
Major Cyber Attacks in Review: February 2024
February 2024 witnessed significant cyber attacks across industries like healthcare, energy, and cryptocurrency, highlighting the persistent threats organizations face. Known threat actors such as BlackCat (ALPHV), IntelBroker, Cactus, and a ransomware related to the Phobos family were involved in the major cyber attacks of February 2024.
To enhance vigilance against such threats, explore SOCRadar’s Cyber Threat Intelligence capabilities through Freemium.
In this blog post, we delve into the pivotal cybersecurity events of February 2024, their implications, and the valuable lessons they offer for securing our digital future.
BlackCat/ALPHV Ransomware Group Claims Massive Data Breach at Change Healthcare
The BlackCat/ALPHV ransomware group has admitted to orchestrating a cyberattack on Optum, a subsidiary of UnitedHealth Group (UHG), causing a disruptive outage on the Change Healthcare platform.
The platform, a critical payment exchange network utilized by over 70,000 U.S. pharmacies, suffered a breach of approximately 6TB of sensitive data. According to the group’s dark web announcement, the stolen data includes proprietary source code, patient records, insurance details, and payment information belonging to various healthcare providers and insurance companies.
Among the affected entities are the U.S. military’s Tricare healthcare program, Medicare, CVS Caremark, MetLife, and numerous healthcare insurance providers. The compromised data encompasses millions of individuals’ medical, dental, and insurance records alongside Personally Identifiable Information (PII). Optum, UnitedHealthcare, and UnitedHealth Group systems remain unaffected by the breach.

Victim listing of BlackCat Ransomware (SOCRadar Dark Web News)
IntelBroker Exposed 2.5M Private Plane Owners’ Records
The threat actor IntelBroker, claimed to have breached Los Angeles International Airport’s (LAX) database in February 2024, compromising 2.5 million private plane owners’ records.
The stolen data included names, email addresses, company names, plane model numbers, CPA numbers, and tail numbers. Exploiting a vulnerability in the airport’s Customer Relationship Management (CRM) system, IntelBroker gained unauthorized access.
IntelBroker disclosed the LAX breach on BreachForums, adding to their list of high-profile hacks.
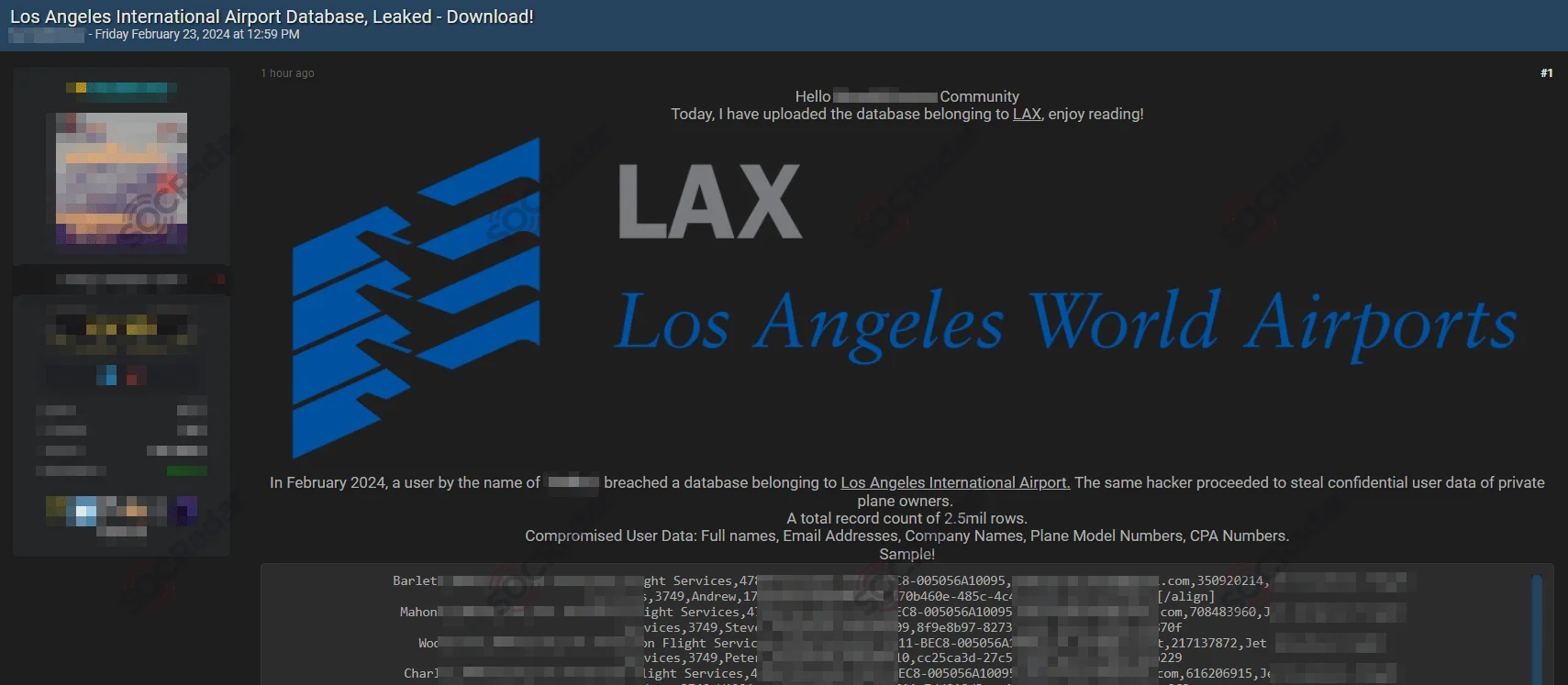
The LAX breach post on the hacker forum (SOCRadar Dark Web News)
