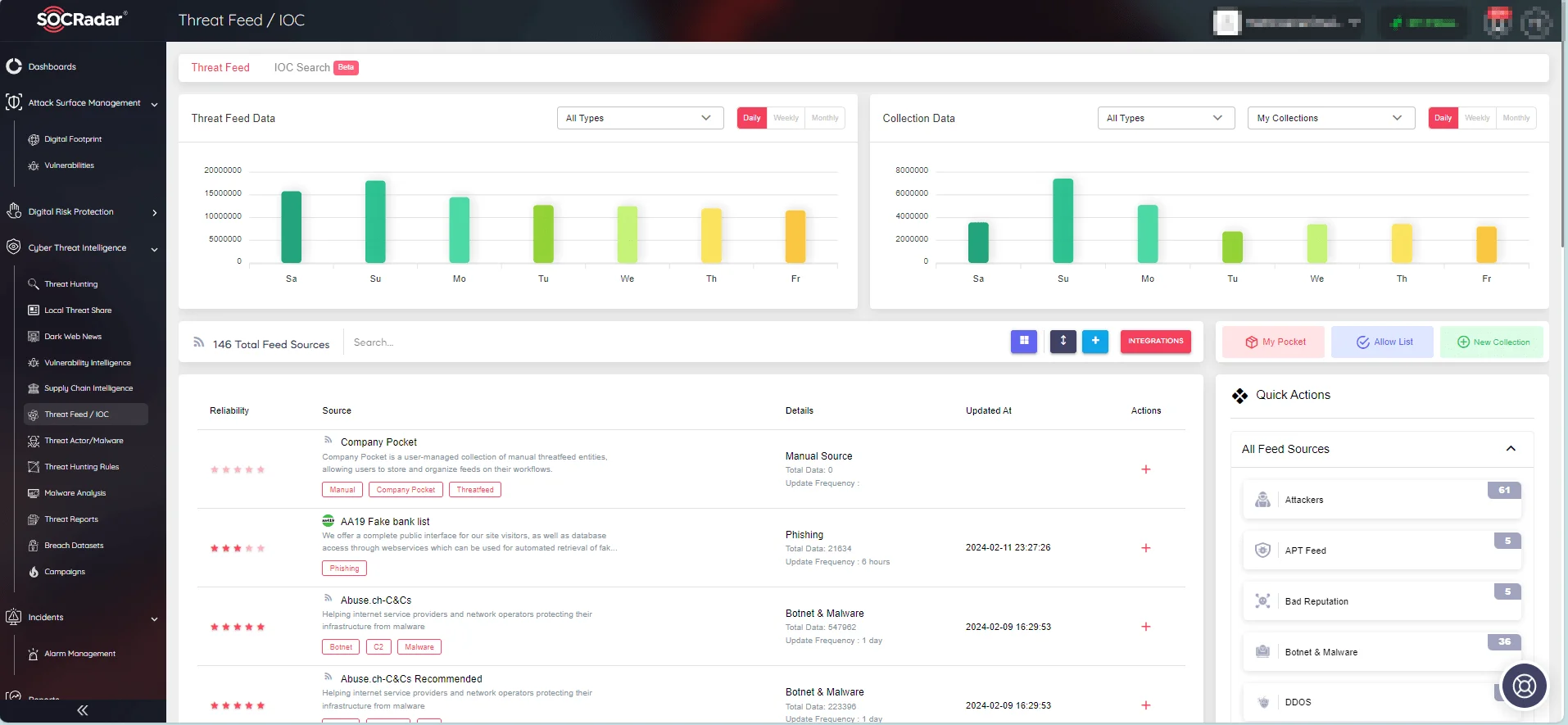
With SOCRadar’s Threat Feed & IoC Management module, cybersecurity professionals can optimize their threat intelligence processes and respond quickly to new threats.
Test the IoC search capabilities provided by the module through SOCRadar Labs’ IoC Radar, a complementary feature.