Arizona Ophthalmology Firm Notifies 2.4 Million Patients of Data Breach
Medical Management Resource Group (MMRG), operating as American Vision Partners, disclosed a November cyberattack affecting nearly 2.4 million patients across multiple states.
The firm works with several ophthalmology practices, such as Barnet Dulaney Perkins Eye Center, Southwestern Eye Center, and Retinal Consultants of Arizona, among others.

The logo of American Vision Partners
The healthcare breach, involving a network server hack, exposed patient data including names, birthdates, medical records, and in some cases, Social Security numbers and insurance details. Prompt actions were taken, including isolating the affected system and engaging cybersecurity experts.
MMRG advised affected patients to monitor credit reports and account statements and offered two years of identity and credit monitoring.
FixedFloat Crypto Exchange Hacked for $26 Million
FixedFloat, a decentralized crypto exchange, fell victim to a hack, resulting in the loss of at least $26 million in Bitcoin and Ethereum. Users reported frozen transactions and missing funds since February 17, with over 400 Bitcoin and 1,700 Ether tokens drained a day later.
Statement of FixedFloat on X
The exchange investigated the security breach, confirmed to be an external attack. Despite initial speculation, the company denies internal involvement. Cybersecurity experts suggest vulnerabilities led to the breach, potentially enabling a wallet drainer attack.
While no user funds were compromised, 30 outstanding orders were affected. FixedFloat, criticized for delayed disclosure, assured users of imminent service restoration and planned to issue a comprehensive post-incident report.
Schneider Electric Targeted by Cactus Ransomware Group in 1.5TB Data Breach
The Cactus ransomware group claimed responsibility for a significant data breach at Schneider Electric, a global leader in energy and automation.
Approximately 1.5TB of data was stolen from Schneider Electric’s Sustainability Business division on January 17, 2024, causing service disruptions to the Resource Advisor cloud platform.

Schneider Electric leak post on Cactus Ransomware’s site. (SOCRadar Dark Web News)
While Schneider Electric confirmed the breach, they assured that other divisions remained unaffected. The Cactus ransomware gang substantiated their claim by publishing 25MB of purportedly stolen data on their Tor leak site, including images of passports and company documents.