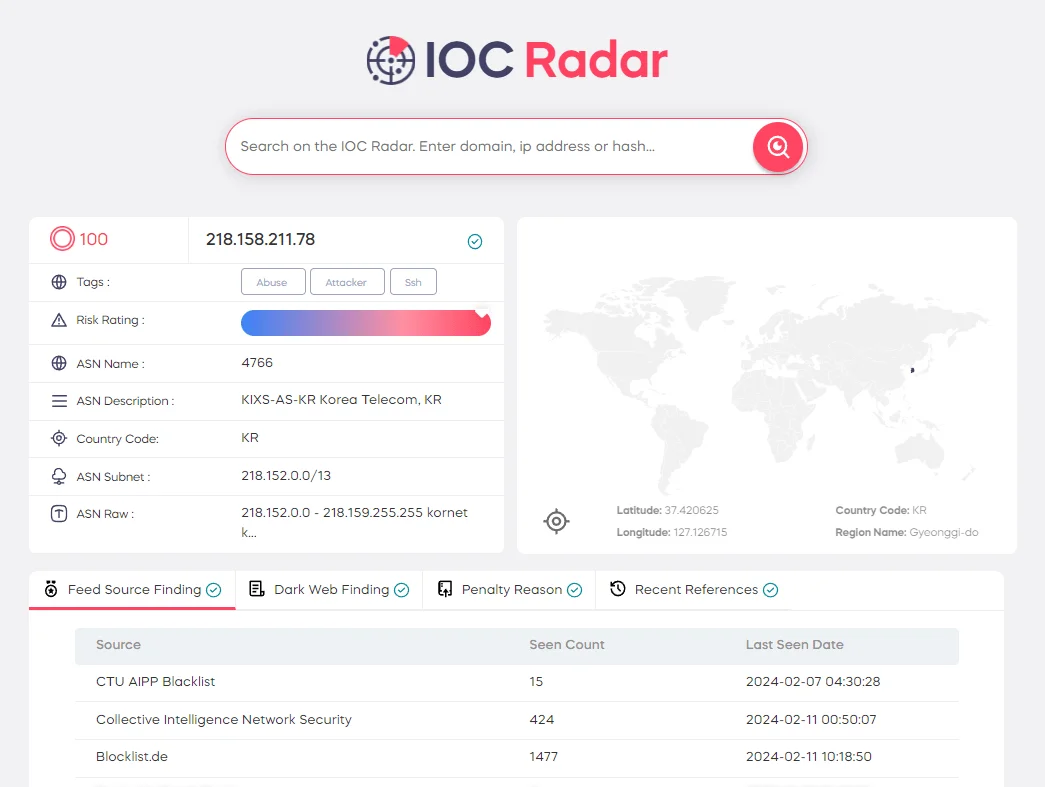
IoC Radar uses artificial intelligence-supported algorithms to provide contextual information about relevant IoCs, allowing you to search for IoCs associated with threat actors and malware.
Making IoCs More Actionable
The effectiveness of Indicators of Compromise (IoCs) relies on their transformative potential from mere identifiers to actionable tools. This transformation is contingent upon key factors—timeliness, accuracy, and relevance.
- Timeliness: The evolving nature of cyber threats demands a timely response. IoCs should be swiftly identified, analyzed, and integrated into defense mechanisms. Addressing this need, the lifespan of an IoC, as discussed in RFC 9424, may be predefined or automatically determined based on its initial characteristics. A prompt end-of-life strategy ensures defenders focus on pertinent threats, minimizing the risk of false positives.
- Accuracy: IoCs must be precise and reliable to be effective. Fragility and precision, as outlined in RFC 9424, influence an IoC’s lifespan. Defenders rely on the accuracy of these indicators to avoid missteps and false alarms.
- Relevance: IoCs are not standalone entities – they require context for meaningful action. Understanding the source, attacker methods, and potential impact enriches the decision-making process for defenders. As highlighted in RFC 9424, IoCs may become invalid due to shifts in threat actor Tactics, Techniques, and Procedures (TTPs) or defender remediation actions, underscoring the importance of contextual awareness.
You can rely on SOCRadar’s Alarms to provide you with contextual awareness by supplying quick insights about security incidents. Real-time alarms sent by the SOCRadar platform offer information about the source and potential impact of a potential security incident, simplifying the response process for defenders.
In essence, SOCRadar’s Alarms elevate the actionable nature of IoCs by delivering timely alerts, accurate information, and relevant context for security incidents. This helps cybersecurity teams effectively respond to threats and minimize the risk of false positives.