Explore the tactics and operations of Cactus Ransomware on SOCRadar’s Dark Web Profile: Cactus Ransomware article.
Data Breach Impacted 2.4 Million Integris Health Patients
Oklahoma City’s Integris Health faced a data breach affecting 2.4 million patients, where hackers sent extortion emails directly to some victims threatening to sell their sensitive data unless demands were met by January 5, 2024. The breach was discovered on November 28 and reported on February 6.
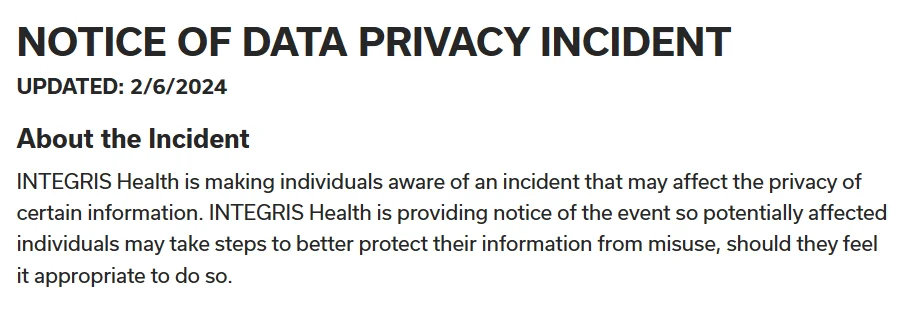
Notice of data privacy incident (Integris Health)
Integris faced class-action lawsuits, with patients alleging delayed notifications. The FBI sought information from those contacted by threat actors, who demanded $50 or threatened to sell patient data on the dark web. Integris, amidst ongoing investigations, remained cautious about divulging specifics.
Massive PLA Token Breach Rocks PlayDapp Ecosystem
Cyber threat actors exploited a stolen private key to mint and steal 1.79 billion PLA tokens from the PlayDapp cryptocurrency ecosystem, which trades in NFTs. The amount of tokens is valued at $290.4 million.

The logo of PlayDapp (PLA)
The breach was reported on February 9, 2024. In response, PlayDapp swiftly moved all tokens to a secure wallet and offered a $1 million “white hat” reward for the return of stolen assets, subsequently threatening legal action against the perpetrators.
Despite efforts to curtail trading and freeze hacker accounts, the tokens’ circulation poses a severe threat to legitimate holders. The attack is mentioned to bear similarities to the operations of Lazarus Group, echoing previous breaches in the crypto-gaming sector, although there has not been a certain attribution for this incident.
PlayDapp urged users to stay vigilant against potential phishing attempts. You can read more about the cyber schemes threatening the cryptocurrency industry in our blog posts:
100 Romanian Hospitals Offline Due to Phobos Ransomware Attack
A ransomware attack has paralyzed 100 hospitals across Romania, targeting the Hipocrate Information System (HIS) used for medical management and patient data. The Romanian Ministry of Health confirmed the attack, with 25 hospitals already reporting encrypted data and 75 others shutting down systems as a precaution.
The cybercrime, demanding 3.5 bitcoin for decryption, prompted a national cybersecurity probe. Per the Romanian National Cyber Security Directorate, affected hospitals are cautioned against contacting the attackers or paying the ransom. The attackers used a ransomware identified as Backmydata from the Phobos family, which highlighted ongoing threats to the healthcare sector.