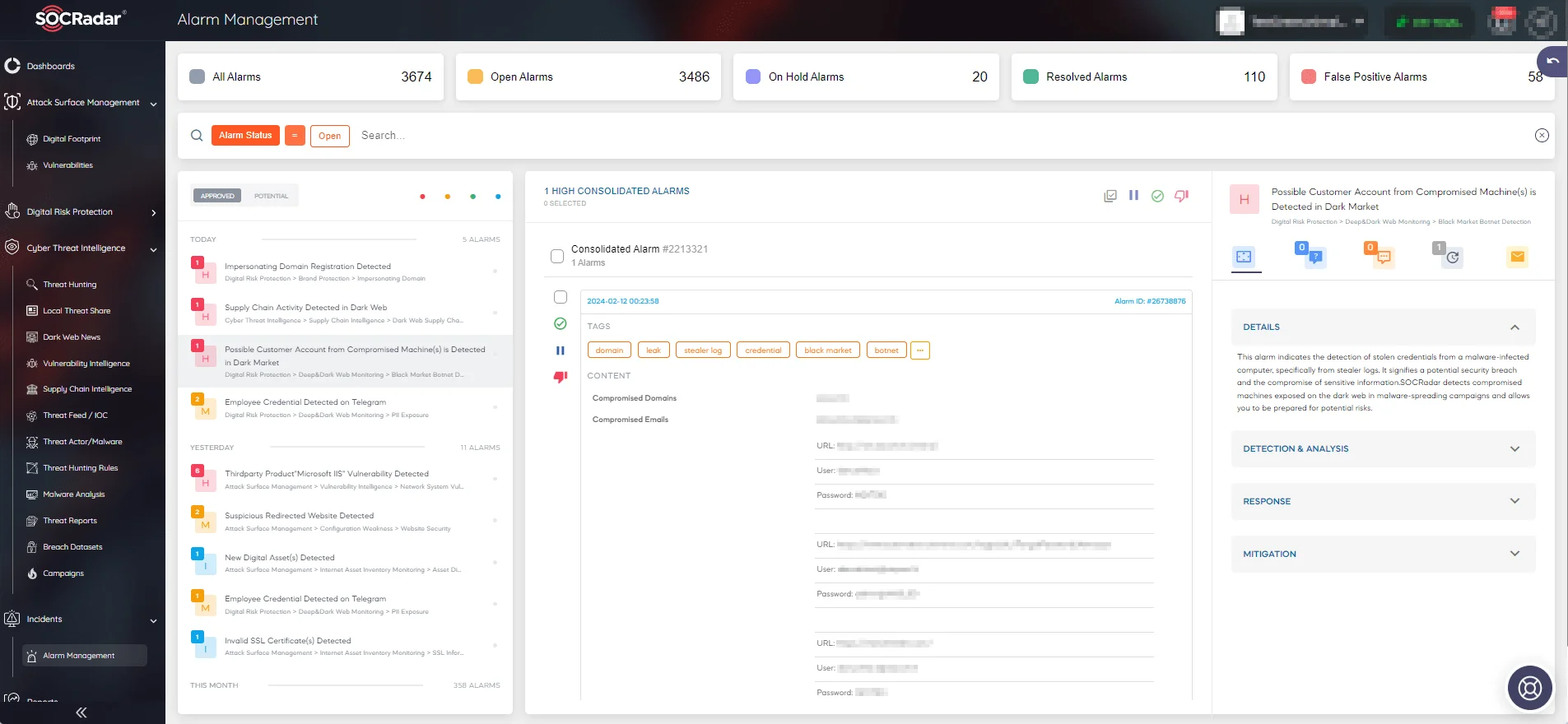
Alarm management page on the SOCRadar platform
Advanced Strategies for Turning IoCs Into Actionable Intelligence
RFC 9424 mentions two concepts – the Pyramid of Pain (PoP) and the Lifecycle of an IoC – to enrich the understanding of how IoCs can contribute to a broad range of defenses, and be actionable.
The Pyramid of Pain (PoP)
At the foundation of effective threat mitigation lies the concept of the Pyramid of Pain (PoP). This model classifies cyber threat indicators based on the varying levels of difficulty adversaries encounter when attempting to evade detection and sustain their attacks. The PoP serves as a guide for analysts, urging them to prioritize impactful strategies against adversaries’ tactics and tools.
For example, detecting and blocking a malicious IP address may provide a temporary barrier, but adversaries can swiftly adapt by changing the IP. Conversely, focusing on higher tiers of the PoP, such as unique malware binaries or Tactics, Techniques, and Procedures (TTPs), delivers more resilient defenses. Prioritizing higher tiers makes it significantly more challenging for adversaries to modify their tactics and continue their attacks.
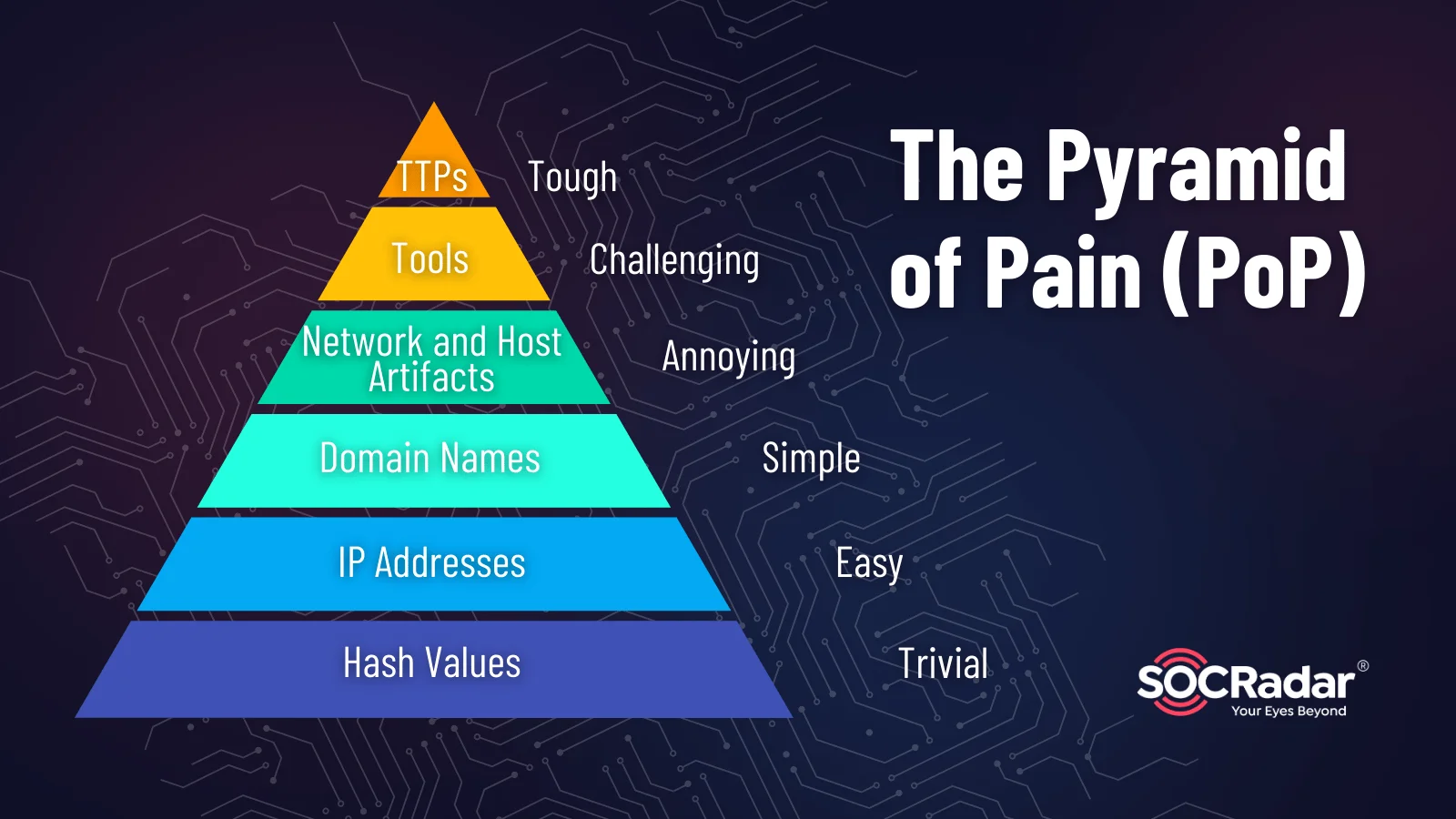
The Pyramid of Pain (PoP)
Understanding the PoP empowers cybersecurity teams to strategically focus on higher tiers, such as TTPs, in their defense efforts. Prioritizing these higher tiers ensures a more resilient defense posture, making it arduous for adversaries to adapt and persist in their attacks.
Cybersecurity teams can prioritize tracking and blocking TTPs, ensuring a more robust defense against evolving threats. Regularly updating IoC databases becomes imperative, aligning defenses with the latest threat intelligence.