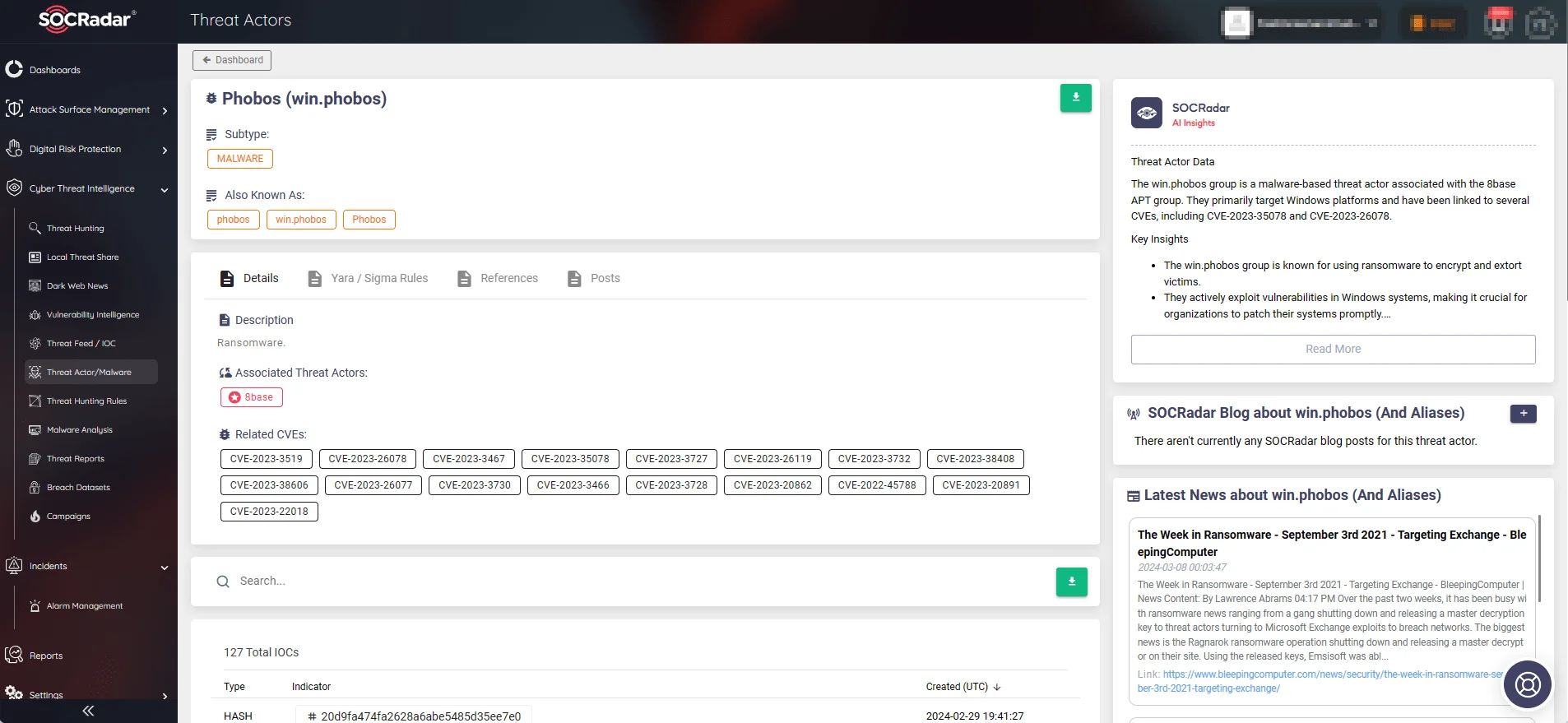
Phobos Malware on SOCRadar’s Threat Actor/Malware page
Major Cyber Attack on French Healthcare Services Firm Viamedis
A cyber attack hit the French healthcare services firm Viamedis, leading to the exposure of sensitive data of policyholders and healthcare professionals. A successful phishing attack on an employee initiated the breach, resulting in unauthorized access to people’s information, including marital status, date of birth, social security numbers, and health insurer details.
Viamedis, however, confirmed that the breach did not compromise banking information, postal details, and contact information.
The full scale of the breach remains undetermined, but it could potentially impact 20 million insured individuals across 84 healthcare organizations for which Viamedis manages payments.
In response to the cyber attack, Viamedis already informed the impacted health organizations, lodged a complaint with the public prosecutor, and notified the authorities.
You can receive a free industry landscape report through SOCRadar Labs, in which you will find insights into current threats looming over the landscape.
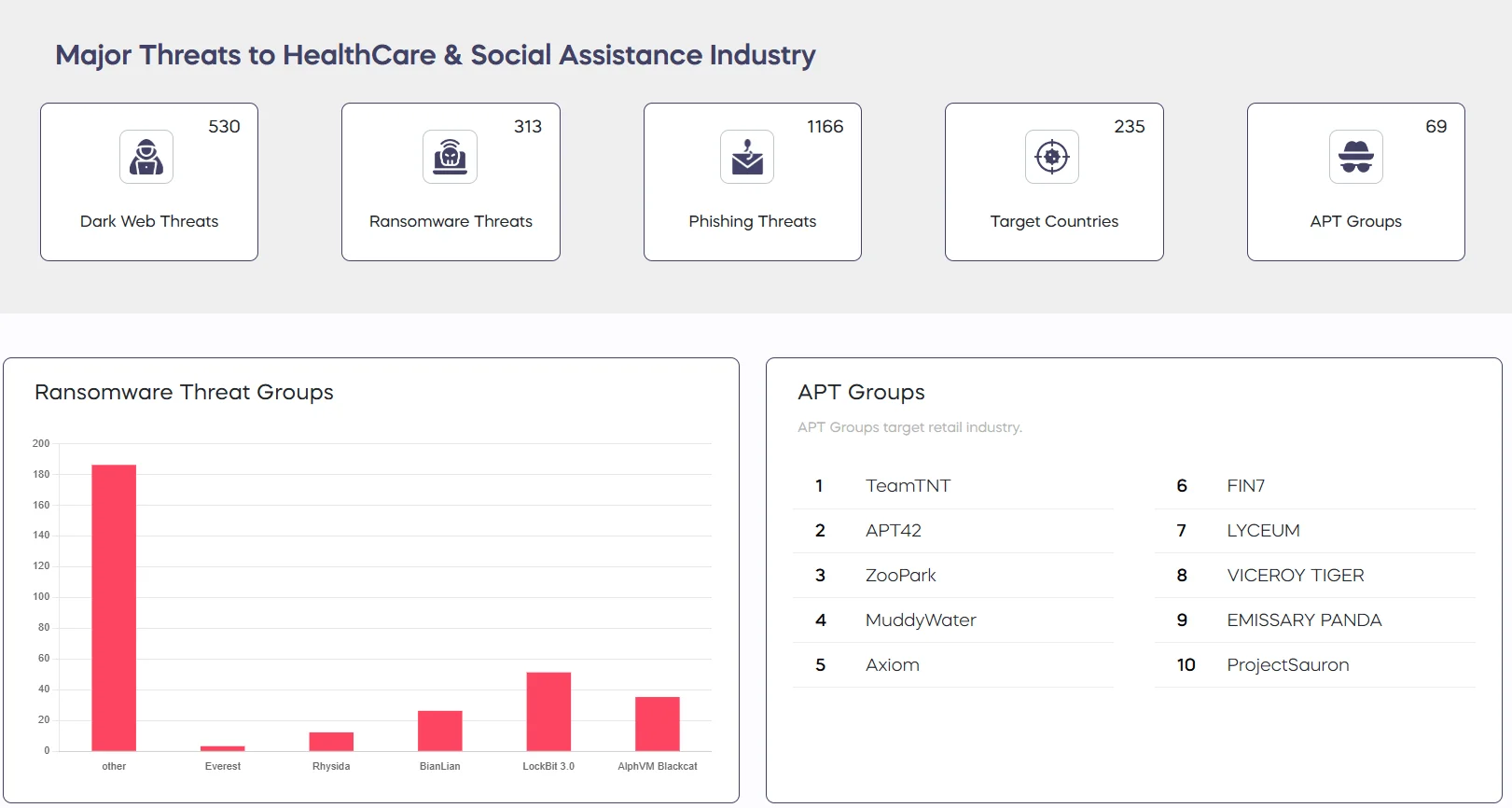
Industry Landscape Report page for Healthcare (SOCRadar Labs)


