The Lifecycle of an IoC
The Lifecycle of an IoC elucidates the stages an IoC traverses from discovery to deployment and eventual end-of-life. Whether identified through routine network traffic analysis or threat feeds, an IoC undergoes a journey of validation, deployment, and continuous monitoring.
For example, suppose an IoC is discovered during network traffic analysis, signaling an unusual data transfer pattern. This IoC is then validated and deployed across the network to thwart similar patterns. As the threat landscape evolves, the IoC may reach its end-of-life due to changes in threat actor Tactics, Techniques, and Procedures (TTPs) or remediation actions taken by defenders, as it loses its relevance.
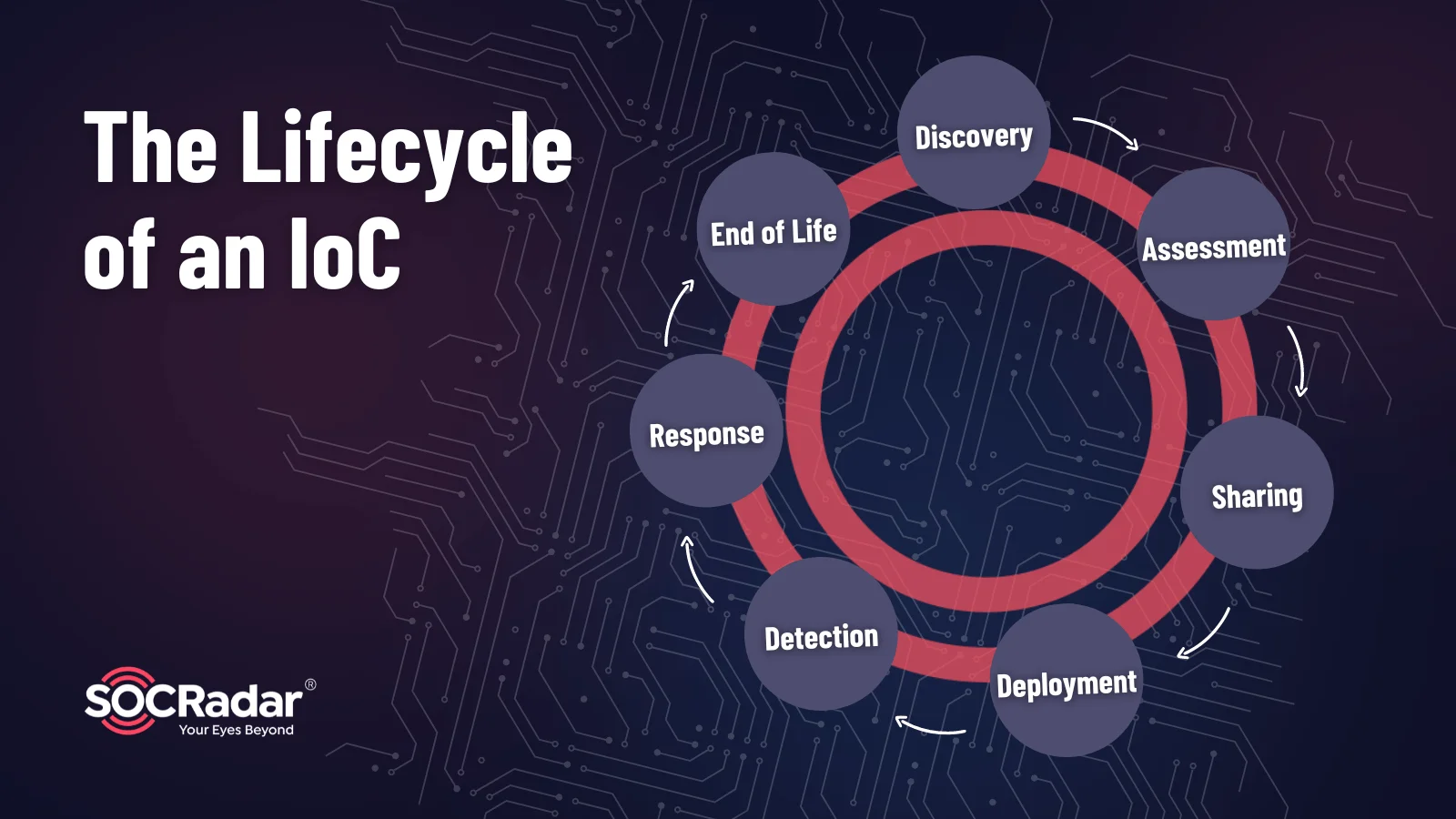
The Lifecycle of an IoC
Comprehending the IoC Lifecycle guides organizations in managing and updating IoCs effectively. From discovery to deployment and eventual retirement, organizations must adapt IoCs to evolving threat landscapes, ensuring a proactive response.
Regularly update IoCs to stay ahead of emerging threats. Implement automated processes for IoC deployment and removal to streamline defense operations. By aligning IoC strategies with the dynamic threat landscape, organizations enhance their resilience against evolving cyber threats.
Fundamental Requirements for Better Intel Sharing
For Indicators of Compromise (IoCs) to wield true efficacy, their detectability must extend seamlessly across a diverse spectrum of internet protocols, tools, and technologies. This broad coverage is achieved through standardization and interoperability, ensuring uniform detection across network traffic, endpoint logs, and application layers.
Cybersecurity systems, ranging from firewalls to Intrusion Detection Systems (IDSs) and antivirus solutions, align through practical implementation of standardized practices. This alignment enhances their collective ability to identify and mitigate threats, fostering a holistic defense strategy adaptable to evolving threats.
Shared language, standardized formats, and interoperable systems streamline the sharing process, allowing IoCs to seamlessly traverse different platforms. Key standards, including Structured Threat Information Expression (STIX), Malware Information Sharing Platform (MISP) core, OpenIoC, and Incident Object Description Exchange Format (IODEF), provide a common ground for IoC representation.
In practical terms, security professionals benefit from platforms adhering to these standards, enabling effortless integration and information exchange. Standardized formats facilitate the creation of structured feeds, enhancing IoC distribution through mechanisms like Trusted Automated Exchange of Intelligence Information (TAXII) and Malware Information Sharing Platforms (MISP).
All in all, IoCs gain actionable significance when shared with timely, accurate, and relevant context, detailing the source, attacker methods, and potential impact; and a standardized language ensures shared information retains value and comprehensibility across diverse cybersecurity landscapes. Embracing a common format empowers cybersecurity professionals to enhance collaboration, sharing IoCs with context-rich details. This collaborative approach enables a collective defense strategy, where threat intelligence is shared effectively, enabling organizations to proactively fortify their defenses against impending threats. In the ever-evolving landscape of cyber threats, these fundamental requirements lay the groundwork for an effective and collaborative defense against malicious activities.
Operational Challenges and Recommendations
Navigating the realm of Indicators of Compromise (IoCs) comes with its operational challenges, presenting a landscape where privacy and data protection concerns loom large. Effectively harnessing IoCs in cyber defense necessitates addressing these challenges head-on.
- Operational Limitations: Defenders must navigate the trade-offs between false positives and the risk of missing attacks when working with different types of IoCs.
- Fragility: The robustness of IoCs must be balanced with the potential for adversaries to alter them, requiring defenders to find a delicate balance.
- Discoverability: Proactive hunting or reactive investigation is necessary to unearth IoCs, with effort influenced by IoC types, attacker sophistication, and timing.
- Completeness: Some IoCs result in a limited set, while others may yield extensive lists, requiring a pragmatic decision on reasonable coverage.
- Precision: The specificity of IoCs, such as hash values or network artifacts, must be balanced to minimize false positives while crafting effective defense strategies.
- Dual and Compromised Use: Context is crucial in determining the efficacy of an IoC, especially when it comes to IP addresses associated with cloud services or compromised legitimate servers.
- Privacy Concerns: Defenders must find a balance between sharing sufficient context for effective detection and safeguarding individual privacy, particularly in larger groups or settings lacking strong inter-member trust.
Addressing these challenges can be aided by automation, streamlining IoC ingestion, processing, and deployment for faster correlation and tailored responses.
In conclusion, a nuanced approach is necessary to overcome operational challenges and fully harness the potential of IoCs in bolstering cyber defenses.
Conclusion
To wrap up, in this blog post, we discussed the role of Indicators of Compromise (IoCs) and emphasized their vital role in boosting cybersecurity, drawing notes from RFC 9424.
The importance of standardized practices and a shared language for IoCs stands out, promoting effective detection and information sharing. The need for timely, accurate, and context-rich intelligence stresses the value of collaborative efforts for robust threat response.
Operational challenges, like balancing IoC robustness and privacy concerns, reveal the intricate landscape defenders navigate. Automation emerges as a key ally, streamlining IoC management and promoting efficient correlation.

































